Proactive defense of untrustworthy machine learning system
A machine learning model and computer technology, applied in transmission systems, integrated learning, instruments, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
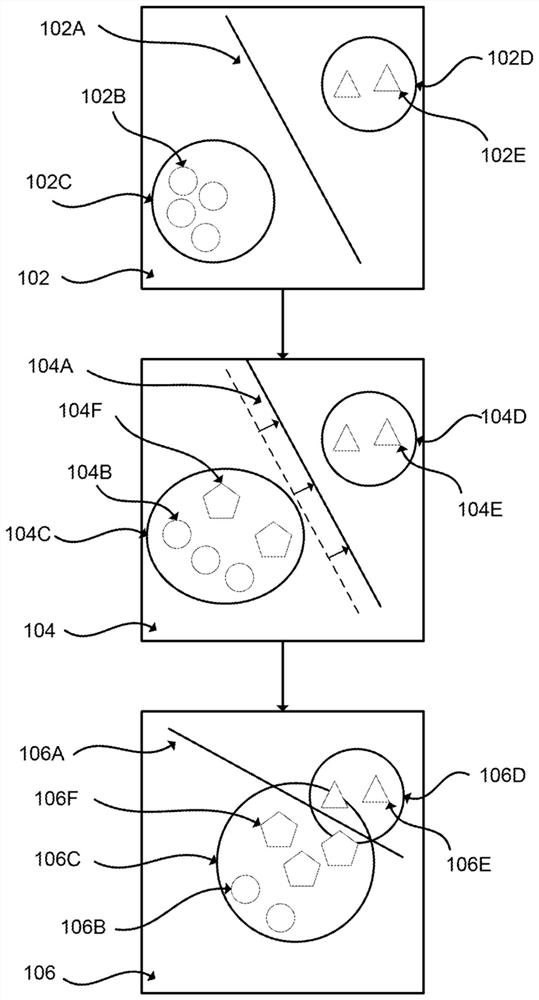
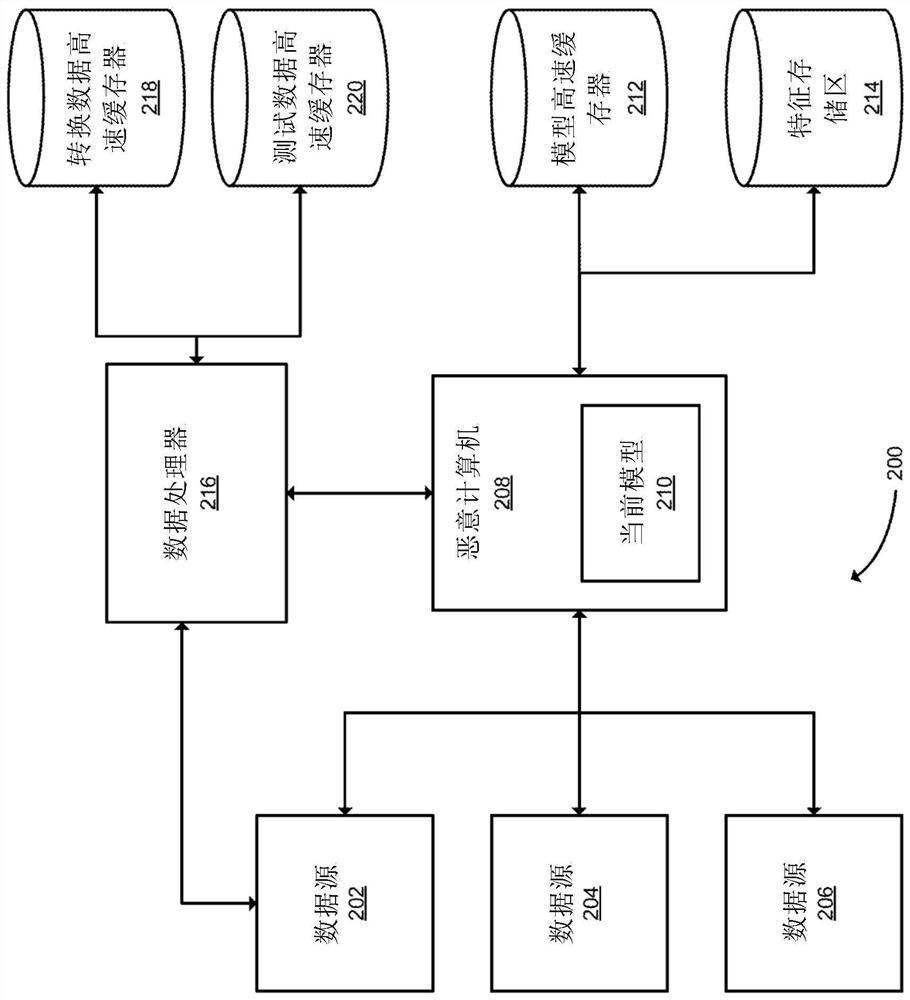
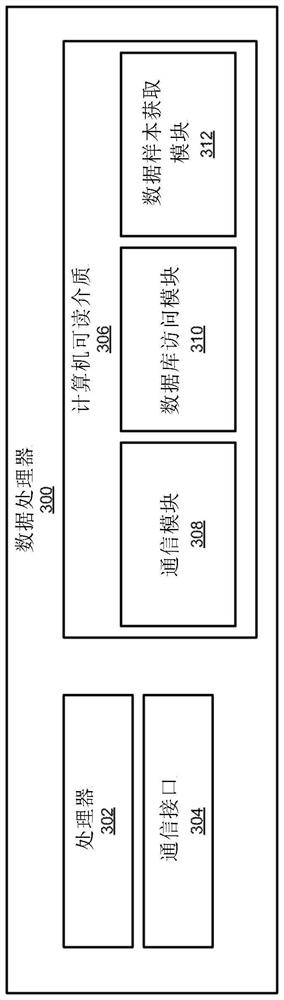
[0033] The following paragraphs introduce some concepts that may be helpful in understanding embodiments of the present invention, model shifting, and improvements over conventional methods and systems. refer to figure 1 Simplified support vector machines in present an example of model shift. After this introduction, refer to figure 2 -6 describes the method and system according to the embodiment in more detail.
[0034] Current anti-fraud systems (eg, CAPTCHAs) are vulnerable to exploitation by malicious entities (eg, hackers). By training a machine learning classifier, a malicious entity can generate classified data that allows the malicious entity to perform malicious actions. Malicious entities can use machine learning classifiers to classify images or alphanumeric characters to bypass CAPTCHA systems. For example, a CAPTCHA can present a series of images to a user attempting to register an email address. CAPTCHA can present 16 images, 5 of which include dogs. The s...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com