Log encryption method and device and log decryption method and device
An encryption method and log technology, which are applied to secure communication devices, computer security devices, and key distribution, can solve the problems of low security of log encryption methods, and achieve the effects of improving the difficulty of cracking, solving low security, and improving security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Example Embodiment
[0024] Example one
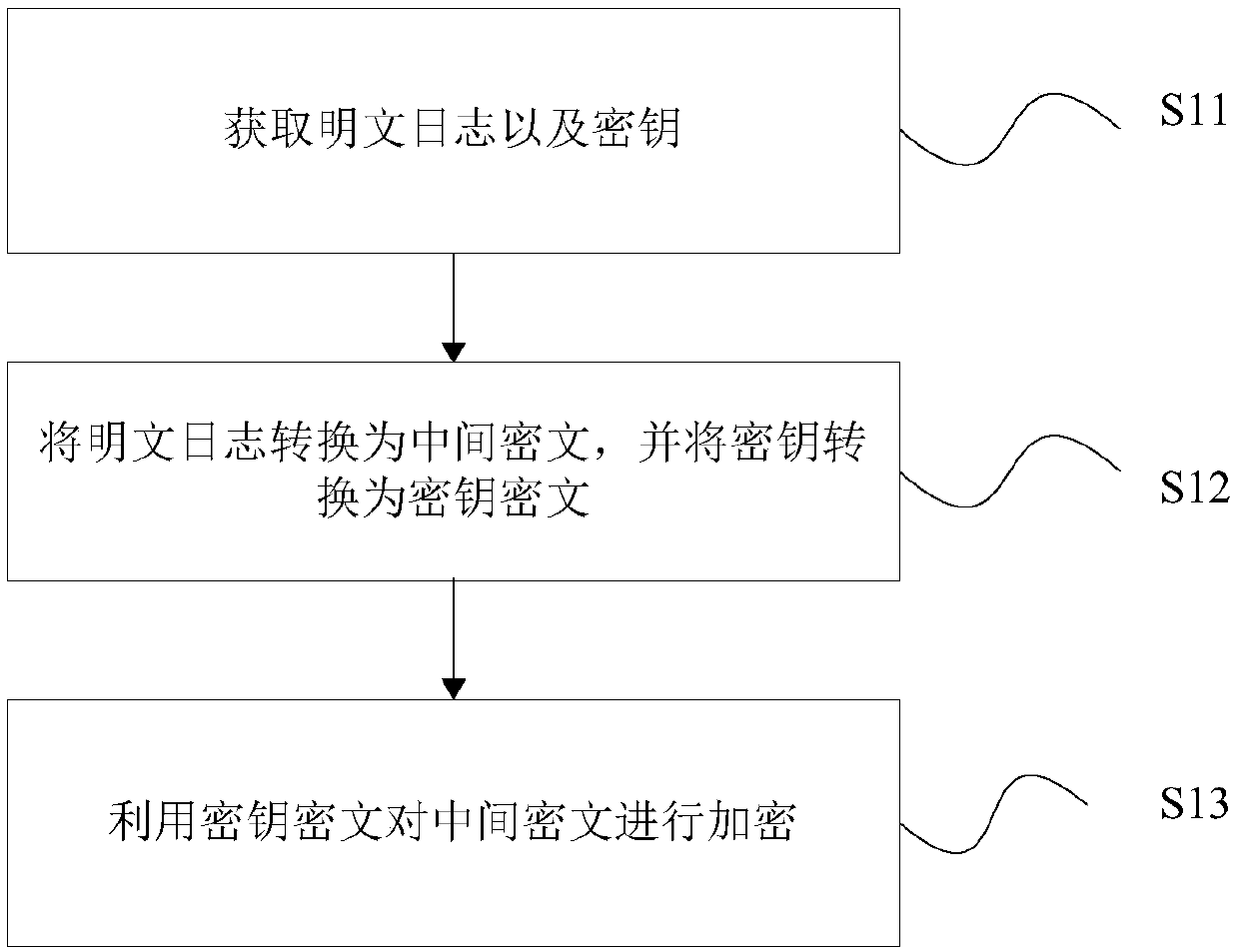
[0025] According to an embodiment of the present invention, a log encryption method is provided, such as figure 1 As shown, the method includes:
[0026] Step S11, obtain the plaintext log and the key;
[0027] Specifically, the plaintext log may be obtained from the PC terminal, or may be obtained from the mobile terminal. The key can be static or dynamically configured. When the key is dynamically configured, different levels of keys can be determined according to different confidential levels. The key can be stored in local storage or external storage.
