Phishing mail detection method and device, equipment and storage medium
A detection method and phishing email technology, applied in electrical components, transmission systems, etc., can solve problems such as powerlessness and inability to detect, and achieve the effect of preventing infringement and improving security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Example Embodiment
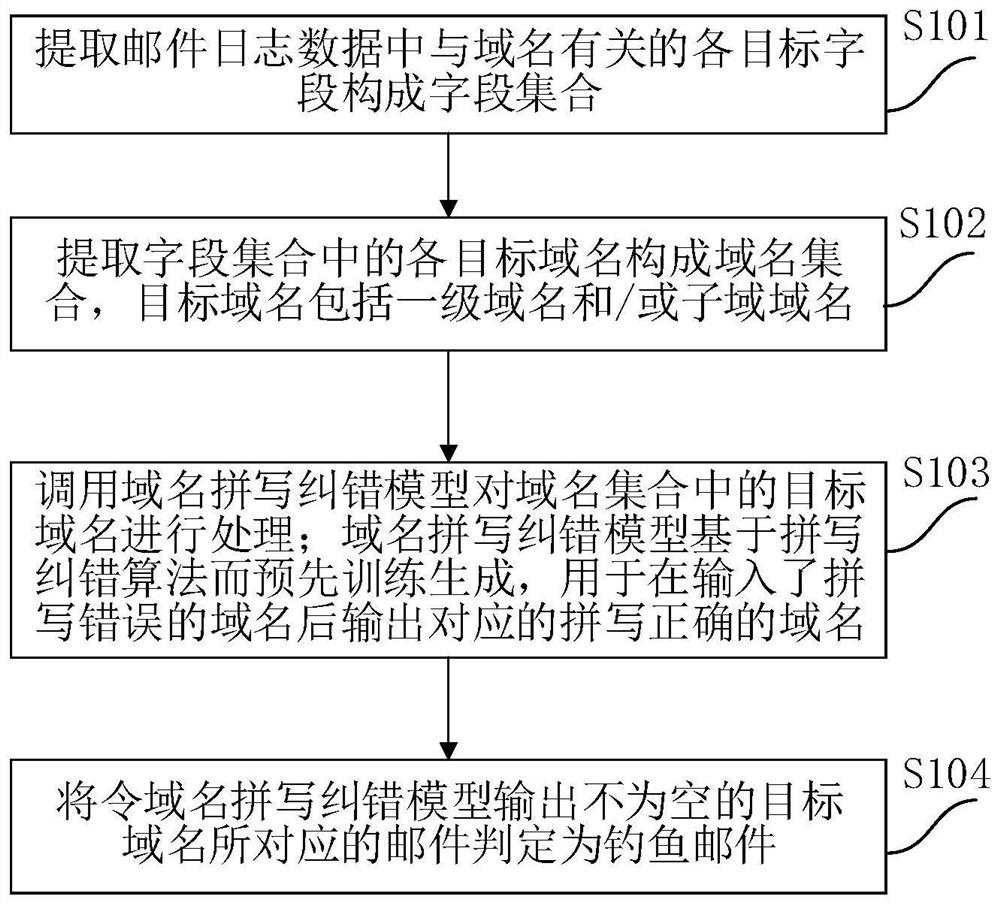
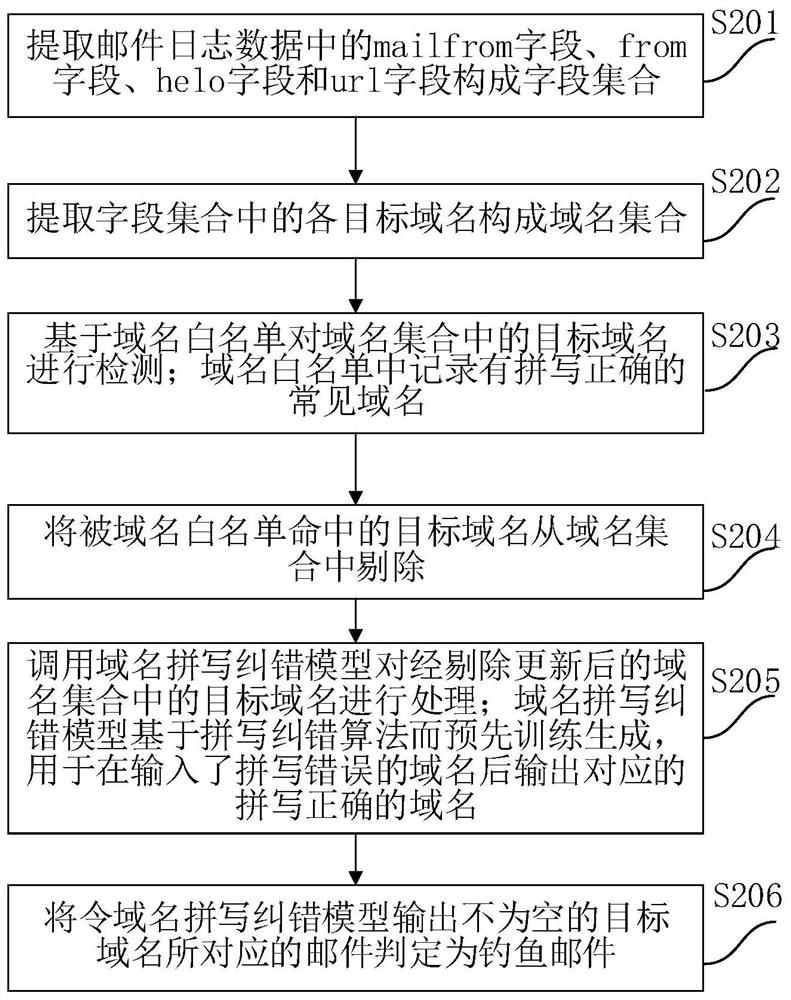
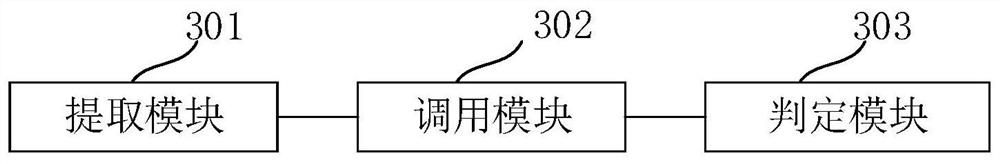
[0043] The core of this application is to provide a test method, device, electronic device, and computer readable storage medium for fishing emails to effectively detect a fishing message using non-spliced confused camouflage means and improve mail security.
[0044] In order to more clear and completely, the technical solutions in the present application embodiment will be described in conjunction with the drawings in the present application embodiment. Based on the embodiments in the present application, one of ordinary skill in the art is in the scope of the present application without making creative labor premistence.
[0045] Fishing mail generally uses camouflage emails, deceives the recipient to reply to the specified recipient, or boot the recipient to the special web page, and these webpages are usually presented into and real-name. The same look, such as a web page, such as bank or financial management, to make the login letter to true, enter credit card or bank card ...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap