Quantum Computing's Potential to Transform Cybersecurity Frameworks
JUL 17, 20259 MIN READ
Generate Your Research Report Instantly with AI Agent
Patsnap Eureka helps you evaluate technical feasibility & market potential.
Quantum Computing Evolution and Cybersecurity Goals
Quantum computing has emerged as a revolutionary technology with the potential to transform various fields, including cybersecurity. The evolution of quantum computing and its implications for cybersecurity frameworks represent a critical area of focus for researchers and industry professionals alike. As quantum computers continue to advance, they pose both opportunities and challenges for existing security paradigms.
The primary goal of quantum computing in the context of cybersecurity is to develop robust, quantum-resistant encryption methods and to leverage quantum properties for enhanced security measures. Quantum computers have the theoretical capability to break many current encryption algorithms, particularly those based on factoring large numbers or solving discrete logarithm problems. This potential threat has spurred efforts to create quantum-resistant cryptographic systems, often referred to as post-quantum cryptography.
Simultaneously, quantum computing offers promising avenues for strengthening cybersecurity frameworks. Quantum key distribution (QKD) stands out as a prime example, utilizing the principles of quantum mechanics to create theoretically unbreakable communication channels. The goal here is to achieve information-theoretic security, a level of protection that remains secure even against attackers with unlimited computational power.
Another significant objective is the development of quantum random number generators (QRNGs), which can produce truly random numbers based on quantum phenomena. These QRNGs aim to enhance the unpredictability and security of cryptographic systems, addressing vulnerabilities in traditional pseudo-random number generators.
The evolution of quantum computing also necessitates a reevaluation of existing security protocols and the development of new quantum-safe algorithms. This includes research into lattice-based cryptography, hash-based signatures, and other post-quantum cryptographic methods. The goal is to create security solutions that can withstand attacks from both classical and quantum computers.
Furthermore, quantum sensing and metrology present opportunities for detecting unauthorized intrusions or alterations in systems with unprecedented precision. These technologies aim to enhance the integrity and reliability of secure communications and data storage systems.
As quantum computing continues to advance, the cybersecurity community faces the challenge of staying ahead of potential threats while harnessing the technology's benefits. This involves not only technical developments but also the creation of new standards, policies, and best practices to govern the use of quantum technologies in cybersecurity contexts.
The primary goal of quantum computing in the context of cybersecurity is to develop robust, quantum-resistant encryption methods and to leverage quantum properties for enhanced security measures. Quantum computers have the theoretical capability to break many current encryption algorithms, particularly those based on factoring large numbers or solving discrete logarithm problems. This potential threat has spurred efforts to create quantum-resistant cryptographic systems, often referred to as post-quantum cryptography.
Simultaneously, quantum computing offers promising avenues for strengthening cybersecurity frameworks. Quantum key distribution (QKD) stands out as a prime example, utilizing the principles of quantum mechanics to create theoretically unbreakable communication channels. The goal here is to achieve information-theoretic security, a level of protection that remains secure even against attackers with unlimited computational power.
Another significant objective is the development of quantum random number generators (QRNGs), which can produce truly random numbers based on quantum phenomena. These QRNGs aim to enhance the unpredictability and security of cryptographic systems, addressing vulnerabilities in traditional pseudo-random number generators.
The evolution of quantum computing also necessitates a reevaluation of existing security protocols and the development of new quantum-safe algorithms. This includes research into lattice-based cryptography, hash-based signatures, and other post-quantum cryptographic methods. The goal is to create security solutions that can withstand attacks from both classical and quantum computers.
Furthermore, quantum sensing and metrology present opportunities for detecting unauthorized intrusions or alterations in systems with unprecedented precision. These technologies aim to enhance the integrity and reliability of secure communications and data storage systems.
As quantum computing continues to advance, the cybersecurity community faces the challenge of staying ahead of potential threats while harnessing the technology's benefits. This involves not only technical developments but also the creation of new standards, policies, and best practices to govern the use of quantum technologies in cybersecurity contexts.
Market Demand for Quantum-Resistant Cryptography
The market demand for quantum-resistant cryptography has been steadily growing as the potential threat of quantum computing to current cryptographic systems becomes more apparent. As quantum computers advance, they pose a significant risk to widely used encryption methods, particularly public-key cryptography systems such as RSA and elliptic curve cryptography. These systems form the backbone of secure communications and data protection across various sectors, including finance, healthcare, government, and telecommunications.
Financial institutions are among the most active in seeking quantum-resistant solutions. Banks, credit card companies, and investment firms handle vast amounts of sensitive financial data and transactions daily. The prospect of quantum computers breaking current encryption methods has led to increased investment in post-quantum cryptography research and development. Major banks are already exploring the integration of quantum-resistant algorithms into their existing security infrastructure.
Government agencies and defense organizations are also driving demand for quantum-resistant cryptography. National security concerns have prompted governments worldwide to invest in developing and implementing quantum-safe encryption standards. The U.S. National Institute of Standards and Technology (NIST) has been at the forefront of this effort, running a post-quantum cryptography standardization process to identify robust algorithms that can withstand quantum attacks.
In the healthcare sector, the need to protect patient data over long periods has created a strong market for quantum-resistant solutions. Medical records often require decades of secure storage, making the industry particularly vulnerable to future quantum attacks on current encryption methods. Healthcare providers and insurance companies are increasingly looking to adopt quantum-resistant encryption to ensure long-term data protection and compliance with privacy regulations.
The telecommunications industry is another significant driver of market demand for quantum-resistant cryptography. As 5G networks roll out and the Internet of Things (IoT) expands, the volume of sensitive data transmitted over these networks is set to increase exponentially. Telecom companies are investing in quantum-safe encryption to secure their infrastructure and protect customer communications from future quantum threats.
Cloud service providers and technology giants are also contributing to the growing demand. Companies like Google, IBM, and Microsoft are not only developing their own quantum computing capabilities but also investing in quantum-resistant encryption to protect their vast data centers and cloud services. These companies recognize the need to future-proof their security measures against the quantum threat.
The automotive industry, with its increasing focus on connected and autonomous vehicles, is emerging as a new market for quantum-resistant cryptography. As vehicles become more reliant on secure communication for safety-critical functions, manufacturers are exploring quantum-safe solutions to protect against long-term security risks.
Financial institutions are among the most active in seeking quantum-resistant solutions. Banks, credit card companies, and investment firms handle vast amounts of sensitive financial data and transactions daily. The prospect of quantum computers breaking current encryption methods has led to increased investment in post-quantum cryptography research and development. Major banks are already exploring the integration of quantum-resistant algorithms into their existing security infrastructure.
Government agencies and defense organizations are also driving demand for quantum-resistant cryptography. National security concerns have prompted governments worldwide to invest in developing and implementing quantum-safe encryption standards. The U.S. National Institute of Standards and Technology (NIST) has been at the forefront of this effort, running a post-quantum cryptography standardization process to identify robust algorithms that can withstand quantum attacks.
In the healthcare sector, the need to protect patient data over long periods has created a strong market for quantum-resistant solutions. Medical records often require decades of secure storage, making the industry particularly vulnerable to future quantum attacks on current encryption methods. Healthcare providers and insurance companies are increasingly looking to adopt quantum-resistant encryption to ensure long-term data protection and compliance with privacy regulations.
The telecommunications industry is another significant driver of market demand for quantum-resistant cryptography. As 5G networks roll out and the Internet of Things (IoT) expands, the volume of sensitive data transmitted over these networks is set to increase exponentially. Telecom companies are investing in quantum-safe encryption to secure their infrastructure and protect customer communications from future quantum threats.
Cloud service providers and technology giants are also contributing to the growing demand. Companies like Google, IBM, and Microsoft are not only developing their own quantum computing capabilities but also investing in quantum-resistant encryption to protect their vast data centers and cloud services. These companies recognize the need to future-proof their security measures against the quantum threat.
The automotive industry, with its increasing focus on connected and autonomous vehicles, is emerging as a new market for quantum-resistant cryptography. As vehicles become more reliant on secure communication for safety-critical functions, manufacturers are exploring quantum-safe solutions to protect against long-term security risks.
Current State of Quantum Computing in Cybersecurity
Quantum computing has emerged as a transformative technology with significant implications for cybersecurity. Currently, the field is in a state of rapid development, with both opportunities and challenges on the horizon. Major tech companies and research institutions are investing heavily in quantum computing research, focusing on its potential to revolutionize cryptography and data protection.
In the realm of cybersecurity, quantum computing presents a double-edged sword. On one hand, it threatens to break many of the encryption algorithms that form the backbone of current security protocols. RSA and ECC, widely used public-key cryptosystems, are particularly vulnerable to quantum attacks using Shor's algorithm. This potential threat has spurred the development of post-quantum cryptography (PQC) to create quantum-resistant algorithms.
