How to Mitigate Security Risks in Electromagnetic Wave Networks?
JUL 11, 20259 MIN READ
Generate Your Research Report Instantly with AI Agent
Patsnap Eureka helps you evaluate technical feasibility & market potential.
EM Network Security Background and Objectives
Electromagnetic wave networks have become an integral part of modern communication systems, enabling wireless connectivity across various applications. However, the inherent nature of these networks exposes them to unique security challenges that require careful consideration and mitigation strategies. The primary objective of this technical research is to explore and develop effective methods to mitigate security risks in electromagnetic wave networks.
The evolution of electromagnetic wave technology has been marked by significant advancements in transmission efficiency, bandwidth utilization, and network architecture. From early radio communications to today's complex 5G networks, the field has witnessed a continuous push towards higher frequencies, wider bandwidths, and more sophisticated modulation techniques. This progression has led to increased data rates and improved connectivity but has also introduced new vulnerabilities that malicious actors can exploit.
As we delve into the security aspects of electromagnetic wave networks, it is crucial to understand the fundamental principles governing wave propagation, interference, and signal processing. These principles form the foundation upon which security measures are built and implemented. The interplay between physical layer characteristics and higher-level protocols presents both challenges and opportunities in securing these networks.
One of the key trends in electromagnetic wave network security is the shift towards a more holistic approach that combines physical layer security measures with cryptographic techniques and intelligent network management. This trend is driven by the recognition that traditional security methods alone are insufficient to address the unique challenges posed by the wireless medium.
The technical goals of this research encompass several key areas. Firstly, we aim to develop robust authentication mechanisms that can withstand sophisticated spoofing and impersonation attacks in electromagnetic wave environments. Secondly, we seek to enhance the confidentiality of transmitted data through advanced encryption techniques tailored for wireless channels. Thirdly, we strive to improve the integrity of communications by designing resilient error detection and correction methods that can operate effectively in the presence of both natural and artificial interference.
Furthermore, this research aims to address the emerging threats posed by quantum computing to electromagnetic wave network security. As quantum computers become more powerful, they have the potential to break many of the cryptographic systems currently used to secure these networks. Therefore, developing quantum-resistant security protocols for electromagnetic wave networks is a critical long-term objective of this study.
By comprehensively examining the technical background and setting clear objectives, this research lays the groundwork for developing innovative solutions to mitigate security risks in electromagnetic wave networks. The outcomes of this study will contribute to the creation of more secure and resilient wireless communication systems, capable of meeting the evolving demands of our increasingly connected world.
The evolution of electromagnetic wave technology has been marked by significant advancements in transmission efficiency, bandwidth utilization, and network architecture. From early radio communications to today's complex 5G networks, the field has witnessed a continuous push towards higher frequencies, wider bandwidths, and more sophisticated modulation techniques. This progression has led to increased data rates and improved connectivity but has also introduced new vulnerabilities that malicious actors can exploit.
As we delve into the security aspects of electromagnetic wave networks, it is crucial to understand the fundamental principles governing wave propagation, interference, and signal processing. These principles form the foundation upon which security measures are built and implemented. The interplay between physical layer characteristics and higher-level protocols presents both challenges and opportunities in securing these networks.
One of the key trends in electromagnetic wave network security is the shift towards a more holistic approach that combines physical layer security measures with cryptographic techniques and intelligent network management. This trend is driven by the recognition that traditional security methods alone are insufficient to address the unique challenges posed by the wireless medium.
The technical goals of this research encompass several key areas. Firstly, we aim to develop robust authentication mechanisms that can withstand sophisticated spoofing and impersonation attacks in electromagnetic wave environments. Secondly, we seek to enhance the confidentiality of transmitted data through advanced encryption techniques tailored for wireless channels. Thirdly, we strive to improve the integrity of communications by designing resilient error detection and correction methods that can operate effectively in the presence of both natural and artificial interference.
Furthermore, this research aims to address the emerging threats posed by quantum computing to electromagnetic wave network security. As quantum computers become more powerful, they have the potential to break many of the cryptographic systems currently used to secure these networks. Therefore, developing quantum-resistant security protocols for electromagnetic wave networks is a critical long-term objective of this study.
By comprehensively examining the technical background and setting clear objectives, this research lays the groundwork for developing innovative solutions to mitigate security risks in electromagnetic wave networks. The outcomes of this study will contribute to the creation of more secure and resilient wireless communication systems, capable of meeting the evolving demands of our increasingly connected world.