[0028] Step S12, converting the plaintext log into an intermediate ciphertext, and converting the key into a key ciphertext;
[0029] Specifically, the plaintext log is converted into the intermediate ciphertext, and the key is converted into the key ciphertext. Through the above conversion, the first encryption of the data can be completed.
[0030] Step S13, encrypt the intermediate ciphertext by using the ke...
Example Embodiment
[0053] Example two
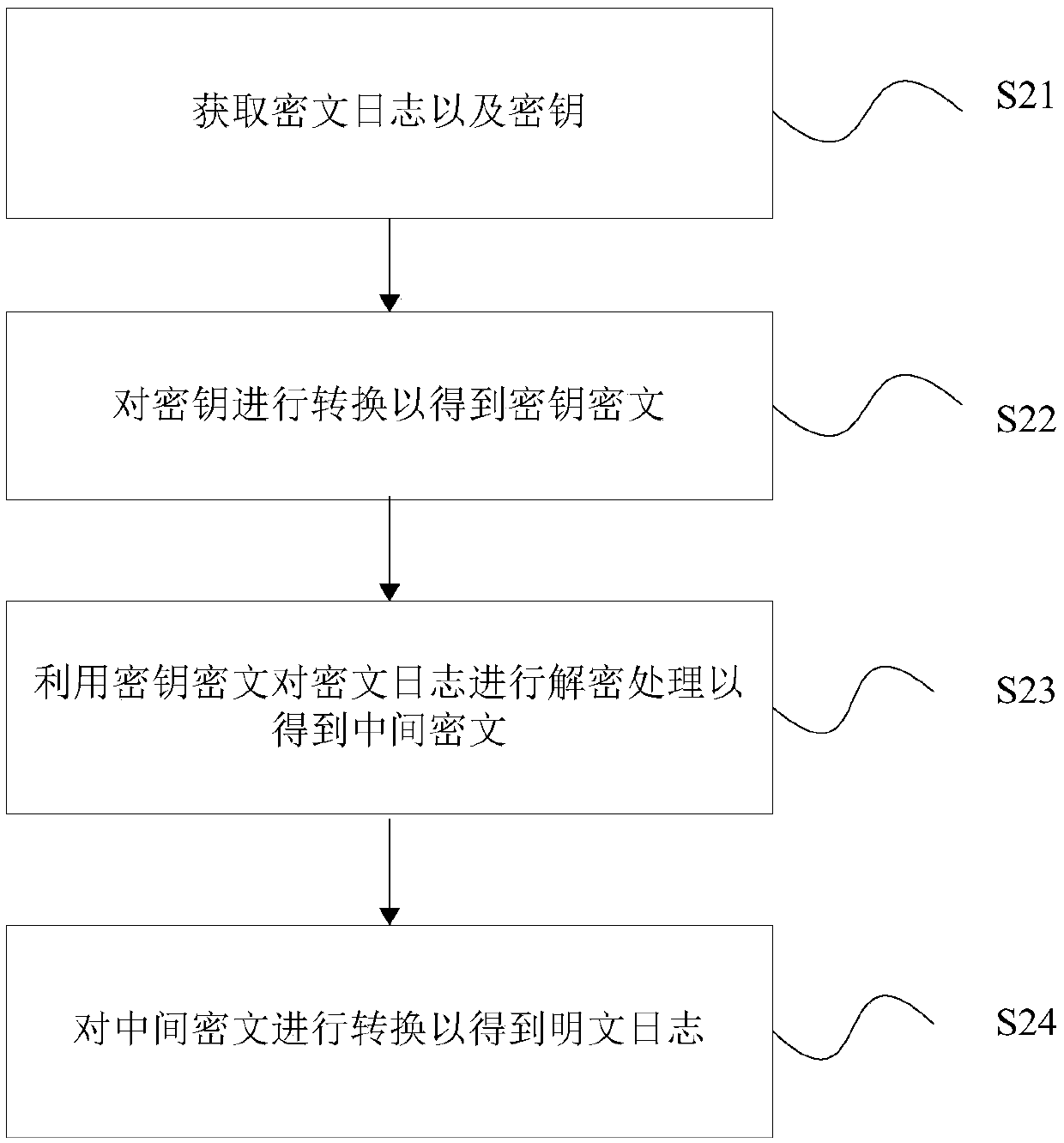
[0054] According to an embodiment of the present invention, a log decryption method is provided, such as figure 2 As shown, the method includes:
[0055] Step S21, obtain the ciphertext log and the key;
[0056] Specifically, the encrypted ciphertext log may be obtained from a PC or a mobile terminal. The key can be static or dynamically configured. When the key is dynamically configured, different levels of keys can be determined according to different confidentiality levels. The key can be stored in local storage or external storage.
[0057] Step S22: Convert the key to obtain the key ciphertext;
[0058] Step S23, using the key ciphertext to decrypt the ciphertext log to obtain an intermediate ciphertext;
[0059] Specifically, the ciphertext log is decrypted for the first time through the key ciphertext to obtain the intermediate ciphertext.
[0060] Step S24: Convert the intermediate ciphertext to obtain a plaintext log.
[0061] Specifically, by converting t...
Example Embodiment
[0081] Example three
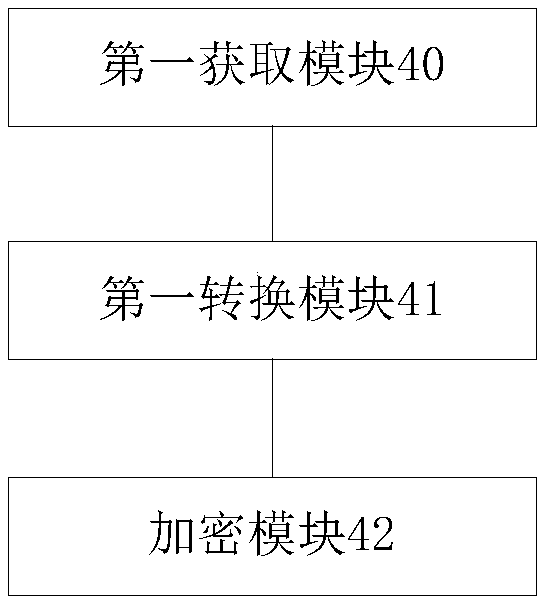
[0082] According to an embodiment of the present invention, a log encryption device is provided, such as image 3 As shown, the device includes:
[0083] The first obtaining module 40 is used to obtain the plaintext log and the key; refer to the description of step S11 for details.
[0084] The first conversion module 41 is configured to convert the plaintext log into an intermediate ciphertext, and convert the key into a key ciphertext; refer to the description of step S12 for details.
[0085] The encryption module 42 is configured to encrypt the intermediate ciphertext by using the key ciphertext. See the description of step S13 for details.
[0086] In the embodiment of the present invention, the above-mentioned first obtaining module 40 is used to obtain a plaintext log and a key; the first conversion module 41 is used to convert the plaintext log into an intermediate ciphertext and convert the key Is the key ciphertext; the encryption module 42 is used to ...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap