Method and apparatus for logging wireless subscription to wireless terminal, wireless terminal and adscription system
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
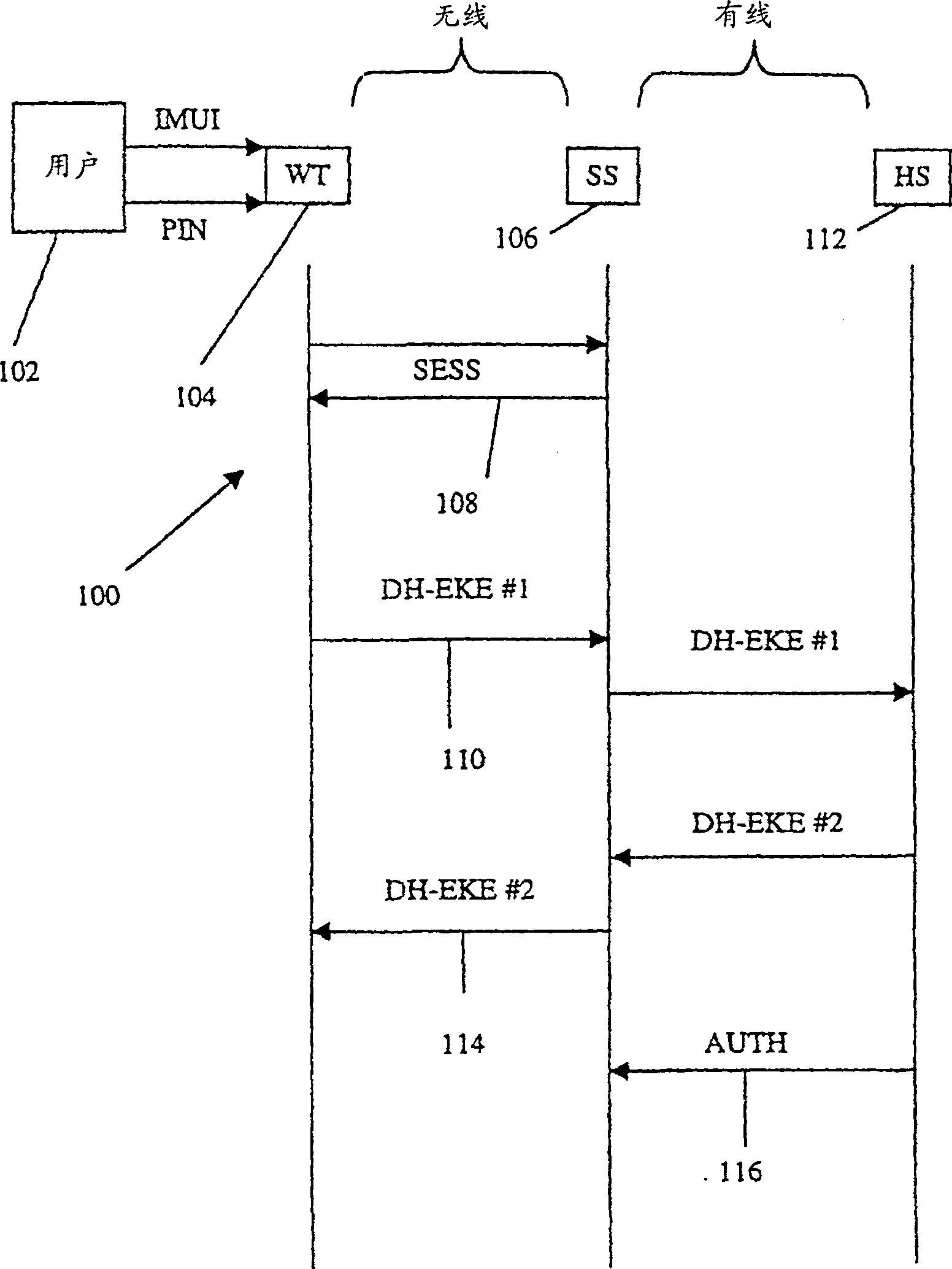
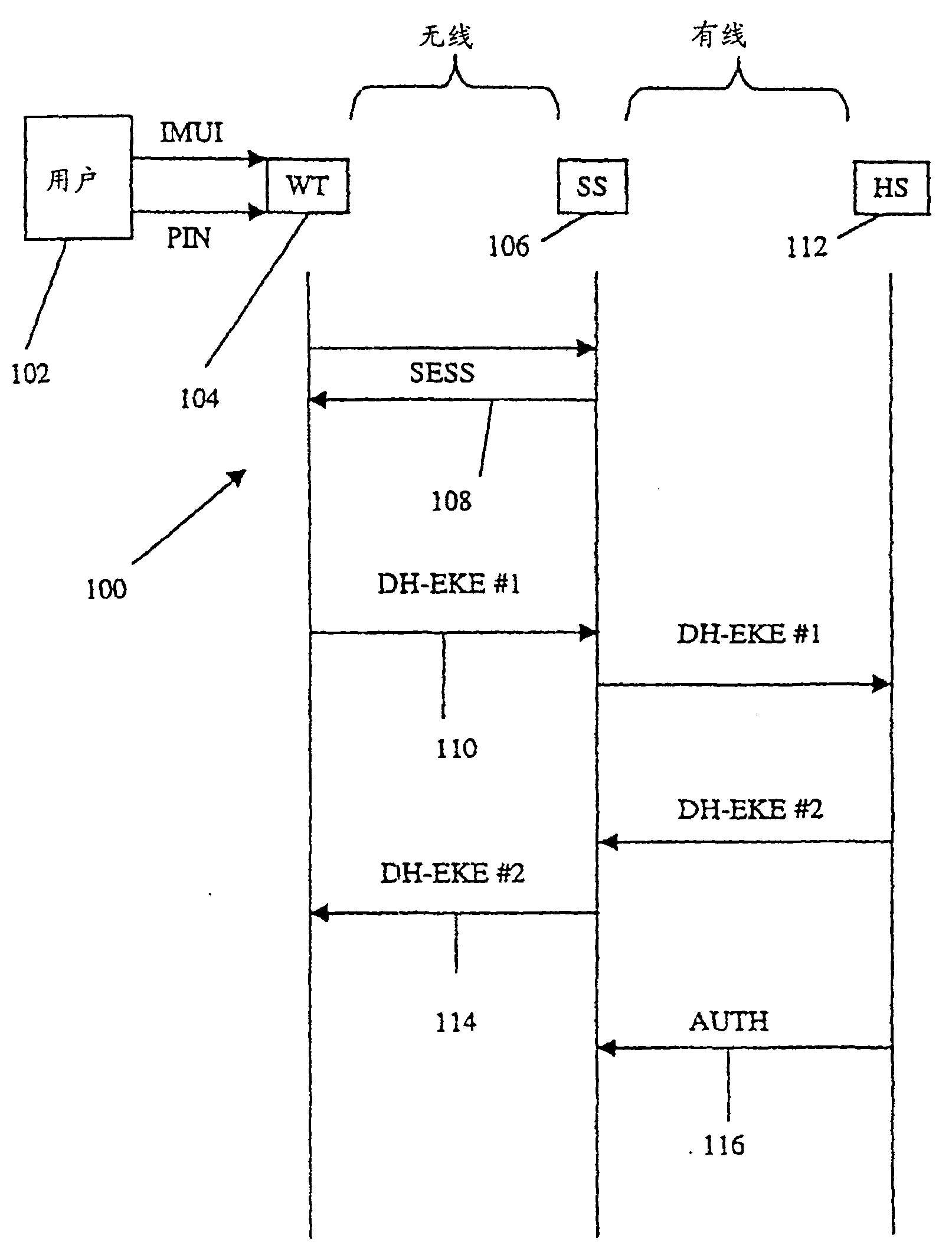
[0035] figure 1 An exchange 100 of DH-EKE messages is shown. User 102 enters his identifier and password into wireless terminal 104 . Terminal 104 tries a pair of Diffie-Hellman (D-H) private and public keys and stores them. Optionally, the terminal 104 and the base station of the serving system 106 perform separate procedures to establish a local session encryption key SESS 108 to protect the user identifier from interception. The terminal 104 encrypts the D-H public key with a cipher, optionally linked with a random number before encryption, and then in the registration request, the user identifier (optionally encrypted under the local session key) and the encrypted public key, i.e., The first DH-EKE message 110 is sent to the base station of the serving system 106 . This requirement should result in dedicated channel allocation, thereby efficiently completing the download process.
