Bluetooth device safe login identity authentication method and device
An authentication method and secure login technology, applied in the field of secure login authentication of Bluetooth devices, can solve the problems of complex information encryption and decryption processing, cracking or interception, and high cost, and achieve the problem of not easy to crack, improve security, and increase cracking. effect of difficulty
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Example Embodiment
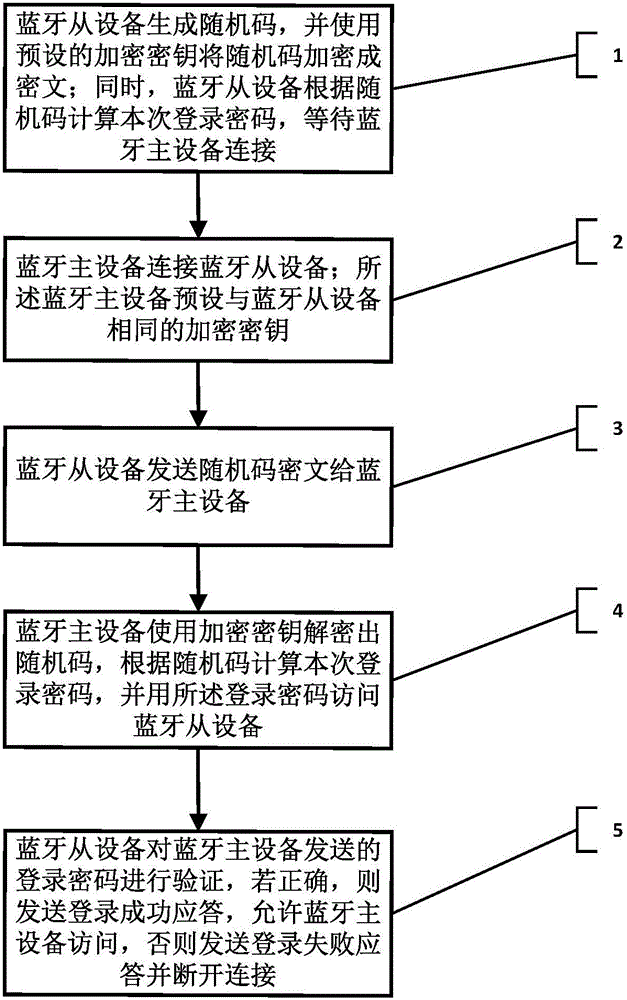
[0033] The technical solutions in the embodiments of the present invention will be clearly and completely described below with reference to the accompanying drawings in the embodiments of the present invention. Obviously, the described embodiments are only a part of the embodiments of the present invention, but not all of the embodiments. Based on the embodiments of the present invention, all other embodiments obtained by those of ordinary skill in the art without creative efforts shall fall within the protection scope of the present invention.
[0034] Bluetooth (Bluetooth): is a wireless technology standard that enables short-range data exchange between fixed devices, mobile devices, and building personal area networks. Bluetooth technology stipulates that when Bluetooth communication is performed between each pair of devices, one must be the master device and the other must be the slave device to communicate. During communication, the master device must search and initiate l...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap