Ownership authentication and key transmission method without losing entropy in ciphertext duplication elimination scene
A technology of ownership authentication and key, which is applied in the field of information security, can solve the problems that the ownership authentication of all file data cannot be guaranteed, the convergent encryption method cannot guarantee semantic security, and there is no secure key transmission method, so as to achieve semantic security and prevent The effect of privacy leakage and security guarantee
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Example Embodiment
[0032] The following describes the present invention in further detail with reference to the drawings and specific embodiments:
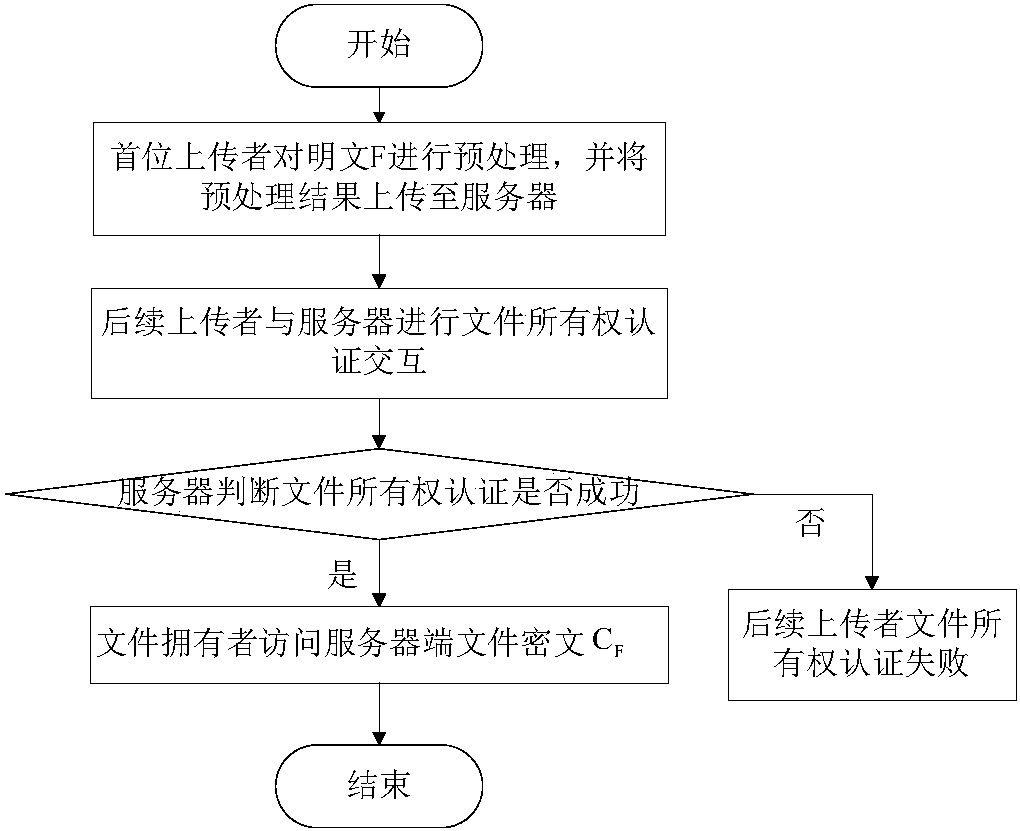
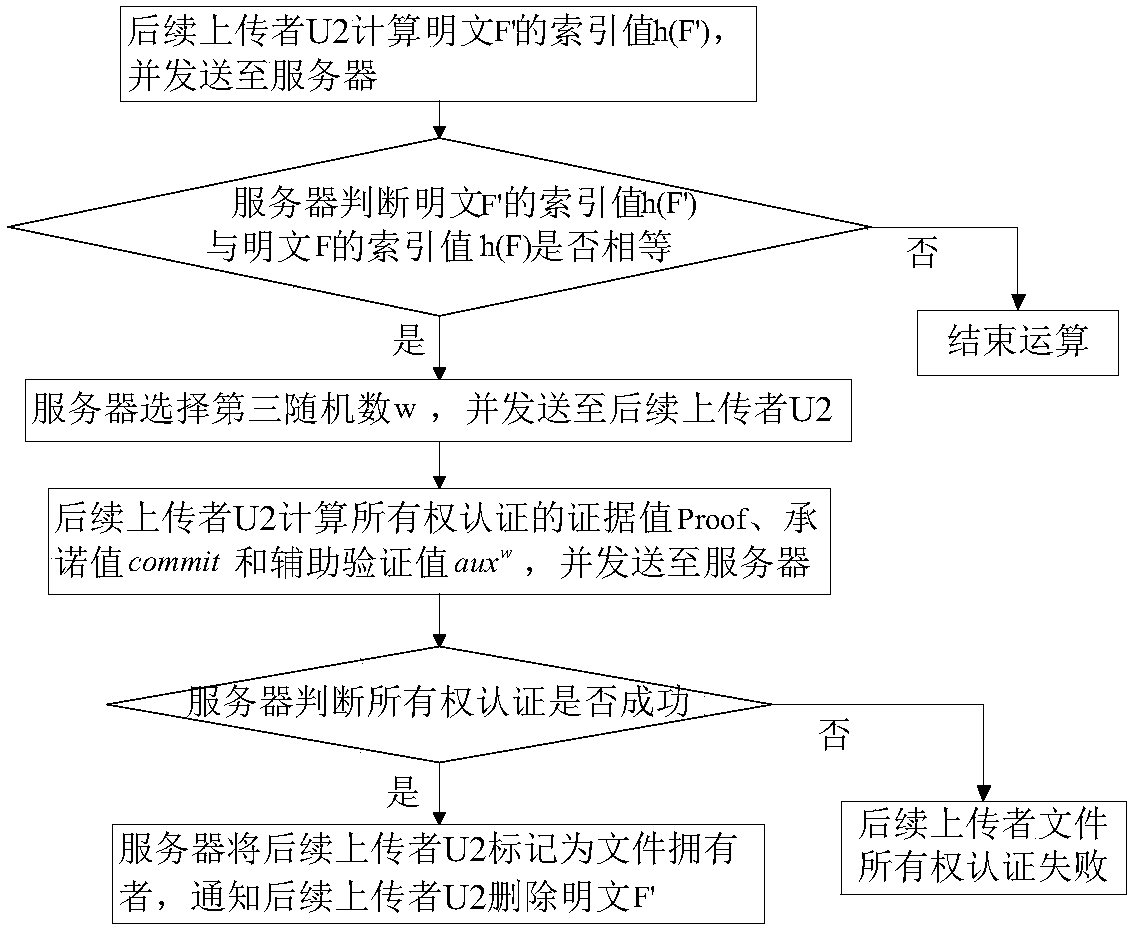
