Credible authentication system between ground network operation control center and satellite under environment of interconnection of mobile grids
A network operation and control center technology, applied in wireless communications, electrical components, security devices, etc., can solve problems such as lack of trusted authentication systems, and achieve the effect of resisting denial of service attacks, reducing resource consumption, and reducing the amount of calculation.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0017] The present invention will be further described below in conjunction with the accompanying drawings and embodiments.
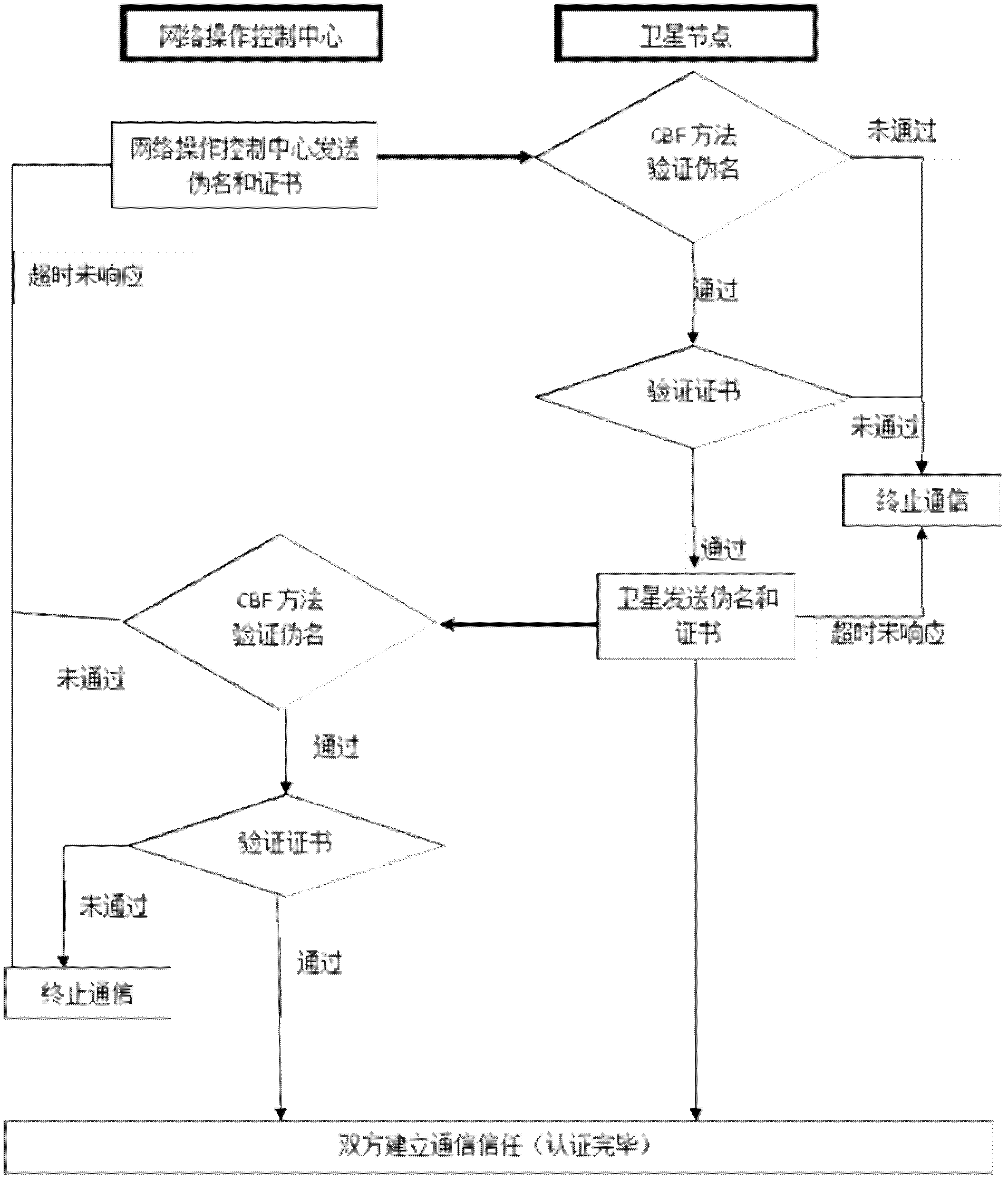
[0018] Such as figure 1 As shown, the security authentication between the network operation control center and the satellite is mainly divided into three steps, and the specific description is as follows:
[0019] Step 1: The party that needs to initiate communication, since the communication process is equivalent and can be exchanged, assuming that the network operation control center initiates communication, the network operation