Data flow monitoring method and apparatus
A monitoring device and data flow technology, applied in the field of communication security, can solve problems such as low detection efficiency, and achieve the effects of improving monitoring efficiency and solving low monitoring efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
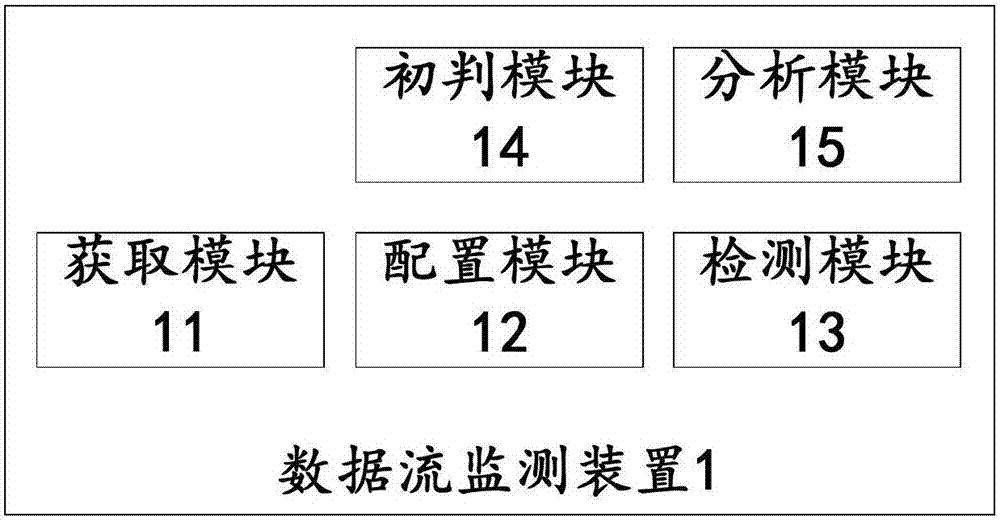
[0031] figure 1 It is a schematic structural diagram of the data flow monitoring device provided in the first embodiment of the present invention, which is represented by figure 1 It can be seen that, in this embodiment, the data flow monitoring device 1 provided by the present invention includes:
[0032] Obtaining module 11, configured to obtain the source identification of the access data flow
[0033] The configuration module 12 is configured to configure the security attributes of the access data flow according to the preset white list and source identification, and the security attributes include white flow, gray flow, and black flow;
[0034] The monitoring module 13 is configured to divide the access data flow according to the security attribute of the access data flow.
[0035] In some embodiments, such as figure 1 As shown, the data flow monitoring device 1 in the above-mentioned embodiment also includes a preliminary judgment module 14, which is used for making a...
no. 2 example
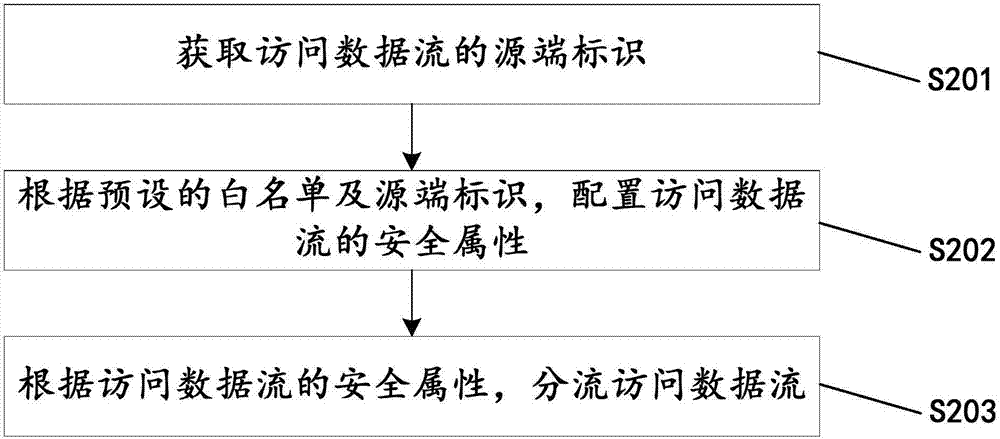
[0042] figure 2 It is a flow chart of the data flow monitoring method provided by the second embodiment of the present invention, consisting of figure 2 It can be seen that, in this embodiment, the data flow monitoring method provided by the present invention includes the following steps:
[0043] S201: Obtain the source identification of the access data flow;
[0044] S202: According to the preset white list and source identification, configure the security attributes of the access data flow, and obtain the security attributes of the access data flow, the security attributes include white flow, gray flow, and black flow;
[0045] S203: Distribute the access data flow according to the security attribute of the access data flow.
[0046] In some embodiments, the method in the above embodiment further includes: making a preliminary judgment on the access data flow, judging whether it is an offensive data flow, and outputting the preliminary judgment result; List, set securi...
no. 3 example
[0052] The present invention will be further explained in combination with specific application scenarios.
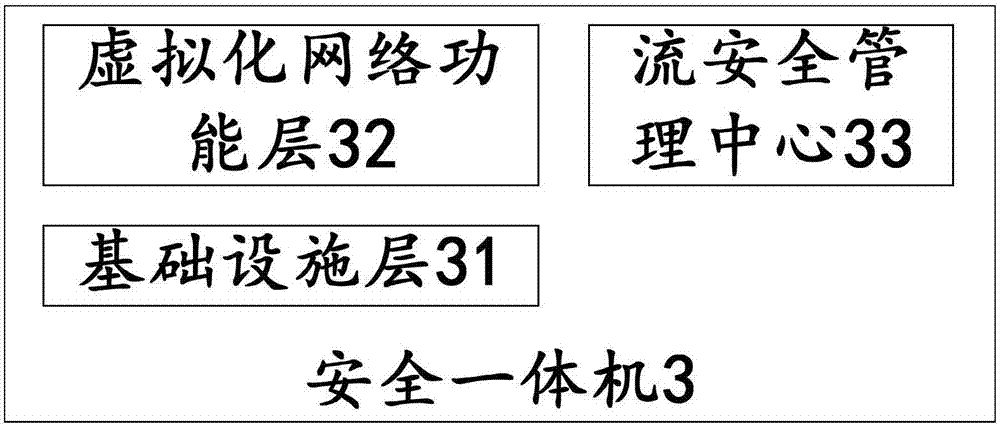
[0053] In view of the relatively low efficiency and high complexity of the network security system existing in the deployment mode of most existing network security devices, in order to improve the detection accuracy of the access data flow and reduce the complexity of deploying the network security system in this embodiment, This embodiment provides an all-in-one security machine oriented to network function virtualization, and each functional module of the all-in-one security machine cooperates to realize the functions of the data stream management device in the first embodiment.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com