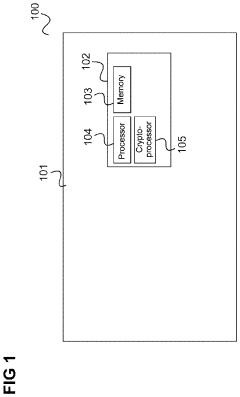
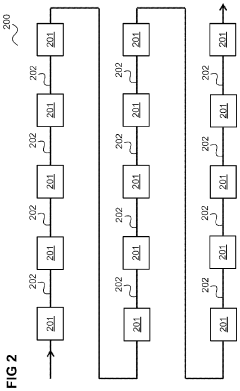
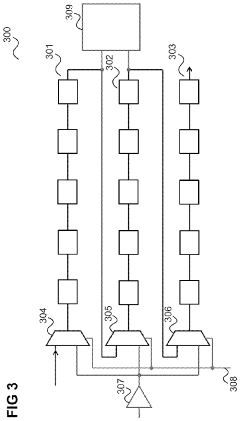
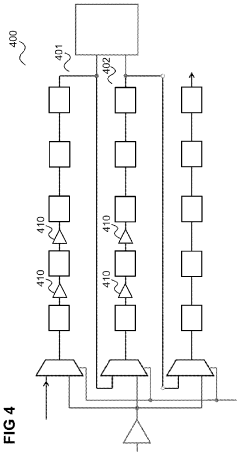
Advancements in Multiplexer Design for Enhanced Security
JUL 13, 20259 MIN READ
Generate Your Research Report Instantly with AI Agent
Patsnap Eureka helps you evaluate technical feasibility & market potential.
Multiplexer Security Evolution and Objectives
Multiplexers have played a crucial role in telecommunications and data transmission for decades. Their evolution in terms of security features has been driven by the increasing need to protect sensitive information in an interconnected world. The journey of multiplexer security began with simple time-division multiplexing (TDM) systems, which offered basic data separation but lacked robust security measures.
As cyber threats became more sophisticated, the focus shifted towards developing multiplexers with enhanced security capabilities. This evolution saw the integration of encryption algorithms directly into multiplexer hardware, marking a significant milestone in secure data transmission. The advent of quantum key distribution (QKD) further revolutionized multiplexer security, offering theoretically unbreakable encryption based on quantum mechanical principles.
Recent advancements have led to the development of software-defined networking (SDN) enabled multiplexers, which provide dynamic security policy enforcement and real-time threat response. These intelligent systems can adapt to changing security landscapes, offering a more resilient defense against evolving cyber attacks.
The primary objectives of modern multiplexer security design are multifaceted. Firstly, there is a strong emphasis on achieving end-to-end encryption without compromising data throughput or introducing significant latency. This requires innovative approaches to hardware acceleration and efficient cryptographic implementations.
Secondly, multiplexer designers aim to enhance the resilience of these devices against side-channel attacks, which exploit physical characteristics of the hardware to extract sensitive information. This has led to the development of tamper-resistant packaging and the implementation of power analysis countermeasures.
Another critical objective is to ensure the scalability of security features in high-capacity multiplexers. As data rates continue to increase, maintaining robust security measures without bottlenecking performance remains a significant challenge. Researchers are exploring parallel processing techniques and dedicated security co-processors to address this issue.
Interoperability is also a key focus, as multiplexers must seamlessly integrate with existing network infrastructure while maintaining stringent security standards. This has driven efforts to develop standardized security protocols and interfaces that can be universally adopted across different multiplexer platforms.
Looking ahead, the future of multiplexer security is likely to involve artificial intelligence and machine learning algorithms for predictive threat detection and autonomous security management. These advancements aim to create self-healing networks capable of identifying and mitigating security breaches in real-time, further enhancing the robustness of data transmission infrastructure.
