Secret code printing method, tracing method and system based on black-and-white printing file
A technology for printing documents and passwords, applied in the field of forensic identification or criminal science, it can solve the problems of poor accuracy and unsatisfactory inspection effect of the printing document formation time, and achieve the effect of improving accuracy and convenient use.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
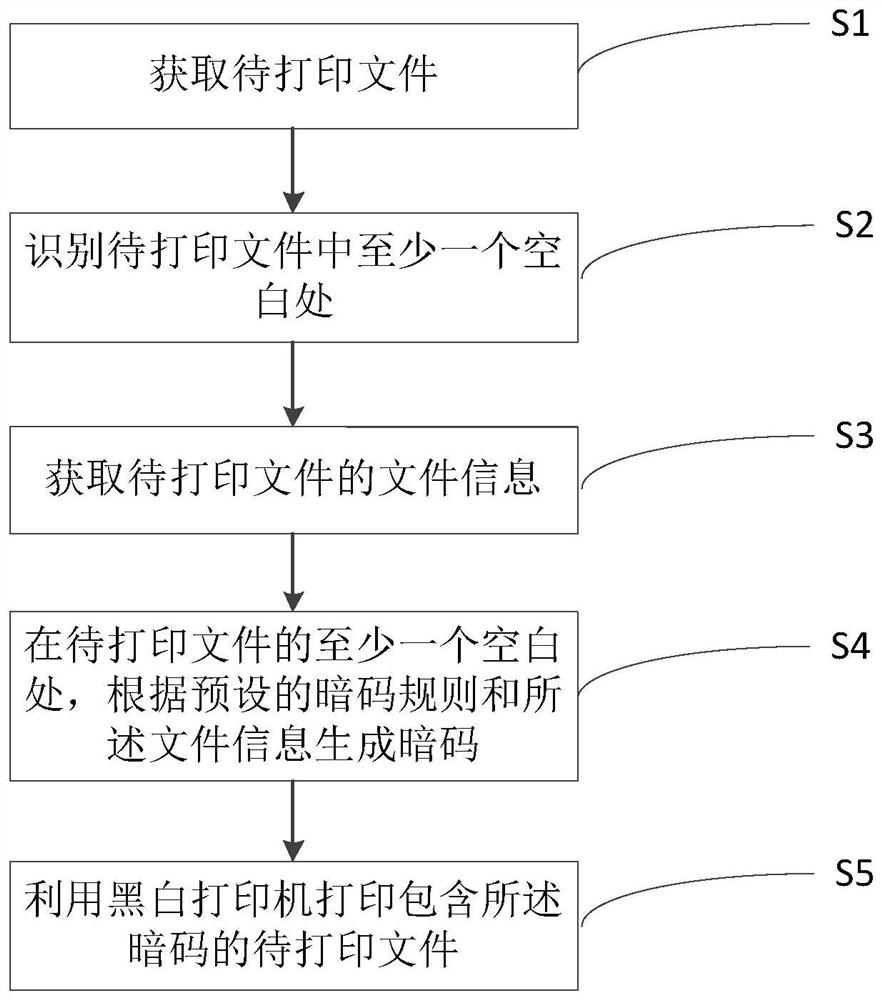
[0039] For the secret code printing method based on black and white print files, see figure 1 , including the following steps:
[0040] S1: Obtain the file to be printed;
[0041] Specifically, the obtained file to be printed is an electronic document, which may be in image format, PDF format or text format.
[0042] S2: identifying at least one blank space in the file to be printed;
[0043] Specifically, the method automatically finds blank spaces in the printed document to lay out the password, for example, at least three blank spaces are found within one page of the printed document to lay out the password. This method lays out the password in the blank space, which can prevent the password from overlapping with the content or picture of the printed file, and fully considers the layout of the content or picture in the printed file.
[0044] S3: Obtain the file information of the file to be printed;
[0045] Specifically, the file information includes one or a combinati...
Embodiment 2
[0059] Embodiment 2 On the basis of other embodiments, the following content is also added:
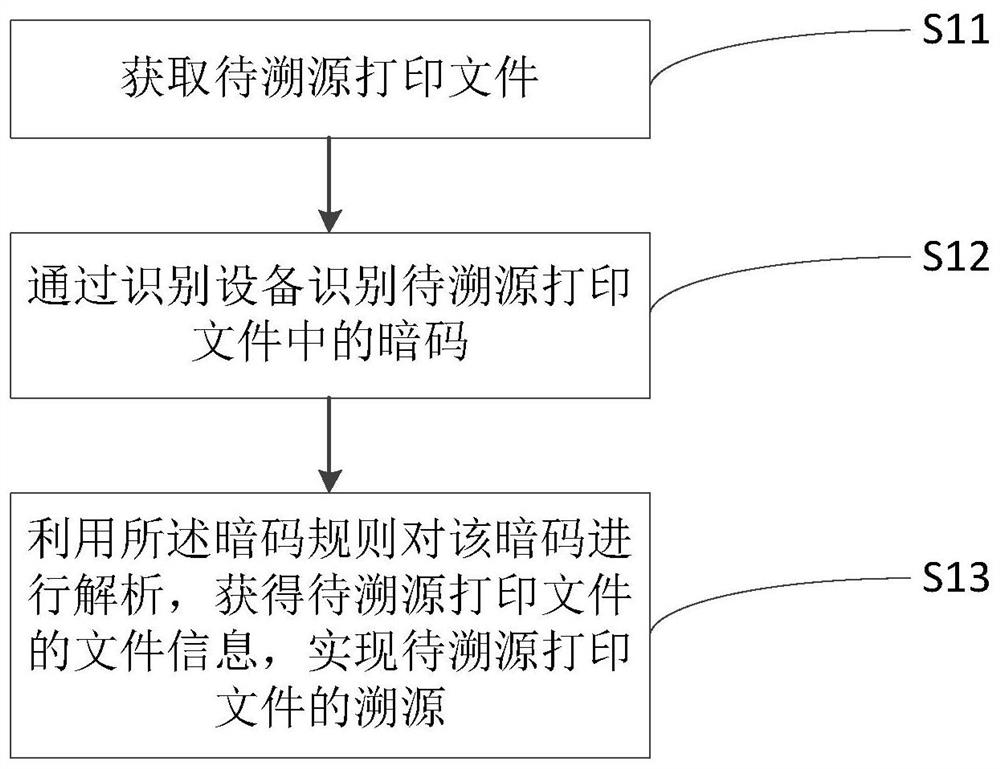
[0060] A traceability method based on black and white printed documents, see figure 2 , including the following steps:
[0061] S11: Obtain the printed file to be traced; the printed file to be traced is printed according to the above-mentioned password printing method;
[0062] Specifically, this method is mainly used to trace the source of the file information of the printed file to be traced, that is, to obtain the printing time and printer information of the printed file to be traced. The printed file to be traced is obtained by printing using the printing method in Embodiment 1.
[0063] S12: Identify the password in the printed document to be traced by the identification device;
[0064] Specifically, the method does not limit specific identification equipment, and the identification equipment needs to have a magnification function, for example, a device with a magnifying gl...
Embodiment 3
[0069] Embodiment 3 On the basis of other embodiments, the following content is also added:
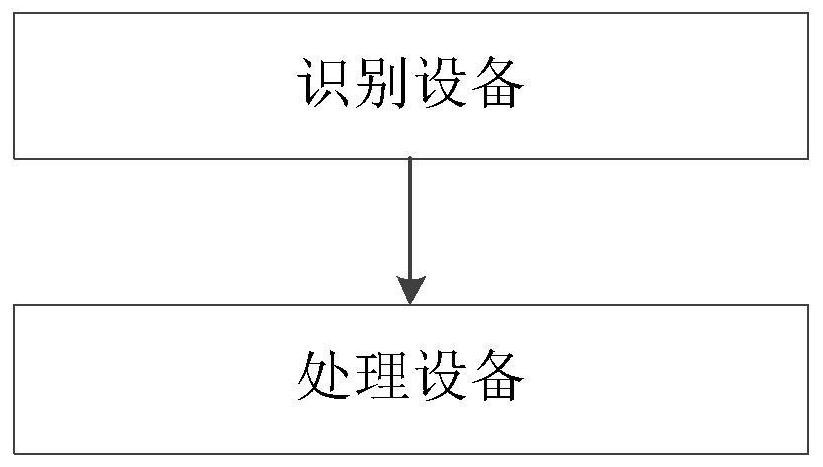
[0070] A traceability system based on black and white printed documents, see image 3 ,include:
[0071] Processing device: used to obtain the printed file to be traced; the printed file to be traced is printed according to the above-mentioned code printing method; the processing device is also used to analyze the code recognized by the identification device by using the code rule to obtain the printed file to be traced The file information of the file realizes the traceability of the printed file to be traced;
[0072] Specifically, the processing device may be a computer, or a mobile terminal or the like.
[0073] Identification equipment: used to identify the passwords in the printed documents to be traced, and send the identified passwords to the processing equipment.
[0074] The system identifies the password in the printed file to be traced through the identification device,...
PUM
| Property | Measurement | Unit |
|---|---|---|
| Diameter | aaaaa | aaaaa |
Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com