Market Demand for Secure EM Wave Communications
The market demand for secure electromagnetic wave communications has been growing exponentially in recent years, driven by the increasing reliance on wireless technologies across various sectors. As the world becomes more interconnected, the need for robust and secure communication systems has become paramount. Industries such as defense, healthcare, finance, and critical infrastructure are particularly sensitive to security risks in EM wave networks, creating a substantial market for advanced security solutions.
In the defense sector, secure EM wave communications are crucial for maintaining tactical advantages and protecting sensitive information. Military organizations worldwide are investing heavily in technologies that can safeguard their communications from interception, jamming, and spoofing attacks. This has led to a surge in demand for advanced encryption methods, frequency-hopping techniques, and anti-jamming systems.
The healthcare industry has also seen a significant increase in the adoption of wireless technologies for patient monitoring, telemedicine, and medical device connectivity. With the stringent privacy regulations surrounding patient data, there is a growing need for secure EM wave communication solutions that can protect sensitive medical information from unauthorized access or tampering.
Financial institutions are another major driver of market demand for secure EM wave communications. As mobile banking and contactless payment systems become more prevalent, the need for robust security measures to protect financial transactions and customer data has intensified. This has created a market for advanced authentication protocols and secure wireless payment technologies.
The Internet of Things (IoT) revolution has further amplified the demand for secure EM wave communications. As billions of devices become interconnected, the potential attack surface for malicious actors expands dramatically. This has led to increased investment in secure IoT protocols and communication standards that can protect vast networks of connected devices from cyber threats.
Critical infrastructure sectors, including energy, transportation, and utilities, are also driving market demand for secure EM wave communications. These industries rely heavily on wireless technologies for monitoring and control systems, making them prime targets for cyber attacks. The need to protect these vital systems from potential disruptions has created a significant market for specialized security solutions tailored to industrial control systems and SCADA networks.
As 5G networks continue to roll out globally, the demand for secure EM wave communications is expected to grow even further. The increased bandwidth and lower latency of 5G networks will enable new applications and use cases, many of which will require robust security measures to protect sensitive data and ensure the integrity of communications.
In the defense sector, secure EM wave communications are crucial for maintaining tactical advantages and protecting sensitive information. Military organizations worldwide are investing heavily in technologies that can safeguard their communications from interception, jamming, and spoofing attacks. This has led to a surge in demand for advanced encryption methods, frequency-hopping techniques, and anti-jamming systems.
The healthcare industry has also seen a significant increase in the adoption of wireless technologies for patient monitoring, telemedicine, and medical device connectivity. With the stringent privacy regulations surrounding patient data, there is a growing need for secure EM wave communication solutions that can protect sensitive medical information from unauthorized access or tampering.
Financial institutions are another major driver of market demand for secure EM wave communications. As mobile banking and contactless payment systems become more prevalent, the need for robust security measures to protect financial transactions and customer data has intensified. This has created a market for advanced authentication protocols and secure wireless payment technologies.
The Internet of Things (IoT) revolution has further amplified the demand for secure EM wave communications. As billions of devices become interconnected, the potential attack surface for malicious actors expands dramatically. This has led to increased investment in secure IoT protocols and communication standards that can protect vast networks of connected devices from cyber threats.
Critical infrastructure sectors, including energy, transportation, and utilities, are also driving market demand for secure EM wave communications. These industries rely heavily on wireless technologies for monitoring and control systems, making them prime targets for cyber attacks. The need to protect these vital systems from potential disruptions has created a significant market for specialized security solutions tailored to industrial control systems and SCADA networks.
As 5G networks continue to roll out globally, the demand for secure EM wave communications is expected to grow even further. The increased bandwidth and lower latency of 5G networks will enable new applications and use cases, many of which will require robust security measures to protect sensitive data and ensure the integrity of communications.
Current Challenges in EM Network Security
Electromagnetic wave networks face numerous security challenges in today's rapidly evolving technological landscape. One of the primary concerns is the vulnerability to eavesdropping and interception of sensitive data. Due to the nature of electromagnetic waves, which propagate through space, unauthorized parties can potentially intercept and decode transmitted information without physical access to the network infrastructure.
Another significant challenge is the susceptibility of EM networks to jamming and interference. Malicious actors can disrupt communication by flooding the network with high-power electromagnetic signals, effectively creating a denial-of-service scenario. This can have severe consequences in critical applications such as military communications, emergency services, or industrial control systems.