As cyber threats became more sophisticated, the focus shifted towards developing multiplexers with enhanced security capabilities. This evolution saw the integration of encryption algorithms directly into multiplexer hardware, marking a significant milestone in secure data transmission. The advent of quantum key distribution (QKD) further revolutionized multiplexer security, offering theoretically unbreakable encryption based on quantum mechanical principles.
Recent advancements have led to the development of software-defined networking (SDN) enabled multiplexers, which provide dynamic security policy enforcement and real-time threat response. These intelligent systems can adapt to changing security landscapes, offering a more resilient defense against evolving cyber attacks.
The primary objectives of modern multiplexer security design are multifaceted. Firstly, there is a strong emphasis on achieving end-to-end encryption without compromising data throughput or introducing significant latency. This requires innovative approaches to hardware acceleration and efficient cryptographic implementations.
Secondly, multiplexer designers aim to enhance the resilience of these devices against side-channel attacks, which exploit physical characteristics of the hardware to extract sensitive information. This has led to the development of tamper-resistant packaging and the implementation of power analysis countermeasures.
Another critical objective is to ensure the scalability of security features in high-capacity multiplexers. As data rates continue to increase, maintaining robust security measures without bottlenecking performance remains a significant challenge. Researchers are exploring parallel processing techniques and dedicated security co-processors to address this issue.
Interoperability is also a key focus, as multiplexers must seamlessly integrate with existing network infrastructure while maintaining stringent security standards. This has driven efforts to develop standardized security protocols and interfaces that can be universally adopted across different multiplexer platforms.
Looking ahead, the future of multiplexer security is likely to involve artificial intelligence and machine learning algorithms for predictive threat detection and autonomous security management. These advancements aim to create self-healing networks capable of identifying and mitigating security breaches in real-time, further enhancing the robustness of data transmission infrastructure.
Market Demand for Secure Multiplexing Solutions
The market demand for secure multiplexing solutions has been experiencing significant growth in recent years, driven by the increasing need for data protection and privacy across various industries. As digital transformation accelerates and more organizations rely on interconnected systems, the importance of secure data transmission has become paramount.
In the telecommunications sector, the demand for secure multiplexers is particularly high. With the rollout of 5G networks and the expansion of fiber-optic infrastructure, service providers are seeking advanced multiplexing solutions that can handle higher data rates while maintaining robust security measures. This trend is expected to continue as 6G technology development progresses, further emphasizing the need for enhanced security in multiplexer designs.
The financial services industry is another key driver of demand for secure multiplexing solutions. Banks, payment processors, and other financial institutions require highly secure data transmission to protect sensitive customer information and prevent fraud. The increasing frequency and sophistication of cyber attacks have led to stricter regulatory requirements, compelling organizations to invest in advanced security technologies, including secure multiplexers.
In the healthcare sector, the growing adoption of telemedicine and electronic health records has created a substantial market for secure data transmission solutions. Healthcare providers must ensure patient data confidentiality while enabling efficient information sharing among different facilities and practitioners. Secure multiplexers play a crucial role in meeting these requirements, contributing to the sector's increasing demand.
The Internet of Things (IoT) and smart city initiatives are also fueling the demand for secure multiplexing solutions. As more devices become interconnected, the volume of data being transmitted across networks is expanding exponentially. This growth necessitates efficient and secure multiplexing technologies to manage the increased data flow while protecting against potential security breaches.
Government and defense sectors represent another significant market for secure multiplexers. These organizations handle highly sensitive information and require advanced encryption and secure transmission capabilities. The ongoing modernization of military communication systems and the increasing focus on cybersecurity in government operations are driving substantial investments in secure multiplexing technologies.
Market analysts project that the global secure multiplexer market will continue to grow at a compound annual growth rate (CAGR) of over 8% in the coming years. This growth is attributed to the increasing awareness of cybersecurity threats, the rising adoption of cloud computing, and the ongoing digital transformation across industries.