On the other hand, quantum computing offers promising advancements in cybersecurity. Quantum key distribution (QKD) leverages the principles of quantum mechanics to create theoretically unbreakable encryption. Several countries and organizations are already implementing QKD networks, albeit on a limited scale due to technical challenges and high costs.
The current state of quantum computing in cybersecurity is characterized by a race between offensive and defensive capabilities. While fully functional large-scale quantum computers capable of breaking current encryption standards are still years away, the cybersecurity community is proactively developing quantum-resistant solutions. The National Institute of Standards and Technology (NIST) is leading efforts to standardize post-quantum cryptographic algorithms, with final selections expected in the near future.
Quantum sensing and quantum random number generation are other areas where quantum technologies are making inroads into cybersecurity. These applications promise enhanced detection of intrusions and improved randomness for cryptographic key generation, respectively.
However, significant challenges remain. Quantum computers are extremely sensitive to environmental disturbances, requiring sophisticated error correction techniques. Scalability is another major hurdle, with current quantum processors limited to a few hundred qubits. Despite these challenges, steady progress is being made, with quantum supremacy demonstrations by companies like Google and IBM marking important milestones.
The cybersecurity industry is actively preparing for the quantum era. Many organizations are conducting "crypto-agility" assessments to ensure their systems can quickly adapt to new cryptographic standards. There is also growing interest in hybrid classical-quantum systems that combine the strengths of both paradigms.
In the realm of cybersecurity, quantum computing presents a double-edged sword. On one hand, it threatens to break many of the encryption algorithms that form the backbone of current security protocols. RSA and ECC, widely used public-key cryptosystems, are particularly vulnerable to quantum attacks using Shor's algorithm. This potential threat has spurred the development of post-quantum cryptography (PQC) to create quantum-resistant algorithms.
On the other hand, quantum computing offers promising advancements in cybersecurity. Quantum key distribution (QKD) leverages the principles of quantum mechanics to create theoretically unbreakable encryption. Several countries and organizations are already implementing QKD networks, albeit on a limited scale due to technical challenges and high costs.
The current state of quantum computing in cybersecurity is characterized by a race between offensive and defensive capabilities. While fully functional large-scale quantum computers capable of breaking current encryption standards are still years away, the cybersecurity community is proactively developing quantum-resistant solutions. The National Institute of Standards and Technology (NIST) is leading efforts to standardize post-quantum cryptographic algorithms, with final selections expected in the near future.
Quantum sensing and quantum random number generation are other areas where quantum technologies are making inroads into cybersecurity. These applications promise enhanced detection of intrusions and improved randomness for cryptographic key generation, respectively.
However, significant challenges remain. Quantum computers are extremely sensitive to environmental disturbances, requiring sophisticated error correction techniques. Scalability is another major hurdle, with current quantum processors limited to a few hundred qubits. Despite these challenges, steady progress is being made, with quantum supremacy demonstrations by companies like Google and IBM marking important milestones.
The cybersecurity industry is actively preparing for the quantum era. Many organizations are conducting "crypto-agility" assessments to ensure their systems can quickly adapt to new cryptographic standards. There is also growing interest in hybrid classical-quantum systems that combine the strengths of both paradigms.
Existing Quantum-Safe Cryptographic Solutions
01 Quantum-resistant cryptographic algorithms
Development of cryptographic algorithms that are resistant to attacks from quantum computers. These algorithms aim to provide secure encryption and digital signatures that cannot be easily broken by quantum computing methods, ensuring long-term data protection in the post-quantum era.- Quantum-resistant cryptographic algorithms: Development of cryptographic algorithms that are resistant to attacks from quantum computers. These algorithms aim to provide secure encryption and digital signatures that cannot be easily broken by quantum computing techniques, ensuring long-term data protection in the post-quantum era.
- Quantum key distribution (QKD) systems: Implementation of quantum key distribution systems for secure communication. QKD leverages quantum mechanics principles to generate and distribute encryption keys, providing a theoretically unbreakable method of key exchange that is resistant to both classical and quantum attacks.
- Post-quantum cryptography integration: Integration of post-quantum cryptographic solutions into existing cybersecurity frameworks and infrastructure. This involves updating current systems, protocols, and applications to incorporate quantum-resistant algorithms and ensure seamless transition to quantum-safe security measures.
