Mobile terminal using method and mobile terminal and mobile terminal system
A mobile terminal and terminal identification technology, applied in the field of communication, can solve problems such as inconvenient operation and uncontrollable security, and achieve the effects of protecting security, increasing trust, and preventing exposure
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0090] The specific implementation manners of the present invention will be described below in conjunction with the accompanying drawings.
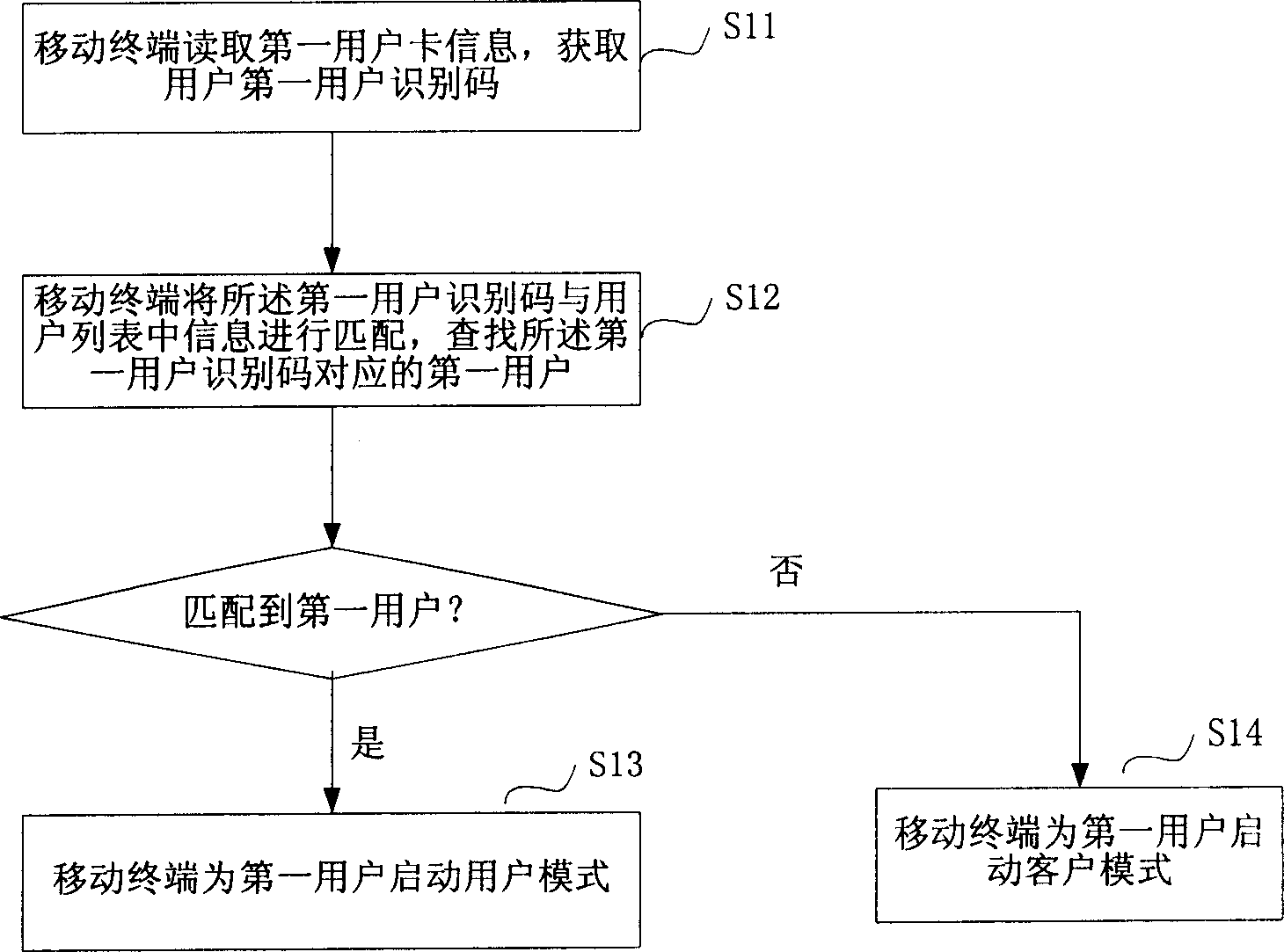
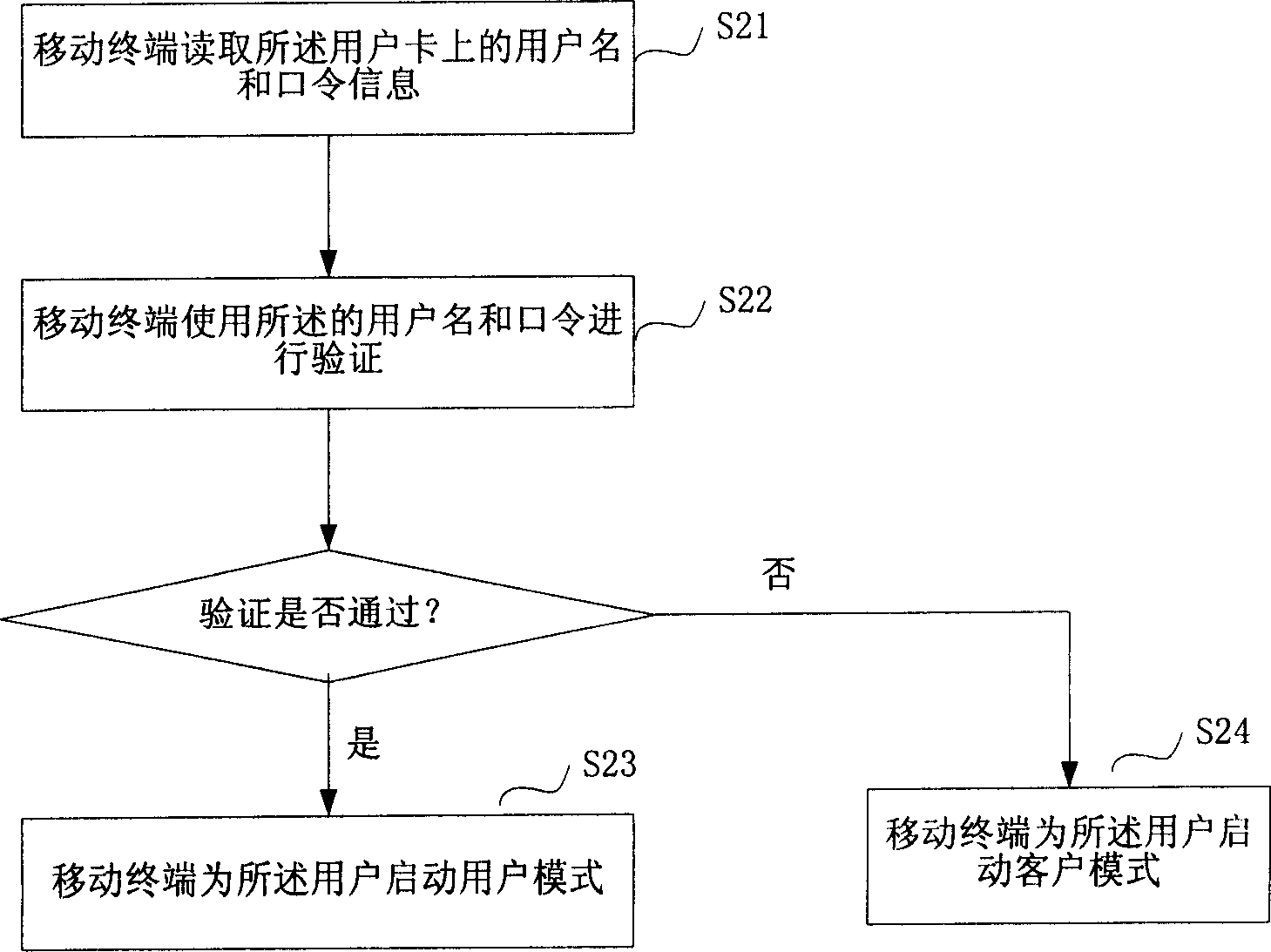
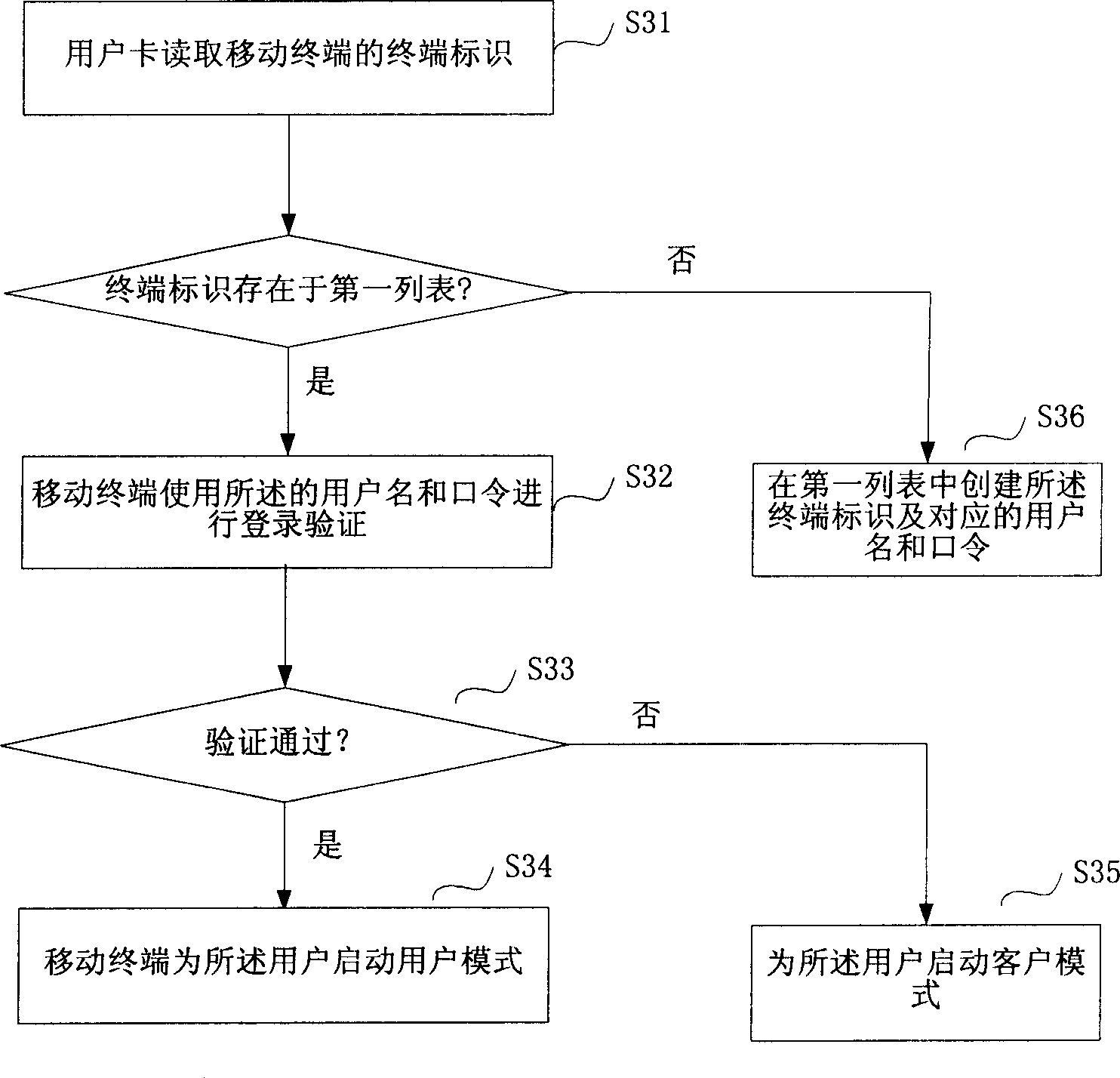
[0091] First explain the concept of user mode. The user mode mainly means that the user can use the program normally after entering the mobile terminal, but the sensitive data such as the accessible phone book, short message, email, and document are bound to the user name. In order to facilitate the identification of each user, the mobile terminal needs to manage and process a user with multiple cards to ensure that each card can effectively activate the user account.
[0092] Option One:
[0093] Normally, whether it is a GSM system or a CDMA system, a mobile terminal user will get a user card (such as a SIM card in the GSM system or a UIM card in the CDMA system) when "connecting to the network", which can be inserted into any GSM-compliant specification or within the mobile terminal of the CDMA specification. The International Mobil...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap