What is TLS Handshake? The Cryptography Behind Secure Web Browsing (RSA vs. ECC Keys)
JUN 26, 2025 |
The Transport Layer Security (TLS) protocol is fundamental to securing communications over the internet. At the heart of this process is the TLS handshake, a cryptographic exchange that establishes a secure connection between a client and a server. This handshake is responsible for negotiating parameters, authenticating parties, and agreeing on encryption keys, all of which are critical to maintaining confidentiality and integrity in web communications.
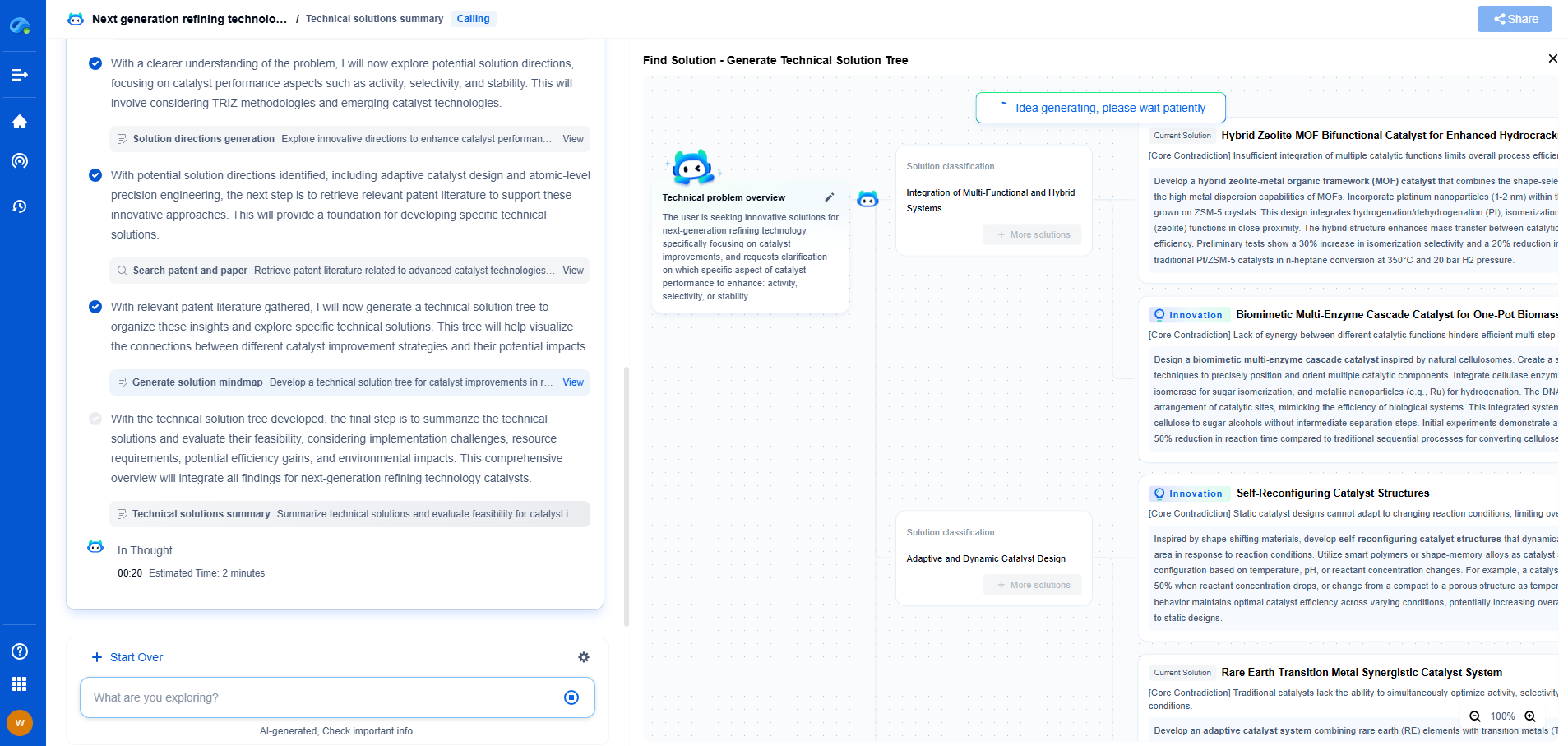
The TLS Handshake Process
The TLS handshake involves several steps that ensure a secure and encrypted connection. It begins when a client, such as a web browser, connects to a server, such as a website, and both parties agree on the security parameters to use throughout their interaction. This negotiation involves:
1. **ClientHello**: The client initiates the handshake by sending a "ClientHello" message, which includes the TLS version it supports, cipher suites, and supported compression methods.