- Quantum random number generators: Utilization of quantum random number generators to enhance cryptographic key generation and other security processes. These generators leverage quantum phenomena to produce truly random numbers, improving the unpredictability and security of encryption systems.
- Hybrid classical-quantum security frameworks: Development of hybrid security frameworks that combine classical and quantum-resistant cryptographic methods. These frameworks aim to provide immediate protection against current threats while also preparing for future quantum-based attacks, ensuring a smooth transition to post-quantum security.
02 Quantum key distribution (QKD) systems
Implementation of quantum key distribution systems for secure communication. QKD uses quantum mechanical principles to generate and distribute encryption keys, providing a theoretically unbreakable method of key exchange that is resistant to both classical and quantum attacks.Expand Specific Solutions03 Hybrid classical-quantum security frameworks
Development of cybersecurity frameworks that combine classical and quantum technologies. These hybrid systems leverage the strengths of both approaches to create robust security solutions that can protect against current threats while preparing for future quantum-based attacks.Expand Specific Solutions04 Quantum-safe network protocols
Design and implementation of network protocols that are resistant to quantum attacks. These protocols aim to secure communication channels and data transmission in a way that remains effective even in the presence of powerful quantum computers.Expand Specific Solutions05 Post-quantum cryptography standardization
Efforts to standardize post-quantum cryptographic algorithms and protocols. This involves evaluating and selecting cryptographic systems that are believed to be secure against both classical and quantum computers, with the goal of creating widely accepted standards for quantum-resistant cybersecurity.Expand Specific Solutions
Key Players in Quantum Computing and Cybersecurity
The quantum computing landscape in cybersecurity is evolving rapidly, with the industry currently in an early development stage. The market size is growing, driven by increasing cybersecurity threats and the potential of quantum computing to revolutionize encryption methods. While the technology is not yet fully mature, significant progress is being made. Key players like IBM, Intel, and Google are investing heavily in quantum research, with startups like Arqit and Equal1 Labs focusing on quantum-safe cryptography. Established financial institutions such as Bank of America and Wells Fargo are exploring quantum applications for secure transactions. Universities and research institutions, including the University of Chicago and Beijing University of Posts & Telecommunications, are contributing to advancements in quantum cybersecurity, indicating a collaborative ecosystem between academia and industry.
Arqit Ltd.
Technical Solution: Arqit specializes in quantum encryption technology, focusing on developing symmetric key agreement protocols that are resistant to quantum attacks. Their flagship product, QuantumCloud™, uses quantum and classical technologies to create encryption keys impervious to quantum computer attacks. Arqit's approach involves satellite-based quantum key distribution (QKD) combined with terrestrial key creation methods, ensuring global coverage and scalability[8]. They are also working on quantum random number generation (QRNG) to enhance the unpredictability and security of encryption keys. Arqit's technology aims to provide a drop-in replacement for existing public key infrastructure (PKI) systems, making quantum-safe encryption accessible to a wide range of industries[9].
Strengths: Specialized focus on quantum encryption, innovative satellite-based QKD approach, and scalable solutions for various industries. Weaknesses: Reliance on satellite infrastructure may pose challenges in certain environments or regions.
Intel Corp.
Technical Solution: Intel is advancing quantum computing's impact on cybersecurity through its development of quantum-resistant cryptography and quantum simulation technologies. Their approach includes creating hardware-based security solutions that can withstand quantum attacks. Intel's Quantum-Resistant Cryptography Initiative focuses on developing and standardizing post-quantum cryptographic algorithms that can be efficiently implemented on classical computing systems[10]. They are also exploring the use of quantum simulators to test and validate quantum-resistant algorithms. Intel's Horse Ridge cryogenic control chip aims to improve the scalability of quantum systems, potentially enabling more powerful quantum computers for cryptanalysis and security applications[11].
Strengths: Strong hardware expertise, ability to integrate quantum-resistant solutions at the chip level, and extensive experience in cryptography. Weaknesses: Less focus on full-stack quantum computing solutions compared to some competitors.
