Cybersecurity Best Practices for DCS Networks
JUL 2, 2025 |
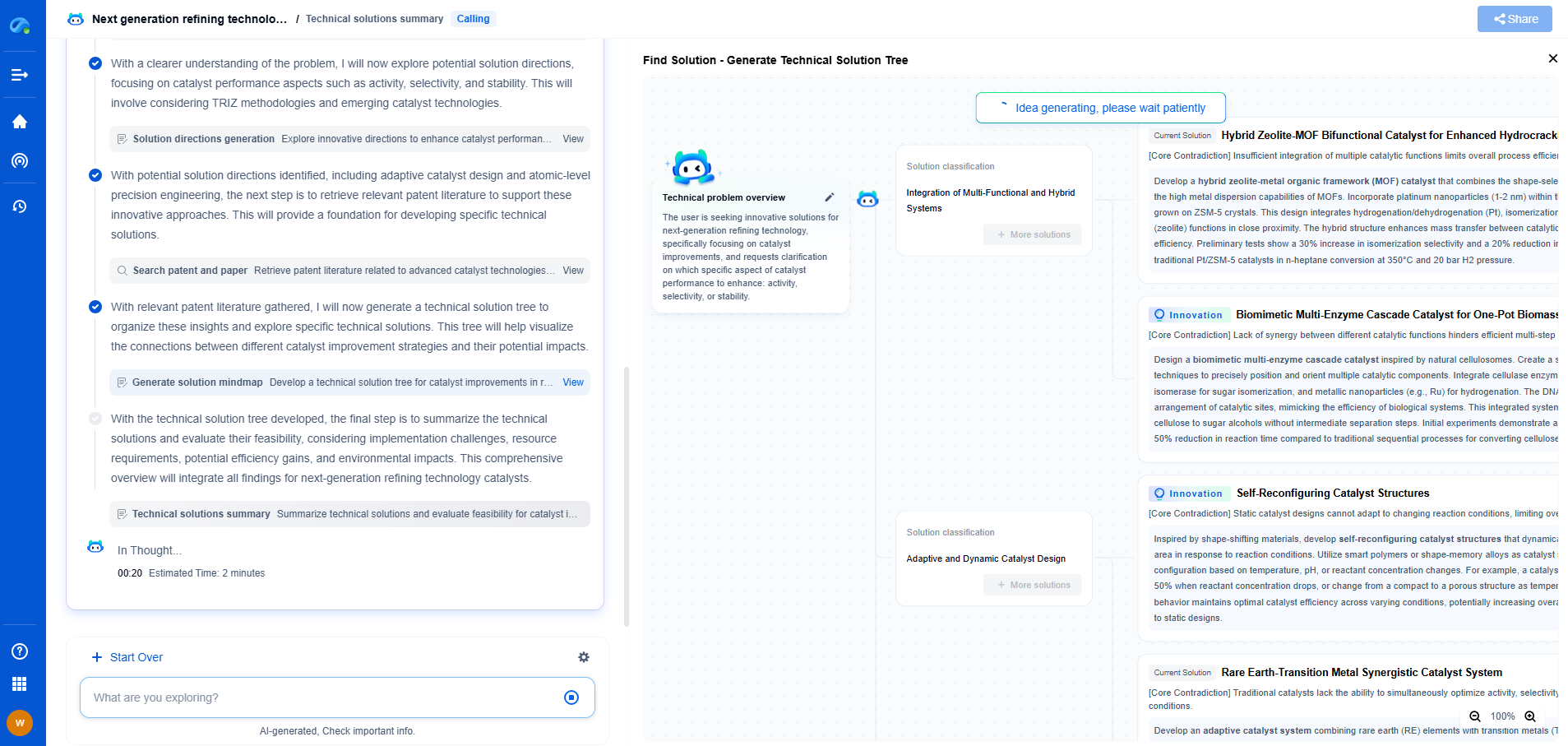
Understanding DCS Network Vulnerabilities
Before diving into security measures, it's essential to understand the vulnerabilities inherent in DCS networks. Traditionally, these systems were designed with a focus on availability and reliability rather than security. Many DCS networks still run on legacy systems that lack robust security features, making them susceptible to threats. Identifying potential weak points such as outdated software, inadequate network segmentation, and unsecured remote access points is the first step toward strengthening their security posture.
Implementing Strong Authentication and Access Control
One of the fundamental strategies for enhancing DCS network security is implementing strong authentication and access control mechanisms. Multi-factor authentication (MFA) should be employed to ensure that only authorized personnel have access to critical components. Additionally, implementing role-based access control (RBAC) helps limit the permissions of users to only what is necessary for their role, reducing the risk of insider threats.
Regular Software Updates and Patch Management
Keeping software and systems up-to-date is crucial in defending against new vulnerabilities. Establish a comprehensive patch management process that includes regular updates of operating systems, applications, and firmware. Prioritize patches based on the severity of vulnerabilities and the criticality of the systems affected. Automating this process where possible can help ensure that updates are applied promptly and consistently across the network.
Network Segmentation and Firewalls
Network segmentation involves dividing the DCS network into smaller, isolated segments to limit the spread of an attack. By using virtual local area networks (VLANs) and firewalls, organizations can control traffic flow between these segments and enforce strict access policies. This approach not only minimizes the impact of a breach but also simplifies monitoring and management.
Intrusion Detection and Response
Implementing an Intrusion Detection System (IDS) or Intrusion Prevention System (IPS) is vital for monitoring and detecting suspicious activities within the DCS network. These systems can be configured to alert administrators to potential security threats in real time, enabling swift response to mitigate risks. An effective incident response plan should also be in place to guide the organization in containing and recovering from cyber incidents.
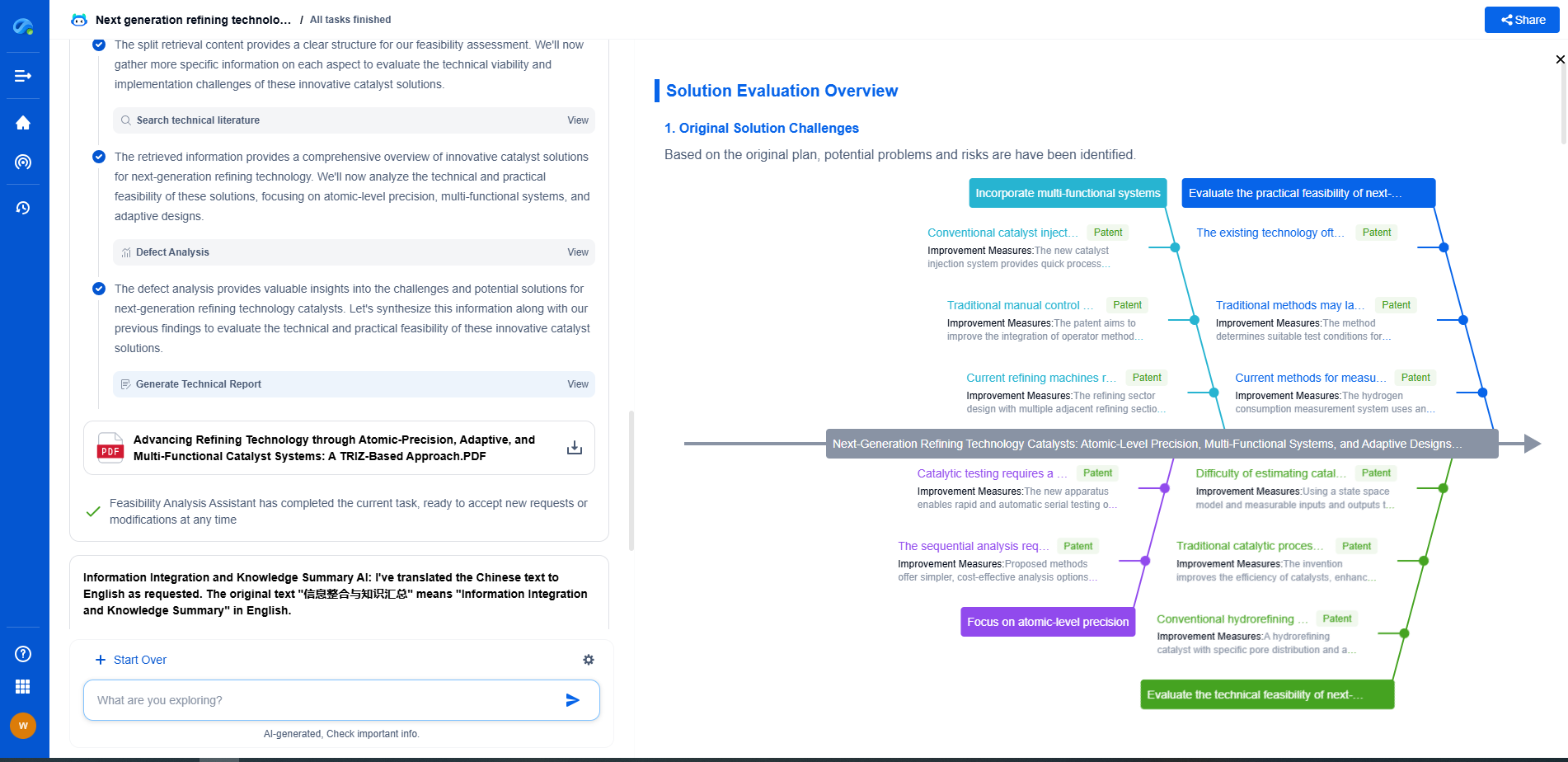
Conducting Regular Security Audits and Assessments
Regular security audits and assessments are critical to identifying vulnerabilities and ensuring compliance with industry standards. Engage third-party experts to conduct penetration testing and vulnerability assessments to provide an objective evaluation of the network's security posture. These audits can uncover hidden vulnerabilities and help prioritize efforts to address them.
Employee Training and Awareness
Human error is a significant factor in many cybersecurity incidents. Therefore, comprehensive training programs are essential to educate employees about cybersecurity best practices and the importance of following security protocols. Encourage a culture of vigilance where employees are aware of potential threats and know how to respond appropriately.
Implementing a Zero Trust Architecture
Adopting a Zero Trust Architecture (ZTA) approach can further enhance the security of DCS networks. This model operates on the principle of never trusting and always verifying, meaning that every access request is treated as a potential threat until it is explicitly verified. This approach requires continuous monitoring and validation of user identities and device health, ensuring that only legitimate users and devices can access sensitive areas of the network.
Collaborating with Industry and Government
Collaboration with industry peers and government entities can provide valuable insights and resources for improving DCS network security. Participate in information-sharing initiatives and join industry groups focused on cybersecurity. These collaborations can help organizations stay informed about the latest threats and trends and leverage collective knowledge to develop more robust security strategies.
By implementing these best practices, organizations can significantly enhance the security of their DCS networks, protecting critical infrastructure from cyber threats. It is vital to continuously evolve and adapt to new threats, ensuring that security measures remain effective in the face of an ever-changing cyber landscape.
Ready to Reinvent How You Work on Control Systems?
Designing, analyzing, and optimizing control systems involves complex decision-making, from selecting the right sensor configurations to ensuring robust fault tolerance and interoperability. If you’re spending countless hours digging through documentation, standards, patents, or simulation results — it's time for a smarter way to work.
Patsnap Eureka is your intelligent AI Agent, purpose-built for R&D and IP professionals in high-tech industries. Whether you're developing next-gen motion controllers, debugging signal integrity issues, or navigating complex regulatory and patent landscapes in industrial automation, Eureka helps you cut through technical noise and surface the insights that matter—faster.
👉 Experience Patsnap Eureka today — Power up your Control Systems innovation with AI intelligence built for engineers and IP minds.
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com