Key-updating method, encryption processing method, key-insulated cryptosystem and terminal device
A terminal device and key update technology, which is applied in the transmission system, digital transmission system, secure communication device, etc., can solve the problems of key update, threat key isolation type cryptosystem, and inability to solve key update, etc., to achieve The effect of improving safety
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 approach
[0053] Next, a first embodiment of the present invention will be described. In addition, in the description of the drawings below, the same or similar symbols are given to the same or similar parts. Wherein, the drawings are schematic, and it should be noted that the proportions of various dimensions thereof are different from the actual ones.
[0054] Therefore, specific dimensions and the like should be determined in consideration of the following description. In addition, of course, the relationship and ratio of mutual dimension also contain the part which differs among drawings.
[0055] (The entire schematic structure of a key-segregated cryptosystem)
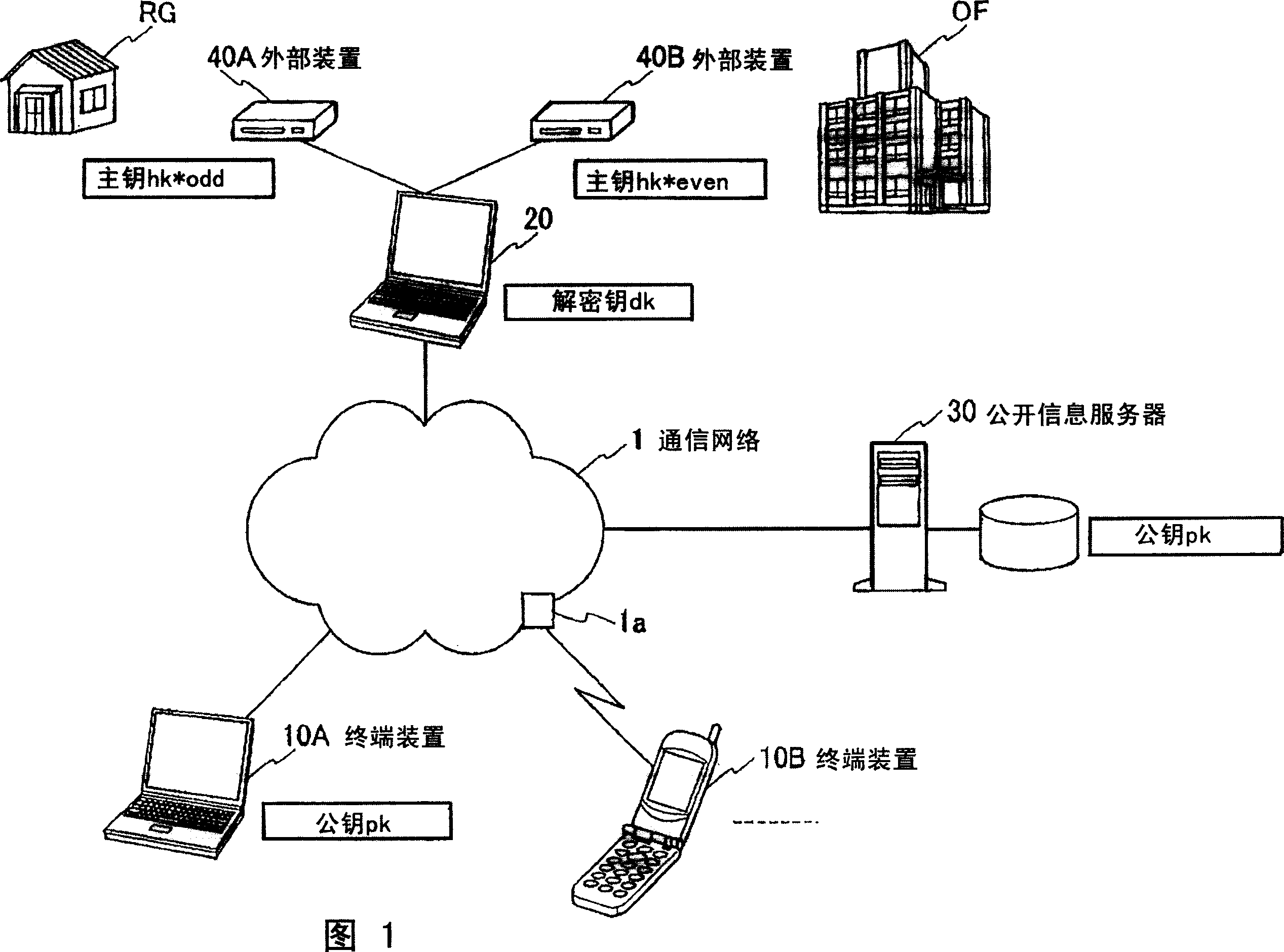
[0056] FIG. 1 is an overall schematic configuration diagram of a key isolation type cryptographic system according to a first embodiment of the present invention. As shown in FIG. 1 , the key isolation type encryption system of this embodiment includes terminal devices 10A and 10B, a terminal device 20 , a public inform...
