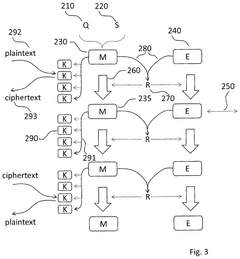
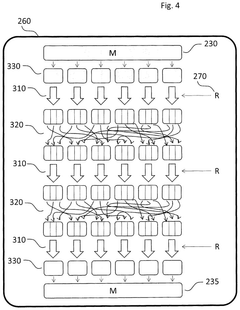
Quantum Computing for Advanced Encryption Methods
JUL 17, 20259 MIN READ
Generate Your Research Report Instantly with AI Agent
Patsnap Eureka helps you evaluate technical feasibility & market potential.
Quantum Cryptography Evolution and Objectives
Quantum cryptography has emerged as a revolutionary field at the intersection of quantum physics and information security. The evolution of this technology can be traced back to the early 1970s when Stephen Wiesner first proposed the concept of quantum money. However, it wasn't until the 1980s that the field truly began to take shape with the introduction of quantum key distribution (QKD) protocols.
The primary objective of quantum cryptography is to leverage the principles of quantum mechanics to create unbreakable encryption methods. This goal is driven by the increasing threat to traditional cryptographic systems posed by the advent of quantum computers. As quantum computing capabilities advance, they threaten to render many current encryption methods obsolete, creating an urgent need for quantum-resistant cryptographic solutions.
Over the past few decades, quantum cryptography has progressed through several key stages. The BB84 protocol, developed by Charles Bennett and Gilles Brassard in 1984, marked a significant milestone as the first practical QKD protocol. This was followed by the development of various other protocols, such as the E91 protocol and the BBM92 protocol, each offering unique advantages and addressing specific security concerns.
Recent years have seen a shift from theoretical research to practical implementation. Quantum cryptography systems have moved from laboratory experiments to real-world applications, with several companies and governments investing in quantum communication networks. The objective now is to scale these systems and integrate them into existing communication infrastructures.
The evolution of quantum cryptography is closely tied to advancements in quantum computing. As quantum computers become more powerful, the focus of quantum cryptography is expanding beyond QKD to include post-quantum cryptography (PQC). PQC aims to develop classical algorithms that can withstand attacks from quantum computers, providing a complementary approach to quantum-based encryption methods.
Looking forward, the objectives of quantum cryptography research are multifaceted. There is a push to improve the efficiency and range of quantum key distribution systems, making them viable for global communication networks. Researchers are also working on developing quantum random number generators and quantum digital signatures to enhance the overall security ecosystem.
Another critical objective is to address the vulnerabilities and practical limitations of current quantum cryptography systems. This includes developing countermeasures against side-channel attacks and improving the reliability of quantum devices in real-world conditions. The ultimate goal is to create a comprehensive quantum-safe cryptographic infrastructure that can protect sensitive information in the post-quantum era.
The primary objective of quantum cryptography is to leverage the principles of quantum mechanics to create unbreakable encryption methods. This goal is driven by the increasing threat to traditional cryptographic systems posed by the advent of quantum computers. As quantum computing capabilities advance, they threaten to render many current encryption methods obsolete, creating an urgent need for quantum-resistant cryptographic solutions.
Over the past few decades, quantum cryptography has progressed through several key stages. The BB84 protocol, developed by Charles Bennett and Gilles Brassard in 1984, marked a significant milestone as the first practical QKD protocol. This was followed by the development of various other protocols, such as the E91 protocol and the BBM92 protocol, each offering unique advantages and addressing specific security concerns.
Recent years have seen a shift from theoretical research to practical implementation. Quantum cryptography systems have moved from laboratory experiments to real-world applications, with several companies and governments investing in quantum communication networks. The objective now is to scale these systems and integrate them into existing communication infrastructures.
The evolution of quantum cryptography is closely tied to advancements in quantum computing. As quantum computers become more powerful, the focus of quantum cryptography is expanding beyond QKD to include post-quantum cryptography (PQC). PQC aims to develop classical algorithms that can withstand attacks from quantum computers, providing a complementary approach to quantum-based encryption methods.
Looking forward, the objectives of quantum cryptography research are multifaceted. There is a push to improve the efficiency and range of quantum key distribution systems, making them viable for global communication networks. Researchers are also working on developing quantum random number generators and quantum digital signatures to enhance the overall security ecosystem.
Another critical objective is to address the vulnerabilities and practical limitations of current quantum cryptography systems. This includes developing countermeasures against side-channel attacks and improving the reliability of quantum devices in real-world conditions. The ultimate goal is to create a comprehensive quantum-safe cryptographic infrastructure that can protect sensitive information in the post-quantum era.
Market Demand for Post-Quantum Encryption
The market demand for post-quantum encryption methods has been steadily growing in recent years, driven by the looming threat of quantum computers potentially breaking current encryption standards. As quantum computing technology advances, organizations across various sectors are increasingly recognizing the need to prepare for a post-quantum era in cybersecurity.
Financial institutions, government agencies, and large corporations are at the forefront of this demand, as they handle vast amounts of sensitive data that must remain secure for extended periods. These entities are particularly concerned about the "harvest now, decrypt later" attack scenario, where adversaries could collect encrypted data today and decrypt it once quantum computers become sufficiently powerful.
The healthcare sector is another significant driver of market demand for post-quantum encryption. With the increasing digitization of medical records and the sensitivity of patient data, healthcare providers and insurers are seeking robust encryption methods that can withstand future quantum attacks.
Telecommunications and cloud service providers are also key players in driving market demand. As they handle enormous volumes of data transmission and storage, ensuring long-term data security is crucial for maintaining customer trust and compliance with data protection regulations.
The automotive industry, particularly in the realm of connected and autonomous vehicles, is emerging as a new frontier for post-quantum encryption. As vehicles become more connected and reliant on secure communication, manufacturers are exploring quantum-resistant encryption to protect against potential future vulnerabilities.
Government initiatives and regulations are further fueling market demand. For instance, the U.S. National Institute of Standards and Technology (NIST) is in the process of standardizing post-quantum cryptographic algorithms, which is expected to accelerate adoption across industries.
The global market for post-quantum cryptography is projected to grow significantly in the coming years. While precise figures vary among different market research reports, there is a consensus on strong double-digit growth rates. This growth is attributed to increasing awareness of quantum computing threats, rising investments in cybersecurity, and the gradual integration of quantum-resistant algorithms into existing security infrastructures.
However, the market also faces challenges. The complexity of implementing post-quantum encryption, the lack of standardization, and the need for extensive testing and validation are factors that may slow down immediate widespread adoption. Additionally, many organizations are adopting a wait-and-see approach, balancing the urgency of quantum-readiness with the costs and complexities of transitioning to new encryption methods.
Financial institutions, government agencies, and large corporations are at the forefront of this demand, as they handle vast amounts of sensitive data that must remain secure for extended periods. These entities are particularly concerned about the "harvest now, decrypt later" attack scenario, where adversaries could collect encrypted data today and decrypt it once quantum computers become sufficiently powerful.
The healthcare sector is another significant driver of market demand for post-quantum encryption. With the increasing digitization of medical records and the sensitivity of patient data, healthcare providers and insurers are seeking robust encryption methods that can withstand future quantum attacks.
Telecommunications and cloud service providers are also key players in driving market demand. As they handle enormous volumes of data transmission and storage, ensuring long-term data security is crucial for maintaining customer trust and compliance with data protection regulations.
The automotive industry, particularly in the realm of connected and autonomous vehicles, is emerging as a new frontier for post-quantum encryption. As vehicles become more connected and reliant on secure communication, manufacturers are exploring quantum-resistant encryption to protect against potential future vulnerabilities.
Government initiatives and regulations are further fueling market demand. For instance, the U.S. National Institute of Standards and Technology (NIST) is in the process of standardizing post-quantum cryptographic algorithms, which is expected to accelerate adoption across industries.
The global market for post-quantum cryptography is projected to grow significantly in the coming years. While precise figures vary among different market research reports, there is a consensus on strong double-digit growth rates. This growth is attributed to increasing awareness of quantum computing threats, rising investments in cybersecurity, and the gradual integration of quantum-resistant algorithms into existing security infrastructures.
However, the market also faces challenges. The complexity of implementing post-quantum encryption, the lack of standardization, and the need for extensive testing and validation are factors that may slow down immediate widespread adoption. Additionally, many organizations are adopting a wait-and-see approach, balancing the urgency of quantum-readiness with the costs and complexities of transitioning to new encryption methods.
Quantum Computing Challenges in Cryptography
Quantum computing presents significant challenges to traditional cryptographic systems, potentially undermining the security of widely used encryption methods. The fundamental principle of quantum computing, which leverages quantum mechanical phenomena such as superposition and entanglement, allows for the processing of vast amounts of information simultaneously. This capability threatens to break many current encryption algorithms, particularly those based on the difficulty of factoring large numbers or solving discrete logarithm problems.
One of the primary challenges is the potential vulnerability of public-key cryptography systems, such as RSA and elliptic curve cryptography, to quantum attacks. Shor's algorithm, when implemented on a sufficiently powerful quantum computer, could efficiently factor large numbers and solve discrete logarithm problems, effectively breaking these encryption methods. This poses a severe threat to the confidentiality and integrity of sensitive data transmitted over the internet and stored in secure systems.
Another significant challenge is the need to develop and implement quantum-resistant cryptographic algorithms, also known as post-quantum cryptography. These algorithms must be secure against both classical and quantum attacks while remaining efficient enough for practical use on classical computers. The National Institute of Standards and Technology (NIST) is currently leading efforts to standardize post-quantum cryptographic algorithms, but the transition to these new methods presents its own set of challenges.
The development of quantum-safe cryptographic protocols and their integration into existing systems is a complex and time-consuming process. It requires extensive testing, validation, and standardization efforts to ensure the new algorithms are secure and compatible with current infrastructure. Moreover, the transition period itself presents a vulnerability window, as systems may need to support both classical and quantum-resistant algorithms simultaneously.
Quantum key distribution (QKD) offers a potential solution by leveraging quantum mechanics to create theoretically unbreakable encryption keys. However, QKD faces its own set of challenges, including limited range, high cost, and the need for specialized hardware. The practical implementation of QKD in large-scale networks remains a significant hurdle.
Furthermore, the rapid advancement of quantum computing technology creates a "harvest now, decrypt later" threat. Adversaries may collect and store encrypted data now, with the intention of decrypting it once sufficiently powerful quantum computers become available. This necessitates the urgent development and deployment of quantum-resistant encryption methods to protect sensitive information with long-term value.
In conclusion, the challenges posed by quantum computing to cryptography are multifaceted and require a coordinated effort from researchers, industry, and government agencies to develop, standardize, and implement quantum-resistant cryptographic solutions. The race against time to secure our digital infrastructure against the quantum threat underscores the critical importance of continued research and innovation in this field.
One of the primary challenges is the potential vulnerability of public-key cryptography systems, such as RSA and elliptic curve cryptography, to quantum attacks. Shor's algorithm, when implemented on a sufficiently powerful quantum computer, could efficiently factor large numbers and solve discrete logarithm problems, effectively breaking these encryption methods. This poses a severe threat to the confidentiality and integrity of sensitive data transmitted over the internet and stored in secure systems.
Another significant challenge is the need to develop and implement quantum-resistant cryptographic algorithms, also known as post-quantum cryptography. These algorithms must be secure against both classical and quantum attacks while remaining efficient enough for practical use on classical computers. The National Institute of Standards and Technology (NIST) is currently leading efforts to standardize post-quantum cryptographic algorithms, but the transition to these new methods presents its own set of challenges.
The development of quantum-safe cryptographic protocols and their integration into existing systems is a complex and time-consuming process. It requires extensive testing, validation, and standardization efforts to ensure the new algorithms are secure and compatible with current infrastructure. Moreover, the transition period itself presents a vulnerability window, as systems may need to support both classical and quantum-resistant algorithms simultaneously.
Quantum key distribution (QKD) offers a potential solution by leveraging quantum mechanics to create theoretically unbreakable encryption keys. However, QKD faces its own set of challenges, including limited range, high cost, and the need for specialized hardware. The practical implementation of QKD in large-scale networks remains a significant hurdle.
Furthermore, the rapid advancement of quantum computing technology creates a "harvest now, decrypt later" threat. Adversaries may collect and store encrypted data now, with the intention of decrypting it once sufficiently powerful quantum computers become available. This necessitates the urgent development and deployment of quantum-resistant encryption methods to protect sensitive information with long-term value.
In conclusion, the challenges posed by quantum computing to cryptography are multifaceted and require a coordinated effort from researchers, industry, and government agencies to develop, standardize, and implement quantum-resistant cryptographic solutions. The race against time to secure our digital infrastructure against the quantum threat underscores the critical importance of continued research and innovation in this field.
Current Quantum-Resistant Algorithms
01 Quantum-resistant cryptographic systems
Development of cryptographic systems that are resistant to attacks from quantum computers. These systems use algorithms and protocols designed to withstand quantum computing capabilities, ensuring data security in a post-quantum world.- Quantum-resistant cryptographic systems: Development of cryptographic systems that can withstand attacks from quantum computers. These systems use advanced mathematical algorithms and techniques to create encryption methods that are believed to be secure against both classical and quantum computing attacks.
- Quantum key distribution (QKD): Implementation of quantum key distribution protocols for secure communication. QKD uses quantum mechanical properties to generate and distribute encryption keys, providing a theoretically unbreakable method of key exchange.
- Post-quantum cryptography algorithms: Creation and optimization of cryptographic algorithms that are resistant to quantum computer attacks. These algorithms are based on mathematical problems that are believed to be difficult for quantum computers to solve, such as lattice-based cryptography and multivariate polynomial cryptography.
- Hybrid classical-quantum encryption systems: Development of encryption systems that combine classical and quantum cryptographic techniques. These hybrid systems aim to provide enhanced security by leveraging the strengths of both classical and quantum approaches, offering a transitional solution as quantum computing evolves.
- Quantum-secure blockchain technology: Integration of quantum-resistant cryptographic techniques into blockchain systems. This approach aims to protect blockchain networks and cryptocurrencies from potential threats posed by future quantum computers, ensuring long-term security and integrity of distributed ledger technologies.
02 Quantum key distribution (QKD)
Implementation of quantum key distribution techniques for secure communication. QKD uses quantum mechanical properties to generate and distribute encryption keys, providing a theoretically unbreakable method of key exchange.Expand Specific Solutions03 Hybrid classical-quantum encryption schemes
Creation of encryption methods that combine classical and quantum techniques. These hybrid schemes leverage the strengths of both approaches to enhance overall security and provide a transition path from classical to quantum-safe cryptography.Expand Specific Solutions04 Quantum random number generators
Development of quantum-based random number generators for cryptographic applications. These generators use quantum phenomena to produce truly random numbers, which are crucial for creating secure encryption keys and improving the overall strength of encryption algorithms.Expand Specific Solutions05 Post-quantum blockchain security
Integration of quantum-resistant algorithms into blockchain technology. This approach aims to secure distributed ledger systems against potential threats from quantum computers, ensuring the long-term viability and security of blockchain-based applications and cryptocurrencies.Expand Specific Solutions
Key Players in Quantum Encryption
The quantum computing landscape for advanced encryption methods is rapidly evolving, with the industry currently in its early growth stage. The market size is expanding, driven by increasing cybersecurity concerns and potential applications across various sectors. While the technology is still maturing, significant progress has been made in recent years. Key players like IBM, Intel, and Microsoft are investing heavily in quantum research and development, alongside specialized quantum computing firms such as Atom Computing and Zapata Computing. These companies are working on both hardware and software solutions, aiming to achieve quantum advantage in encryption and cryptography. The competition is fierce, with both established tech giants and innovative startups vying for leadership in this transformative field.
Atom Computing, Inc.
Technical Solution: Atom Computing specializes in neutral atom quantum computing, which offers potential advantages for certain encryption and cryptography tasks. Their Phoenix system uses optical tweezers to manipulate individual atoms, achieving high coherence times and scalability[7]. While not primarily focused on encryption, their quantum computing platform could be leveraged for quantum key distribution and the development of quantum-resistant algorithms. Atom Computing's approach allows for the creation of large qubit arrays with high fidelity, which could be particularly useful for simulating complex cryptographic systems and testing the security of existing encryption methods against quantum attacks[8].
Strengths: Scalable neutral atom technology, potential for large qubit arrays. Weaknesses: Less direct focus on encryption applications compared to some competitors.
Zapata Computing, Inc.
Technical Solution: Zapata Computing focuses on quantum software and algorithms, including applications in cryptography and security. Their Orquestra platform enables the development and deployment of quantum-classical hybrid algorithms, which can be applied to encryption challenges. Zapata has been working on quantum-inspired algorithms for optimization problems related to cryptography, such as integer factorization and discrete logarithms[9]. They also collaborate with hardware providers to test and implement quantum encryption methods on various quantum architectures. Zapata's approach includes developing quantum machine learning techniques that could potentially enhance cryptanalysis and the creation of more robust encryption schemes[10].
Strengths: Strong focus on quantum software and algorithms, platform-agnostic approach. Weaknesses: Reliance on third-party hardware for quantum computations.
Breakthrough Quantum Encryption Techniques
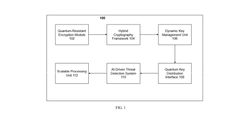
Advanced quantum-resistant encryption protocols with hybrid cryptography and dynamic key management for enhanced cloud security
PatentActiveIN202441067794A
Innovation
- A comprehensive security framework integrating quantum-resistant encryption algorithms, hybrid cryptography, dynamic key management, quantum key distribution, and AI-driven threat detection, along with a scalable processing unit to ensure efficient performance and adaptability.
Method for quantum-secured communication
PatentPendingUS20250080338A1
Innovation
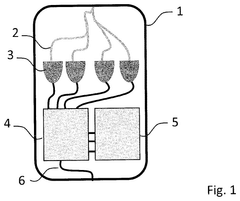
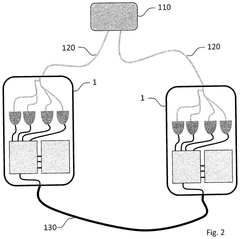
- The implementation of quantum-enabled hardware security modules (qHSM) that share a secret key over a temporarily common quantum channel, allowing for secure symmetrical encryption without the need for continuous quantum links.
Quantum Internet Infrastructure
The development of quantum internet infrastructure is a critical component in the advancement of quantum computing for encryption methods. This infrastructure aims to create a network that can transmit quantum information securely over long distances, enabling the full potential of quantum encryption technologies.
At the core of quantum internet infrastructure is the concept of quantum entanglement, which allows for the creation of unbreakable communication links. These links form the backbone of a quantum network, enabling the secure transmission of quantum states across vast distances. The implementation of quantum repeaters is crucial in overcoming the limitations of quantum state degradation over long distances, allowing for the extension of quantum networks beyond local areas.
One of the key challenges in building quantum internet infrastructure is the development of quantum memory devices. These devices are essential for storing and manipulating quantum information, enabling the creation of quantum routers and switches necessary for a functional quantum network. Current research focuses on various physical systems for quantum memory, including trapped ions, superconducting circuits, and nitrogen-vacancy centers in diamond.
The integration of existing classical internet infrastructure with quantum networks presents another significant challenge. Hybrid systems that can seamlessly transition between classical and quantum communication protocols are being developed to ensure compatibility and gradual adoption of quantum internet technologies. This approach allows for the coexistence of classical and quantum networks during the transition period.
Quantum key distribution (QKD) systems are a crucial application of quantum internet infrastructure, providing a method for generating and distributing encryption keys that are theoretically immune to eavesdropping. The implementation of satellite-based QKD systems has demonstrated the feasibility of global quantum communication networks, paving the way for intercontinental quantum-secured communication.
As quantum internet infrastructure continues to evolve, standardization efforts are underway to ensure interoperability between different quantum network implementations. Organizations such as the European Telecommunications Standards Institute (ETSI) and the International Telecommunication Union (ITU) are working on developing standards for quantum communication protocols and interfaces.
The realization of a fully functional quantum internet will revolutionize secure communication, enabling advanced encryption methods that are resistant to attacks from both classical and quantum computers. This infrastructure will not only support quantum encryption but also enable distributed quantum computing and secure multi-party quantum computations, opening up new possibilities for secure data processing and analysis in fields such as finance, healthcare, and national security.
At the core of quantum internet infrastructure is the concept of quantum entanglement, which allows for the creation of unbreakable communication links. These links form the backbone of a quantum network, enabling the secure transmission of quantum states across vast distances. The implementation of quantum repeaters is crucial in overcoming the limitations of quantum state degradation over long distances, allowing for the extension of quantum networks beyond local areas.
One of the key challenges in building quantum internet infrastructure is the development of quantum memory devices. These devices are essential for storing and manipulating quantum information, enabling the creation of quantum routers and switches necessary for a functional quantum network. Current research focuses on various physical systems for quantum memory, including trapped ions, superconducting circuits, and nitrogen-vacancy centers in diamond.
The integration of existing classical internet infrastructure with quantum networks presents another significant challenge. Hybrid systems that can seamlessly transition between classical and quantum communication protocols are being developed to ensure compatibility and gradual adoption of quantum internet technologies. This approach allows for the coexistence of classical and quantum networks during the transition period.
Quantum key distribution (QKD) systems are a crucial application of quantum internet infrastructure, providing a method for generating and distributing encryption keys that are theoretically immune to eavesdropping. The implementation of satellite-based QKD systems has demonstrated the feasibility of global quantum communication networks, paving the way for intercontinental quantum-secured communication.
As quantum internet infrastructure continues to evolve, standardization efforts are underway to ensure interoperability between different quantum network implementations. Organizations such as the European Telecommunications Standards Institute (ETSI) and the International Telecommunication Union (ITU) are working on developing standards for quantum communication protocols and interfaces.
