Method for achieving safe operation of power special mobile terminal on basis of isolation technique
A mobile terminal and safe work technology, applied in the information field, can solve problems such as sensitive information leakage, data eavesdropping, data destruction, etc., and achieve the effect of solving potential safety hazards
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Example Embodiment
[0032] The specific implementation manners of the present invention will be further described in detail below in conjunction with the accompanying drawings.
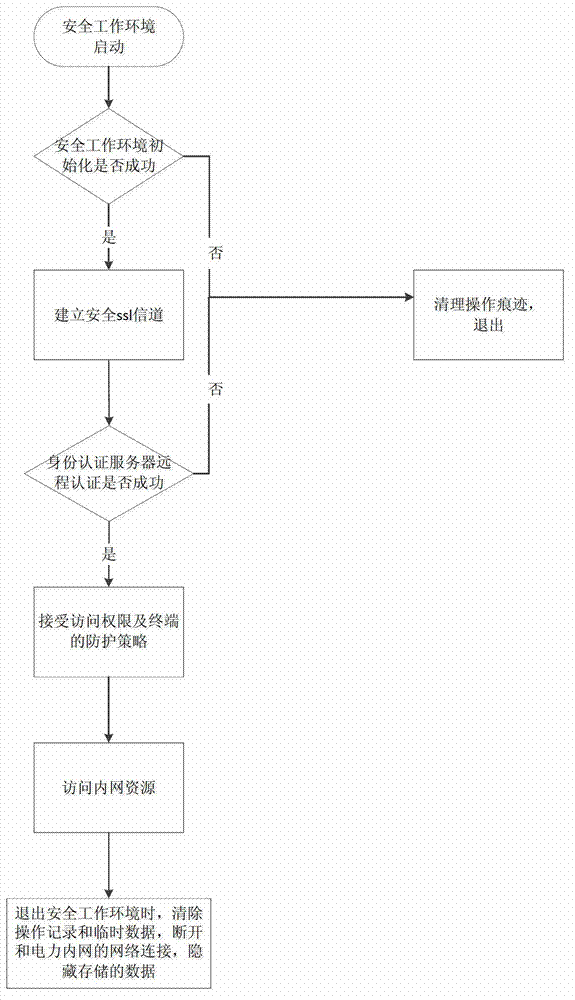
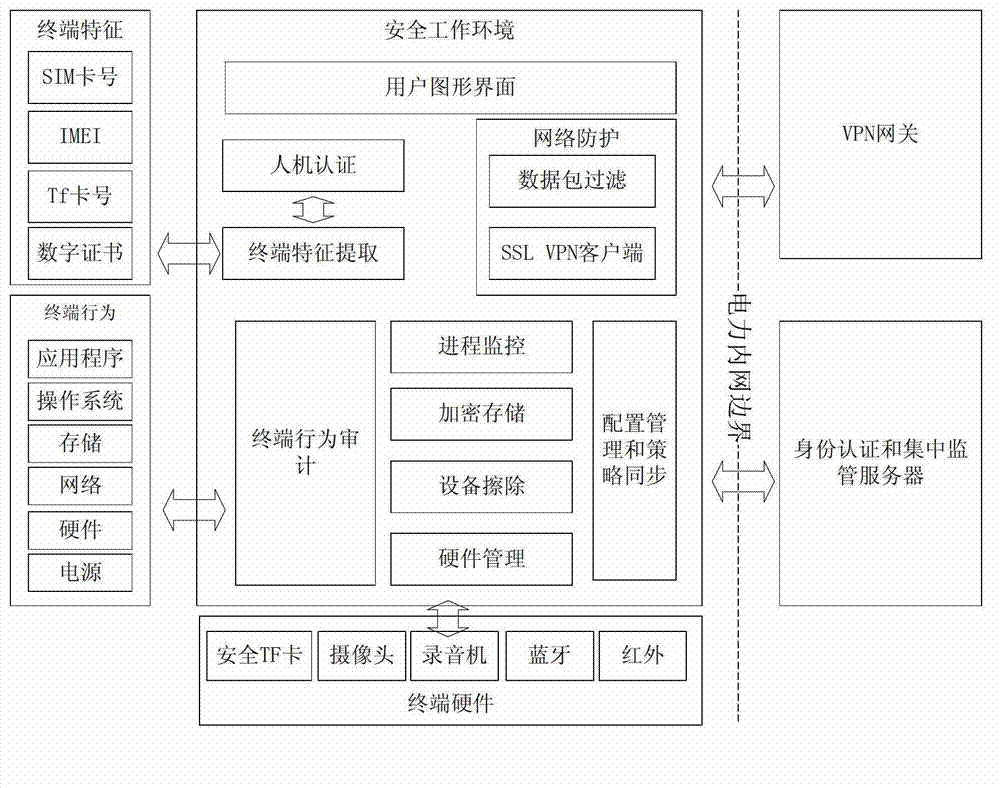
[0033] The implementation method of the safe work of the electric power dedicated mobile terminal based on the isolation technology proposed in this embodiment, its process is as follows figure 1 shown, including the following steps:
[0034] (1) Initialize the safe working environment, carry out local authentication, and check whether the mobile terminal meets the requirements for establishing a safe working environment, including whether it has a power-specific safe TF card and SIM card;
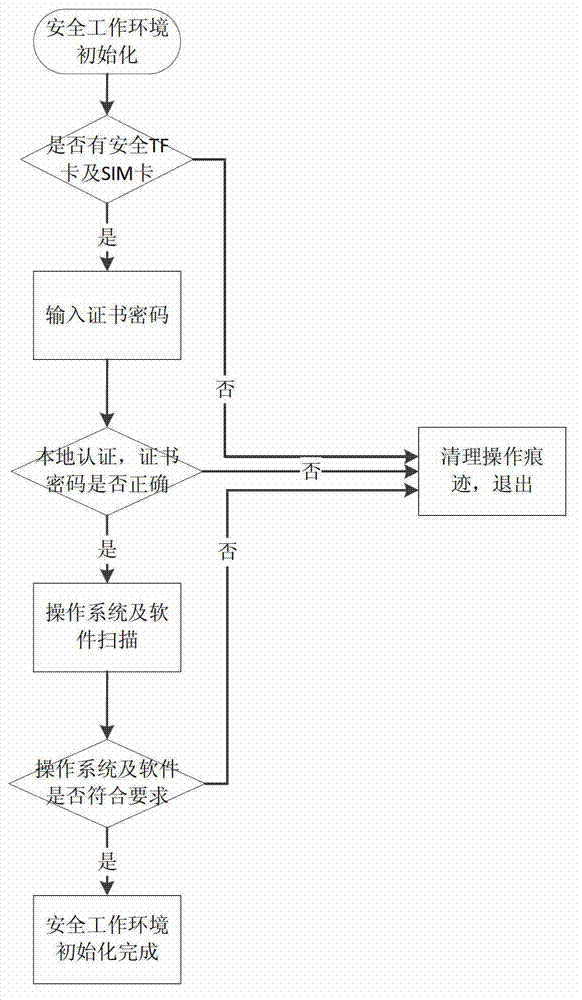
[0035] The process of initializing the safe working environment is as follows: figure 2 shown, including the following steps:
[0036] 1) Scan the hardware to determine whether there is a secure TF card and SIM card, if yes, go to step 2), otherwise exit the initialization process of the safe working environment and clean up the o...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap