A detection method and system for a heap controllable allocation vulnerability
A detection method and vulnerability technology, which is applied in the field of detection of heap controllable allocation vulnerabilities, can solve security risks, heap buffer overflow and other problems, and achieve the effect of improving correctness and comprehensiveness
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0020] The present invention will be described in detail below in conjunction with specific embodiments and drawings, but the present invention is not limited thereto.
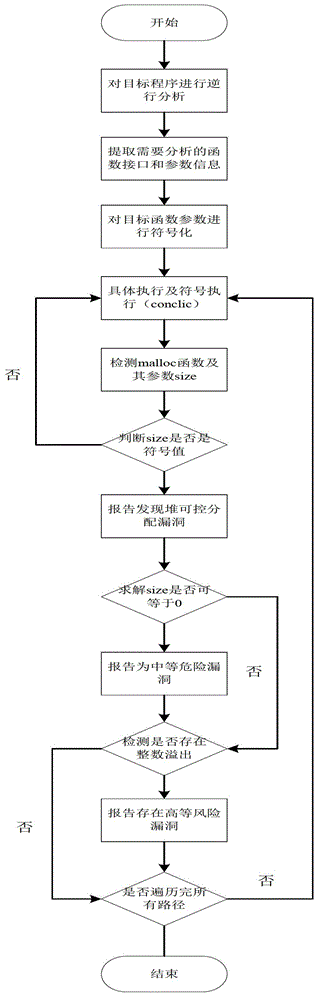
[0021] Such as figure 1 As shown, the method for detecting the controllable heap allocation vulnerability that the present invention will propose includes the following steps:
[0022] 1. Reverse engineer the target analysis file to obtain the function and parameter information that needs to be analyzed;
[0023] 2. Symbolize the parameters of the function to be analyzed,
[0024] 3. Use the symbolic execution engine based on virtual machine technology to analyze the combination of specific execution and symbolic execution of the target program, so that all paths can be traversed.
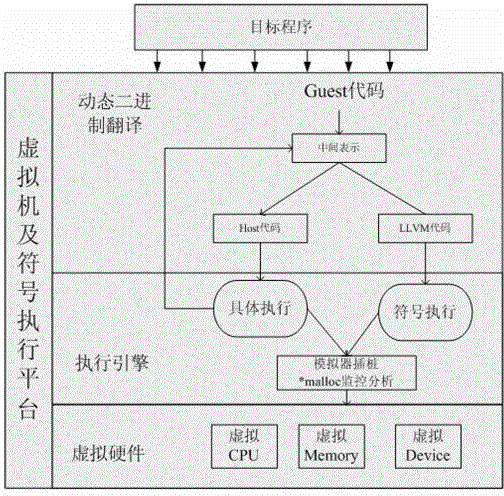
[0025] 4. Use binary translation technology to monitor and analyze the *malloc function (the function that implements heap allocation, such as kmalloc in the Linux kernel).
[0026] 5. When the target program executes to the mon...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com