2. **ServerHello**: The server responds with a "ServerHello" message, selecting the TLS version, cipher suite, and compression method from the client's list. Additionally, the server provides its digital certificate, which includes its public key.
3. **Authentication and Pre-Master Secret**: The client authenticates the server's identity through its digital certificate. If valid, the client generates a pre-master secret, which is then encrypted with the server's public key and sent to the server.
4. **Session Keys Generation**: Both server and client use the pre-master secret, along with random values exchanged in the hello messages, to compute a shared session key. This key will encrypt subsequent data, ensuring privacy and integrity.
5. **Finished Messages**: Both parties send a "Finished" message, encrypted with the session key, confirming the handshake's success. If there are no errors, the secure connection is established.
Cryptography Behind TLS: RSA vs. ECC
A pivotal aspect of the TLS handshake is the choice of encryption algorithms, with RSA (Rivest-Shamir-Adleman) and ECC (Elliptic Curve Cryptography) being the most prevalent.
RSA Encryption
RSA, developed in 1977, is a public-key cryptographic system that relies on the mathematical properties of large prime numbers. Its security is based on the difficulty of factoring the product of two large primes, a task that is computationally demanding. One of RSA's primary advantages is its widespread adoption and maturity. However, it requires larger key sizes (often 2048 bits or more) to maintain a high security level, which can lead to slower performance during the handshake.
ECC Encryption
ECC, introduced in the 1980s, offers the same level of security as RSA but with significantly smaller key sizes. For instance, an ECC key of 256 bits provides comparable security to a 3072-bit RSA key. This efficiency results from ECC's ability to leverage the algebraic structure of elliptic curves over finite fields, which allows for faster computations and reduced computational load during the TLS handshake.
Comparing RSA and ECC in TLS
When comparing RSA and ECC in the context of the TLS handshake, several factors come into play:
1. **Performance**: ECC's smaller key sizes lead to faster computations, reducing the handshake time and improving overall performance, particularly on mobile devices where processing power and battery life are crucial.
2. **Security**: Both RSA and ECC offer robust security. However, ECC's design allows it to remain secure against potential future threats, such as advances in quantum computing, which could undermine RSA's security due to its reliance on integer factorization.
3. **Implementation Complexity**: While ECC provides performance benefits, its mathematical complexity can make it more challenging to implement correctly, which may lead to vulnerabilities if not handled with care.
Conclusion
The TLS handshake is a cornerstone of secure web browsing, ensuring that data exchanged between clients and servers remains private and untampered. By understanding the cryptographic underpinnings, particularly the roles of RSA and ECC, one can appreciate the delicate balance between performance, security, and complexity that drives the evolution of internet protocols. As the digital landscape continues to evolve, the choice between RSA and ECC will remain pivotal in shaping the future of secure communications.
Unleash the Full Potential of AI Innovation with Patsnap Eureka
The frontier of machine learning evolves faster than ever—from foundation models and neuromorphic computing to edge AI and self-supervised learning. Whether you're exploring novel architectures, optimizing inference at scale, or tracking patent landscapes in generative AI, staying ahead demands more than human bandwidth.
Patsnap Eureka, our intelligent AI assistant built for R&D professionals in high-tech sectors, empowers you with real-time expert-level analysis, technology roadmap exploration, and strategic mapping of core patents—all within a seamless, user-friendly interface.
👉 Try Patsnap Eureka today to accelerate your journey from ML ideas to IP assets—request a personalized demo or activate your trial now.
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com