Method for hiding and reinforcing Android App application resources
A technology of resources and resource files, applied in the field of Android applications, can solve problems such as illegally obtaining application codes, achieve the effects of ensuring security, increasing reverse analysis costs, and ensuring the writing of specifications
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
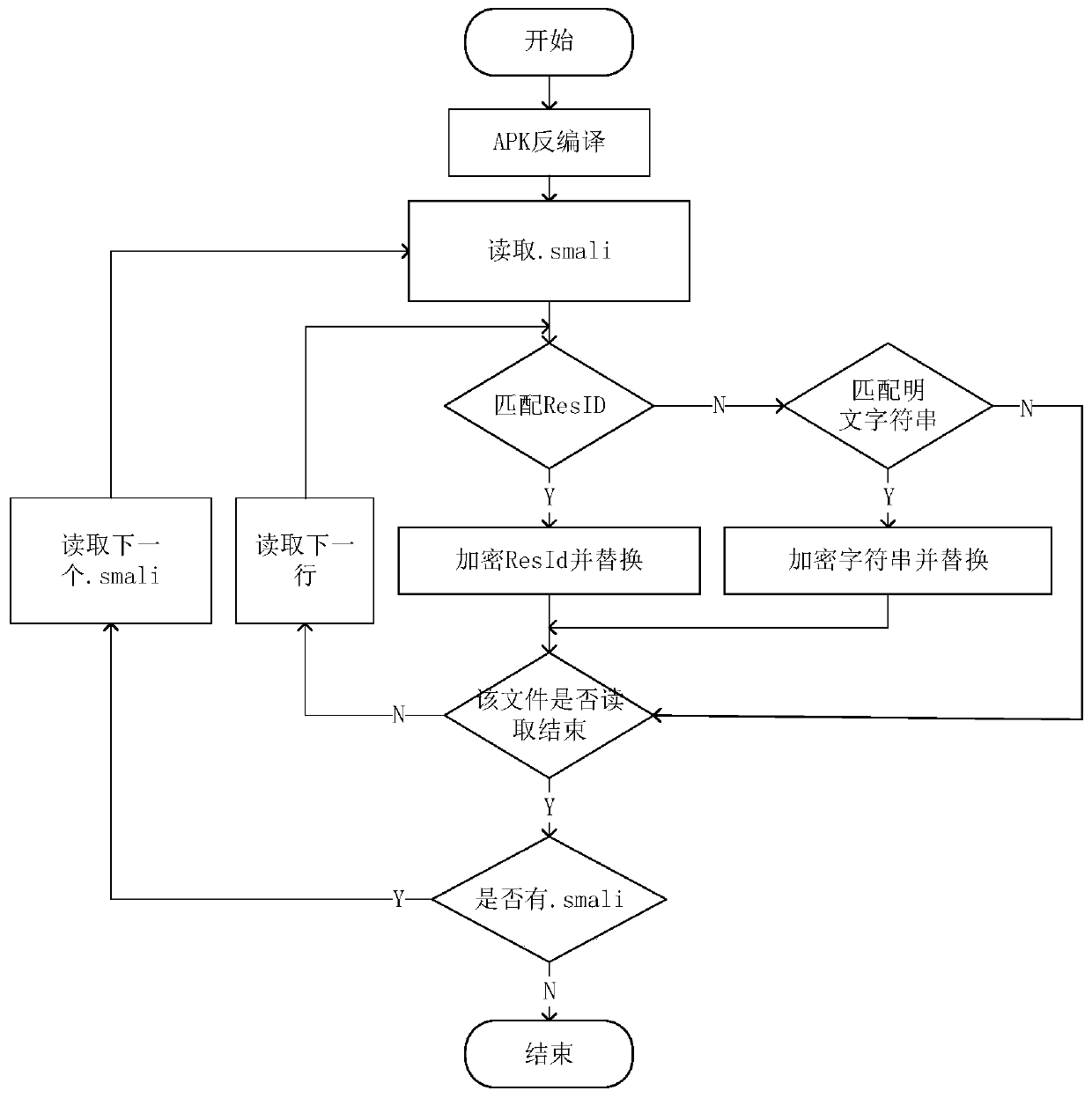
[0047] Embodiment 1, resource id encryption
[0048] Step 1. Encryption can be divided into resource id encryption and plaintext string encryption in the code.
[0049] Resource id encryption is mainly aimed at changing the process of searching for resource files through resource ids in the code. The plaintext strings in the code are mainly for strings that are directly referenced in the code without adding the string to the resource file.
[0050] Step 2. Decompile the App file and get its .smali folder.
[0051] Step 3. Use regular expressions to identify the statements in the .smali file, and replace specific codes.
[0052] 3.1) First obtain all .smali files, and then traverse each file.
[0053] 3.2) For a .smali file, read line by line, and then use regular expressions to match whether it is a resource id.
[0054] 3.3) If the match is successful, use the encryption method to generate a random key to encrypt the resource id, and use the key and the encrypted number as...
Embodiment 2
[0062] Embodiment 2, plaintext string encryption
[0063] Step 1. Encryption can be divided into resource id encryption and plaintext string encryption in the code.
[0064] Resource id encryption is mainly aimed at changing the process of searching for resource files through resource ids in the code. The plaintext strings in the code are mainly for strings that are directly referenced in the code without adding the string to the resource file.
[0065] Step 2. Decompile the App file and get its .smali folder.
[0066] Step 3. Use regular expressions to identify the statements in the .smali file, and replace specific codes.
[0067] 3.1) First obtain all .smali files, and then traverse each file.
[0068] 3.2) For a .smali file, read line by line, and then use regular expressions to match whether it is a resource id.
[0069] 3.3) Encrypt resource file id successfully, go to 3.2. If it does not match, go directly to 3.4.
[0070] 3.4) Use a regular expression to match the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com