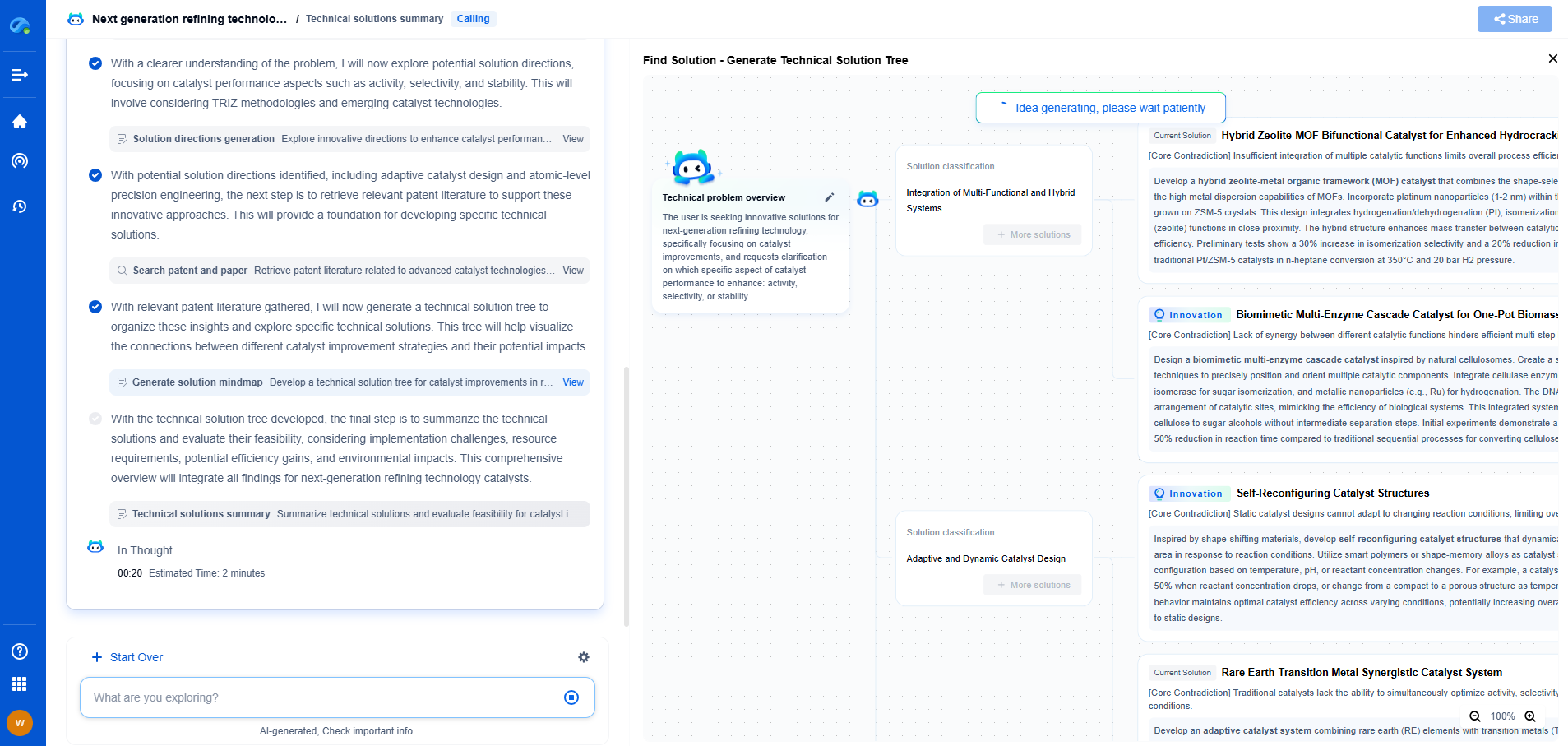
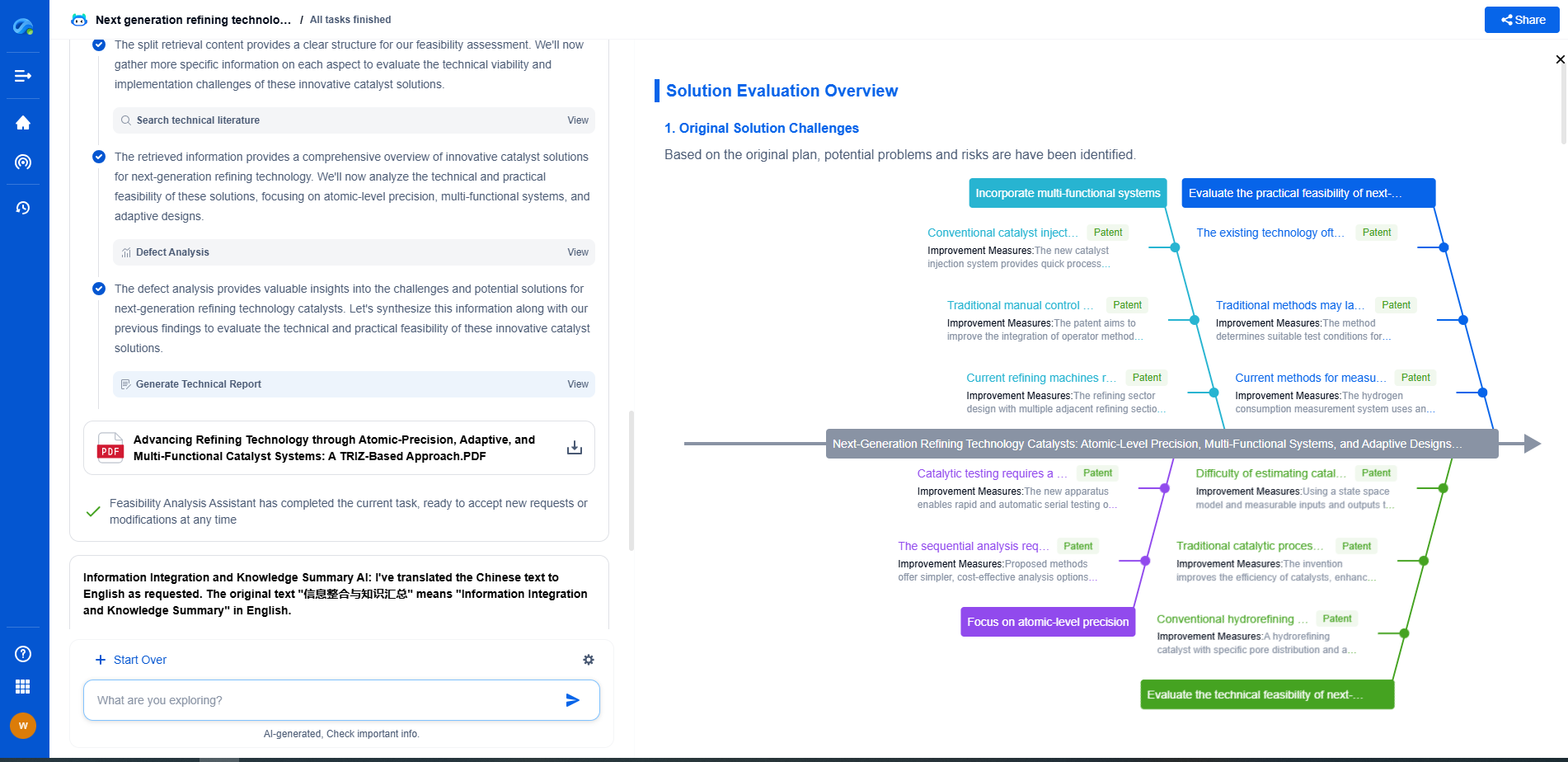
Zero Trust Architecture (ZTA): Redesigning Networks for Security
JUN 27, 2025 |
In an era where cyber threats are becoming increasingly sophisticated and pervasive, traditional network security models are proving insufficient. The Zero Trust Architecture (ZTA) emerges as a transformative approach, challenging the conventional “trust but verify” stance by implementing a more rigorous “never trust, always verify” ideology. This paradigm shift ensures that organizations maintain a robust security posture, even as their network boundaries blur with the adoption of cloud services, mobile devices, and remote work.
