Method and system for detecting malicious PDF documents
A malicious and document technology, applied in the field of computer communication detection, can solve problems such as difficulty in training an accurate detection model
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
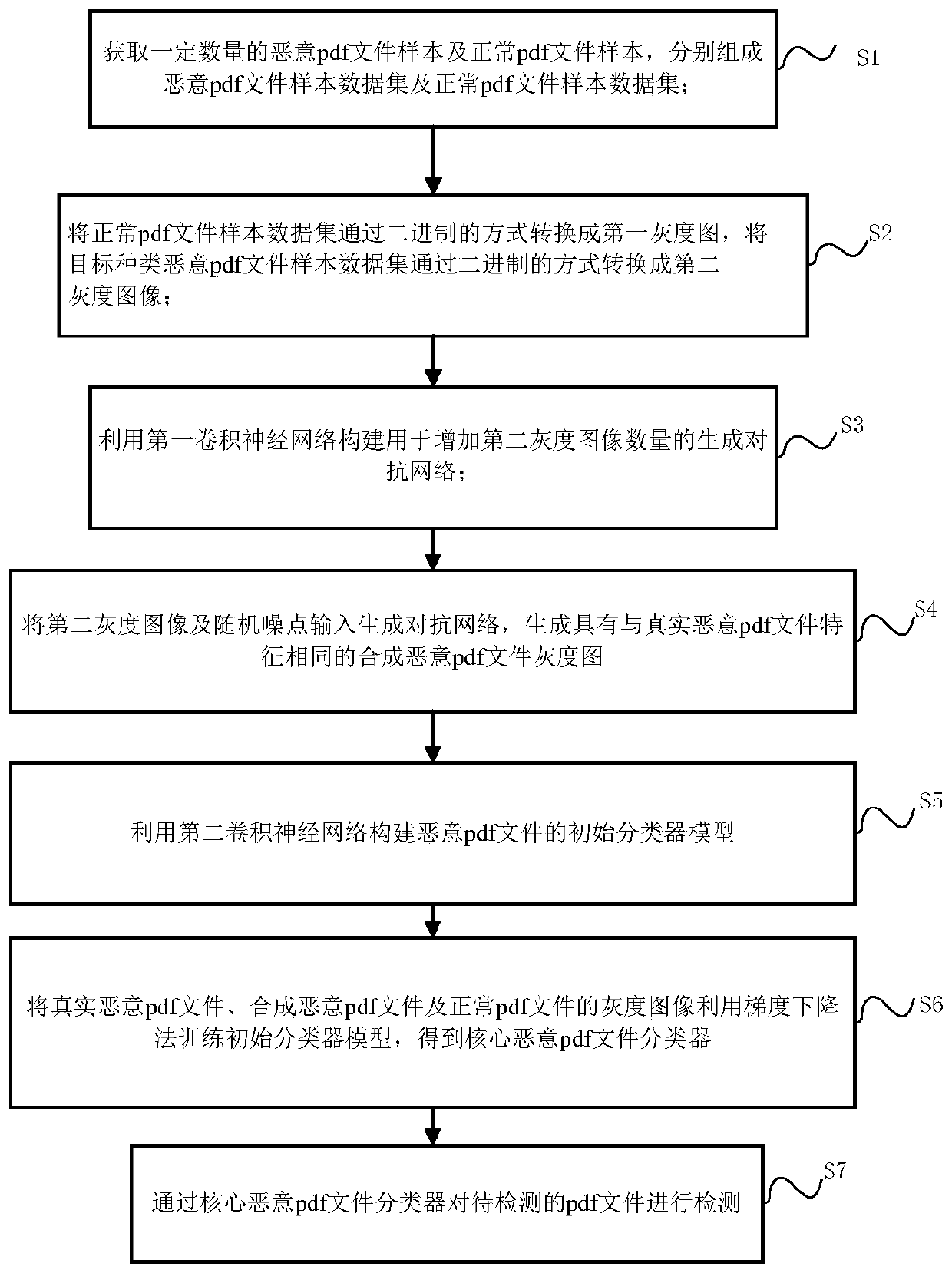
[0042] Such as figure 1 A flow chart of a method for detecting malicious PDF documents shown, the method comprising:
[0043] S1. Obtain a certain number of malicious PDF file samples and normal PDF file samples to form a malicious PDF file sample data set and a normal PDF file sample data set respectively; the number of normal PDF file samples ranges from 10,000 to 50,000, depending on the number of samples Enough, each model formed by the subsequent convolutional neural network can fully learn the features, and two endpoint values can be obtained. In this embodiment, the number of normal PDF file samples is 50000, and the number of malicious PDF file samples is normal PDF 1 / 4 of the file sample size.
[0044] S2. The normal PDF file sample data set is replaced by a first grayscale image in a binary manner; the target type malicious PDF file sample data set is converted into a second grayscale image in a binary manner;
[0045] The conversion process described is:
[0046]...
example
[0063] Practical examples of the present invention are as follows:
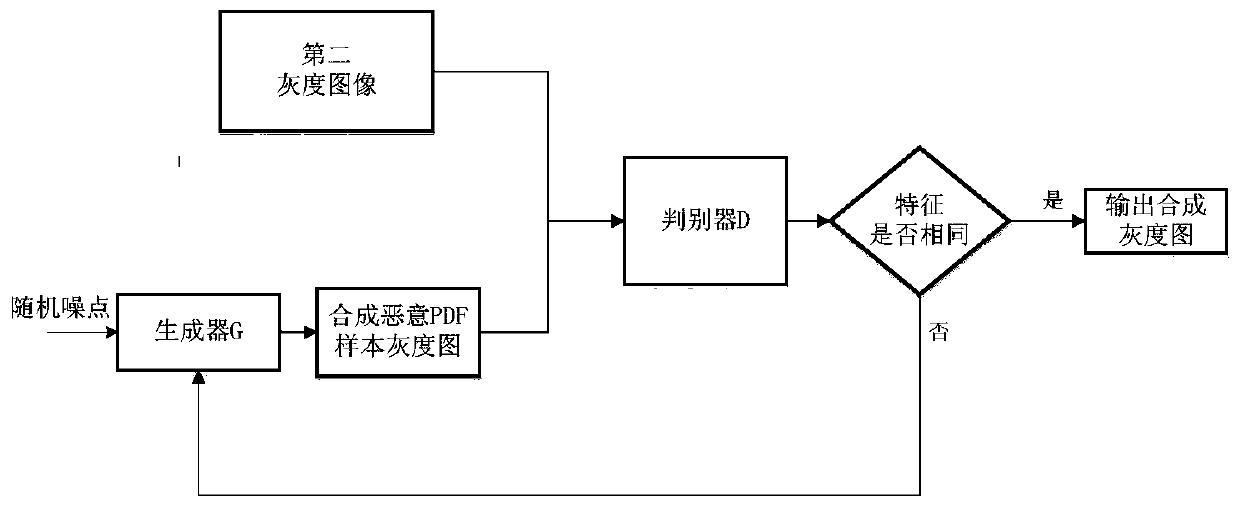
[0064] S10: Obtain a certain number of target type malicious PDF file samples and a sufficient number of normal PDF file samples respectively, as the input of the generation confrontation network used for data enhancement, and the input of the training convolutional neural network malicious file detector;
[0065] Traditional deep learning requires a large number of malicious PDF file samples and a sufficient number of normal PDF file samples, and the number of positive and negative samples must be balanced in order to achieve better results when training the initial classifier model. However, under normal circumstances, it is difficult to obtain sufficient samples of malicious PDF files, and when new types of PDF files appear, the problem of insufficient number of new malicious PDF samples will be faced.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com