UEFI (Unified Extensible Firmware Interface)-based identity label generation system and UEFI-based identity label generation method
A technology for generating systems and identity marks, applied in the field of computer security, to achieve the effect of not being easy to tamper with and delete
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0023] The present invention will be described in detail below with reference to the accompanying drawings and examples.
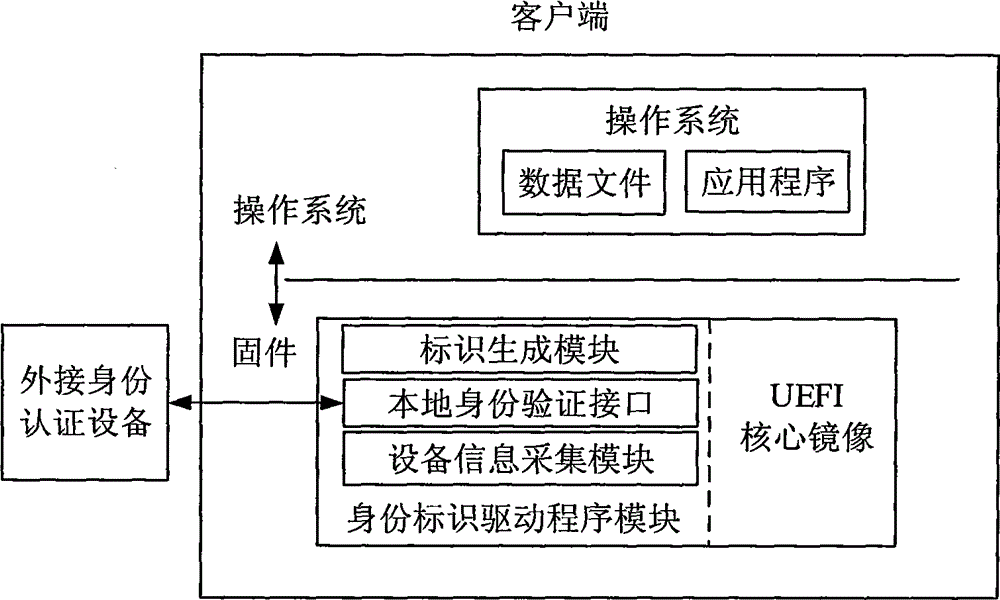
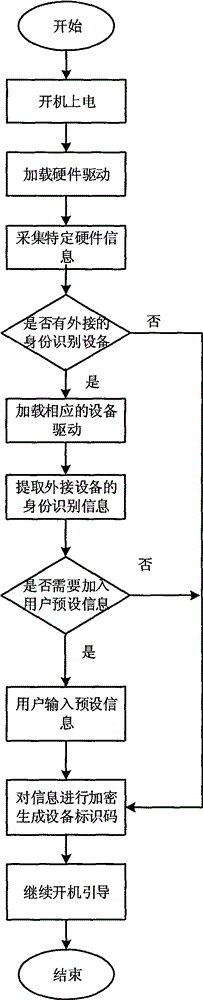
[0024] as attached figure 1 As shown, the present invention provides a UEFI-based identity generation system, the system includes a device information collection module, a local identity verification interface, and a logo generation module; wherein, the device information collection module is used to collect hardware information of the device , the local identity verification interface is used to access external identity verification devices, such as U-key, IC card, etc.; the identification generation module can combine local device information and external device information to generate a unique device identification code.
[0025] Before the application of the present invention, it needs to be deployed on the computer terminal first, and the methods that can be selected include:
[0026] a) Add the driver module to the UEFI core image.
[0027] b) Moun...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com