no. 2 approach
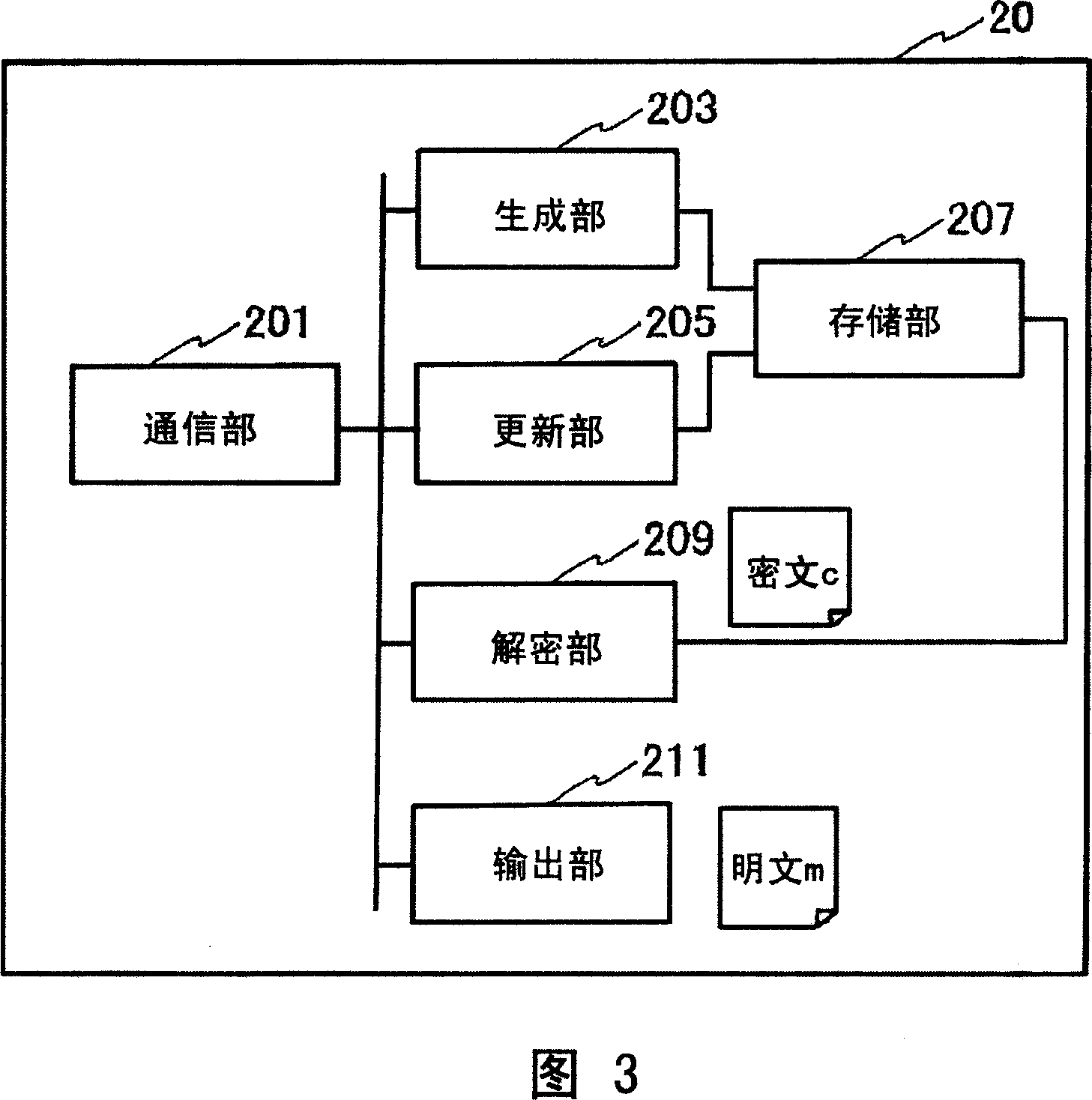
[0148] Next, a second embodiment of the present invention will be described. Hereinafter, differences from the first embodiment described above will be mainly described.
[0149] (Logical block structure of key isolation type cryptosystem)
[0150] The logical block configuration of the terminal device 10A (10B), the terminal device 20, the public information server 30, and the external device 40 (40B) constituting the key isolation type cryptographic system of this embodiment is similar to that of the terminal device 10A of the first embodiment of the present invention. (10B), the terminal device 20, the public information server 30, and the external device 40 (40B) are the same.
