Quantum Computing Techniques for Cloud Computing Security
JUL 17, 20259 MIN READ
Generate Your Research Report Instantly with AI Agent
Patsnap Eureka helps you evaluate technical feasibility & market potential.
Quantum Computing in Cloud Security: Background and Objectives
Quantum computing has emerged as a revolutionary technology with the potential to transform various fields, including cloud computing security. The convergence of quantum computing and cloud security represents a significant shift in the landscape of information protection and data integrity. This technological fusion aims to address the growing challenges in cybersecurity while leveraging the immense computational power of quantum systems.
The evolution of quantum computing can be traced back to the early 1980s when Richard Feynman proposed the idea of using quantum mechanical effects to perform computations. Since then, the field has progressed rapidly, with major milestones including the development of quantum algorithms, the creation of the first quantum bits (qubits), and the construction of increasingly powerful quantum processors.
In the context of cloud computing security, quantum technologies offer both unprecedented opportunities and formidable challenges. On one hand, quantum computing promises to enhance encryption methods, secure communication channels, and improve data protection mechanisms. Quantum key distribution (QKD), for instance, provides a means of sharing encryption keys with theoretically unbreakable security. On the other hand, the advent of large-scale quantum computers poses a significant threat to current cryptographic systems, potentially rendering many existing security protocols obsolete.
The primary objective of integrating quantum computing techniques into cloud security is to develop robust, quantum-resistant security solutions that can withstand attacks from both classical and quantum adversaries. This involves creating new cryptographic algorithms, enhancing key management systems, and implementing quantum-safe network protocols. Additionally, researchers aim to harness quantum computing's power to detect and mitigate security threats more efficiently, potentially revolutionizing intrusion detection and prevention systems.
Another crucial goal is to establish a quantum-secure cloud infrastructure that can support the storage and processing of sensitive data in a post-quantum world. This includes developing quantum-resistant authentication mechanisms, secure multi-party computation protocols, and quantum-enhanced privacy-preserving technologies. The ultimate aim is to create a cloud ecosystem that remains secure even in the face of advanced quantum attacks.
As the field progresses, there is a growing emphasis on standardizing quantum-safe cryptographic algorithms and protocols. International bodies such as NIST are actively working on evaluating and selecting post-quantum cryptographic standards to ensure a smooth transition to quantum-resistant security measures across global cloud infrastructures.
The evolution of quantum computing can be traced back to the early 1980s when Richard Feynman proposed the idea of using quantum mechanical effects to perform computations. Since then, the field has progressed rapidly, with major milestones including the development of quantum algorithms, the creation of the first quantum bits (qubits), and the construction of increasingly powerful quantum processors.
In the context of cloud computing security, quantum technologies offer both unprecedented opportunities and formidable challenges. On one hand, quantum computing promises to enhance encryption methods, secure communication channels, and improve data protection mechanisms. Quantum key distribution (QKD), for instance, provides a means of sharing encryption keys with theoretically unbreakable security. On the other hand, the advent of large-scale quantum computers poses a significant threat to current cryptographic systems, potentially rendering many existing security protocols obsolete.
The primary objective of integrating quantum computing techniques into cloud security is to develop robust, quantum-resistant security solutions that can withstand attacks from both classical and quantum adversaries. This involves creating new cryptographic algorithms, enhancing key management systems, and implementing quantum-safe network protocols. Additionally, researchers aim to harness quantum computing's power to detect and mitigate security threats more efficiently, potentially revolutionizing intrusion detection and prevention systems.
Another crucial goal is to establish a quantum-secure cloud infrastructure that can support the storage and processing of sensitive data in a post-quantum world. This includes developing quantum-resistant authentication mechanisms, secure multi-party computation protocols, and quantum-enhanced privacy-preserving technologies. The ultimate aim is to create a cloud ecosystem that remains secure even in the face of advanced quantum attacks.