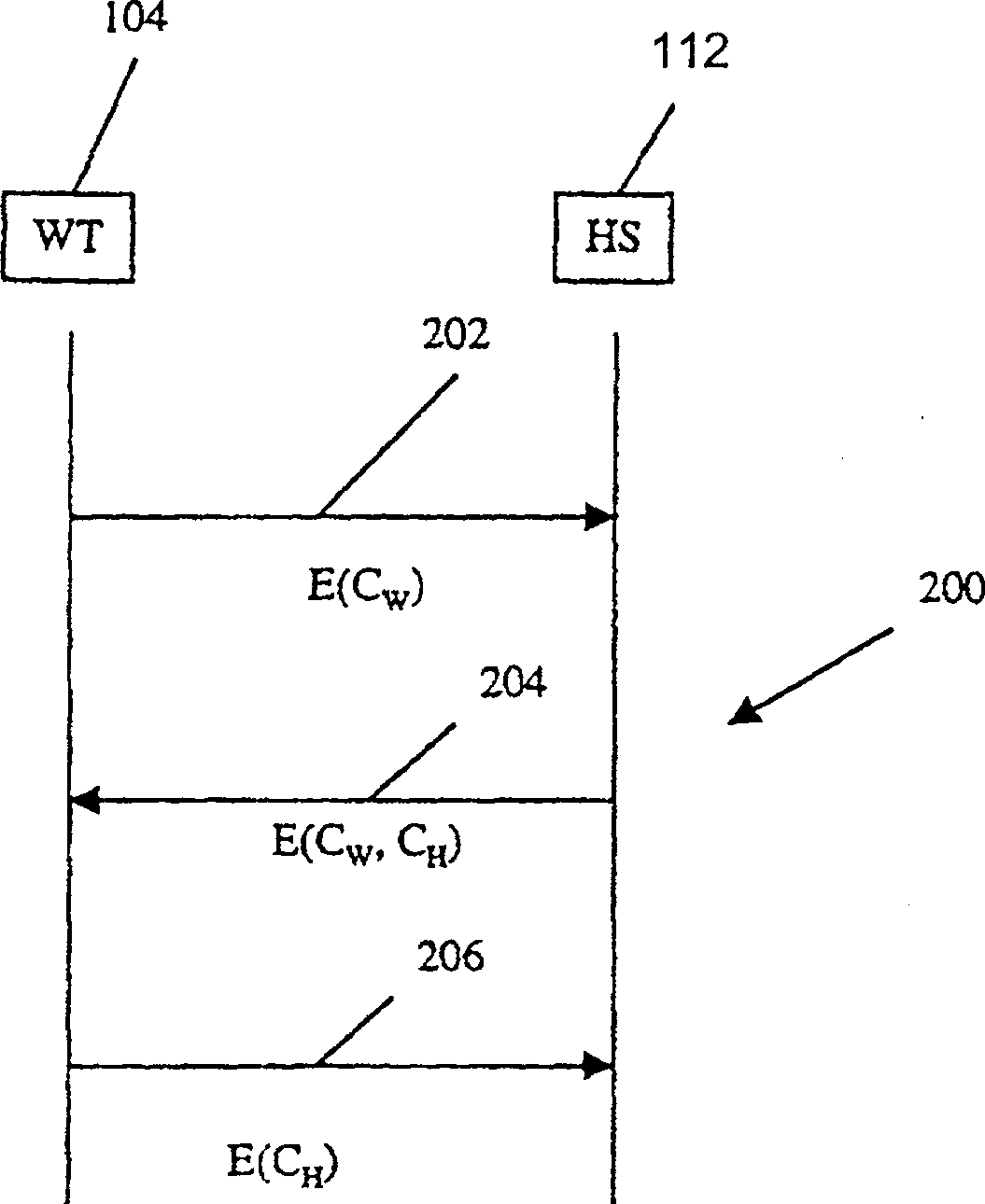
[0036] The service system 106 contacts the home system 112 requiring subscription regis...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com