Method, device, client and equipment for defending against distributed denial-of-service attacks
A distributed rejection and client-side technology, applied in the field of network security, can solve the problems of mistakenly discarding regular messages and the complexity of DDOS attack defense methods
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
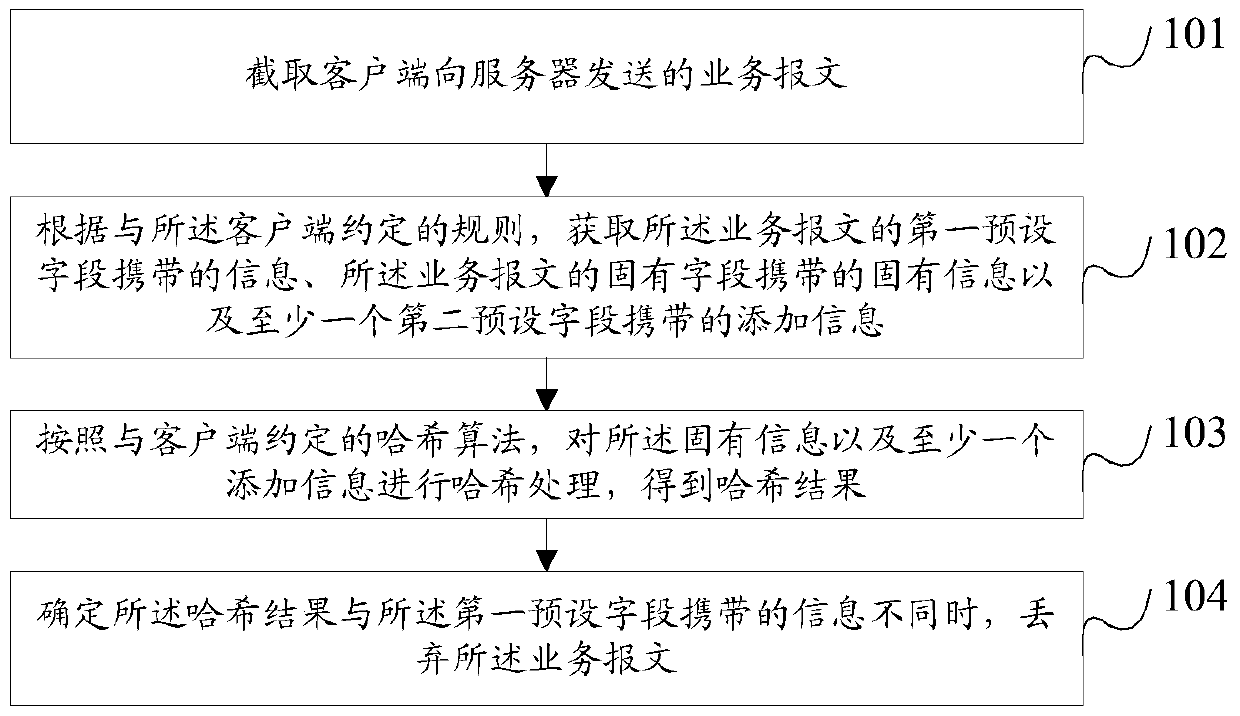
[0157] Embodiments of the present invention provide a method for defending against distributed denial of service attacks, such as figure 1 shown, including:
[0158] Step 101, intercepting the service message sent by the client to the server.
[0159] Specifically, the device (defense device) for defending against DDOS attacks intercepts the service message sent by the client to the server, and the service message sent by the client is TCP (Transmission Control Protocol, Transmission Control Protocol) or UDP (User Datagram Protocol, user data message protocol) format, including: TCP request message, UDP request message and other messages for communicating with the server.