In the telecommunications sector, the demand for secure multiplexers is particularly high. With the rollout of 5G networks and the expansion of fiber-optic infrastructure, service providers are seeking advanced multiplexing solutions that can handle higher data rates while maintaining robust security measures. This trend is expected to continue as 6G technology development progresses, further emphasizing the need for enhanced security in multiplexer designs.
The financial services industry is another key driver of demand for secure multiplexing solutions. Banks, payment processors, and other financial institutions require highly secure data transmission to protect sensitive customer information and prevent fraud. The increasing frequency and sophistication of cyber attacks have led to stricter regulatory requirements, compelling organizations to invest in advanced security technologies, including secure multiplexers.
In the healthcare sector, the growing adoption of telemedicine and electronic health records has created a substantial market for secure data transmission solutions. Healthcare providers must ensure patient data confidentiality while enabling efficient information sharing among different facilities and practitioners. Secure multiplexers play a crucial role in meeting these requirements, contributing to the sector's increasing demand.
The Internet of Things (IoT) and smart city initiatives are also fueling the demand for secure multiplexing solutions. As more devices become interconnected, the volume of data being transmitted across networks is expanding exponentially. This growth necessitates efficient and secure multiplexing technologies to manage the increased data flow while protecting against potential security breaches.
Government and defense sectors represent another significant market for secure multiplexers. These organizations handle highly sensitive information and require advanced encryption and secure transmission capabilities. The ongoing modernization of military communication systems and the increasing focus on cybersecurity in government operations are driving substantial investments in secure multiplexing technologies.
Market analysts project that the global secure multiplexer market will continue to grow at a compound annual growth rate (CAGR) of over 8% in the coming years. This growth is attributed to the increasing awareness of cybersecurity threats, the rising adoption of cloud computing, and the ongoing digital transformation across industries.
Current Challenges in Multiplexer Security
Multiplexers play a crucial role in modern communication systems, but their security vulnerabilities have become increasingly apparent in recent years. One of the primary challenges facing multiplexer security is the susceptibility to side-channel attacks. These attacks exploit unintended information leakage through power consumption, electromagnetic emissions, or timing variations, potentially compromising sensitive data transmitted through the multiplexer.
Another significant challenge is the vulnerability to physical tampering. As multiplexers are often deployed in accessible locations, they are susceptible to unauthorized physical access, which could lead to data interception or manipulation. Developing tamper-resistant designs and implementing robust physical security measures remain ongoing challenges for multiplexer manufacturers and system integrators.
The increasing complexity of multiplexer architectures also presents security challenges. As multiplexers evolve to handle higher data rates and more complex signal processing, the potential attack surface expands. This complexity makes it difficult to thoroughly analyze and secure all potential vulnerabilities, leaving room for unforeseen security weaknesses.
Encryption implementation in multiplexers is another area of concern. While encryption is essential for securing data transmission, integrating robust encryption algorithms into multiplexer designs without compromising performance or introducing latency is a significant challenge. Balancing security with efficiency remains a key focus for multiplexer designers.
The rapid evolution of quantum computing poses a long-term threat to current cryptographic methods used in multiplexer security. As quantum computers become more powerful, they may be able to break traditional encryption algorithms, necessitating the development of quantum-resistant security measures for multiplexers.
Standardization and interoperability issues also present challenges in multiplexer security. With various proprietary security implementations across different manufacturers, ensuring seamless and secure communication between multiplexers from different vendors can be problematic. Establishing industry-wide security standards while allowing for innovation remains a delicate balance.
Lastly, the growing threat of sophisticated cyber attacks targeting critical infrastructure, including communication networks, puts increased pressure on multiplexer security. Defending against advanced persistent threats and zero-day vulnerabilities requires constant vigilance and rapid response capabilities, challenging the traditional approach to multiplexer design and security implementation.
Another significant challenge is the vulnerability to physical tampering. As multiplexers are often deployed in accessible locations, they are susceptible to unauthorized physical access, which could lead to data interception or manipulation. Developing tamper-resistant designs and implementing robust physical security measures remain ongoing challenges for multiplexer manufacturers and system integrators.
The increasing complexity of multiplexer architectures also presents security challenges. As multiplexers evolve to handle higher data rates and more complex signal processing, the potential attack surface expands. This complexity makes it difficult to thoroughly analyze and secure all potential vulnerabilities, leaving room for unforeseen security weaknesses.
Encryption implementation in multiplexers is another area of concern. While encryption is essential for securing data transmission, integrating robust encryption algorithms into multiplexer designs without compromising performance or introducing latency is a significant challenge. Balancing security with efficiency remains a key focus for multiplexer designers.
The rapid evolution of quantum computing poses a long-term threat to current cryptographic methods used in multiplexer security. As quantum computers become more powerful, they may be able to break traditional encryption algorithms, necessitating the development of quantum-resistant security measures for multiplexers.
Standardization and interoperability issues also present challenges in multiplexer security. With various proprietary security implementations across different manufacturers, ensuring seamless and secure communication between multiplexers from different vendors can be problematic. Establishing industry-wide security standards while allowing for innovation remains a delicate balance.
Lastly, the growing threat of sophisticated cyber attacks targeting critical infrastructure, including communication networks, puts increased pressure on multiplexer security. Defending against advanced persistent threats and zero-day vulnerabilities requires constant vigilance and rapid response capabilities, challenging the traditional approach to multiplexer design and security implementation.
Existing Secure Multiplexer Architectures
01 Secure multiplexing in optical networks
Implementing secure multiplexing techniques in optical networks to enhance data transmission security. This involves using advanced encryption methods and secure protocols to protect multiplexed signals from unauthorized access or interception.- Secure multiplexing in optical networks: This approach focuses on enhancing security in optical network multiplexers. It involves techniques for secure data transmission, encryption methods, and protection against eavesdropping in multiplexed optical signals. These solutions aim to safeguard sensitive information transmitted through optical networks.
- Multiplexer security in wireless communication systems: This category addresses security measures for multiplexers in wireless communication systems. It includes methods for secure signal processing, authentication protocols, and protection against unauthorized access or interference in wireless multiplexing environments. These techniques aim to enhance the overall security of wireless communication networks.
- Hardware-based security for multiplexers: This approach involves implementing security features directly in multiplexer hardware. It includes tamper-resistant designs, secure key storage, and hardware-based encryption modules. These hardware solutions aim to provide a robust security foundation for multiplexer operations.
- Secure multiplexing protocols and algorithms: This category focuses on developing and implementing secure multiplexing protocols and algorithms. It includes advanced encryption techniques, secure channel allocation methods, and robust error detection and correction mechanisms. These protocols aim to ensure the integrity and confidentiality of multiplexed data.
- Multiplexer security in video surveillance systems: This approach addresses security concerns in multiplexers used for video surveillance applications. It includes methods for secure video signal processing, encryption of multiplexed video streams, and protection against unauthorized access to surveillance data. These solutions aim to enhance the security and privacy of video surveillance systems.
