Quantum Computing and its Implications for Internet Security
JUL 17, 20259 MIN READ
Generate Your Research Report Instantly with AI Agent
Patsnap Eureka helps you evaluate technical feasibility & market potential.
Quantum Computing Evolution and Objectives
Quantum computing has emerged as a revolutionary technology with the potential to transform various fields, including internet security. The evolution of quantum computing can be traced back to the early 1980s when Richard Feynman proposed the idea of using quantum mechanical systems for computation. Since then, the field has progressed rapidly, driven by advancements in quantum physics, computer science, and engineering.
The primary objective of quantum computing in the context of internet security is to develop systems that can perform complex calculations exponentially faster than classical computers. This capability has significant implications for cryptography, which forms the backbone of modern internet security protocols. Quantum computers have the potential to break many of the encryption algorithms currently used to secure online communications and transactions.
One of the key milestones in quantum computing was the development of Shor's algorithm in 1994, which demonstrated the theoretical ability of quantum computers to factor large numbers efficiently. This discovery posed a direct threat to widely used public-key cryptography systems, such as RSA, which rely on the difficulty of factoring large numbers.
As quantum computing technology continues to advance, researchers and industry leaders are focusing on several key objectives. These include increasing the number of qubits in quantum systems, improving qubit coherence times, and developing error correction techniques to enhance the reliability of quantum computations. The ultimate goal is to achieve quantum supremacy, a state where quantum computers can solve problems that are practically impossible for classical computers.
In the realm of internet security, the evolution of quantum computing has sparked a race to develop quantum-resistant cryptographic algorithms. This field, known as post-quantum cryptography, aims to create encryption methods that can withstand attacks from both classical and quantum computers. The National Institute of Standards and Technology (NIST) is leading efforts to standardize post-quantum cryptographic algorithms, with the goal of ensuring long-term security for sensitive data and communications.
Another important objective in the quantum computing landscape is the development of quantum key distribution (QKD) systems. QKD leverages the principles of quantum mechanics to create theoretically unbreakable encryption keys, offering a potential solution to secure communication in the quantum era. However, practical implementation challenges, such as limited transmission distances and the need for specialized hardware, still need to be addressed.
As quantum computing continues to evolve, its impact on internet security is expected to grow exponentially. The technology presents both challenges and opportunities, necessitating a proactive approach from researchers, policymakers, and industry stakeholders to ensure the continued security and integrity of digital infrastructure in the quantum age.
The primary objective of quantum computing in the context of internet security is to develop systems that can perform complex calculations exponentially faster than classical computers. This capability has significant implications for cryptography, which forms the backbone of modern internet security protocols. Quantum computers have the potential to break many of the encryption algorithms currently used to secure online communications and transactions.
One of the key milestones in quantum computing was the development of Shor's algorithm in 1994, which demonstrated the theoretical ability of quantum computers to factor large numbers efficiently. This discovery posed a direct threat to widely used public-key cryptography systems, such as RSA, which rely on the difficulty of factoring large numbers.
As quantum computing technology continues to advance, researchers and industry leaders are focusing on several key objectives. These include increasing the number of qubits in quantum systems, improving qubit coherence times, and developing error correction techniques to enhance the reliability of quantum computations. The ultimate goal is to achieve quantum supremacy, a state where quantum computers can solve problems that are practically impossible for classical computers.
In the realm of internet security, the evolution of quantum computing has sparked a race to develop quantum-resistant cryptographic algorithms. This field, known as post-quantum cryptography, aims to create encryption methods that can withstand attacks from both classical and quantum computers. The National Institute of Standards and Technology (NIST) is leading efforts to standardize post-quantum cryptographic algorithms, with the goal of ensuring long-term security for sensitive data and communications.
Another important objective in the quantum computing landscape is the development of quantum key distribution (QKD) systems. QKD leverages the principles of quantum mechanics to create theoretically unbreakable encryption keys, offering a potential solution to secure communication in the quantum era. However, practical implementation challenges, such as limited transmission distances and the need for specialized hardware, still need to be addressed.
As quantum computing continues to evolve, its impact on internet security is expected to grow exponentially. The technology presents both challenges and opportunities, necessitating a proactive approach from researchers, policymakers, and industry stakeholders to ensure the continued security and integrity of digital infrastructure in the quantum age.