As the field progresses, there is a growing emphasis on standardizing quantum-safe cryptographic algorithms and protocols. International bodies such as NIST are actively working on evaluating and selecting post-quantum cryptographic standards to ensure a smooth transition to quantum-resistant security measures across global cloud infrastructures.
Market Analysis for Quantum-Enhanced Cloud Security
The market for quantum-enhanced cloud security solutions is experiencing rapid growth as organizations increasingly recognize the potential threats posed by quantum computing to traditional cryptographic systems. This emerging sector is driven by the need to protect sensitive data and communications in the cloud against future quantum attacks, a concern that has gained significant traction among enterprises, government agencies, and financial institutions.
Current market estimates suggest that the global quantum cryptography market, which includes quantum-enhanced cloud security, is projected to reach several billion dollars by 2025. This growth is fueled by increasing investments in quantum technologies and the rising awareness of quantum computing's potential to break existing encryption methods. Major cloud service providers, including Amazon Web Services, Google Cloud, and Microsoft Azure, have already begun integrating quantum-resistant algorithms into their security offerings, signaling a shift in the market landscape.
The demand for quantum-enhanced cloud security solutions is particularly strong in sectors handling highly sensitive data, such as finance, healthcare, and defense. These industries are at the forefront of adopting quantum-safe encryption methods to secure their cloud infrastructure. Additionally, government initiatives and regulations aimed at preparing for the post-quantum era are driving market growth, with several countries investing heavily in quantum-resistant cryptography research and development.
Key market trends include the development of hybrid classical-quantum security solutions, which combine traditional encryption methods with quantum key distribution (QKD) systems. This approach allows organizations to enhance their security posture while leveraging existing infrastructure. Another emerging trend is the integration of post-quantum cryptography (PQC) algorithms into cloud security protocols, providing a software-based solution that can be more readily deployed across existing networks.
The competitive landscape is characterized by a mix of established cybersecurity firms, quantum technology startups, and major tech giants. Companies specializing in quantum key distribution hardware, such as ID Quantique and QuintessenceLabs, are gaining traction. Simultaneously, software-focused firms developing post-quantum cryptographic solutions, like ISARA Corporation and PQShield, are attracting significant investment.
Market challenges include the high cost of implementing quantum-enhanced security solutions, the need for specialized expertise, and the current limitations in quantum technology scalability. However, these barriers are expected to diminish as the technology matures and becomes more accessible to a broader range of organizations.
In conclusion, the market for quantum-enhanced cloud security is poised for substantial growth, driven by increasing awareness of quantum threats and the need for robust, future-proof security solutions in cloud computing environments. As the technology evolves and becomes more mainstream, it is expected to reshape the cloud security landscape significantly in the coming years.
Current market estimates suggest that the global quantum cryptography market, which includes quantum-enhanced cloud security, is projected to reach several billion dollars by 2025. This growth is fueled by increasing investments in quantum technologies and the rising awareness of quantum computing's potential to break existing encryption methods. Major cloud service providers, including Amazon Web Services, Google Cloud, and Microsoft Azure, have already begun integrating quantum-resistant algorithms into their security offerings, signaling a shift in the market landscape.
The demand for quantum-enhanced cloud security solutions is particularly strong in sectors handling highly sensitive data, such as finance, healthcare, and defense. These industries are at the forefront of adopting quantum-safe encryption methods to secure their cloud infrastructure. Additionally, government initiatives and regulations aimed at preparing for the post-quantum era are driving market growth, with several countries investing heavily in quantum-resistant cryptography research and development.
Key market trends include the development of hybrid classical-quantum security solutions, which combine traditional encryption methods with quantum key distribution (QKD) systems. This approach allows organizations to enhance their security posture while leveraging existing infrastructure. Another emerging trend is the integration of post-quantum cryptography (PQC) algorithms into cloud security protocols, providing a software-based solution that can be more readily deployed across existing networks.
The competitive landscape is characterized by a mix of established cybersecurity firms, quantum technology startups, and major tech giants. Companies specializing in quantum key distribution hardware, such as ID Quantique and QuintessenceLabs, are gaining traction. Simultaneously, software-focused firms developing post-quantum cryptographic solutions, like ISARA Corporation and PQShield, are attracting significant investment.
Market challenges include the high cost of implementing quantum-enhanced security solutions, the need for specialized expertise, and the current limitations in quantum technology scalability. However, these barriers are expected to diminish as the technology matures and becomes more accessible to a broader range of organizations.
In conclusion, the market for quantum-enhanced cloud security is poised for substantial growth, driven by increasing awareness of quantum threats and the need for robust, future-proof security solutions in cloud computing environments. As the technology evolves and becomes more mainstream, it is expected to reshape the cloud security landscape significantly in the coming years.
Current State and Challenges in Quantum-Secure Cloud Computing
The current state of quantum-secure cloud computing is characterized by a complex interplay of technological advancements and persistent challenges. As quantum computing capabilities continue to evolve, the potential threat to traditional cryptographic systems used in cloud security becomes increasingly apparent. This has led to a surge in research and development efforts focused on quantum-resistant cryptographic algorithms and protocols.
One of the primary challenges in this field is the development and implementation of post-quantum cryptography (PQC) solutions that can withstand attacks from both classical and quantum computers. While several promising PQC algorithms have been proposed, their integration into existing cloud infrastructure presents significant technical hurdles. These include issues related to key size, computational overhead, and compatibility with legacy systems.
Another critical challenge is the need for quantum-safe key distribution mechanisms. Quantum Key Distribution (QKD) has emerged as a potential solution, offering theoretically unbreakable security based on the principles of quantum mechanics. However, the practical implementation of QKD in cloud environments faces limitations in terms of distance, scalability, and cost-effectiveness.
The current state of quantum-secure cloud computing also involves addressing the vulnerabilities in existing cryptographic systems. Many cloud service providers are in the process of assessing their cryptographic infrastructures and developing transition strategies to quantum-resistant algorithms. This transition is complicated by the need to maintain backward compatibility and ensure minimal disruption to existing services.
Furthermore, there is an ongoing challenge in standardizing quantum-resistant cryptographic protocols. Organizations such as NIST are working on evaluating and standardizing post-quantum cryptographic algorithms, but this process is time-consuming and requires extensive testing and validation.
Another significant challenge lies in the development of quantum-resistant hardware security modules (HSMs) and trusted platform modules (TPMs). These components play a crucial role in securing cloud infrastructure, and their adaptation to quantum-resistant algorithms is essential for comprehensive quantum security.
The field is also grappling with the challenge of quantum-safe identity and access management (IAM) systems. As quantum computers threaten current public-key cryptography, new approaches to secure authentication and authorization in cloud environments are being explored, including lattice-based and multivariate cryptographic schemes.
In conclusion, while significant progress has been made in developing quantum-secure technologies for cloud computing, the field faces numerous challenges in terms of implementation, standardization, and integration with existing systems. The race to achieve quantum security in cloud computing continues to drive innovation and collaboration across academia, industry, and government sectors.
One of the primary challenges in this field is the development and implementation of post-quantum cryptography (PQC) solutions that can withstand attacks from both classical and quantum computers. While several promising PQC algorithms have been proposed, their integration into existing cloud infrastructure presents significant technical hurdles. These include issues related to key size, computational overhead, and compatibility with legacy systems.
Another critical challenge is the need for quantum-safe key distribution mechanisms. Quantum Key Distribution (QKD) has emerged as a potential solution, offering theoretically unbreakable security based on the principles of quantum mechanics. However, the practical implementation of QKD in cloud environments faces limitations in terms of distance, scalability, and cost-effectiveness.
The current state of quantum-secure cloud computing also involves addressing the vulnerabilities in existing cryptographic systems. Many cloud service providers are in the process of assessing their cryptographic infrastructures and developing transition strategies to quantum-resistant algorithms. This transition is complicated by the need to maintain backward compatibility and ensure minimal disruption to existing services.
