Malicious application detection method and device based on network flow, equipment and medium
A malicious application and network traffic technology, applied in computer security devices, instruments, platform integrity maintenance, etc., can solve problems such as network burden, identification difficulties, and difficulty in online detection of malicious applications, so as to improve efficiency and accuracy and save network. The effect of resources
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Example Embodiment
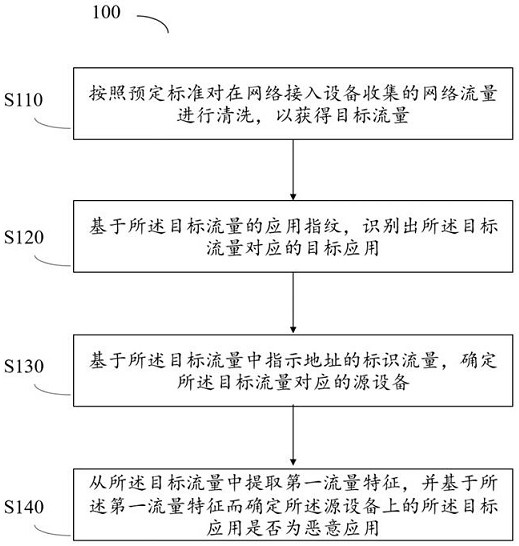
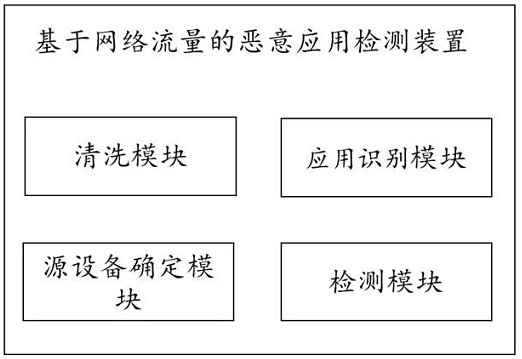
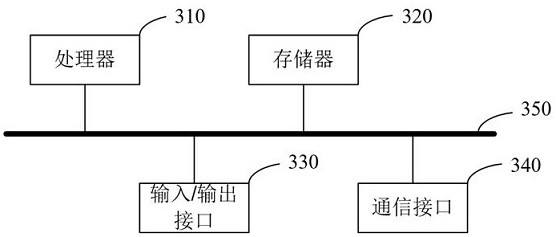
[0041] In order to make the objects, technical solutions, and advantages of the present disclosure, the present disclosure will be described in detail below with reference to the accompanying drawings.
[0042] It should be noted that the technical terms or scientific terms used in the disclosed embodiments, unless otherwise defined, the technical terms used in the disclosure of which should be understood by those who have general skills in the art of the present disclosure. The "first", "second" and similar words used in the embodiments of the present disclosure do not represent any order, quantity, or importance, but only to distinguish different components. Similar words to "include" or "include", meaning that the elements or objects of the previously mentioned previously enumerated elements or objects that appear later in the word, without excluding other elements or objects.
[0043] At present, both the anti-virus product of mobile terminal equipment or the server's software...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap