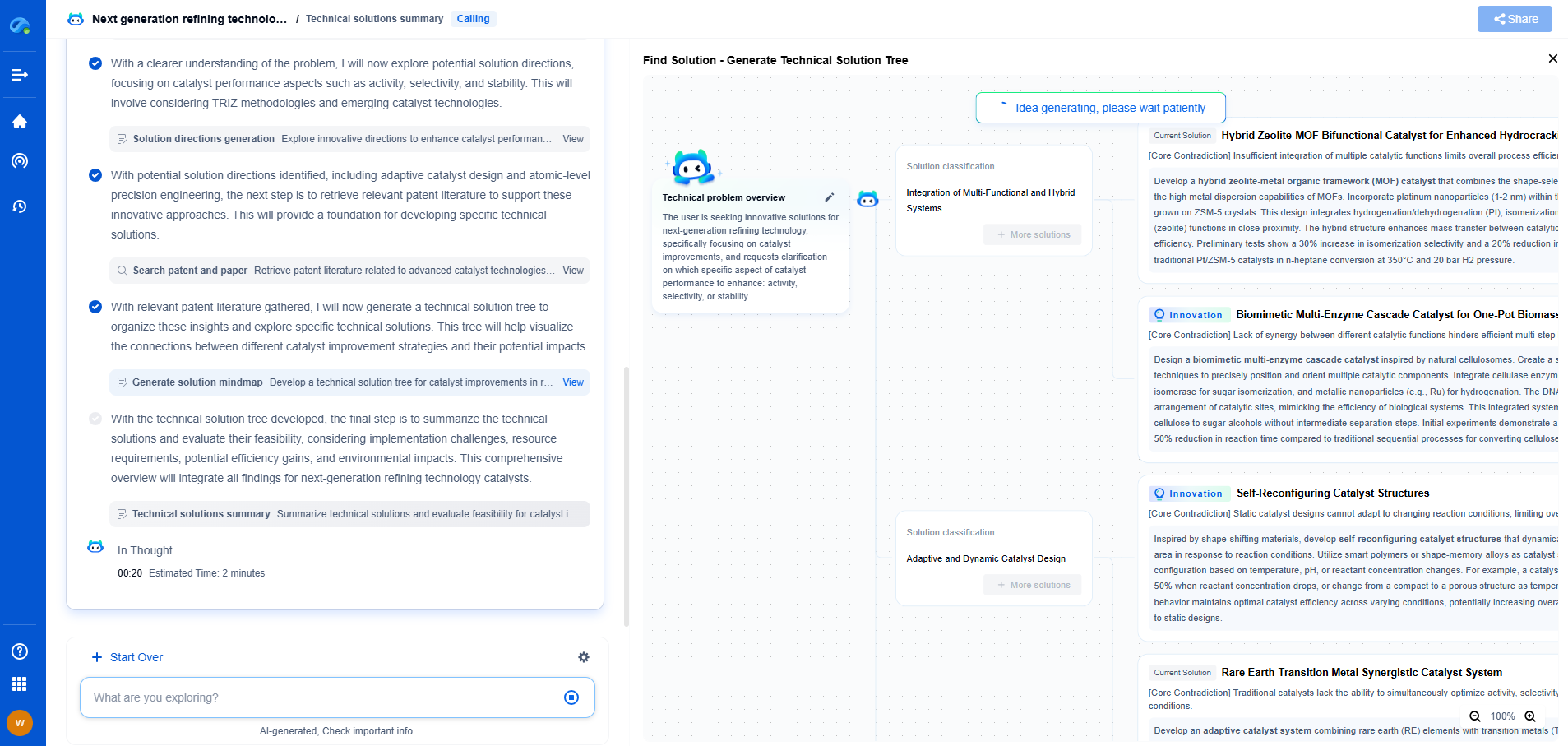
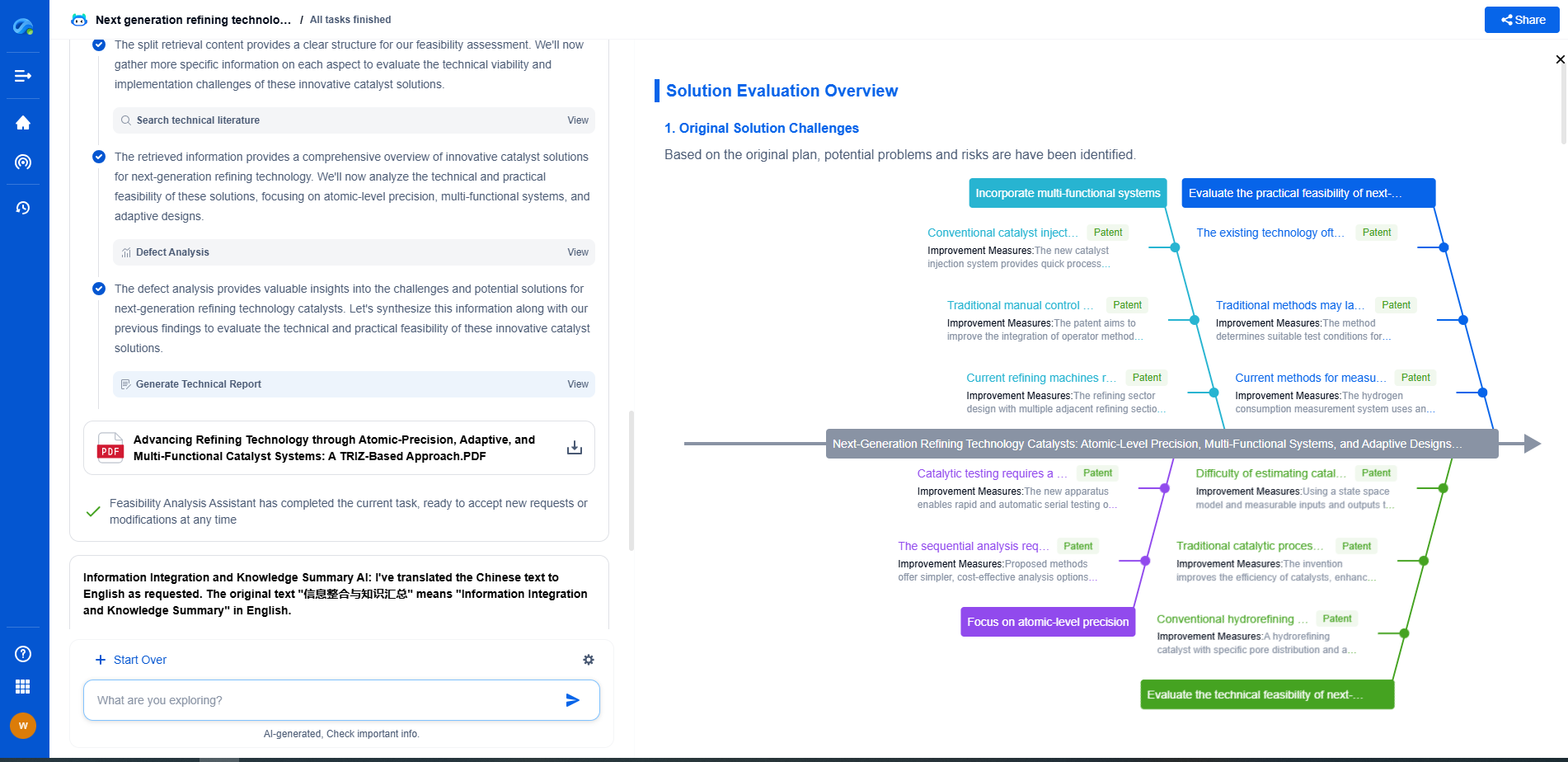
Firewall Placement Strategies: Where to Filter Traffic in Your Network
JUN 27, 2025 |
The digital landscape is ever-evolving, and so are the threats that loom over it. In this environment, firewalls remain a critical component of network security. However, it's not just about having a firewall; where you place it can significantly impact its effectiveness. Understanding the nuances of firewall placement strategies is key to ensuring that your network remains secure and efficient.
Perimeter Firewalls: The First Line of Defense
Traditionally, perimeter firewalls have been the first line of defense, placed at the boundary between an internal network and external networks, like the Internet. This placement is crucial for filtering incoming and outgoing traffic and is typically the first point of contact for potential threats. Perimeter firewalls help in blocking unauthorized access, securing sensitive data, and preventing denial-of-service attacks.
While effective, relying solely on perimeter firewalls is no longer sufficient. The emergence of cloud computing, remote work, and mobile devices necessitates additional layers of security beyond the traditional perimeter.
Internal Firewalls: Securing Within the Network
Internal firewalls add an extra layer of security by segmenting the network into smaller, more manageable sections. This segmentation helps in controlling and monitoring traffic within the network and is essential for preventing lateral movement of threats. For instance, if a threat actor gains access to one segment of the network, internal firewalls can prevent them from easily moving to other segments.
This strategy is particularly beneficial for large organizations with complex network architectures. By implementing internal firewalls, you not only bolster security but also enhance compliance with industry regulations that mandate strict data protection measures.
DMZ Firewalls: A Safe Zone for External Access
A demilitarized zone (DMZ) acts as a buffer zone between the internal network and untrusted external networks. Placing a firewall between the DMZ and the internal network is crucial for securing web servers, email servers, and other public-facing applications. The DMZ firewall allows external users to access these services without providing them access to the internal network, thereby safeguarding sensitive data.
DMZ firewalls are essential for organizations that host services accessible to external users, such as e-commerce platforms. They help in isolating potential threats and protecting the internal network from vulnerabilities that might be exploited via public-facing applications.
Cloud-Based Firewalls: Extending Security Beyond Physical Boundaries
With the rise of cloud computing, the need for cloud-based firewalls has increased. These firewalls are designed to protect cloud-hosted applications and data. They provide capabilities such as traffic inspection, threat prevention, and application control, essential for maintaining security in cloud environments.
Placing firewalls in the cloud requires a strategic approach that considers the shared responsibility model of cloud security. Organizations must ensure that their cloud provider's security measures are complemented by their own firewall configurations to achieve a robust security posture.
Virtual Firewalls: Protecting Virtual Environments
As organizations increasingly deploy virtual machines and containers, virtual firewalls have become indispensable. Virtual firewalls offer protection for virtual environments, securing traffic between virtual machines and containers. They are scalable and flexible, making them ideal for dynamic environments where traffic patterns can change rapidly.
Strategically placing virtual firewalls within virtual networks ensures that security policies are consistently enforced, regardless of where virtual assets are deployed. This placement is particularly important in hybrid cloud environments where virtual and physical resources coexist.
Conclusion: The Importance of a Layered Approach
In the ever-changing landscape of network security, a single firewall placement strategy is often insufficient. Organizations must adopt a layered approach, utilizing perimeter, internal, DMZ, cloud-based, and virtual firewalls to create a comprehensive security framework. Such a strategy not only protects against external threats but also mitigates risks within the network.
By carefully considering where to place firewalls and how to tailor their configurations, organizations can ensure that their networks remain resilient against a wide array of threats. Ultimately, the goal is to build a secure network environment that supports organizational objectives while safeguarding critical data and assets.
Unlock Next-Gen Innovation in Communication Technology with Patsnap Eureka
The field of communication technology is evolving at breakneck speed—from 5G and satellite systems to next-gen wireless protocols and quantum communications. Staying ahead demands more than just information—it requires strategic insights, real-time patent intelligence, and a deep understanding of technological trajectories.
Patsnap Eureka, our intelligent AI assistant built for R&D professionals in high-tech sectors, empowers you with real-time expert-level analysis, technology roadmap exploration, and strategic mapping of core patents—all within a seamless, user-friendly interface. Whether you're optimizing signal processing designs, navigating 3GPP standards, or exploring IP strategies for IoT and 6G networks, Eureka helps you move faster, think deeper, and innovate smarter.
Try Patsnap Eureka today—and see how it can transform the way you work across the entire communication technology innovation lifecycle.
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com