The realization of a fully functional quantum internet will revolutionize secure communication, enabling advanced encryption methods that are resistant to attacks from both classical and quantum computers. This infrastructure will not only support quantum encryption but also enable distributed quantum computing and secure multi-party quantum computations, opening up new possibilities for secure data processing and analysis in fields such as finance, healthcare, and national security.
Quantum Cryptography Standards
Quantum cryptography standards are rapidly evolving to meet the challenges posed by the advent of quantum computing. These standards aim to ensure the security of encrypted communications in a post-quantum world. The National Institute of Standards and Technology (NIST) has been at the forefront of developing quantum-resistant cryptographic algorithms through its Post-Quantum Cryptography Standardization process.
The NIST process began in 2016 and has progressed through multiple rounds of evaluation. In July 2022, NIST announced the selection of four candidate algorithms for standardization: CRYSTALS-Kyber for general encryption, and CRYSTALS-Dilithium, FALCON, and SPHINCS+ for digital signatures. These algorithms are based on lattice-based, multivariate, and hash-based cryptography, which are believed to be resistant to attacks by both classical and quantum computers.
The European Telecommunications Standards Institute (ETSI) has also been active in developing quantum cryptography standards. ETSI's Quantum-Safe Cryptography (QSC) working group has published several specifications and guidelines for the implementation of quantum-safe cryptographic systems. These include recommendations for hybrid key exchange methods that combine classical and quantum-resistant algorithms to provide a smooth transition to post-quantum security.
In addition to post-quantum cryptography, standards are being developed for Quantum Key Distribution (QKD) systems. The International Telecommunication Union (ITU) has established the Focus Group on Quantum Information Technology for Networks (FG-QIT4N) to develop technical specifications for quantum-based communication networks. This group is working on standardizing QKD protocols, interfaces, and network architectures.
The International Organization for Standardization (ISO) and the International Electrotechnical Commission (IEC) have formed a joint technical committee (ISO/IEC JTC 1/SC 27) to develop standards for quantum-resistant cryptographic techniques. Their work includes the development of a framework for quantum-resistant algorithms and protocols, as well as guidelines for migration to quantum-safe cryptosystems.
As quantum computing technology advances, these standards will continue to evolve. Organizations and businesses are being encouraged to adopt a crypto-agile approach, allowing for the rapid replacement of cryptographic algorithms as new standards emerge. This flexibility will be crucial in maintaining security in the face of quantum threats while standards are still being finalized and implemented globally.
The NIST process began in 2016 and has progressed through multiple rounds of evaluation. In July 2022, NIST announced the selection of four candidate algorithms for standardization: CRYSTALS-Kyber for general encryption, and CRYSTALS-Dilithium, FALCON, and SPHINCS+ for digital signatures. These algorithms are based on lattice-based, multivariate, and hash-based cryptography, which are believed to be resistant to attacks by both classical and quantum computers.
The European Telecommunications Standards Institute (ETSI) has also been active in developing quantum cryptography standards. ETSI's Quantum-Safe Cryptography (QSC) working group has published several specifications and guidelines for the implementation of quantum-safe cryptographic systems. These include recommendations for hybrid key exchange methods that combine classical and quantum-resistant algorithms to provide a smooth transition to post-quantum security.
In addition to post-quantum cryptography, standards are being developed for Quantum Key Distribution (QKD) systems. The International Telecommunication Union (ITU) has established the Focus Group on Quantum Information Technology for Networks (FG-QIT4N) to develop technical specifications for quantum-based communication networks. This group is working on standardizing QKD protocols, interfaces, and network architectures.
The International Organization for Standardization (ISO) and the International Electrotechnical Commission (IEC) have formed a joint technical committee (ISO/IEC JTC 1/SC 27) to develop standards for quantum-resistant cryptographic techniques. Their work includes the development of a framework for quantum-resistant algorithms and protocols, as well as guidelines for migration to quantum-safe cryptosystems.
As quantum computing technology advances, these standards will continue to evolve. Organizations and businesses are being encouraged to adopt a crypto-agile approach, allowing for the rapid replacement of cryptographic algorithms as new standards emerge. This flexibility will be crucial in maintaining security in the face of quantum threats while standards are still being finalized and implemented globally.
Unlock deeper insights with Patsnap Eureka Quick Research — get a full tech report to explore trends and direct your research. Try now!
Generate Your Research Report Instantly with AI Agent
Supercharge your innovation with Patsnap Eureka AI Agent Platform!