Cybersecurity Market Demand Analysis
The cybersecurity market has experienced significant growth in recent years, driven by the increasing frequency and sophistication of cyber threats. With the advent of quantum computing, this demand is expected to surge even further. Quantum computers have the potential to break many of the encryption algorithms currently used to secure internet communications and data storage, creating a pressing need for quantum-resistant security solutions.
The global cybersecurity market size was valued at $167.13 billion in 2020 and is projected to reach $372.04 billion by 2028, growing at a CAGR of 10.9% from 2021 to 2028. This growth is largely attributed to the rising number of cyber attacks, the increasing adoption of IoT and cloud services, and stringent data protection regulations. However, the emergence of quantum computing is expected to accelerate this growth even further.
As quantum computers become more powerful and accessible, they pose a significant threat to current encryption methods. RSA and ECC, two widely used public-key cryptography systems, are particularly vulnerable to quantum attacks. This vulnerability has created a urgent demand for quantum-resistant cryptography solutions, also known as post-quantum cryptography.
The National Institute of Standards and Technology (NIST) has been leading efforts to standardize post-quantum cryptography algorithms. Their ongoing process has sparked increased interest and investment in quantum-resistant security solutions across various industries. Financial institutions, healthcare providers, and government agencies are among the sectors most actively seeking robust cybersecurity measures to protect against future quantum threats.
The demand for quantum-resistant encryption is not limited to large enterprises. Small and medium-sized businesses are also recognizing the need to future-proof their security infrastructure. This has led to a growing market for managed security services that offer quantum-safe solutions, making advanced cybersecurity accessible to a broader range of organizations.
In addition to encryption, quantum computing is driving demand for other cybersecurity technologies. Quantum key distribution (QKD) systems, which use quantum mechanics principles to secure communication channels, are gaining traction. The global QKD market is expected to grow from $495.9 million in 2020 to $1.9 billion by 2025, at a CAGR of 31.8%.
As awareness of quantum computing threats grows, there is an increasing demand for cybersecurity professionals with expertise in quantum-resistant technologies. This has led to a skills gap in the industry, with organizations struggling to find qualified personnel to implement and manage quantum-safe security solutions. Consequently, there is a rising market for training and certification programs focused on post-quantum cryptography and related technologies.
The global cybersecurity market size was valued at $167.13 billion in 2020 and is projected to reach $372.04 billion by 2028, growing at a CAGR of 10.9% from 2021 to 2028. This growth is largely attributed to the rising number of cyber attacks, the increasing adoption of IoT and cloud services, and stringent data protection regulations. However, the emergence of quantum computing is expected to accelerate this growth even further.
As quantum computers become more powerful and accessible, they pose a significant threat to current encryption methods. RSA and ECC, two widely used public-key cryptography systems, are particularly vulnerable to quantum attacks. This vulnerability has created a urgent demand for quantum-resistant cryptography solutions, also known as post-quantum cryptography.
The National Institute of Standards and Technology (NIST) has been leading efforts to standardize post-quantum cryptography algorithms. Their ongoing process has sparked increased interest and investment in quantum-resistant security solutions across various industries. Financial institutions, healthcare providers, and government agencies are among the sectors most actively seeking robust cybersecurity measures to protect against future quantum threats.
The demand for quantum-resistant encryption is not limited to large enterprises. Small and medium-sized businesses are also recognizing the need to future-proof their security infrastructure. This has led to a growing market for managed security services that offer quantum-safe solutions, making advanced cybersecurity accessible to a broader range of organizations.
In addition to encryption, quantum computing is driving demand for other cybersecurity technologies. Quantum key distribution (QKD) systems, which use quantum mechanics principles to secure communication channels, are gaining traction. The global QKD market is expected to grow from $495.9 million in 2020 to $1.9 billion by 2025, at a CAGR of 31.8%.
As awareness of quantum computing threats grows, there is an increasing demand for cybersecurity professionals with expertise in quantum-resistant technologies. This has led to a skills gap in the industry, with organizations struggling to find qualified personnel to implement and manage quantum-safe security solutions. Consequently, there is a rising market for training and certification programs focused on post-quantum cryptography and related technologies.
Quantum Computing State and Challenges
Quantum computing has made significant strides in recent years, yet it still faces numerous challenges that hinder its widespread adoption and practical implementation. The current state of quantum computing is characterized by a mix of promising advancements and persistent obstacles.