Authentication and access control pose additional security risks in EM networks. Ensuring that only authorized devices and users can connect to and communicate within the network is crucial. However, traditional authentication methods may not always be suitable or sufficient for the unique characteristics of electromagnetic wave-based systems.
The increasing prevalence of Internet of Things (IoT) devices and smart systems has expanded the attack surface for EM networks. Many of these devices have limited computational resources and may lack robust security features, making them potential entry points for attackers to compromise the entire network.
Electromagnetic side-channel attacks represent a growing concern. These attacks exploit unintentional electromagnetic emissions from electronic devices to extract sensitive information, such as encryption keys or confidential data. As devices become more compact and powerful, mitigating these side-channel vulnerabilities becomes increasingly challenging.
The dynamic nature of EM networks, particularly in mobile and ad-hoc scenarios, introduces additional security complexities. Maintaining secure connections and ensuring data integrity in environments with constantly changing network topologies and varying signal strengths requires sophisticated adaptive security mechanisms.
Lastly, the emergence of quantum computing poses a long-term threat to current encryption methods used in EM networks. As quantum computers become more powerful, they may be able to break widely used cryptographic algorithms, necessitating the development and implementation of quantum-resistant security protocols for electromagnetic wave communications.
Another significant challenge is the susceptibility of EM networks to jamming and interference. Malicious actors can disrupt communication by flooding the network with high-power electromagnetic signals, effectively creating a denial-of-service scenario. This can have severe consequences in critical applications such as military communications, emergency services, or industrial control systems.
Authentication and access control pose additional security risks in EM networks. Ensuring that only authorized devices and users can connect to and communicate within the network is crucial. However, traditional authentication methods may not always be suitable or sufficient for the unique characteristics of electromagnetic wave-based systems.
The increasing prevalence of Internet of Things (IoT) devices and smart systems has expanded the attack surface for EM networks. Many of these devices have limited computational resources and may lack robust security features, making them potential entry points for attackers to compromise the entire network.
Electromagnetic side-channel attacks represent a growing concern. These attacks exploit unintentional electromagnetic emissions from electronic devices to extract sensitive information, such as encryption keys or confidential data. As devices become more compact and powerful, mitigating these side-channel vulnerabilities becomes increasingly challenging.
The dynamic nature of EM networks, particularly in mobile and ad-hoc scenarios, introduces additional security complexities. Maintaining secure connections and ensuring data integrity in environments with constantly changing network topologies and varying signal strengths requires sophisticated adaptive security mechanisms.
Lastly, the emergence of quantum computing poses a long-term threat to current encryption methods used in EM networks. As quantum computers become more powerful, they may be able to break widely used cryptographic algorithms, necessitating the development and implementation of quantum-resistant security protocols for electromagnetic wave communications.
Existing EM Network Security Solutions
01 Network intrusion detection and prevention
Systems and methods for detecting and preventing unauthorized access to electromagnetic wave networks. This includes monitoring network traffic, identifying suspicious patterns, and implementing security measures to block potential threats. Advanced algorithms and machine learning techniques are used to enhance detection accuracy and response time.- Network Intrusion Detection and Prevention: Systems and methods for detecting and preventing unauthorized access to electromagnetic wave networks. This includes real-time monitoring of network traffic, identifying suspicious patterns, and implementing countermeasures to block potential threats. Advanced algorithms and machine learning techniques are used to improve detection accuracy and response time.
- Encryption and Secure Communication Protocols: Development of robust encryption methods and secure communication protocols specifically designed for electromagnetic wave networks. These technologies aim to protect data transmission from interception and tampering, ensuring confidentiality and integrity of information exchanged over wireless networks.
- Electromagnetic Shielding and Signal Isolation: Techniques for shielding electromagnetic wave networks from external interference and unauthorized access. This includes the use of specialized materials and designs to create physical barriers that prevent signal leakage and protect against eavesdropping. Methods for isolating critical network components to enhance security are also developed.
- Authentication and Access Control Mechanisms: Implementation of advanced authentication methods and access control systems tailored for electromagnetic wave networks. These include multi-factor authentication, biometric verification, and dynamic access policies to ensure that only authorized users and devices can connect to and utilize the network resources.
- Vulnerability Assessment and Risk Management: Development of tools and methodologies for conducting comprehensive vulnerability assessments of electromagnetic wave networks. This includes identifying potential weak points, simulating attack scenarios, and implementing risk management strategies to mitigate security threats. Regular security audits and updates are emphasized to maintain network resilience.
