Device for computer internal information security to prevent non-professional person USB disk insertion
A technology of internal information and inserting devices, which is applied in the field of network information security, can solve problems such as poor contact, loss of internal data, and insufficient contact, and achieve the effect of preventing poor contact
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
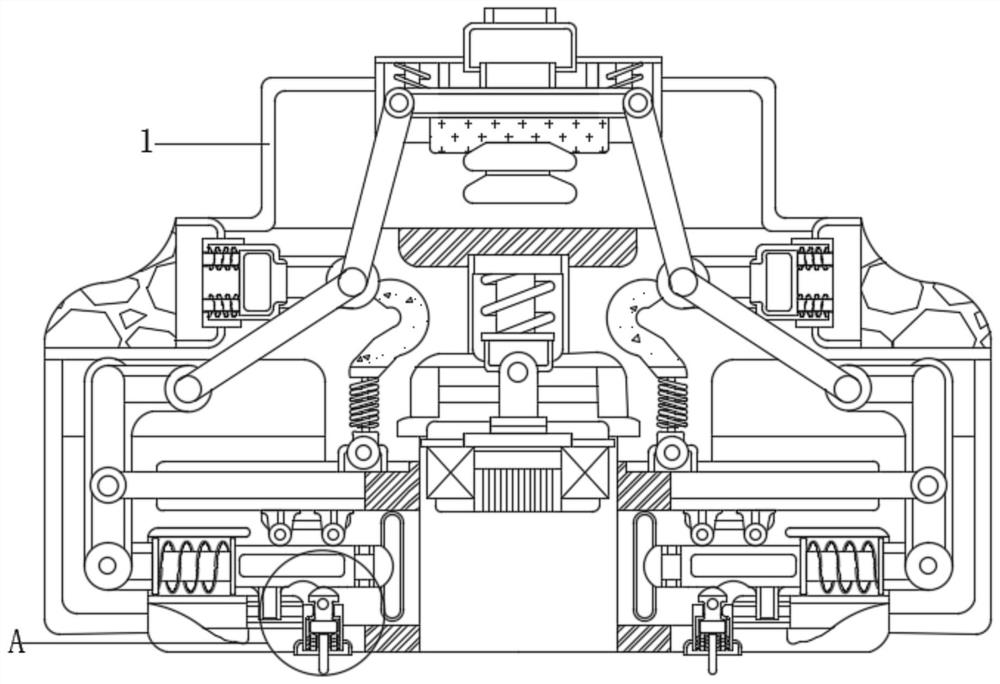
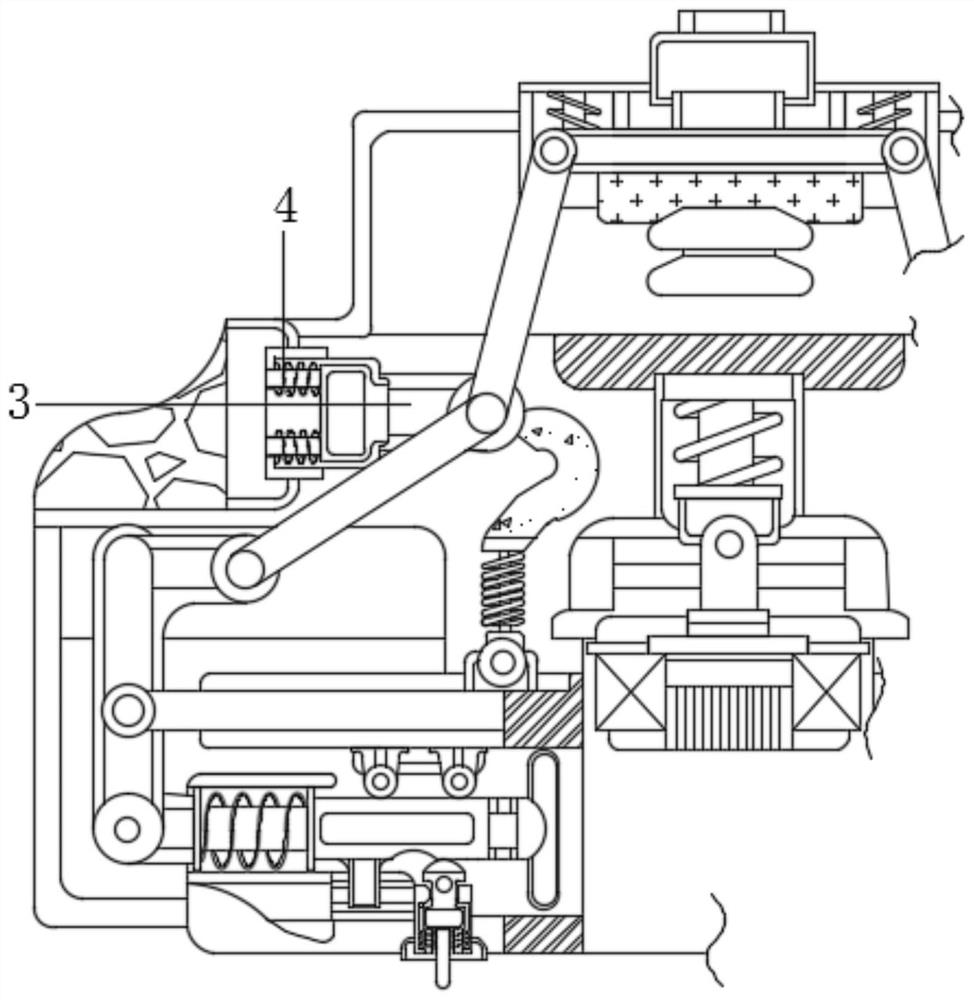
[0026] see figure 1 , figure 2 , image 3 and Figure 6 , a device for preventing non-professionals from inserting U disks for computer internal information security, including a limit mechanism 5 and a plug-in mechanism 2, the limit mechanism 5 includes a lower pressing rod 51, and the left end of the lower pressing rod 51 is movably connected with a rotating rod 52 , the front end of the rotating rod 52 is movably connected with a support rod 53, the lower end of the rotating rod 52 is movably connected with a guide post 54, the outer surface of the guide post 54 is movably connected with a resistance spring 55, and the right end of the guide post 54 is fixedly connected with a limit block 56, and also includes a card The connecting mechanism 6 includes a clamping block 61 inside, the lower end of the clamping block 61 is fixedly connected with an energy gathering spring 62 , and the lower end of the clamping block 61 is fixedly connected with a pull rod 63 .
[0027] Wh...
Embodiment 2
[0029] see figure 1 , figure 2 , Figure 4 and Figure 5 , a device for preventing non-professionals from inserting U disks for computer internal information security, including a limit mechanism 5 and a plug-in mechanism 2, the limit mechanism 5 includes a lower pressing rod 51, and the left end of the lower pressing rod 51 is movably connected with a rotating rod 52 The front end of the rotating rod 52 is movably connected with a support rod 53, the lower end of the rotating rod 52 is movably connected with a guide post 54, the outer surface of the guide post 54 is movably connected with a resistance spring 55, and the right end of the guide post 54 is fixedly connected with a limit block 56. The power connection mechanism 7 includes a movable rod 71 inside, the upper end of the movable rod 71 is movably connected with a balance rod 72, the upper end of the balance rod 72 is fixedly connected with a tension spring 73, and the lower end of the balance rod 72 is fixedly con...
Embodiment 3
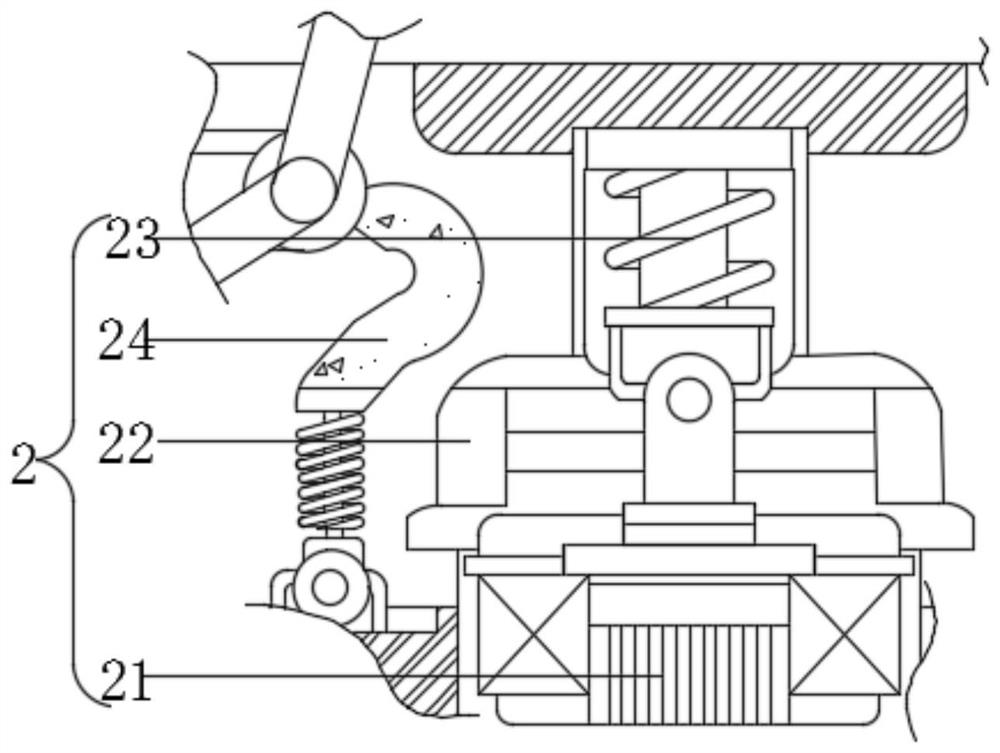
[0034] see Figure 1-5, a device for preventing non-professionals from inserting U disks for computer internal information security, including a limit mechanism 5 and a plug-in mechanism 2, the limit mechanism 5 includes a lower pressing rod 51, and the left end of the lower pressing rod 51 is movably connected with a rotating rod 52 , the front end of the rotating rod 52 is movably connected with a support rod 53, the lower end of the rotating rod 52 is movably connected with a guide post 54, the outer surface of the guide post 54 is movably connected with a resistance spring 55, the right end of the guide post 54 is fixedly connected with a limit block 56, and the plug-in mechanism 2 The interior includes an interface 21, the upper end of the interface 21 is fixedly connected with a wrapping block 22, the upper end of the wrapping block 22 is fixedly connected with a return spring 23, the left end of the wrapping block 22 is movably connected with a resistance rod 24, and the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com