Core Quantum Algorithms for Cryptanalysis
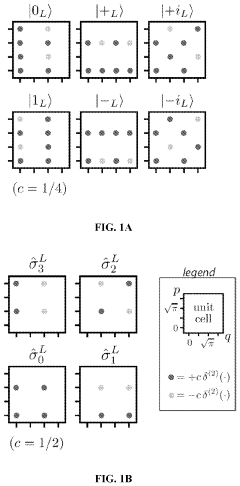
System and methods for producing magic states for universal quantum computation using GKP error correction
PatentActiveUS20220101173A1
Innovation
- The method involves producing magic states for GKP-qubit-based quantum computing using GKP error correction on a Gaussian input state, requiring only Gaussian operations and a single type of non-Gaussian state, the logical-0 state, eliminating the need for external qubits and additional non-Gaussian resources.
Quantum Computing Standards and Regulations
As quantum computing technology advances, the need for standardization and regulatory frameworks becomes increasingly critical. The development of quantum computing standards and regulations is essential to ensure interoperability, security, and ethical use of this transformative technology. Several international organizations and governmental bodies are actively working on establishing guidelines and protocols for quantum computing applications, particularly in the realm of cybersecurity.
The National Institute of Standards and Technology (NIST) in the United States has been at the forefront of developing quantum-resistant cryptographic standards. Their Post-Quantum Cryptography Standardization project aims to identify and standardize algorithms that can withstand attacks from both classical and quantum computers. This initiative is crucial for maintaining the integrity of encrypted communications in the quantum era.
In Europe, the European Telecommunications Standards Institute (ETSI) has established a Quantum-Safe Cryptography working group. This group focuses on developing specifications for quantum-safe cryptographic primitives and protocols, addressing the potential threats posed by quantum computers to current cryptographic systems. Their work complements NIST's efforts and provides a European perspective on quantum computing standards.
The International Organization for Standardization (ISO) and the International Electrotechnical Commission (IEC) have jointly formed a working group on quantum computing (ISO/IEC JTC 1/WG 14). This group is tasked with developing international standards for quantum computing, including terminology, performance benchmarking, and security considerations. Their work is essential for creating a common language and framework for quantum computing across different countries and industries.
Regulatory bodies are also beginning to address the implications of quantum computing on existing cybersecurity regulations. For instance, the European Union's General Data Protection Regulation (GDPR) may need to be updated to account for the potential impact of quantum computing on data encryption and privacy protection. Similarly, financial regulators are considering how quantum computing might affect current risk management and security protocols in the banking and finance sectors.
As quantum computing continues to evolve, it is likely that we will see the emergence of more specific regulations governing its use in sensitive applications, such as national security, healthcare, and financial services. These regulations will need to balance the potential benefits of quantum computing with the need to protect critical infrastructure and personal data from quantum-enabled attacks.
The development of quantum computing standards and regulations is an ongoing process that requires collaboration between academia, industry, and government agencies. As the technology matures, these standards and regulations will play a crucial role in shaping the future of quantum computing and its impact on cybersecurity frameworks.
The National Institute of Standards and Technology (NIST) in the United States has been at the forefront of developing quantum-resistant cryptographic standards. Their Post-Quantum Cryptography Standardization project aims to identify and standardize algorithms that can withstand attacks from both classical and quantum computers. This initiative is crucial for maintaining the integrity of encrypted communications in the quantum era.
In Europe, the European Telecommunications Standards Institute (ETSI) has established a Quantum-Safe Cryptography working group. This group focuses on developing specifications for quantum-safe cryptographic primitives and protocols, addressing the potential threats posed by quantum computers to current cryptographic systems. Their work complements NIST's efforts and provides a European perspective on quantum computing standards.
The International Organization for Standardization (ISO) and the International Electrotechnical Commission (IEC) have jointly formed a working group on quantum computing (ISO/IEC JTC 1/WG 14). This group is tasked with developing international standards for quantum computing, including terminology, performance benchmarking, and security considerations. Their work is essential for creating a common language and framework for quantum computing across different countries and industries.
Regulatory bodies are also beginning to address the implications of quantum computing on existing cybersecurity regulations. For instance, the European Union's General Data Protection Regulation (GDPR) may need to be updated to account for the potential impact of quantum computing on data encryption and privacy protection. Similarly, financial regulators are considering how quantum computing might affect current risk management and security protocols in the banking and finance sectors.
As quantum computing continues to evolve, it is likely that we will see the emergence of more specific regulations governing its use in sensitive applications, such as national security, healthcare, and financial services. These regulations will need to balance the potential benefits of quantum computing with the need to protect critical infrastructure and personal data from quantum-enabled attacks.
The development of quantum computing standards and regulations is an ongoing process that requires collaboration between academia, industry, and government agencies. As the technology matures, these standards and regulations will play a crucial role in shaping the future of quantum computing and its impact on cybersecurity frameworks.
Quantum-Resistant Infrastructure Challenges
The implementation of quantum-resistant infrastructure presents significant challenges for organizations worldwide. As quantum computing advances, traditional cryptographic systems become increasingly vulnerable, necessitating a comprehensive overhaul of existing security frameworks. One primary challenge is the development and standardization of post-quantum cryptographic algorithms. While several candidates have been proposed, their practical implementation and integration into existing systems remain complex and resource-intensive processes.
Another critical challenge lies in the transition period between current and quantum-resistant systems. Organizations must maintain backward compatibility while gradually implementing new security measures, a task that requires careful planning and execution. This transition phase may expose systems to vulnerabilities if not managed properly, potentially creating security gaps that malicious actors could exploit.
The scalability of quantum-resistant solutions poses another significant hurdle. As quantum computers grow more powerful, the computational requirements for quantum-resistant algorithms may increase, potentially straining existing hardware and network infrastructure. This scalability issue is particularly concerning for resource-constrained devices and Internet of Things (IoT) ecosystems, where implementing robust quantum-resistant measures may prove challenging due to limited processing power and memory.
Furthermore, the human factor presents a substantial challenge in the adoption of quantum-resistant infrastructure. Organizations must invest heavily in training and education to ensure that IT professionals and end-users understand the implications of quantum computing on cybersecurity and can effectively implement and use new security protocols. This knowledge gap could lead to misconfigurations or improper use of quantum-resistant technologies, potentially compromising their effectiveness.
The cost of implementing quantum-resistant infrastructure is another significant barrier. Organizations must allocate substantial resources to research, development, and deployment of new security measures, which may strain budgets, particularly for smaller enterprises. This financial burden could lead to uneven adoption of quantum-resistant technologies across different sectors and regions, potentially creating vulnerabilities in global cybersecurity ecosystems.
Lastly, the regulatory landscape surrounding quantum-resistant technologies is still evolving. The lack of clear, universally accepted standards and regulations may lead to fragmented approaches to quantum-resistant infrastructure implementation, potentially creating interoperability issues and complicating international cybersecurity efforts. As quantum computing continues to advance, addressing these challenges will be crucial for building a resilient, quantum-resistant cybersecurity infrastructure capable of protecting sensitive data and critical systems in the post-quantum era.
Another critical challenge lies in the transition period between current and quantum-resistant systems. Organizations must maintain backward compatibility while gradually implementing new security measures, a task that requires careful planning and execution. This transition phase may expose systems to vulnerabilities if not managed properly, potentially creating security gaps that malicious actors could exploit.
The scalability of quantum-resistant solutions poses another significant hurdle. As quantum computers grow more powerful, the computational requirements for quantum-resistant algorithms may increase, potentially straining existing hardware and network infrastructure. This scalability issue is particularly concerning for resource-constrained devices and Internet of Things (IoT) ecosystems, where implementing robust quantum-resistant measures may prove challenging due to limited processing power and memory.
Furthermore, the human factor presents a substantial challenge in the adoption of quantum-resistant infrastructure. Organizations must invest heavily in training and education to ensure that IT professionals and end-users understand the implications of quantum computing on cybersecurity and can effectively implement and use new security protocols. This knowledge gap could lead to misconfigurations or improper use of quantum-resistant technologies, potentially compromising their effectiveness.
The cost of implementing quantum-resistant infrastructure is another significant barrier. Organizations must allocate substantial resources to research, development, and deployment of new security measures, which may strain budgets, particularly for smaller enterprises. This financial burden could lead to uneven adoption of quantum-resistant technologies across different sectors and regions, potentially creating vulnerabilities in global cybersecurity ecosystems.
Lastly, the regulatory landscape surrounding quantum-resistant technologies is still evolving. The lack of clear, universally accepted standards and regulations may lead to fragmented approaches to quantum-resistant infrastructure implementation, potentially creating interoperability issues and complicating international cybersecurity efforts. As quantum computing continues to advance, addressing these challenges will be crucial for building a resilient, quantum-resistant cybersecurity infrastructure capable of protecting sensitive data and critical systems in the post-quantum era.
Unlock deeper insights with Patsnap Eureka Quick Research — get a full tech report to explore trends and direct your research. Try now!
Generate Your Research Report Instantly with AI Agent
Supercharge your innovation with Patsnap Eureka AI Agent Platform!