A kind of private encrypted data identification method and system
A technology of encrypted data and identification method, applied in the field of private encrypted data identification, can solve the problem of low accuracy and efficiency of encrypted data, and achieve the effect of dynamic analysis and rapid identification
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0061] In this embodiment 1, during the loading process of the data to be identified, data collection is performed through a Gigabit (or 10 Gigabit network port) and a high-speed drive module of a network card.
[0062] According to the collected data, analyze according to the four-layer protocol of TCP / IP (Ethernet layer, network layer, transport layer, application layer) to obtain standard protocol fields, and use the standard protocol fields as the comparison object as the basis for the private protocol identification logic judgment . The specific analysis process and content of different layer protocols are as follows:
[0063] 1) Ethernet layer protocol analysis:
[0064] Analyze VLAN protocol, PPPOE protocol, MPLS protocol, parse user-defined Ethernet protocol or add additional private protocol data to Ethernet; parse to get mac address, vlan id, network layer protocol id and other fields.
[0065] 2) Network layer protocol analysis:
[0066] Analyze IPV4, IPV6, ARP, ...
Embodiment 2
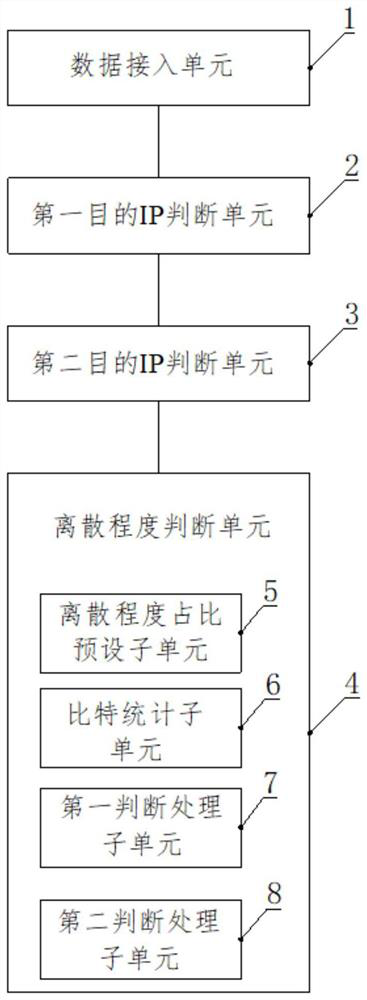
[0090] see image 3 , Embodiment 2 of the present invention also provides a private encrypted data identification system, including:
[0091] A data access unit 1, configured to obtain the parsed data to be identified, and preset a blacklist IP list and a whitelist IP list;
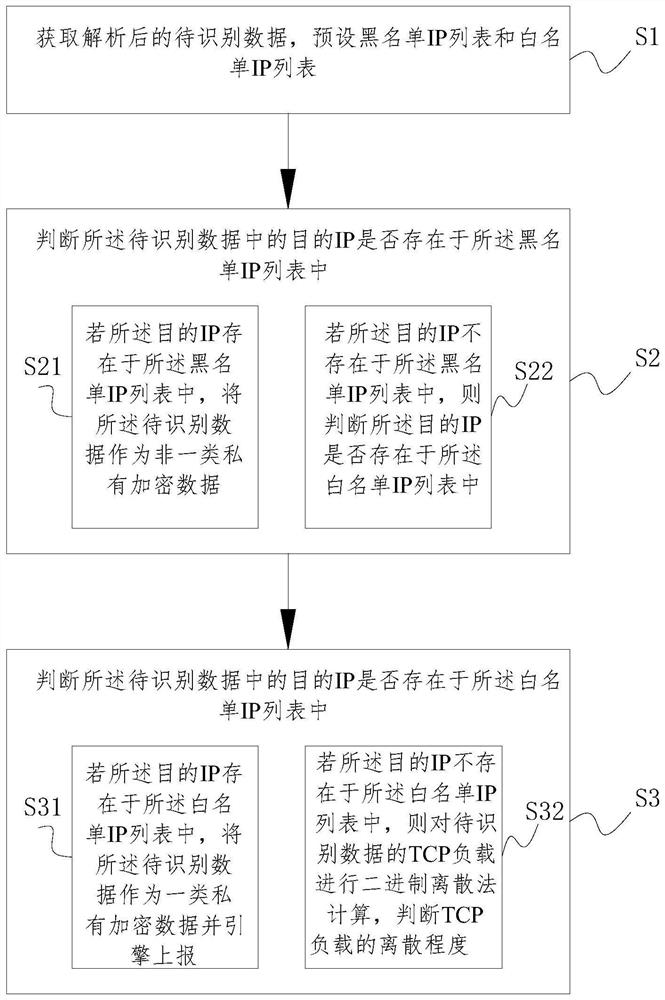
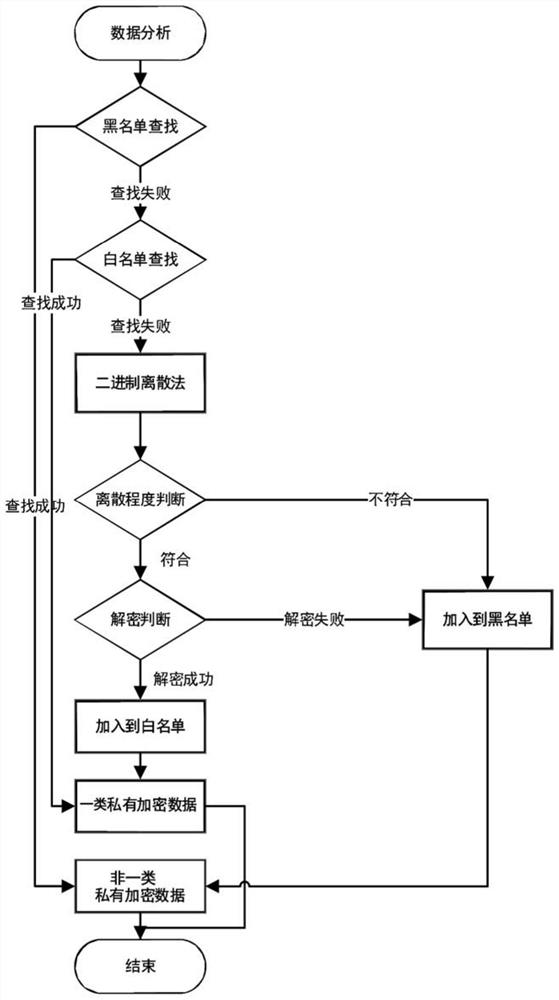
[0092] The first destination IP judgment unit 2 is used to judge whether the destination IP in the data to be identified exists in the blacklist IP list:
[0093] If the destination IP exists in the blacklist IP list, the to-be-identified data is regarded as non-classified private encrypted data;
[0094] If the destination IP does not exist in the blacklist IP list, then determine whether the destination IP exists in the whitelist IP list;
[0095] The second destination IP judgment unit 3 is used to judge whether the destination IP in the data to be identified exists in the whitelist IP list:
[0096] If the destination IP exists in the whitelist IP list, take the data to be identified as a class of ...
Embodiment 3
[0111] Embodiment 3 of the present invention provides a non-transitory computer-readable storage medium, where a program code of a private encrypted data identification method is stored in the computer-readable storage medium, and the program code includes a program code for executing Embodiment 1 or any one thereof Instructions for possible implementations of private encrypted data identification methods.
[0112] A computer-readable storage medium can be any available medium that can be accessed by a computer or a data storage device such as a server, a data center, or the like that includes an integration of one or more available media. The usable media may be magnetic media (eg, floppy disks, hard disks, magnetic tapes), optical media (eg, DVD), or semiconductor media (eg, Solid State Disk (SSD)), and the like.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com