control center will send the pseudonym and certificate of the machine to the satellite for authentication;
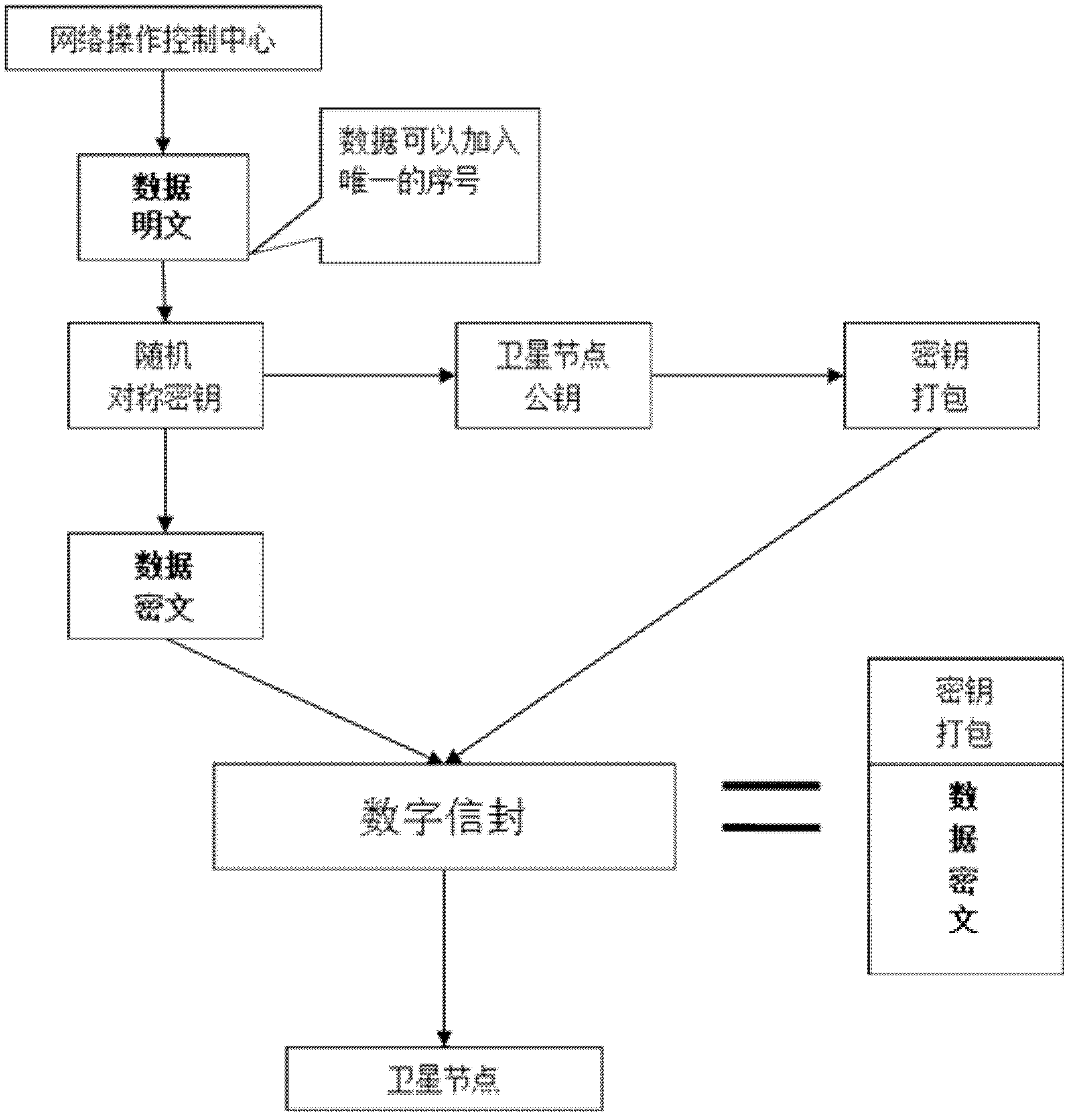
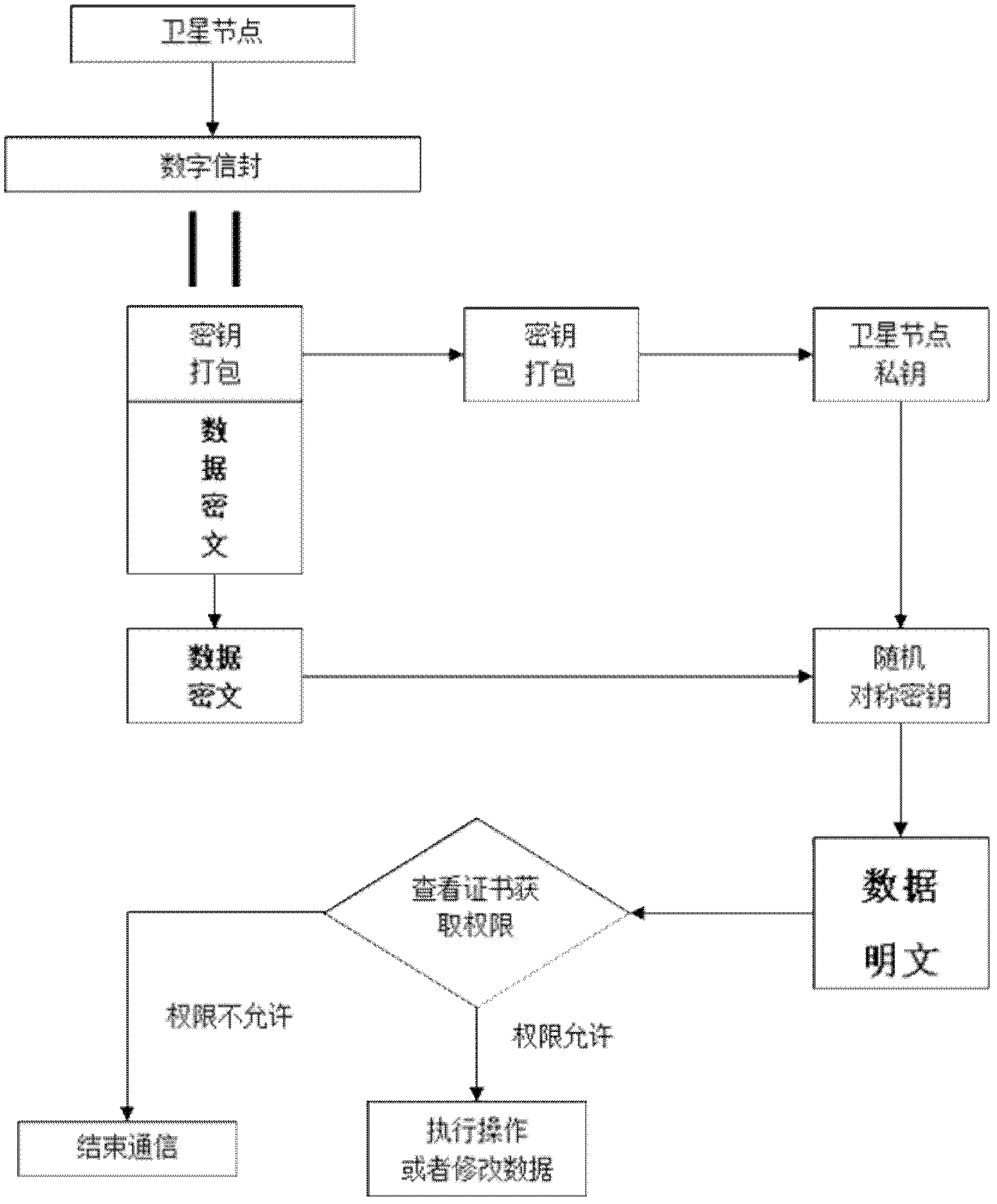
[0020] Step 2: After receiving the message, the satellite first calculates the Compressed Bloom Filters value of the sender's pseudonym, and conducts preliminary authentication to check whether the sender is trustworthy. If the pseudonym verification fails, the authentication fails and ends. Communication, if the auth...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com