Fuzzy testing method and device for automatically mining vulnerabilities
A technology of fuzz testing and vulnerability, which is applied in the field of application security and can solve the problems of low automation of fuzz testing and inability to fuzz the same target file.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
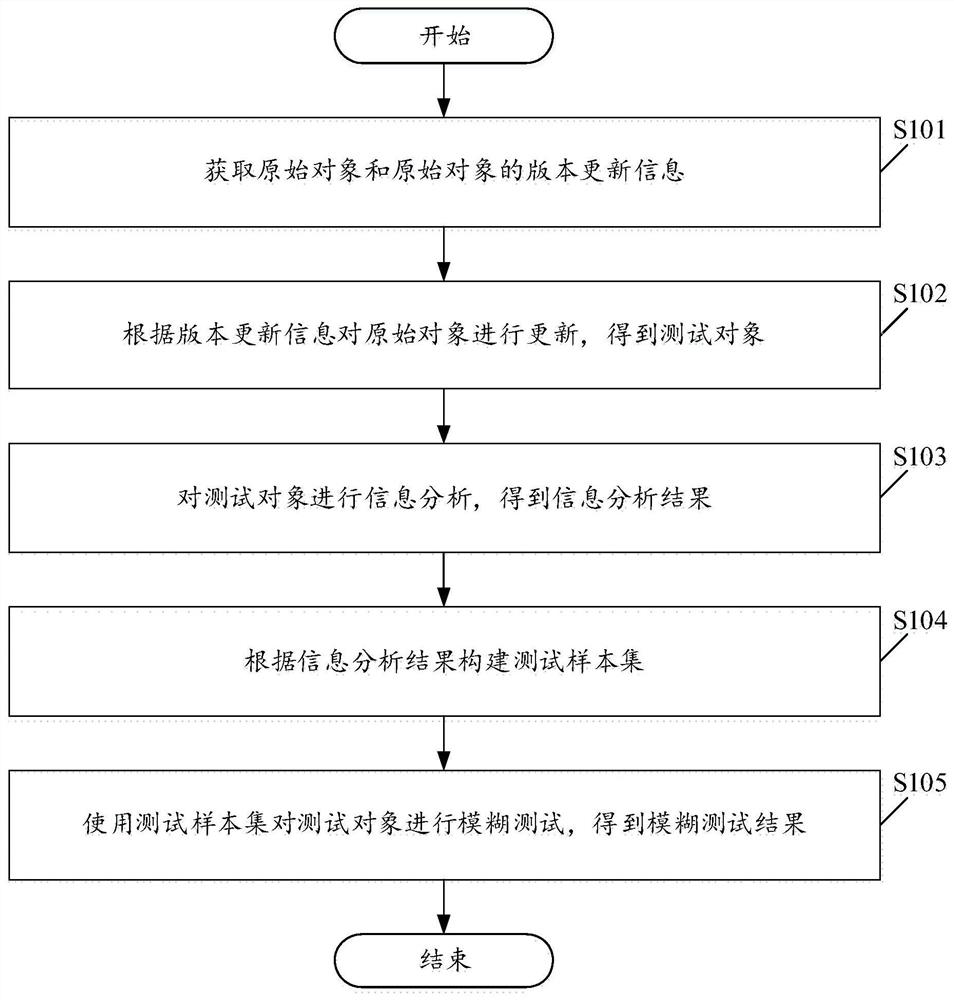
[0050] Please see figure 1 , figure 1 The embodiment of the present application provides a schematic flowchart of a fuzzing method for automatic vulnerability mining. Among them, the fuzzing method for automatic vulnerability mining includes:
[0051] S101. Obtain an original object and version update information of the original object.
[0052] In this embodiment, the original object can be any program with file and protocol analysis, including open-source and closed-source programs.
[0053] S102. The original object is updated according to the version update information to obtain the test object.
[0054] In this embodiment, the method can monitor the software release information of the original object. If a new version of the software is released, the original object is updated to the latest version to obtain the above-mentioned test object.
[0055] S103. Perform information analysis on the test object to obtain an information analysis result.
[0056] In this embod...
Embodiment 2
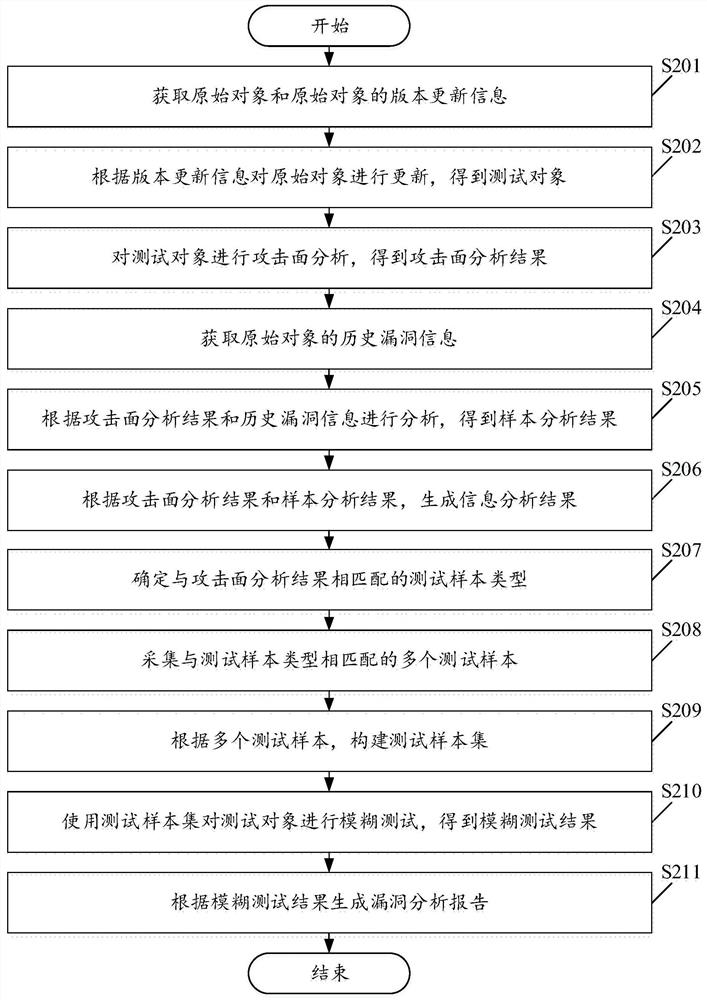
[0066] Please see figure 2 , figure 2 It is a schematic flow chart of a fuzzing method for automatically mining vulnerabilities provided by the embodiment of the present application. Such as figure 2 As shown, among them, the fuzzing method for automatic mining of vulnerabilities includes:
[0067] S201. Obtain an original object and version update information of the original object.
[0068] In this embodiment, the method may periodically scan the publishing website of the test object. If it is found that there is a new version of the test object, it will automatically download the latest version and iterate the current test version. If it finds that the test object has new vulnerabilities or defect submission information, it will automatically download the corresponding abnormal sample and add it to the test sample set.
[0069] In this embodiment, the method can also implement manual monitoring as a supplement to automatic monitoring. Once a new situation that canno...
Embodiment 3
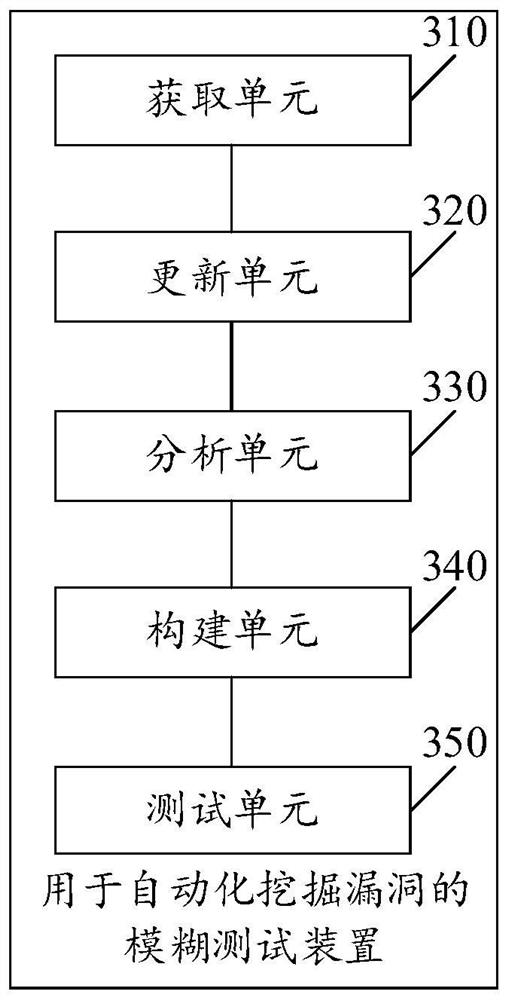
[0109] Please see image 3 , image 3 It is a schematic structural diagram of a fuzz testing device for automatic vulnerability mining provided by the embodiment of the present application. Such as image 3 As shown, the fuzz testing device for automatic vulnerability mining includes:
[0110] An acquisition unit 310, configured to acquire the original object and version update information of the original object;
[0111] An update unit 320, configured to update the original object according to the version update information to obtain the test object;
[0112]An analysis unit 330, configured to perform information analysis on the test object to obtain an information analysis result;
[0113] A construction unit 340, configured to construct a test sample set according to information analysis results;
[0114] The testing unit 350 is configured to use the test sample set to perform a fuzz test on the test object to obtain a fuzz test result.
[0115] In the embodiment of t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com