[0033] Reference figure 1 , A method of ownership authentication and key transfer without loss of entropy in ciphertext deduplication scenarios, including the following steps:
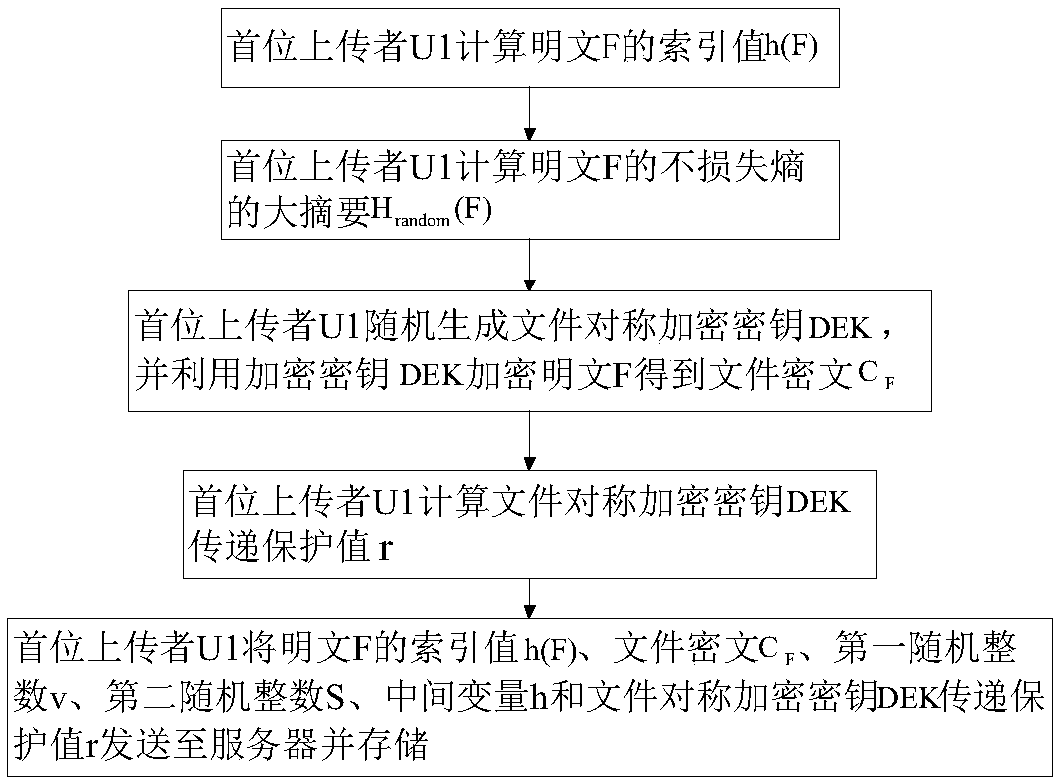
[0034] Step 1. U1, the first uploader of the file, preprocesses the plaintext F and uploads the preprocessing result to the server. The implementation steps are as follows figure 2 Shown:
[0035] Step 1a) The first uploader U1 uses the md5 hash function to calculate the index value of the plaintext F h(F)=md5(F);
[0036] Step 1b) The first uploader U1 uses the independent pairwise hash method to calculate the large file digest H of the plaintext F without loss of entropy random (F):
[0037] Step 1b1) The first uploader U1 divides the plaintext F into blocks, and obtains the plaintext F={w 1 ,w 2 ,...,W i ,...,W l }, where w i Represents the plaintext F={w 1 ,w 2 ,...,W i ,...,W l...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap