Method and equipment for carrying out safety communication between USB device and host
A technology for secure communication and host, applied in the field of data communication, can solve problems such as hidden dangers, and achieve the effect of simple equipment, convenient use, and increased difficulty
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
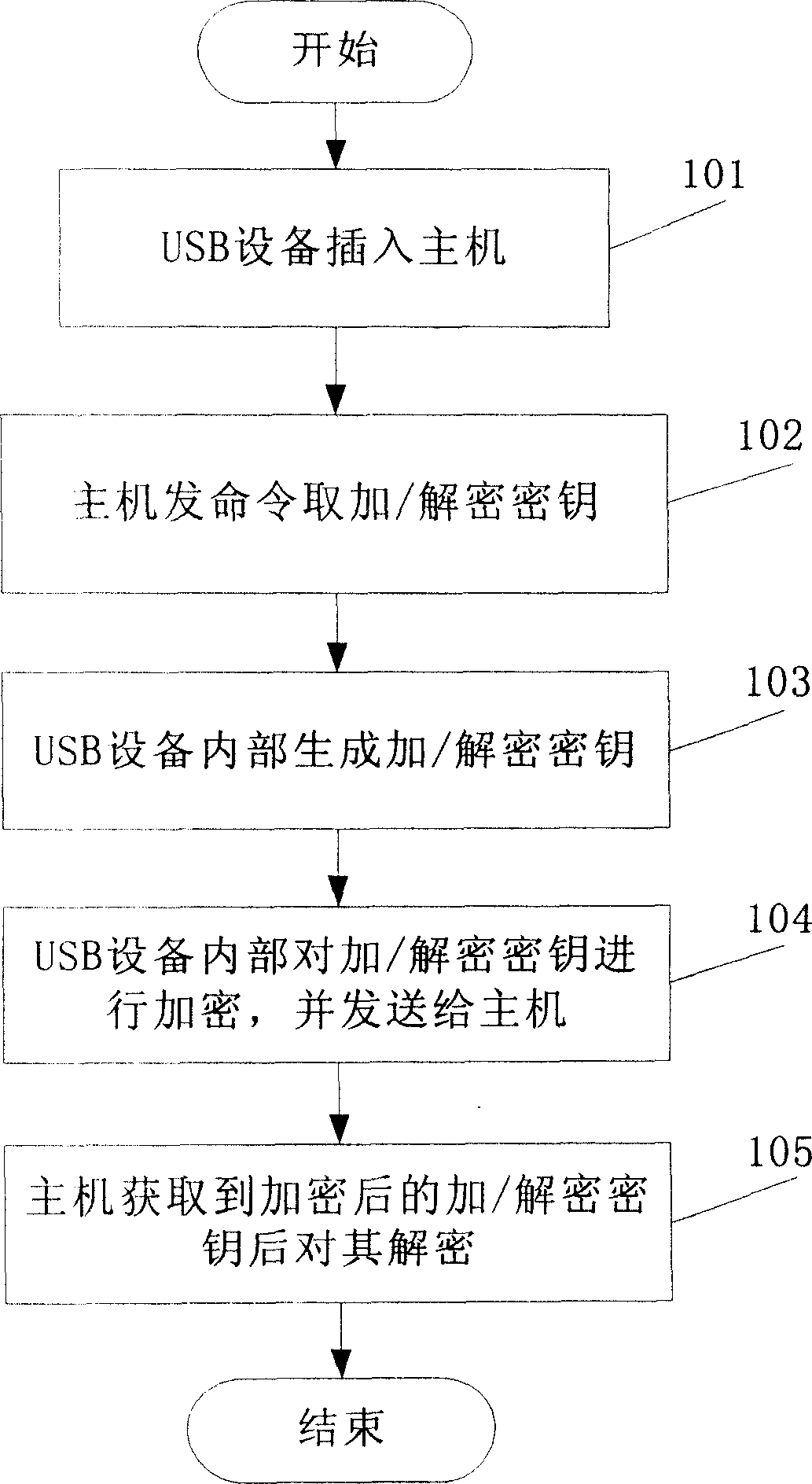
[0043] The encryption / decryption key can be a fixed key or a dynamic key. If it is a fixed key, the fixed key is directly used for data communication. see figure 1 , the dynamic key generation process is as follows:
[0044] Step 101: Plug the USB device into the host.
[0045] The encryption / decryption key is generated when the connection between the USB device and the host is established, or during the communication process between the USB device and the host. In this embodiment, it is performed when the connection between the USB device and the host is just established.
[0046] Step 102: The host sends a command to obtain the encryption / decryption key.
[0047] If a symmetric algorithm is used, the encryption key and the decryption key are the same; if an asymmetric algorithm is used, the encryption key and the decryption key are public-private key pairs, which are different.
[0048] Step 103: the USB device generates an encryption / decryption key after receiving the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com