A method for transmitting keys, a receiving terminal and a distributing terminal
A technology for receiving terminals and transmitting keys, which is applied in the field of data processing, and can solve problems such as a large amount of manpower, MK key security threats, and high operation and maintenance costs, so as to ensure security and reliability, simplify the transmission process, and avoid malicious The effect of the code
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
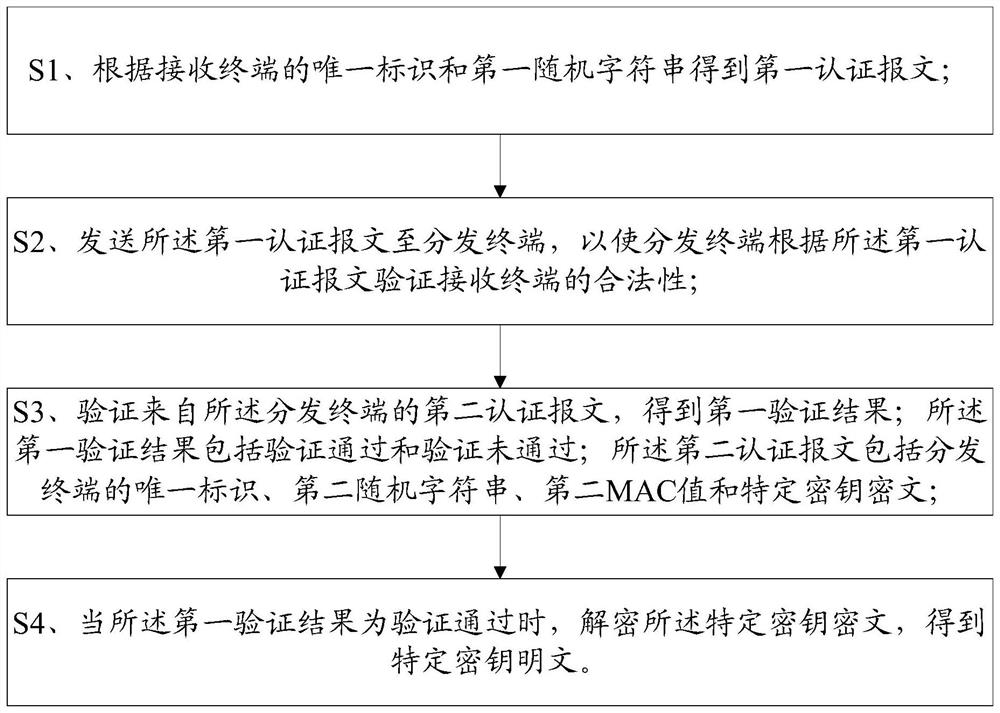
[0117] This embodiment provides a method for transmitting a key, including:
[0118] S1. The receiving terminal generates a transmission authentication key and a transmission encryption key; the transmission authentication key is unique; the transmission encryption key is unique;
[0119] The receiving terminal sends the transmission authentication key and the transmission encryption key to the transmission key management terminal, so that the transmission key management terminal synchronizes the transmission authentication key and the transmission encryption key to the distribution terminal;
[0120] The distribution terminal obtains the transmission authentication key corresponding to more than one receiving terminal from the transmission key management terminal, and obtains a transmission authentication key set; each transmission authentication key in the transmission authentication key set is unique; the distribution terminal obtains the transmission authentication key set ...