One of the primary challenges in quantum computing is maintaining quantum coherence. Quantum systems are extremely sensitive to environmental disturbances, which can cause decoherence and lead to errors in computations. Researchers are actively working on developing better error correction techniques and more stable qubit architectures to mitigate this issue.
Scalability remains another major hurdle. While small-scale quantum computers with dozens of qubits have been demonstrated, scaling up to hundreds or thousands of qubits necessary for practical applications is proving to be a formidable task. This challenge involves not only increasing the number of qubits but also maintaining their quality and interconnectivity.
The development of quantum algorithms is progressing, but there is still a significant gap between theoretical possibilities and practical implementations. Many quantum algorithms that show promise in theory are yet to be realized on actual quantum hardware due to limitations in current quantum systems.
Hardware limitations also pose significant challenges. Current quantum computers require extremely low temperatures and highly controlled environments to operate, making them expensive and difficult to maintain. Efforts are underway to develop more robust and less environmentally sensitive quantum computing technologies.
In the context of internet security, quantum computing presents both opportunities and threats. While quantum computers could potentially break many current encryption methods, they also offer the possibility of developing new, more secure encryption techniques. The race is on to develop quantum-resistant cryptography before large-scale quantum computers become a reality.
Despite these challenges, progress in quantum computing continues. Tech giants and startups alike are investing heavily in quantum research and development. Advancements in areas such as superconducting qubits, trapped ions, and topological qubits are pushing the boundaries of what's possible in quantum computing.
The global quantum computing landscape is diverse, with significant research efforts spread across North America, Europe, and Asia. Each region brings unique strengths to the field, fostering a competitive yet collaborative international research environment.
As the field progresses, interdisciplinary collaboration becomes increasingly crucial. Quantum computing requires expertise not only in physics and computer science but also in materials science, engineering, and mathematics. This multidisciplinary nature adds complexity to the development process but also drives innovation.
One of the primary challenges in quantum computing is maintaining quantum coherence. Quantum systems are extremely sensitive to environmental disturbances, which can cause decoherence and lead to errors in computations. Researchers are actively working on developing better error correction techniques and more stable qubit architectures to mitigate this issue.
Scalability remains another major hurdle. While small-scale quantum computers with dozens of qubits have been demonstrated, scaling up to hundreds or thousands of qubits necessary for practical applications is proving to be a formidable task. This challenge involves not only increasing the number of qubits but also maintaining their quality and interconnectivity.
The development of quantum algorithms is progressing, but there is still a significant gap between theoretical possibilities and practical implementations. Many quantum algorithms that show promise in theory are yet to be realized on actual quantum hardware due to limitations in current quantum systems.
Hardware limitations also pose significant challenges. Current quantum computers require extremely low temperatures and highly controlled environments to operate, making them expensive and difficult to maintain. Efforts are underway to develop more robust and less environmentally sensitive quantum computing technologies.
In the context of internet security, quantum computing presents both opportunities and threats. While quantum computers could potentially break many current encryption methods, they also offer the possibility of developing new, more secure encryption techniques. The race is on to develop quantum-resistant cryptography before large-scale quantum computers become a reality.
Despite these challenges, progress in quantum computing continues. Tech giants and startups alike are investing heavily in quantum research and development. Advancements in areas such as superconducting qubits, trapped ions, and topological qubits are pushing the boundaries of what's possible in quantum computing.
The global quantum computing landscape is diverse, with significant research efforts spread across North America, Europe, and Asia. Each region brings unique strengths to the field, fostering a competitive yet collaborative international research environment.
As the field progresses, interdisciplinary collaboration becomes increasingly crucial. Quantum computing requires expertise not only in physics and computer science but also in materials science, engineering, and mathematics. This multidisciplinary nature adds complexity to the development process but also drives innovation.
Current Post-Quantum Cryptography Solutions
01 Quantum Key Distribution (QKD) for secure communication
Quantum Key Distribution utilizes quantum mechanics principles to generate and distribute cryptographic keys securely. This technology enables the detection of any eavesdropping attempts, ensuring the confidentiality of communication over the internet. QKD systems can be integrated into existing network infrastructures to enhance cybersecurity.- Quantum-resistant cryptography: Developing cryptographic algorithms that are resistant to attacks from quantum computers. These algorithms aim to secure internet communications and data transmission in the post-quantum era, ensuring that encrypted information remains protected even against advanced quantum computing capabilities.