02 Encryption-based multiplexer security
Incorporating encryption algorithms directly into multiplexer designs to ensure data security at the hardware level. This approach involves integrating cryptographic modules within the multiplexer circuitry to encrypt and decrypt data streams in real-time.Expand Specific Solutions03 Secure multiplexing for wireless communication
Developing secure multiplexing techniques specifically for wireless communication systems. This includes implementing robust authentication mechanisms and secure channel allocation to prevent unauthorized access and ensure the integrity of multiplexed wireless signals.Expand Specific Solutions04 Physical layer security for multiplexers
Enhancing multiplexer security at the physical layer by implementing tamper-resistant designs and secure hardware modules. This approach focuses on preventing physical attacks and unauthorized modifications to the multiplexer hardware.Expand Specific Solutions05 Secure time-division multiplexing
Implementing secure time-division multiplexing techniques to protect against timing-based attacks and ensure the confidentiality of time-sensitive data. This involves developing advanced scheduling algorithms and secure synchronization methods for multiplexed signals.Expand Specific Solutions
Key Players in Secure Multiplexer Industry
The advancements in multiplexer design for enhanced security are at a critical juncture, with the market showing significant growth potential. The industry is in a transitional phase, moving from traditional designs to more sophisticated, security-focused solutions. Key players like Infineon Technologies, NXP Semiconductors, and Huawei Technologies are driving innovation, leveraging their expertise in semiconductor and communication technologies. The market is experiencing rapid expansion due to increasing demand for secure data transmission in various sectors. While established companies are refining existing technologies, emerging firms like Beijing Duosi Security Chip Technology are introducing novel approaches, indicating a moderate level of technological maturity with room for further advancements.
Infineon Technologies AG
Technical Solution: Infineon has developed advanced multiplexer designs for enhanced security, focusing on hardware-based security solutions. Their approach integrates secure elements and trusted platform modules (TPMs) into multiplexer architectures. This integration allows for hardware-level encryption, secure key storage, and tamper-resistant operations [1]. Infineon's multiplexers incorporate side-channel attack resistance and physical security measures, ensuring data integrity and confidentiality even in hostile environments [3]. The company has also implemented dynamic reconfiguration capabilities in their multiplexers, allowing for real-time adaptation to emerging security threats [5].
Strengths: Strong hardware-based security, integration with existing security elements, and adaptability to new threats. Weaknesses: Potentially higher cost and complexity compared to software-based solutions, and may require specialized knowledge for implementation.
Altera Corp.
Technical Solution: Altera, now part of Intel, has developed advanced multiplexer designs focusing on FPGA-based security solutions. Their approach leverages the flexibility of FPGAs to create adaptable and secure multiplexer architectures. Altera's designs incorporate hardened security IP cores, including AES encryption engines and secure key management systems, directly into the FPGA fabric [13]. The company has also implemented anti-tamper technologies, such as bitstream encryption and authentication, to prevent unauthorized modification or reverse engineering of multiplexer configurations [14]. Additionally, Altera's multiplexers feature dynamic partial reconfiguration capabilities, allowing for real-time security updates without system downtime [15].
Strengths: High flexibility and customization potential, strong protection against physical attacks, and ability to update security features in real-time. Weaknesses: May require specialized FPGA programming skills, and potentially higher initial costs compared to ASIC solutions.
Innovative Encryption Techniques for Multiplexers
Integrated Circuit and Method for Protecting an Integrated Circuit Against Reverse Engineering
PatentPendingUS20230153472A1
Innovation
- The integration of a bit generation circuit using existing signal chains and arbiter circuits to generate secret bits based on propagation time differences between signal chains, allowing for secure operation without additional gate expenditure and masking the secret generation process.
Method for building a security image by multiplexing color images
PatentWO2019170679A1
Innovation
- A method for constructing security images by multiplexing color images using a marking technique that selects and combines sets of colors based on illumination and observation modes, optimizing the number of displayable images without requiring spatial filtering systems, and using laser structuring of metal nanoparticles to create hypercolors that change appearance depending on conditions.
Regulatory Compliance for Secure Multiplexers
Regulatory compliance for secure multiplexers has become increasingly critical in the evolving landscape of cybersecurity and data protection. As multiplexers play a vital role in routing and managing data flows within communication systems, ensuring their security and adherence to regulatory standards is paramount.
The regulatory framework for secure multiplexers encompasses a wide range of standards and guidelines. These include the General Data Protection Regulation (GDPR) in the European Union, which sets strict requirements for data protection and privacy. In the United States, the Federal Information Security Management Act (FISMA) and the National Institute of Standards and Technology (NIST) guidelines provide comprehensive security standards for federal information systems.
Compliance with these regulations often requires multiplexer manufacturers to implement robust security features. These may include encryption capabilities, access control mechanisms, and audit logging functionalities. Additionally, secure multiplexers must often undergo rigorous testing and certification processes to demonstrate their compliance with industry standards such as Common Criteria or FIPS 140-2.
The telecommunications sector, in particular, faces stringent regulatory requirements for secure multiplexers. The International Telecommunication Union (ITU) provides recommendations for secure network equipment, including multiplexers, which are widely adopted by national regulatory bodies. These recommendations often cover aspects such as physical security, cryptographic protocols, and secure management interfaces.
In the financial services industry, regulations like the Payment Card Industry Data Security Standard (PCI DSS) impose strict requirements on the security of data transmission systems, including multiplexers used in payment processing networks. Compliance with these standards often necessitates advanced security features and regular security audits.
As the threat landscape continues to evolve, regulatory bodies are constantly updating their requirements for secure multiplexers. This dynamic environment challenges manufacturers to stay ahead of emerging threats and adapt their designs to meet new compliance standards. The trend towards software-defined networking (SDN) and network function virtualization (NFV) is also influencing regulatory approaches, as these technologies introduce new security considerations for multiplexer design and deployment.
Regulatory compliance for secure multiplexers extends beyond technical specifications to encompass organizational processes and policies. Manufacturers and operators of secure multiplexers must often implement comprehensive security management systems, including incident response plans, regular vulnerability assessments, and employee training programs.
The regulatory framework for secure multiplexers encompasses a wide range of standards and guidelines. These include the General Data Protection Regulation (GDPR) in the European Union, which sets strict requirements for data protection and privacy. In the United States, the Federal Information Security Management Act (FISMA) and the National Institute of Standards and Technology (NIST) guidelines provide comprehensive security standards for federal information systems.
Compliance with these regulations often requires multiplexer manufacturers to implement robust security features. These may include encryption capabilities, access control mechanisms, and audit logging functionalities. Additionally, secure multiplexers must often undergo rigorous testing and certification processes to demonstrate their compliance with industry standards such as Common Criteria or FIPS 140-2.
The telecommunications sector, in particular, faces stringent regulatory requirements for secure multiplexers. The International Telecommunication Union (ITU) provides recommendations for secure network equipment, including multiplexers, which are widely adopted by national regulatory bodies. These recommendations often cover aspects such as physical security, cryptographic protocols, and secure management interfaces.
In the financial services industry, regulations like the Payment Card Industry Data Security Standard (PCI DSS) impose strict requirements on the security of data transmission systems, including multiplexers used in payment processing networks. Compliance with these standards often necessitates advanced security features and regular security audits.
As the threat landscape continues to evolve, regulatory bodies are constantly updating their requirements for secure multiplexers. This dynamic environment challenges manufacturers to stay ahead of emerging threats and adapt their designs to meet new compliance standards. The trend towards software-defined networking (SDN) and network function virtualization (NFV) is also influencing regulatory approaches, as these technologies introduce new security considerations for multiplexer design and deployment.
Regulatory compliance for secure multiplexers extends beyond technical specifications to encompass organizational processes and policies. Manufacturers and operators of secure multiplexers must often implement comprehensive security management systems, including incident response plans, regular vulnerability assessments, and employee training programs.
Performance Impact of Security Enhancements
The integration of advanced security features in multiplexer designs inevitably impacts system performance. This trade-off between security and performance is a critical consideration in the development of secure multiplexer architectures. The performance impact can be observed in various aspects of multiplexer operation, including throughput, latency, and power consumption.
One of the primary performance concerns is the reduction in data throughput. Security enhancements often involve additional processing steps, such as encryption, authentication, or integrity checks. These operations introduce computational overhead, which can slow down the multiplexing process. For instance, implementing robust encryption algorithms may require multiple clock cycles per data packet, reducing the overall throughput of the multiplexer.
Latency is another key performance metric affected by security enhancements. The additional processing time required for security operations can introduce delays in data transmission. This increased latency can be particularly problematic in time-sensitive applications, such as real-time communication systems or high-frequency trading platforms. Designers must carefully balance the level of security with acceptable latency thresholds for specific use cases.
Power consumption is also significantly impacted by security enhancements. The additional computational requirements for security operations typically lead to increased power draw. This can be a critical concern in battery-powered devices or energy-efficient systems. Moreover, the heat generated from increased power consumption may necessitate more robust cooling solutions, further complicating the design process.
However, it's important to note that the performance impact of security enhancements can vary depending on the specific implementation and the chosen security measures. Some modern approaches aim to minimize performance degradation through hardware acceleration of security functions. For example, dedicated cryptographic co-processors can offload security operations from the main multiplexer logic, reducing the performance overhead.
Furthermore, advancements in algorithm efficiency and implementation techniques have led to more optimized security solutions. Lightweight cryptographic algorithms, for instance, are designed to provide adequate security with minimal computational requirements, making them suitable for resource-constrained environments.
The choice of security protocols and their implementation can also significantly influence performance impact. For example, selective encryption techniques that only secure critical data portions can reduce the overall performance overhead compared to full data encryption. Similarly, adaptive security mechanisms that adjust the level of protection based on the perceived threat level can help balance security and performance dynamically.
In conclusion, while security enhancements in multiplexer design inevitably affect performance, the extent of this impact can be managed through careful design choices and innovative implementation strategies. As the field continues to evolve, researchers and engineers strive to develop solutions that provide robust security with minimal performance penalties, ensuring that secure multiplexers can meet the demanding requirements of modern communication systems.
One of the primary performance concerns is the reduction in data throughput. Security enhancements often involve additional processing steps, such as encryption, authentication, or integrity checks. These operations introduce computational overhead, which can slow down the multiplexing process. For instance, implementing robust encryption algorithms may require multiple clock cycles per data packet, reducing the overall throughput of the multiplexer.
Latency is another key performance metric affected by security enhancements. The additional processing time required for security operations can introduce delays in data transmission. This increased latency can be particularly problematic in time-sensitive applications, such as real-time communication systems or high-frequency trading platforms. Designers must carefully balance the level of security with acceptable latency thresholds for specific use cases.
Power consumption is also significantly impacted by security enhancements. The additional computational requirements for security operations typically lead to increased power draw. This can be a critical concern in battery-powered devices or energy-efficient systems. Moreover, the heat generated from increased power consumption may necessitate more robust cooling solutions, further complicating the design process.
However, it's important to note that the performance impact of security enhancements can vary depending on the specific implementation and the chosen security measures. Some modern approaches aim to minimize performance degradation through hardware acceleration of security functions. For example, dedicated cryptographic co-processors can offload security operations from the main multiplexer logic, reducing the performance overhead.
Furthermore, advancements in algorithm efficiency and implementation techniques have led to more optimized security solutions. Lightweight cryptographic algorithms, for instance, are designed to provide adequate security with minimal computational requirements, making them suitable for resource-constrained environments.
The choice of security protocols and their implementation can also significantly influence performance impact. For example, selective encryption techniques that only secure critical data portions can reduce the overall performance overhead compared to full data encryption. Similarly, adaptive security mechanisms that adjust the level of protection based on the perceived threat level can help balance security and performance dynamically.
In conclusion, while security enhancements in multiplexer design inevitably affect performance, the extent of this impact can be managed through careful design choices and innovative implementation strategies. As the field continues to evolve, researchers and engineers strive to develop solutions that provide robust security with minimal performance penalties, ensuring that secure multiplexers can meet the demanding requirements of modern communication systems.
Unlock deeper insights with Patsnap Eureka Quick Research — get a full tech report to explore trends and direct your research. Try now!
Generate Your Research Report Instantly with AI Agent
Supercharge your innovation with Patsnap Eureka AI Agent Platform!