02 Encryption and secure communication protocols
Development of robust encryption methods and secure communication protocols for electromagnetic wave networks. These technologies ensure data confidentiality and integrity during transmission, protecting against eavesdropping and man-in-the-middle attacks. Implementation of advanced cryptographic algorithms and key management systems enhance overall network security.Expand Specific Solutions03 Electromagnetic shielding and signal isolation
Techniques for shielding electromagnetic wave networks from external interference and unauthorized access. This includes the use of specialized materials and designs to isolate sensitive network components and prevent signal leakage. Advanced shielding methods help mitigate risks associated with electromagnetic eavesdropping and side-channel attacks.Expand Specific Solutions04 Authentication and access control mechanisms
Implementation of robust authentication and access control systems for electromagnetic wave networks. These mechanisms ensure that only authorized users and devices can access network resources. Multi-factor authentication, biometric verification, and dynamic access policies are employed to enhance security and prevent unauthorized intrusions.Expand Specific Solutions05 Vulnerability assessment and risk management
Methodologies for identifying and assessing vulnerabilities in electromagnetic wave networks. This includes regular security audits, penetration testing, and risk analysis to identify potential weaknesses. Implementing proactive risk management strategies and continuous monitoring helps maintain network security and resilience against evolving threats.Expand Specific Solutions
Key Players in EM Network Security Industry
The electromagnetic wave network security landscape is evolving rapidly, with the market in its growth phase. As the technology matures and adoption increases, the market size is expanding, driven by growing concerns over cybersecurity threats. Key players like Huawei, Samsung, and Nokia are leading innovation, leveraging their expertise in telecommunications and network infrastructure. Emerging companies such as Honor Device Co. and Xiaomi are also making significant strides, particularly in consumer-facing applications. The competitive landscape is characterized by a mix of established tech giants and agile startups, each contributing to advancing security measures in electromagnetic wave networks.
Samsung Electronics Co., Ltd.
Technical Solution: Samsung has developed a comprehensive security solution for electromagnetic wave networks, with a particular focus on IoT and smart device ecosystems. Their approach includes the implementation of blockchain technology for secure device authentication and data integrity verification[7]. Samsung has also developed a proprietary secure element chip, embedded in their devices, which provides hardware-based protection against various electromagnetic attacks[8]. Additionally, they have implemented advanced machine learning algorithms for real-time threat detection and response in wireless networks. Samsung's solution also incorporates dynamic frequency hopping techniques to mitigate jamming and interference risks in crowded electromagnetic environments[9].
Strengths: Strong integration with IoT ecosystems, hardware-based security features, and innovative use of blockchain technology. Weaknesses: May be more focused on consumer devices rather than enterprise-level network infrastructure.
Nokia Technologies Oy
Technical Solution: Nokia has developed a robust security framework for electromagnetic wave networks, focusing on 5G and beyond. Their approach includes advanced network slicing techniques, which allow for the creation of isolated virtual networks with tailored security policies[4]. Nokia's security solution incorporates AI-driven anomaly detection and response systems, capable of identifying and mitigating threats in real-time across the network[5]. They have also implemented enhanced authentication protocols, including biometric and behavioral analysis, to ensure secure access to network resources. Furthermore, Nokia has developed specialized hardware security modules (HSMs) designed to protect cryptographic keys and sensitive data in electromagnetic wave environments[6].
Strengths: Strong focus on 5G security, AI-driven threat detection, and advanced network slicing capabilities. Weaknesses: May require significant infrastructure upgrades for full implementation.
Core Innovations in EM Wave Protection
IC package
PatentInactiveUS20120086110A1
Innovation
- An IC package design incorporating a magnetic body and a conductive board, where the magnetic body is arranged on the surface of the conductive board facing the IC chip, effectively shields electromagnetic waves by reducing their leakage through the side surfaces and preventing invasion from outside.