Embodiment 2
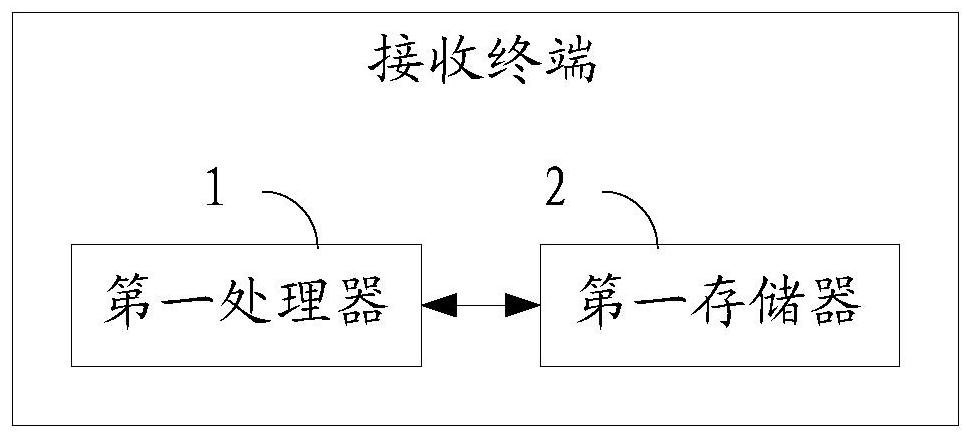
[0171] This embodiment provides a receiving terminal, including one or more first processors 1 and a first memory 2, the first memory 2 stores a program, and is configured to be controlled by the one or more first processors 1Perform the following steps:
[0172] S1. Generate a transmission authentication key and a transmission encryption key; the transmission authentication key is unique; the transmission encryption key is unique;
[0173] Sending the transmission authentication key and the transmission encryption key to the transmission key management terminal, so that the transmission key management terminal synchronizes the transmission authentication key and the transmission encryption key to the distribution terminal.
[0174] S2. Obtain the first authentication message according to the unique identifier of the receiving terminal and the first random character string; specifically:
[0175] Randomly generate a string of more than 16 bytes to obtain the first random stri...
Embodiment 3
[0187] Embodiment three provided by the present invention is:
[0188] This embodiment provides a method for transmitting a key, including:
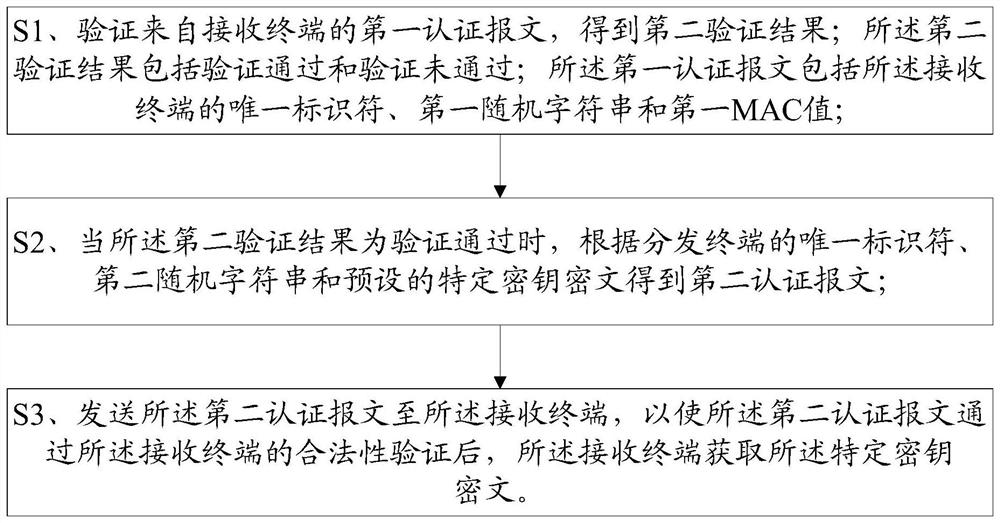
[0189] S1. Obtain transmission authentication keys corresponding to more than one receiving terminal from the transmission key management terminal, and obtain a transmission authentication key set; each transmission authentication key in the transmission authentication key set is unique;
[0190] The transmission encryption key corresponding to more than one distribution terminal is obtained from the transmission key management terminal to obtain a transmission encryption key set; each transmission encryption key in the transmission encryption key set is unique.
[0191] S2. Verify the first authentication message from the receiving terminal to obtain a second verification result; the second verification result includes verification passed and verification failed; the first authentication message includes the unique identifier of the rec...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com