- Quantum key distribution (QKD): Implementing quantum key distribution systems for secure communication over the internet. QKD uses quantum mechanical principles to generate and distribute encryption keys, providing a theoretically unbreakable method of secure communication that is resistant to both classical and quantum attacks.
- Quantum random number generation: Utilizing quantum processes to generate truly random numbers for cryptographic purposes. These quantum random number generators enhance the security of encryption keys and other cryptographic operations, improving overall internet security against sophisticated attacks.
- Quantum-safe network protocols: Developing and implementing new network protocols that are resistant to quantum attacks. These protocols aim to secure internet infrastructure, including routing and authentication mechanisms, to ensure the integrity and confidentiality of data transmission in a quantum computing environment.
- Hybrid classical-quantum security systems: Creating security systems that combine classical and quantum technologies to provide enhanced protection. These hybrid systems leverage the strengths of both classical and quantum computing to create multi-layered security solutions for internet communications and data storage.
02 Post-quantum cryptography algorithms
Development of cryptographic algorithms resistant to attacks by quantum computers. These algorithms are designed to withstand potential threats from future quantum computers, ensuring long-term security for internet communications and data storage. Implementation of post-quantum cryptography in existing systems and protocols is a key focus area.Expand Specific Solutions03 Quantum-resistant blockchain technology
Adaptation of blockchain technology to resist quantum computing attacks. This involves developing new consensus mechanisms and cryptographic primitives that can withstand potential quantum computer threats. Quantum-resistant blockchains aim to secure digital transactions and smart contracts in a post-quantum world.Expand Specific Solutions04 Quantum random number generators for enhanced security
Utilization of quantum phenomena to generate true random numbers for cryptographic purposes. Quantum random number generators provide a higher level of unpredictability compared to classical methods, enhancing the security of encryption keys and other cryptographic applications in internet security.Expand Specific Solutions05 Hybrid classical-quantum security systems
Integration of quantum and classical security technologies to create robust, multi-layered security solutions. These hybrid systems combine the strengths of both quantum and classical approaches, providing enhanced protection against both current and future threats to internet security.Expand Specific Solutions
Key Quantum Computing Players
The quantum computing landscape is evolving rapidly, with significant implications for internet security. The industry is in its early stages, characterized by intense research and development efforts from both established tech giants and specialized startups. Market size projections vary, but estimates suggest substantial growth potential in the coming years. Technological maturity is advancing, with companies like D-Wave Systems, IBM, and Google making notable progress in quantum hardware development. Arqit Ltd. and InfoSec Global are focusing on quantum-resistant cryptography, while major players such as Intel, Samsung, and Fujitsu are investing in quantum research. Universities and research institutions, including the University of Chicago and Singapore University of Technology & Design, are contributing to the field's advancement. As quantum computing capabilities grow, the race to develop quantum-safe encryption methods is intensifying, involving both private sector and government entities.
D-Wave Systems, Inc.
Technical Solution: D-Wave focuses on quantum annealing technology, which is particularly suited for optimization problems. While not directly addressing traditional cryptography, their approach has implications for certain aspects of internet security. D-Wave's latest Advantage system features over 5000 qubits and 15-way qubit connectivity[6]. They are exploring applications in cybersecurity, such as optimizing network security configurations and detecting anomalies in large datasets. D-Wave's quantum annealing technology could potentially be used to solve certain optimization problems related to cryptographic systems faster than classical computers[7].
Strengths: Leader in quantum annealing technology, practical applications in optimization. Weaknesses: Limited applicability to traditional cryptographic problems, not focused on general-purpose quantum computing.
Samsung Electronics Co., Ltd.
Technical Solution: Samsung is approaching quantum computing and internet security from multiple angles. They are developing quantum-resistant cryptographic solutions for their mobile devices and IoT products. Samsung's research includes the development of quantum random number generators (QRNG) for enhanced security in mobile devices[10]. They are also exploring the integration of post-quantum cryptography in their semiconductor products. In collaboration with ID Quantique, Samsung has implemented QRNG technology in their Galaxy Quantum smartphone series, providing a hardware-based random number generator for improved encryption[11].