The Core Principles of Zero Trust
At its heart, Zero Trust is built on several foundational principles. Firstly, it assumes that threats could be both external and internal. Therefore, no entity, whether inside or outside the network perimeter, is automatically trusted. Verification is required at every step, regardless of the source or location of the request.
Secondly, ZTA emphasizes the principle of least privilege. Users and devices are given only the access necessary to perform their tasks, reducing the potential attack surface. This minimizes the risk of lateral movement within the network, should an attacker gain entry.
Lastly, continuous monitoring and validation are key. Unlike traditional models that authenticate users at the point of login, Zero Trust requires ongoing verification of user identity, device health, and application behavior throughout the session.
Implementing Zero Trust Architecture
Transitioning to a Zero Trust model involves a series of strategic steps that must be carefully tailored to an organization’s specific needs. The process typically begins with a comprehensive assessment of the existing network environment to identify assets, users, and traffic flows. Understanding what needs protection and how users interact with data is crucial in designing an effective Zero Trust strategy.
Next, organizations should implement micro-segmentation to create small, isolated zones within the network. Micro-segmentation allows for precise control over traffic between segments, ensuring that even if a breach occurs in one segment, it cannot easily spread throughout the entire network.
Identity and access management (IAM) systems play a critical role in ZTA. Implementing multi-factor authentication (MFA) and implementing stringent identity verification processes can significantly reduce unauthorized access risks. Additionally, employing adaptive access controls that consider user behavior and context can enhance security without hampering user experience.
The Role of Technology in Zero Trust
Technology is a crucial enabler of Zero Trust Architecture. Solutions such as advanced threat protection, data loss prevention, and endpoint detection and response are integral to maintaining security in a Zero Trust environment. These technologies provide the necessary tools to monitor, detect, and respond to potential threats in real-time.
Cloud-based services can further enhance a Zero Trust strategy by providing scalable and flexible security solutions. Cloud providers often offer integrated security features, such as identity and access management and encryption, that align with Zero Trust principles. Leveraging these tools can help organizations implement a consistent security framework across both on-premises and cloud environments.
Challenges and Considerations
While the benefits of Zero Trust are compelling, the transition to such a model is not without challenges. One significant hurdle is the complexity of implementing Zero Trust in legacy systems and networks. Organizations must carefully plan the migration process to minimize disruption and ensure compatibility with existing infrastructure.
Another consideration is the potential impact on user experience. Excessive security measures can lead to frustration and decreased productivity if not properly balanced. Therefore, it is vital to design Zero Trust solutions that maintain robust security while offering seamless user interaction.
Conclusion: Embracing a Secure Future
Zero Trust Architecture represents a significant shift in how organizations perceive and manage network security. By adopting a "never trust, always verify" stance, businesses can effectively safeguard their digital assets against evolving threats. As cyber risks continue to rise, Zero Trust provides a proactive approach to security, ensuring that organizations are well-equipped to protect their networks and data in an increasingly connected world. Embracing this architecture is not merely a technological upgrade but a strategic move towards a more secure and resilient future.
Unlock Next-Gen Innovation in Communication Technology with Patsnap Eureka
The field of communication technology is evolving at breakneck speed—from 5G and satellite systems to next-gen wireless protocols and quantum communications. Staying ahead demands more than just information—it requires strategic insights, real-time patent intelligence, and a deep understanding of technological trajectories.
Patsnap Eureka, our intelligent AI assistant built for R&D professionals in high-tech sectors, empowers you with real-time expert-level analysis, technology roadmap exploration, and strategic mapping of core patents—all within a seamless, user-friendly interface. Whether you're optimizing signal processing designs, navigating 3GPP standards, or exploring IP strategies for IoT and 6G networks, Eureka helps you move faster, think deeper, and innovate smarter.
Try Patsnap Eureka today—and see how it can transform the way you work across the entire communication technology innovation lifecycle.
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com