Cell selection and inter-frequency handover
PatentInactiveEP1675427A1
Innovation
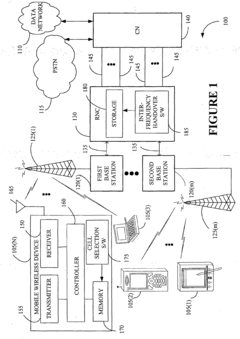
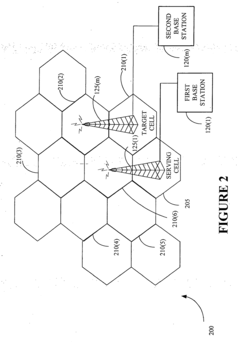
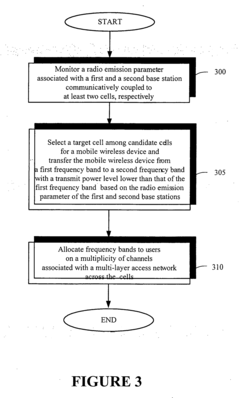
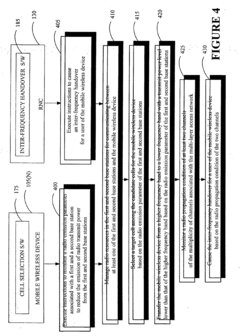
- A method for allocating frequency bands to users across multiple channels associated with base stations, monitoring radio emission parameters to select a target cell and perform inter-frequency handovers, reducing transmission power and allocating lower frequency bands to minimize electromagnetic exposure and optimize resource usage.
Regulatory Framework for EM Network Security
The regulatory framework for electromagnetic (EM) network security is a critical component in mitigating security risks in EM wave networks. As the use of EM networks continues to expand across various sectors, governments and international bodies have recognized the need for comprehensive regulations to ensure the safety and integrity of these systems.
At the international level, the International Telecommunication Union (ITU) plays a pivotal role in setting standards and guidelines for EM network security. The ITU-T X.1205 recommendation, for instance, provides a framework for cybersecurity in telecommunication networks, including those utilizing EM waves. This recommendation outlines best practices for securing network infrastructure, data transmission, and access control mechanisms.
National regulatory bodies have also developed specific frameworks to address EM network security within their jurisdictions. In the United States, the Federal Communications Commission (FCC) has implemented regulations such as the Communications Assistance for Law Enforcement Act (CALEA) and the Secure Networks Act, which mandate security measures for telecommunications providers and equipment manufacturers.
The European Union has established the Network and Information Security (NIS) Directive, which requires member states to adopt national cybersecurity strategies and establish Computer Security Incident Response Teams (CSIRTs). This directive specifically addresses the security of critical infrastructure, including EM networks used in telecommunications and energy sectors.
In Asia, countries like China and Japan have implemented their own regulatory frameworks. China's Cybersecurity Law and Multi-Level Protection Scheme (MLPS) 2.0 impose strict requirements on network operators, including those managing EM networks. Japan's Basic Act on Cybersecurity provides a foundation for protecting critical information infrastructure, encompassing EM network security.
These regulatory frameworks typically encompass several key areas: risk assessment and management, encryption standards, access control measures, incident reporting and response protocols, and regular security audits. They often require organizations to implement robust security policies, conduct employee training, and maintain up-to-date security technologies.
Compliance with these regulations is enforced through various mechanisms, including mandatory reporting, periodic audits, and penalties for non-compliance. Many frameworks also encourage information sharing and collaboration between industry stakeholders and government agencies to enhance overall security posture.
As EM network technologies continue to evolve, regulatory frameworks must adapt to address emerging threats and vulnerabilities. This includes developing regulations for new technologies such as 5G networks, Internet of Things (IoT) devices, and quantum communication systems, which rely heavily on EM wave transmission.
At the international level, the International Telecommunication Union (ITU) plays a pivotal role in setting standards and guidelines for EM network security. The ITU-T X.1205 recommendation, for instance, provides a framework for cybersecurity in telecommunication networks, including those utilizing EM waves. This recommendation outlines best practices for securing network infrastructure, data transmission, and access control mechanisms.
National regulatory bodies have also developed specific frameworks to address EM network security within their jurisdictions. In the United States, the Federal Communications Commission (FCC) has implemented regulations such as the Communications Assistance for Law Enforcement Act (CALEA) and the Secure Networks Act, which mandate security measures for telecommunications providers and equipment manufacturers.
The European Union has established the Network and Information Security (NIS) Directive, which requires member states to adopt national cybersecurity strategies and establish Computer Security Incident Response Teams (CSIRTs). This directive specifically addresses the security of critical infrastructure, including EM networks used in telecommunications and energy sectors.
In Asia, countries like China and Japan have implemented their own regulatory frameworks. China's Cybersecurity Law and Multi-Level Protection Scheme (MLPS) 2.0 impose strict requirements on network operators, including those managing EM networks. Japan's Basic Act on Cybersecurity provides a foundation for protecting critical information infrastructure, encompassing EM network security.
These regulatory frameworks typically encompass several key areas: risk assessment and management, encryption standards, access control measures, incident reporting and response protocols, and regular security audits. They often require organizations to implement robust security policies, conduct employee training, and maintain up-to-date security technologies.
Compliance with these regulations is enforced through various mechanisms, including mandatory reporting, periodic audits, and penalties for non-compliance. Many frameworks also encourage information sharing and collaboration between industry stakeholders and government agencies to enhance overall security posture.
As EM network technologies continue to evolve, regulatory frameworks must adapt to address emerging threats and vulnerabilities. This includes developing regulations for new technologies such as 5G networks, Internet of Things (IoT) devices, and quantum communication systems, which rely heavily on EM wave transmission.
Emerging Threats in EM Wave Networks
Electromagnetic wave networks, while offering unprecedented connectivity and communication capabilities, are increasingly becoming targets for sophisticated cyber attacks. As these networks expand and evolve, new vulnerabilities emerge, presenting a complex landscape of potential threats. One of the most significant emerging threats is the exploitation of radio frequency (RF) vulnerabilities. Attackers are developing advanced techniques to intercept, manipulate, or disrupt RF signals, potentially compromising the integrity and confidentiality of transmitted data.
Another growing concern is the rise of quantum computing and its potential to break current encryption methods used in EM wave networks. As quantum computers become more powerful, they pose a significant threat to the security of these networks, potentially rendering current cryptographic protocols obsolete. This necessitates the development of quantum-resistant encryption methods to safeguard future communications.
The proliferation of Internet of Things (IoT) devices connected through EM wave networks introduces a new attack surface. Many IoT devices lack robust security measures, making them vulnerable entry points for malicious actors to infiltrate larger networks. This threat is compounded by the sheer number of devices and the difficulty in managing and updating their security protocols.
Electromagnetic pulse (EMP) attacks represent another emerging threat to EM wave networks. These high-intensity bursts of electromagnetic energy can disrupt or destroy electronic equipment, potentially causing widespread communication blackouts. As EMP weapons become more sophisticated and accessible, the risk to critical infrastructure relying on EM wave networks increases significantly.
The advent of software-defined radio (SDR) technology has also introduced new security challenges. While SDR offers flexibility and efficiency, it also provides attackers with powerful tools to analyze and exploit RF signals. This technology can be used to create more sophisticated jamming techniques or to impersonate legitimate network nodes, leading to potential data breaches or network disruptions.
Lastly, the increasing use of artificial intelligence and machine learning in network attacks poses a significant threat. These technologies enable attackers to develop more adaptive and intelligent malware capable of evading traditional security measures. AI-powered attacks can analyze network behavior patterns and exploit vulnerabilities at an unprecedented scale and speed, making them particularly challenging to detect and mitigate.
Another growing concern is the rise of quantum computing and its potential to break current encryption methods used in EM wave networks. As quantum computers become more powerful, they pose a significant threat to the security of these networks, potentially rendering current cryptographic protocols obsolete. This necessitates the development of quantum-resistant encryption methods to safeguard future communications.
The proliferation of Internet of Things (IoT) devices connected through EM wave networks introduces a new attack surface. Many IoT devices lack robust security measures, making them vulnerable entry points for malicious actors to infiltrate larger networks. This threat is compounded by the sheer number of devices and the difficulty in managing and updating their security protocols.
Electromagnetic pulse (EMP) attacks represent another emerging threat to EM wave networks. These high-intensity bursts of electromagnetic energy can disrupt or destroy electronic equipment, potentially causing widespread communication blackouts. As EMP weapons become more sophisticated and accessible, the risk to critical infrastructure relying on EM wave networks increases significantly.
The advent of software-defined radio (SDR) technology has also introduced new security challenges. While SDR offers flexibility and efficiency, it also provides attackers with powerful tools to analyze and exploit RF signals. This technology can be used to create more sophisticated jamming techniques or to impersonate legitimate network nodes, leading to potential data breaches or network disruptions.
Lastly, the increasing use of artificial intelligence and machine learning in network attacks poses a significant threat. These technologies enable attackers to develop more adaptive and intelligent malware capable of evading traditional security measures. AI-powered attacks can analyze network behavior patterns and exploit vulnerabilities at an unprecedented scale and speed, making them particularly challenging to detect and mitigate.
Unlock deeper insights with Patsnap Eureka Quick Research — get a full tech report to explore trends and direct your research. Try now!
Generate Your Research Report Instantly with AI Agent
Supercharge your innovation with Patsnap Eureka AI Agent Platform!