Strengths: Large consumer electronics market share, integration of quantum technologies in consumer products. Weaknesses: Less focus on large-scale quantum computing, primarily concentrating on quantum-enhanced security for existing products.
Quantum-Resistant Algorithms Analysis
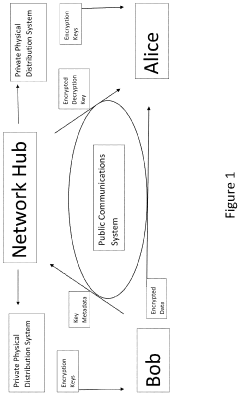
One-time-pad encryption system and methods
PatentActiveUS20230171088A1
Innovation
- The Quantum Lock system employs quantum-resistant OTP encryption with true random number generators and a secure network for key distribution and management, using a central hub to facilitate secure communication without relying on physical key exchange, ensuring the security of blockchain systems and protecting against quantum computer attacks.
Quantum Computing Standardization Efforts
Quantum computing standardization efforts are gaining momentum as the technology advances and its potential impact on various fields, including internet security, becomes more apparent. These efforts aim to establish common frameworks, protocols, and benchmarks for quantum computing systems, ensuring interoperability and facilitating the development of quantum-safe cryptography.
Several international organizations and consortia are leading the charge in quantum computing standardization. The National Institute of Standards and Technology (NIST) in the United States has been at the forefront, initiating the Post-Quantum Cryptography Standardization process to develop quantum-resistant cryptographic algorithms. This multi-year effort involves evaluating and selecting candidate algorithms that can withstand attacks from both classical and quantum computers.
The European Telecommunications Standards Institute (ETSI) has established a Quantum-Safe Cryptography working group, focusing on developing standards for quantum-safe cryptographic primitives and protocols. Their work includes creating specifications for quantum key distribution systems and quantum-resistant public key algorithms.
The International Organization for Standardization (ISO) and the International Electrotechnical Commission (IEC) have formed a joint technical committee (ISO/IEC JTC 1) to address quantum computing standardization. This committee is working on developing standards for quantum computing terminology, performance benchmarking, and security requirements.
In the private sector, the Quantum Economic Development Consortium (QED-C) is collaborating with industry partners to develop standards for quantum computing hardware and software interfaces. Their efforts aim to create a common language and set of specifications for quantum computing systems, enabling better integration and interoperability across different platforms.
Standardization efforts also extend to quantum programming languages and software development kits. The quantum software community is working towards establishing common practices and frameworks, such as OpenQASM for quantum assembly language and Qiskit for quantum circuit design and execution.
As quantum computing technology continues to evolve, these standardization efforts will play a crucial role in ensuring the security and reliability of quantum systems. They will also facilitate the integration of quantum computing with existing classical computing infrastructure, paving the way for hybrid quantum-classical systems that can address complex computational challenges in various domains, including cybersecurity.
Several international organizations and consortia are leading the charge in quantum computing standardization. The National Institute of Standards and Technology (NIST) in the United States has been at the forefront, initiating the Post-Quantum Cryptography Standardization process to develop quantum-resistant cryptographic algorithms. This multi-year effort involves evaluating and selecting candidate algorithms that can withstand attacks from both classical and quantum computers.
The European Telecommunications Standards Institute (ETSI) has established a Quantum-Safe Cryptography working group, focusing on developing standards for quantum-safe cryptographic primitives and protocols. Their work includes creating specifications for quantum key distribution systems and quantum-resistant public key algorithms.
The International Organization for Standardization (ISO) and the International Electrotechnical Commission (IEC) have formed a joint technical committee (ISO/IEC JTC 1) to address quantum computing standardization. This committee is working on developing standards for quantum computing terminology, performance benchmarking, and security requirements.
In the private sector, the Quantum Economic Development Consortium (QED-C) is collaborating with industry partners to develop standards for quantum computing hardware and software interfaces. Their efforts aim to create a common language and set of specifications for quantum computing systems, enabling better integration and interoperability across different platforms.
Standardization efforts also extend to quantum programming languages and software development kits. The quantum software community is working towards establishing common practices and frameworks, such as OpenQASM for quantum assembly language and Qiskit for quantum circuit design and execution.
As quantum computing technology continues to evolve, these standardization efforts will play a crucial role in ensuring the security and reliability of quantum systems. They will also facilitate the integration of quantum computing with existing classical computing infrastructure, paving the way for hybrid quantum-classical systems that can address complex computational challenges in various domains, including cybersecurity.