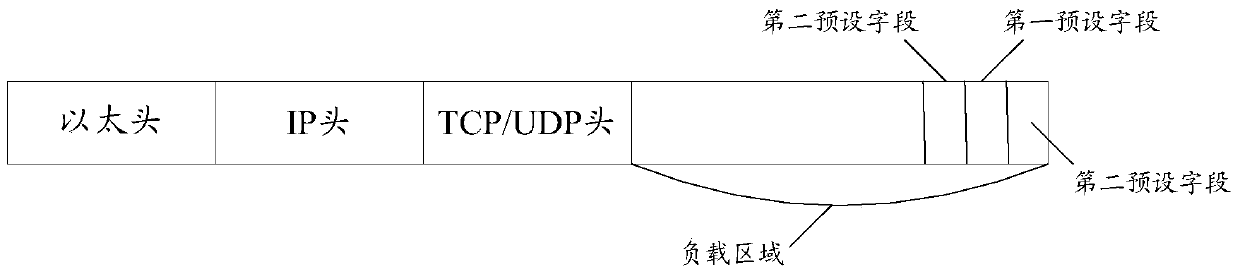
[0160] Step 102, according to the rules agreed with the client, obtain the information carried in the first preset field of the service message, the inherent information carried in the inherent field of the service message, and at least one second preset field carried to add information.
[0161] Among t...
Embodiment 2
[0190] figure 1 The provided embodiment is based on the description of the method for defending against distributed denial-of-service attacks provided by the embodiments of the present invention based on the defense device side. The method for defending against distributed denial-of-service attacks provided by the embodiments of the present invention will be described in detail below based on the client side.
[0191] and figure 1 Corresponding to the provided embodiments, the embodiments of the present invention also provide a method for defending against distributed denial of service, such as Figure 5 shown, including:
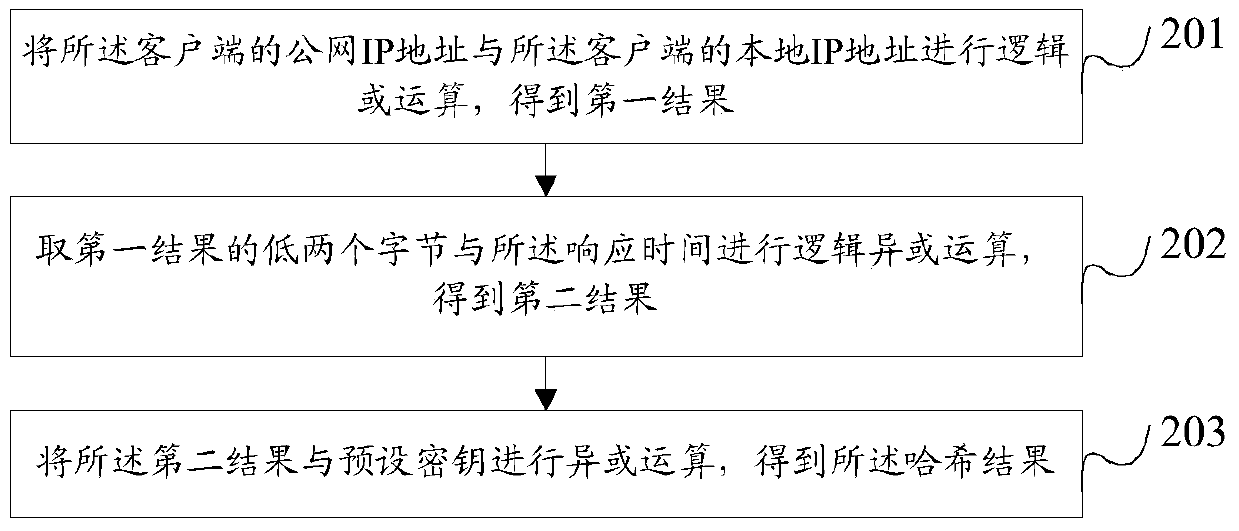
[0192] Step 401: Perform hash processing on the information carried in the inherent fields of the service message and at least one piece of added information according to the hash algorithm agreed with the defense device to obtain a hash result.
[0193] Step 402: Edit the hash result into the first preset field of the service message according to the rul...
Embodiment 3
[0207] because Figure 5 The service message in the provided embodiment carries the response time of the last response message returned by the server to the client, but in the prior art, when the server returns the response message to the client, it does not carry the response message in the response message. The response time, therefore, the embodiment of the present invention also provides a method for defending against distributed denial of service attacks, such as Figure 7 shown, including:
[0208] Step 601, when the server receives the service message sent by the client, it extracts the local time.
[0209] The local time is: the difference between the number of seconds corresponding to the moment when the server returns the response message and the standard time. The local time in step 601 is the response time of the response packet returned by the server to the client mentioned in the above embodiment.
[0210] Step 602: Carry the local time in a preset field of a ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com