Furthermore, there is an ongoing challenge in standardizing quantum-resistant cryptographic protocols. Organizations such as NIST are working on evaluating and standardizing post-quantum cryptographic algorithms, but this process is time-consuming and requires extensive testing and validation.
Another significant challenge lies in the development of quantum-resistant hardware security modules (HSMs) and trusted platform modules (TPMs). These components play a crucial role in securing cloud infrastructure, and their adaptation to quantum-resistant algorithms is essential for comprehensive quantum security.
The field is also grappling with the challenge of quantum-safe identity and access management (IAM) systems. As quantum computers threaten current public-key cryptography, new approaches to secure authentication and authorization in cloud environments are being explored, including lattice-based and multivariate cryptographic schemes.
In conclusion, while significant progress has been made in developing quantum-secure technologies for cloud computing, the field faces numerous challenges in terms of implementation, standardization, and integration with existing systems. The race to achieve quantum security in cloud computing continues to drive innovation and collaboration across academia, industry, and government sectors.
Existing Quantum-Safe Cloud Security Solutions
01 Quantum-resistant cryptography
Developing cryptographic algorithms that are resistant to attacks from quantum computers. This includes post-quantum cryptography techniques and quantum key distribution systems to ensure secure communication in the quantum era.- Quantum-resistant cryptography: Developing cryptographic algorithms that are resistant to attacks from quantum computers. This includes post-quantum cryptography techniques and quantum key distribution methods to ensure secure communication in the quantum era.
- Quantum random number generation: Utilizing quantum phenomena to generate truly random numbers for enhanced security in various applications, including encryption and secure communication protocols.
- Quantum-safe blockchain: Developing blockchain technologies that are resistant to quantum attacks, ensuring the long-term security and integrity of distributed ledger systems in the face of quantum computing advancements.
- Quantum entanglement for secure communication: Leveraging quantum entanglement properties to create secure communication channels that are theoretically impossible to intercept without detection, enhancing the security of sensitive data transmission.
- Quantum-safe network protocols: Developing and implementing network protocols that are resistant to quantum attacks, ensuring the security of internet infrastructure and communication systems in the quantum computing era.
02 Quantum random number generation
Utilizing quantum phenomena to generate truly random numbers for enhancing cryptographic key generation and other security applications. This technique improves the unpredictability and security of encryption systems.Expand Specific Solutions03 Quantum-safe blockchain
Developing blockchain technologies that are resistant to quantum attacks. This includes modifying existing blockchain protocols or creating new ones that incorporate quantum-resistant cryptographic algorithms to protect digital assets and transactions.Expand Specific Solutions04 Quantum entanglement for secure communication
Leveraging quantum entanglement properties for secure communication channels. This technique allows for the detection of eavesdropping attempts and ensures the integrity of transmitted information.Expand Specific Solutions05 Quantum-enhanced machine learning for cybersecurity
Applying quantum computing techniques to enhance machine learning algorithms used in cybersecurity applications. This includes improving threat detection, anomaly identification, and predictive analysis of potential security breaches.Expand Specific Solutions
Key Players in Quantum Computing and Cloud Security
The quantum computing techniques for cloud computing security market is in its early stages of development, with significant potential for growth. The market size is expanding rapidly as organizations recognize the importance of quantum-resistant security solutions. While the technology is still maturing, several key players are making substantial advancements. Companies like IBM, Alibaba, and Huawei are investing heavily in quantum computing research and development, focusing on cloud security applications. Startups such as Arqit and QuantumCTek are also emerging as innovative forces in this space. The competitive landscape is characterized by a mix of established tech giants and specialized quantum computing firms, all vying to develop and commercialize quantum-safe encryption methods for cloud environments.
Alibaba Group Holding Ltd.
Technical Solution: Alibaba has developed a quantum-resistant cloud security solution that focuses on post-quantum cryptography (PQC) algorithms. Their approach includes implementing lattice-based and hash-based cryptographic schemes, which are considered resistant to quantum attacks. Alibaba Cloud has integrated these PQC algorithms into their key management service, allowing customers to generate and manage quantum-resistant keys[4]. They have also developed a quantum-safe Virtual Private Network (VPN) solution that uses PQC algorithms for key exchange and digital signatures[5]. Additionally, Alibaba has been working on a hybrid quantum-classical cloud platform that leverages both quantum and classical resources for enhanced security and computational capabilities[6].
Strengths: Strong focus on practical implementation of post-quantum cryptography; Integration with existing cloud services; Large-scale testing and deployment capabilities. Weaknesses: Limited experience in quantum hardware development compared to some competitors; Potential challenges in global adoption due to geopolitical concerns.
International Business Machines Corp.
Technical Solution: IBM has developed a quantum-safe cryptography solution for cloud computing security. Their approach combines traditional cryptographic algorithms with quantum-resistant ones to create hybrid cryptosystems. These systems can protect against both classical and quantum attacks. IBM's quantum-safe cryptography uses lattice-based cryptography, specifically the Ring-Learning With Errors (Ring-LWE) problem, which is believed to be resistant to quantum attacks[1]. They have also implemented a Quantum Random Number Generator (QRNG) to enhance the security of encryption keys[2]. IBM's quantum network allows for secure key distribution using Quantum Key Distribution (QKD) protocols, providing an additional layer of security for cloud communications[3].
Strengths: Comprehensive approach combining classical and quantum-resistant algorithms; Integration with existing cloud infrastructure; Backed by IBM's extensive research in quantum computing. Weaknesses: Potential performance overhead due to hybrid cryptosystems; Reliance on the unproven long-term security of lattice-based cryptography.
Core Quantum Algorithms for Enhanced Cloud Security
Advanced quantum-resistant encryption protocols with hybrid cryptography and dynamic key management for enhanced cloud security
PatentActiveIN202441067794A
Innovation
- A comprehensive security framework integrating quantum-resistant encryption algorithms, hybrid cryptography, dynamic key management, quantum key distribution, and AI-driven threat detection, along with a scalable processing unit to ensure efficient performance and adaptability.
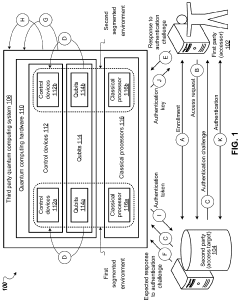
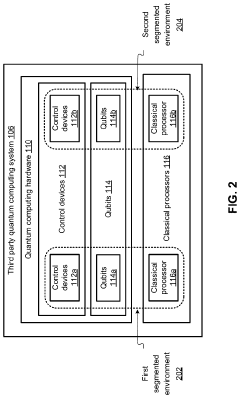
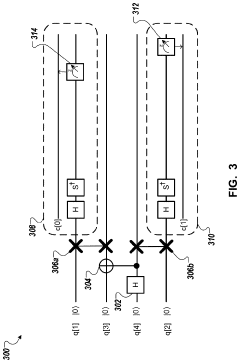
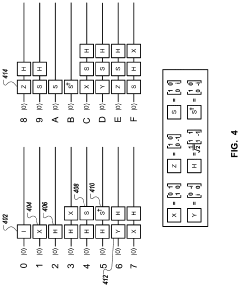
Authentication using key distribution through segmented quantum computing environments
PatentActiveUS20210377034A1
Innovation
- The use of quantum key distribution through segmented quantum computing environments to generate and manage encryption keys and authorization tokens, ensuring secure authentication and authorization by performing quantum computations within independent and ephemeral computing environments.
Quantum Computing Standards and Regulations
The development of quantum computing has necessitated the creation of new standards and regulations to ensure the security, interoperability, and ethical use of this powerful technology. Several international organizations and governmental bodies are actively working on establishing frameworks for quantum computing standards and regulations.
The International Organization for Standardization (ISO) and the International Electrotechnical Commission (IEC) have formed a joint technical committee, ISO/IEC JTC 1/SC 27, focusing on quantum computing security standards. This committee is developing guidelines for quantum-resistant cryptographic algorithms and protocols to protect cloud computing systems from potential quantum attacks.
In the United States, the National Institute of Standards and Technology (NIST) is leading efforts to standardize post-quantum cryptography. NIST's Post-Quantum Cryptography Standardization project aims to identify and evaluate quantum-resistant public-key cryptographic algorithms for use in cloud computing and other digital systems.
The European Telecommunications Standards Institute (ETSI) has established a Quantum-Safe Cryptography working group to develop standards for quantum-safe key exchanges and digital signatures. These standards are crucial for ensuring the security of cloud computing infrastructures in the quantum era.
Regulatory bodies are also addressing the implications of quantum computing for data protection and privacy. The European Union's General Data Protection Regulation (GDPR) is being reviewed to consider the potential impact of quantum computing on data encryption and privacy safeguards in cloud environments.
In China, the National Development and Reform Commission has included quantum computing in its strategic emerging industries plan, emphasizing the need for standards and regulations to guide the technology's development and application in cloud security.
The IEEE Standards Association has launched the Quantum Computing Working Group (IEEE P7130) to develop standards for quantum computing terminology and performance metrics. These standards will help ensure consistency and comparability in quantum computing applications for cloud security.
As quantum computing advances, international collaboration on standards and regulations becomes increasingly important. The Quantum Economic Development Consortium (QED-C) is working to facilitate global cooperation in quantum technology standardization, including its applications in cloud computing security.
Emerging regulations are also addressing the ethical implications of quantum computing in cloud security. The World Economic Forum's Global Future Council on Quantum Computing is developing guidelines for responsible quantum computing practices, including considerations for data privacy and security in cloud environments.
The International Organization for Standardization (ISO) and the International Electrotechnical Commission (IEC) have formed a joint technical committee, ISO/IEC JTC 1/SC 27, focusing on quantum computing security standards. This committee is developing guidelines for quantum-resistant cryptographic algorithms and protocols to protect cloud computing systems from potential quantum attacks.
In the United States, the National Institute of Standards and Technology (NIST) is leading efforts to standardize post-quantum cryptography. NIST's Post-Quantum Cryptography Standardization project aims to identify and evaluate quantum-resistant public-key cryptographic algorithms for use in cloud computing and other digital systems.
The European Telecommunications Standards Institute (ETSI) has established a Quantum-Safe Cryptography working group to develop standards for quantum-safe key exchanges and digital signatures. These standards are crucial for ensuring the security of cloud computing infrastructures in the quantum era.
Regulatory bodies are also addressing the implications of quantum computing for data protection and privacy. The European Union's General Data Protection Regulation (GDPR) is being reviewed to consider the potential impact of quantum computing on data encryption and privacy safeguards in cloud environments.
In China, the National Development and Reform Commission has included quantum computing in its strategic emerging industries plan, emphasizing the need for standards and regulations to guide the technology's development and application in cloud security.
The IEEE Standards Association has launched the Quantum Computing Working Group (IEEE P7130) to develop standards for quantum computing terminology and performance metrics. These standards will help ensure consistency and comparability in quantum computing applications for cloud security.
As quantum computing advances, international collaboration on standards and regulations becomes increasingly important. The Quantum Economic Development Consortium (QED-C) is working to facilitate global cooperation in quantum technology standardization, including its applications in cloud computing security.
Emerging regulations are also addressing the ethical implications of quantum computing in cloud security. The World Economic Forum's Global Future Council on Quantum Computing is developing guidelines for responsible quantum computing practices, including considerations for data privacy and security in cloud environments.
Quantum-Classical Hybrid Security Architectures
Quantum-Classical Hybrid Security Architectures represent a promising approach to enhancing cloud computing security by leveraging the strengths of both quantum and classical computing systems. These architectures aim to combine the computational power and unique properties of quantum systems with the reliability and widespread infrastructure of classical systems to create robust security solutions.
At the core of these hybrid architectures is the concept of quantum-assisted classical cryptography. This approach utilizes quantum key distribution (QKD) to generate and distribute encryption keys securely, while classical encryption algorithms handle the actual data encryption and decryption processes. By integrating QKD into existing classical security protocols, these hybrid systems can significantly enhance the overall security of cloud computing environments.
One key advantage of quantum-classical hybrid architectures is their ability to provide long-term security. While current classical encryption methods may become vulnerable to future quantum attacks, hybrid systems can adapt by incorporating quantum-resistant algorithms and continuously updating their quantum components. This flexibility ensures that cloud security measures can evolve alongside advancements in quantum computing technology.
Implementing quantum-classical hybrid architectures in cloud computing environments presents several challenges. These include the need for specialized hardware to support quantum operations, the development of interfaces between quantum and classical systems, and the integration of quantum-enhanced security protocols into existing cloud infrastructure. However, ongoing research and development efforts are addressing these challenges, with several proof-of-concept demonstrations already showing promising results.
A notable feature of these hybrid architectures is their potential to offer quantum-enhanced authentication and access control mechanisms. By leveraging quantum phenomena such as superposition and entanglement, these systems can create unforgeable quantum tokens or signatures, providing an additional layer of security for user authentication and data access in cloud environments.
Furthermore, quantum-classical hybrid architectures open up possibilities for advanced threat detection and response capabilities. Quantum algorithms can be employed to analyze complex patterns and anomalies in network traffic, potentially identifying security breaches or malicious activities faster and more accurately than classical methods alone. This quantum-enhanced threat intelligence can then be seamlessly integrated into classical security information and event management (SIEM) systems, enabling more effective and timely responses to security incidents in cloud environments.
At the core of these hybrid architectures is the concept of quantum-assisted classical cryptography. This approach utilizes quantum key distribution (QKD) to generate and distribute encryption keys securely, while classical encryption algorithms handle the actual data encryption and decryption processes. By integrating QKD into existing classical security protocols, these hybrid systems can significantly enhance the overall security of cloud computing environments.
One key advantage of quantum-classical hybrid architectures is their ability to provide long-term security. While current classical encryption methods may become vulnerable to future quantum attacks, hybrid systems can adapt by incorporating quantum-resistant algorithms and continuously updating their quantum components. This flexibility ensures that cloud security measures can evolve alongside advancements in quantum computing technology.
Implementing quantum-classical hybrid architectures in cloud computing environments presents several challenges. These include the need for specialized hardware to support quantum operations, the development of interfaces between quantum and classical systems, and the integration of quantum-enhanced security protocols into existing cloud infrastructure. However, ongoing research and development efforts are addressing these challenges, with several proof-of-concept demonstrations already showing promising results.
A notable feature of these hybrid architectures is their potential to offer quantum-enhanced authentication and access control mechanisms. By leveraging quantum phenomena such as superposition and entanglement, these systems can create unforgeable quantum tokens or signatures, providing an additional layer of security for user authentication and data access in cloud environments.
Furthermore, quantum-classical hybrid architectures open up possibilities for advanced threat detection and response capabilities. Quantum algorithms can be employed to analyze complex patterns and anomalies in network traffic, potentially identifying security breaches or malicious activities faster and more accurately than classical methods alone. This quantum-enhanced threat intelligence can then be seamlessly integrated into classical security information and event management (SIEM) systems, enabling more effective and timely responses to security incidents in cloud environments.
Unlock deeper insights with Patsnap Eureka Quick Research — get a full tech report to explore trends and direct your research. Try now!
Generate Your Research Report Instantly with AI Agent
Supercharge your innovation with Patsnap Eureka AI Agent Platform!