Quantum Computing Ethics and Privacy Concerns
The advent of quantum computing brings forth significant ethical and privacy concerns that demand careful consideration. As quantum computers become more powerful and accessible, they pose potential threats to existing encryption methods, potentially compromising the privacy and security of sensitive information.
One of the primary ethical concerns is the potential for quantum computers to break current encryption standards, which could lead to unauthorized access to personal, financial, and governmental data. This capability raises questions about the responsibility of quantum computing developers and users in maintaining data integrity and protecting individual privacy rights.
Privacy concerns extend beyond data security to the realm of personal autonomy. Quantum computing's ability to process vast amounts of data quickly could enable more sophisticated surveillance and tracking systems, potentially infringing on personal freedoms and civil liberties. The ethical implications of such capabilities must be thoroughly examined and regulated to prevent misuse.
Another critical ethical consideration is the potential for quantum computing to exacerbate existing societal inequalities. As quantum technology advances, there is a risk that only wealthy nations and large corporations will have access to its benefits, widening the digital divide and creating new forms of technological disparity.
The development of quantum computing also raises questions about the ethical use of its immense computational power. While it offers tremendous potential for scientific advancement and problem-solving, it could also be used for malicious purposes, such as creating more sophisticated cyberattacks or developing advanced weapons systems.
Addressing these ethical and privacy concerns requires a multifaceted approach. It is crucial to develop robust quantum-resistant encryption methods to protect sensitive information in the post-quantum era. Additionally, establishing clear ethical guidelines and regulatory frameworks for quantum computing research, development, and application is essential to ensure responsible use of this technology.
Transparency and public engagement are vital in addressing these concerns. Educating the public about quantum computing's potential impacts on privacy and security can help foster informed discussions and decision-making processes. Collaborative efforts between governments, industry leaders, and academic institutions are necessary to develop comprehensive strategies for mitigating risks while maximizing the benefits of quantum computing.
In conclusion, as quantum computing continues to advance, it is imperative to proactively address the associated ethical and privacy concerns. Balancing the immense potential of this technology with the need to protect individual rights and societal values will be crucial in shaping a responsible and equitable quantum future.
One of the primary ethical concerns is the potential for quantum computers to break current encryption standards, which could lead to unauthorized access to personal, financial, and governmental data. This capability raises questions about the responsibility of quantum computing developers and users in maintaining data integrity and protecting individual privacy rights.
Privacy concerns extend beyond data security to the realm of personal autonomy. Quantum computing's ability to process vast amounts of data quickly could enable more sophisticated surveillance and tracking systems, potentially infringing on personal freedoms and civil liberties. The ethical implications of such capabilities must be thoroughly examined and regulated to prevent misuse.
Another critical ethical consideration is the potential for quantum computing to exacerbate existing societal inequalities. As quantum technology advances, there is a risk that only wealthy nations and large corporations will have access to its benefits, widening the digital divide and creating new forms of technological disparity.
The development of quantum computing also raises questions about the ethical use of its immense computational power. While it offers tremendous potential for scientific advancement and problem-solving, it could also be used for malicious purposes, such as creating more sophisticated cyberattacks or developing advanced weapons systems.
Addressing these ethical and privacy concerns requires a multifaceted approach. It is crucial to develop robust quantum-resistant encryption methods to protect sensitive information in the post-quantum era. Additionally, establishing clear ethical guidelines and regulatory frameworks for quantum computing research, development, and application is essential to ensure responsible use of this technology.
Transparency and public engagement are vital in addressing these concerns. Educating the public about quantum computing's potential impacts on privacy and security can help foster informed discussions and decision-making processes. Collaborative efforts between governments, industry leaders, and academic institutions are necessary to develop comprehensive strategies for mitigating risks while maximizing the benefits of quantum computing.
In conclusion, as quantum computing continues to advance, it is imperative to proactively address the associated ethical and privacy concerns. Balancing the immense potential of this technology with the need to protect individual rights and societal values will be crucial in shaping a responsible and equitable quantum future.
Unlock deeper insights with Patsnap Eureka Quick Research — get a full tech report to explore trends and direct your research. Try now!
Generate Your Research Report Instantly with AI Agent
Supercharge your innovation with Patsnap Eureka AI Agent Platform!