[0151] (1) Terminal device 10A
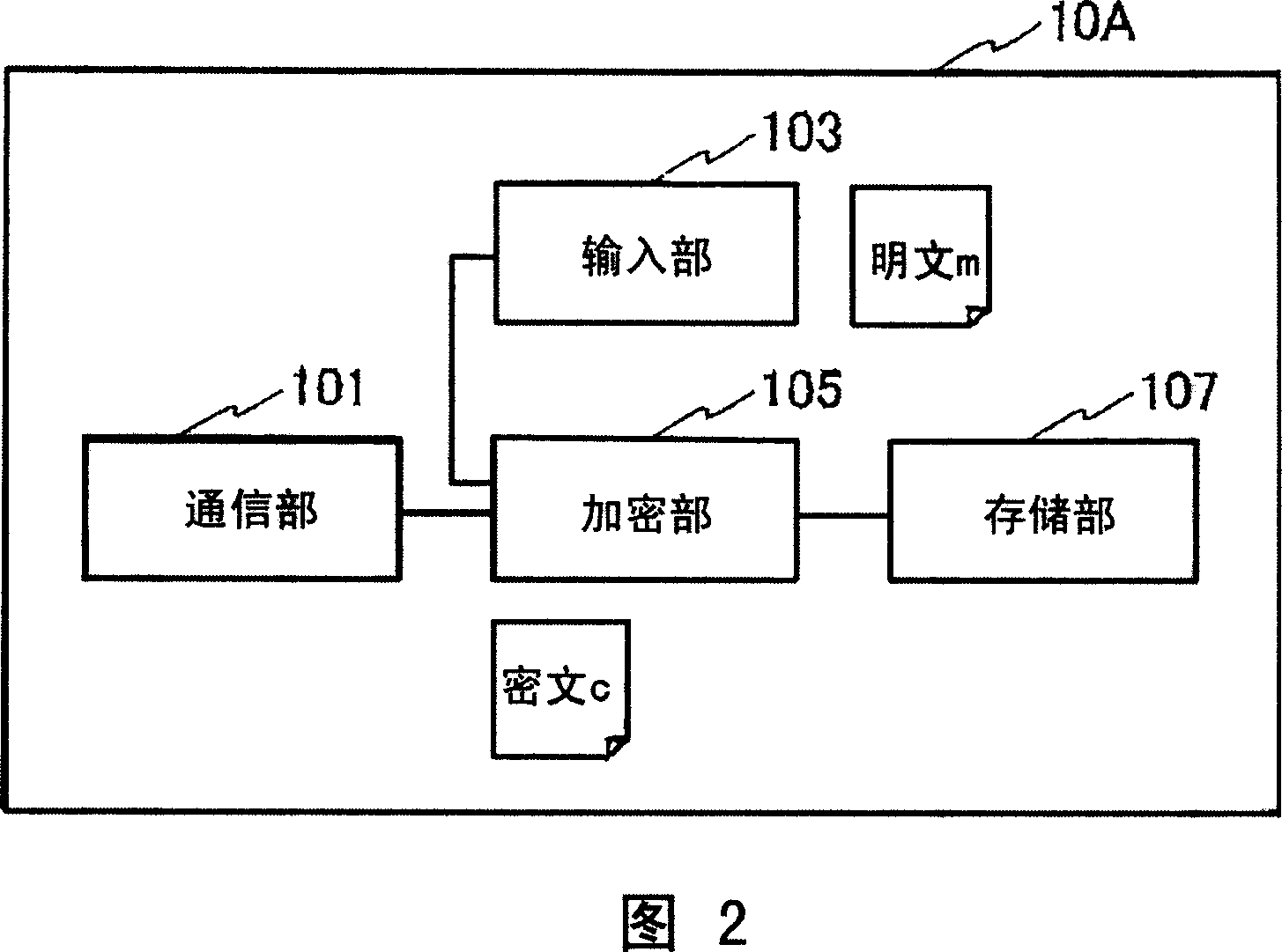
[0152] In this embodiment, the encryption unit 105 encrypts plaintext m using the following public key pk. First, the encryption unit 105 uses and decrypts the key dk j-1 (The terminal private key after the first update) corresponds to the public key pk j-1 (th...
no. 3 approach
[0178]A third embodiment of the present invention will be described below. In the above-mentioned first and second embodiments, it is necessary to interactively use two external devices (external devices 40A, 40B) to generate key update information for updating the decryption key dk (terminal private key). In this embodiment, the two external devices can be used without interaction. That is, the present embodiment considers improving the user's convenience while securing a certain level of security of a key-separated cryptographic system.
[0179] Specifically, in this embodiment, the decryption key dk is updated every day. The user of the terminal device 20 updates the decryption key dk every day using the external device 40B installed in the OF. Furthermore, the user of the terminal device 20 updates the decryption key dk once a month using the external device 40A installed in his home RG.
[0180] The user of the terminal device 20 does not necessarily have to interactiv...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com