Encryption Method of Chaotic Parallel Data Based on Virtual Computing and Data Optimization
An encryption method and data optimization technology, applied in digital transmission systems, electrical components, transmission systems, etc., can solve problems such as inability to perform encryption processing and ineffective use of physical computing cores
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0033] The embodiments of the present invention will be described in further detail below with reference to the accompanying drawings and examples. The following examples are intended to illustrate the present invention, but not to limit the scope of the present invention.
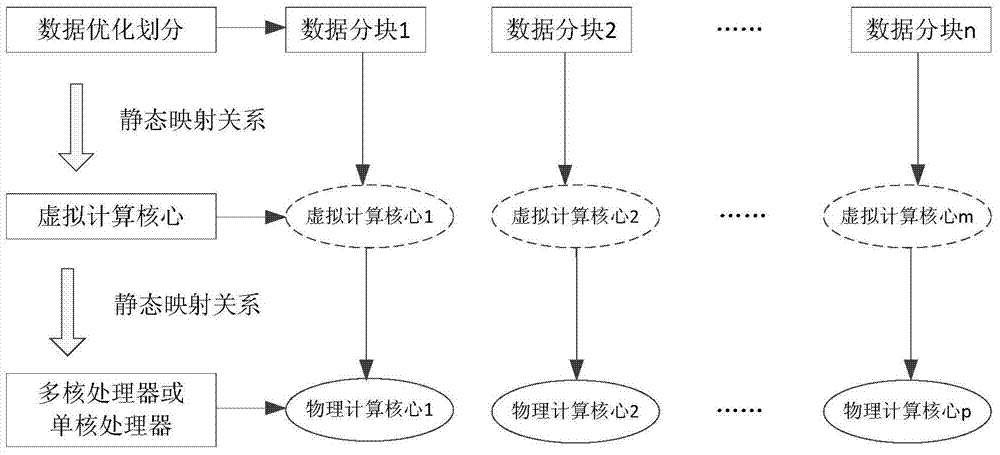
[0034] In parallel computing, if the amount of data processed is small, the parallel computing cost after data division is either equal to the serial computing efficiency of a single processor, or lower than the serial processing efficiency. Therefore, how to perform parallel data division for different data is also an urgent problem to be solved in parallel computing.
[0035] see figure 1 , an embodiment of the present invention proposes an encryption method for chaotic parallel data based on virtual computing and data optimization, including:
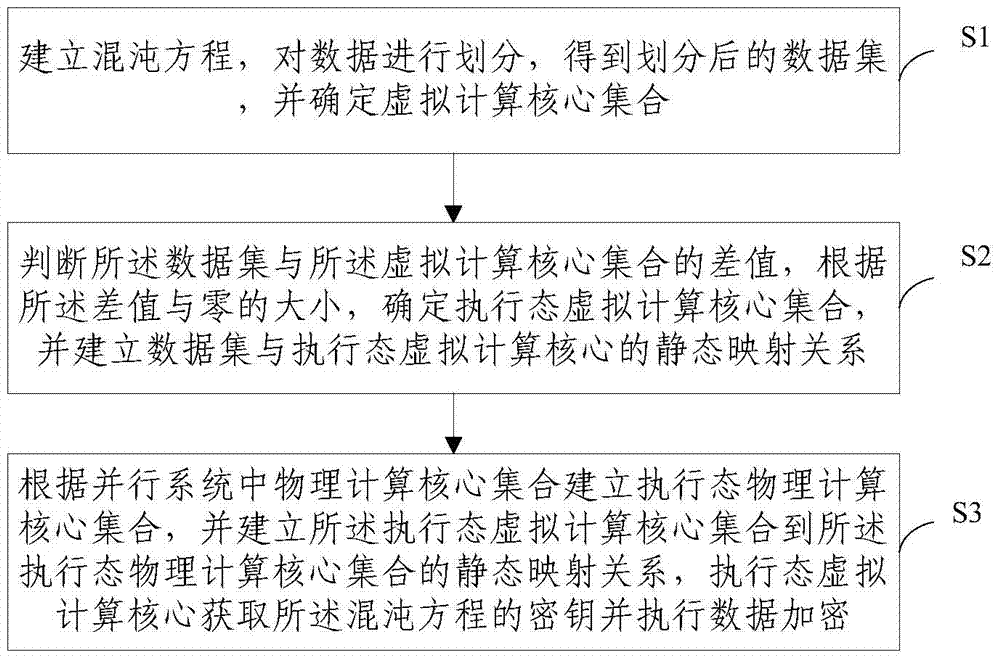
[0036] S1, establish a chaos equation, divide the data, obtain the divided data set, and determine the virtual computing core set;
[0037] S2. Determine the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com