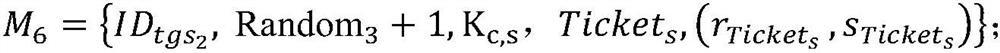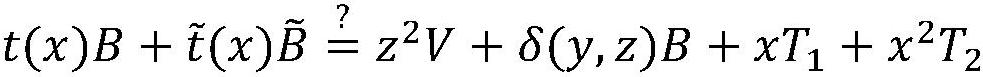Bulletprofs-based Kerberos cross-domain authentication method
An authentication method and domain authentication technology, which is applied in the direction of instruments, electronic digital data processing, digital data protection, etc., can solve the problems of user information leakage and the inability to realize anonymous login and anonymous access of users, so as to reduce the number of interactions, reduce communication traffic, The effect of avoiding leakage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Example Embodiment
[0131] Example:
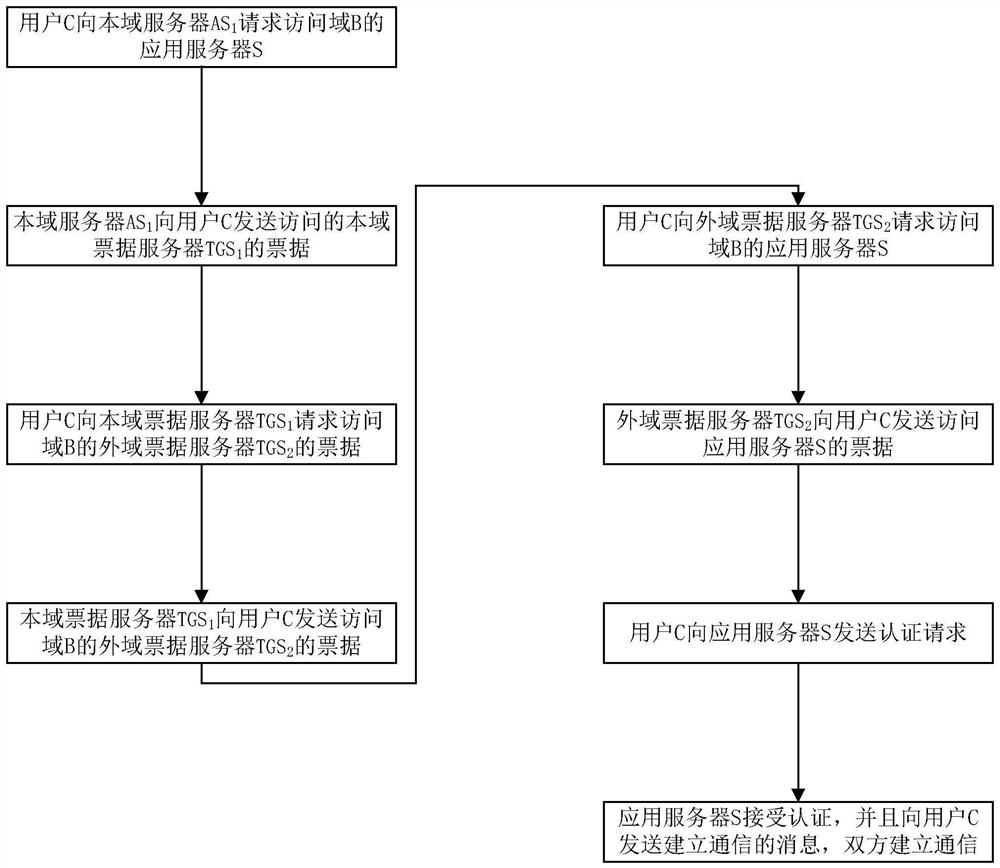
[0132] like figure 1 As shown, the Bulletproofs-based Kerberos cross-domain authentication method process in this embodiment includes:
[0133] S1. User C communicates with the authentication server AS in this domain 1 Request to access the application server S of the foreign domain;
[0134] S2, the authentication server AS of this domain 1 After confirming the identity of user C, send user C to access the intra-domain ticket license server TGS of this domain 1 the bill
[0135] S3. User C obtains the ticket according to the To the intra-domain ticket license server TGS 1 Request access to the Outland Ticket Permission Server TGS 2 the bill
[0136] S4, intra-domain ticket license server TGS 1 After confirming the identity of user C, send the access to the foreign domain ticket license server TGS to user C 2 the bill
[0137] S5. User C constructs the parameters of non-interactive Bulletproofs authentication, that is, data that proves his i...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap