Quantum Computing Techniques for Enhanced Cyber Threat Intelligence
JUL 17, 20259 MIN READ
Generate Your Research Report Instantly with AI Agent
Patsnap Eureka helps you evaluate technical feasibility & market potential.
Quantum CTI Background
Quantum Computing Techniques for Enhanced Cyber Threat Intelligence (CTI) represent a cutting-edge intersection of quantum physics and cybersecurity. This emerging field leverages the unique properties of quantum systems to revolutionize the way we detect, analyze, and respond to cyber threats. The development of quantum CTI is driven by the increasing sophistication of cyber attacks and the limitations of classical computing in addressing complex cybersecurity challenges.
The foundation of quantum CTI lies in the principles of quantum mechanics, particularly superposition and entanglement. These quantum phenomena allow for the processing of vast amounts of data simultaneously, enabling more comprehensive and rapid threat analysis. Quantum computing's ability to solve certain problems exponentially faster than classical computers makes it particularly suited for cryptography, pattern recognition, and anomaly detection – all crucial components of effective cyber threat intelligence.
The evolution of quantum CTI is closely tied to advancements in quantum hardware and algorithms. Early quantum computers, while limited in capabilities, demonstrated potential in solving optimization problems relevant to cybersecurity. As quantum systems have grown in qubit count and stability, their application to CTI has expanded. Current research focuses on developing quantum algorithms specifically tailored for threat detection and analysis, as well as creating quantum-resistant encryption methods to safeguard against future quantum-enabled attacks.
One of the primary drivers for quantum CTI is the looming threat of quantum computers breaking current encryption standards. This potential vulnerability has spurred research into post-quantum cryptography and quantum key distribution, aiming to create secure communication channels that can withstand attacks from both classical and quantum adversaries. Simultaneously, quantum sensing technologies are being explored for their potential to detect subtle intrusions and anomalies in network traffic that might elude classical detection methods.
The integration of quantum techniques into CTI workflows presents both opportunities and challenges. While quantum computing offers unprecedented processing power for complex threat analysis, it also requires significant expertise to implement and interpret results effectively. Organizations and researchers are working to bridge the gap between quantum theory and practical cybersecurity applications, developing tools and frameworks that can harness quantum capabilities within existing CTI infrastructures.
As the field of quantum CTI continues to mature, it promises to enhance various aspects of cybersecurity, including threat prediction, real-time attack detection, and automated response mechanisms. The potential for quantum-enhanced machine learning algorithms to identify previously unknown threat patterns and behaviors is particularly exciting, potentially ushering in a new era of proactive cybersecurity measures.
The foundation of quantum CTI lies in the principles of quantum mechanics, particularly superposition and entanglement. These quantum phenomena allow for the processing of vast amounts of data simultaneously, enabling more comprehensive and rapid threat analysis. Quantum computing's ability to solve certain problems exponentially faster than classical computers makes it particularly suited for cryptography, pattern recognition, and anomaly detection – all crucial components of effective cyber threat intelligence.
The evolution of quantum CTI is closely tied to advancements in quantum hardware and algorithms. Early quantum computers, while limited in capabilities, demonstrated potential in solving optimization problems relevant to cybersecurity. As quantum systems have grown in qubit count and stability, their application to CTI has expanded. Current research focuses on developing quantum algorithms specifically tailored for threat detection and analysis, as well as creating quantum-resistant encryption methods to safeguard against future quantum-enabled attacks.
One of the primary drivers for quantum CTI is the looming threat of quantum computers breaking current encryption standards. This potential vulnerability has spurred research into post-quantum cryptography and quantum key distribution, aiming to create secure communication channels that can withstand attacks from both classical and quantum adversaries. Simultaneously, quantum sensing technologies are being explored for their potential to detect subtle intrusions and anomalies in network traffic that might elude classical detection methods.
The integration of quantum techniques into CTI workflows presents both opportunities and challenges. While quantum computing offers unprecedented processing power for complex threat analysis, it also requires significant expertise to implement and interpret results effectively. Organizations and researchers are working to bridge the gap between quantum theory and practical cybersecurity applications, developing tools and frameworks that can harness quantum capabilities within existing CTI infrastructures.
As the field of quantum CTI continues to mature, it promises to enhance various aspects of cybersecurity, including threat prediction, real-time attack detection, and automated response mechanisms. The potential for quantum-enhanced machine learning algorithms to identify previously unknown threat patterns and behaviors is particularly exciting, potentially ushering in a new era of proactive cybersecurity measures.
Quantum CTI Market
The quantum cyber threat intelligence (CTI) market is experiencing rapid growth as organizations seek advanced solutions to combat increasingly sophisticated cyber threats. This emerging sector combines the power of quantum computing with traditional CTI methodologies to enhance threat detection, analysis, and response capabilities.
Market demand for quantum CTI solutions is driven by the escalating complexity and frequency of cyberattacks, coupled with the limitations of classical computing in addressing these challenges. As quantum technologies mature, their potential to revolutionize cybersecurity becomes more apparent, attracting significant interest from both government and private sector entities.
The global quantum CTI market is projected to expand substantially over the next decade, with estimates suggesting a compound annual growth rate (CAGR) exceeding 20% through 2030. This growth is fueled by increasing investments in quantum research and development, as well as the rising adoption of quantum-inspired algorithms in cybersecurity applications.
Key market segments within the quantum CTI space include quantum-resistant cryptography, quantum key distribution (QKD) systems, and quantum-enhanced machine learning for threat analysis. Each of these segments addresses specific vulnerabilities and challenges in the cybersecurity landscape, contributing to the overall market expansion.
Geographically, North America currently leads the quantum CTI market, driven by substantial government funding and a robust ecosystem of quantum technology companies. However, Europe and Asia-Pacific regions are rapidly catching up, with countries like China, Japan, and Germany making significant strides in quantum research and commercialization.
Industry trends indicate a growing convergence between quantum computing and artificial intelligence in the CTI domain. This synergy is expected to yield more powerful and efficient threat intelligence platforms capable of processing vast amounts of data and identifying complex attack patterns in real-time.
The market is also witnessing increased collaboration between quantum technology providers, cybersecurity firms, and academic institutions. These partnerships aim to accelerate the development and deployment of practical quantum CTI solutions, bridging the gap between theoretical research and real-world applications.
As the quantum CTI market evolves, challenges such as high implementation costs, technical complexity, and the need for specialized expertise are being addressed through innovative business models and training programs. This is expected to lower barriers to entry and drive wider adoption across various industries, further expanding the market potential.
Market demand for quantum CTI solutions is driven by the escalating complexity and frequency of cyberattacks, coupled with the limitations of classical computing in addressing these challenges. As quantum technologies mature, their potential to revolutionize cybersecurity becomes more apparent, attracting significant interest from both government and private sector entities.
The global quantum CTI market is projected to expand substantially over the next decade, with estimates suggesting a compound annual growth rate (CAGR) exceeding 20% through 2030. This growth is fueled by increasing investments in quantum research and development, as well as the rising adoption of quantum-inspired algorithms in cybersecurity applications.
Key market segments within the quantum CTI space include quantum-resistant cryptography, quantum key distribution (QKD) systems, and quantum-enhanced machine learning for threat analysis. Each of these segments addresses specific vulnerabilities and challenges in the cybersecurity landscape, contributing to the overall market expansion.
Geographically, North America currently leads the quantum CTI market, driven by substantial government funding and a robust ecosystem of quantum technology companies. However, Europe and Asia-Pacific regions are rapidly catching up, with countries like China, Japan, and Germany making significant strides in quantum research and commercialization.
Industry trends indicate a growing convergence between quantum computing and artificial intelligence in the CTI domain. This synergy is expected to yield more powerful and efficient threat intelligence platforms capable of processing vast amounts of data and identifying complex attack patterns in real-time.
The market is also witnessing increased collaboration between quantum technology providers, cybersecurity firms, and academic institutions. These partnerships aim to accelerate the development and deployment of practical quantum CTI solutions, bridging the gap between theoretical research and real-world applications.
As the quantum CTI market evolves, challenges such as high implementation costs, technical complexity, and the need for specialized expertise are being addressed through innovative business models and training programs. This is expected to lower barriers to entry and drive wider adoption across various industries, further expanding the market potential.
Quantum CTI Challenges
The integration of quantum computing techniques into cyber threat intelligence (CTI) presents significant challenges that must be addressed for effective implementation. One primary challenge is the current limitations in quantum hardware. While quantum computers have shown promise in solving complex problems, they are still in their infancy and lack the stability and scalability required for widespread CTI applications. Quantum systems are highly sensitive to environmental disturbances, leading to decoherence and errors in computations, which can compromise the reliability of threat intelligence analysis.
Another major challenge lies in the development of quantum-resistant cryptography. As quantum computers advance, they pose a potential threat to existing encryption methods, particularly those based on factoring large numbers or solving discrete logarithm problems. This necessitates the urgent development and implementation of post-quantum cryptographic algorithms to safeguard sensitive CTI data and communications. The transition to quantum-resistant cryptography is a complex process that requires significant resources and coordination across the cybersecurity industry.
The shortage of skilled professionals with expertise in both quantum computing and cybersecurity presents a significant hurdle. The interdisciplinary nature of quantum CTI demands a workforce that can bridge the gap between these two complex fields. Training and educating professionals to understand quantum algorithms, quantum error correction, and their applications in threat intelligence is a time-consuming and challenging process.
Data integration and compatibility issues also pose challenges in quantum CTI. Existing CTI systems and databases are designed for classical computing architectures. Adapting these systems to work with quantum algorithms and quantum data structures requires substantial re-engineering and may lead to compatibility issues with legacy systems. This transition could potentially disrupt existing CTI workflows and require significant investments in infrastructure upgrades.
Furthermore, the ethical and legal implications of quantum-enhanced CTI raise concerns. The potential for quantum computers to break current encryption methods could lead to privacy violations and legal challenges. Establishing new regulatory frameworks and international agreements to govern the use of quantum technologies in cybersecurity is crucial but complex, given the rapidly evolving nature of the field.
Lastly, the high costs associated with quantum computing research and development present a significant barrier to entry for many organizations. The specialized equipment, extreme cooling requirements, and ongoing maintenance of quantum systems demand substantial financial resources. This economic challenge may limit the adoption of quantum CTI techniques to only the largest and most well-funded organizations, potentially creating a significant disparity in cybersecurity capabilities across different sectors and organizations.
Another major challenge lies in the development of quantum-resistant cryptography. As quantum computers advance, they pose a potential threat to existing encryption methods, particularly those based on factoring large numbers or solving discrete logarithm problems. This necessitates the urgent development and implementation of post-quantum cryptographic algorithms to safeguard sensitive CTI data and communications. The transition to quantum-resistant cryptography is a complex process that requires significant resources and coordination across the cybersecurity industry.
The shortage of skilled professionals with expertise in both quantum computing and cybersecurity presents a significant hurdle. The interdisciplinary nature of quantum CTI demands a workforce that can bridge the gap between these two complex fields. Training and educating professionals to understand quantum algorithms, quantum error correction, and their applications in threat intelligence is a time-consuming and challenging process.
Data integration and compatibility issues also pose challenges in quantum CTI. Existing CTI systems and databases are designed for classical computing architectures. Adapting these systems to work with quantum algorithms and quantum data structures requires substantial re-engineering and may lead to compatibility issues with legacy systems. This transition could potentially disrupt existing CTI workflows and require significant investments in infrastructure upgrades.
Furthermore, the ethical and legal implications of quantum-enhanced CTI raise concerns. The potential for quantum computers to break current encryption methods could lead to privacy violations and legal challenges. Establishing new regulatory frameworks and international agreements to govern the use of quantum technologies in cybersecurity is crucial but complex, given the rapidly evolving nature of the field.
Lastly, the high costs associated with quantum computing research and development present a significant barrier to entry for many organizations. The specialized equipment, extreme cooling requirements, and ongoing maintenance of quantum systems demand substantial financial resources. This economic challenge may limit the adoption of quantum CTI techniques to only the largest and most well-funded organizations, potentially creating a significant disparity in cybersecurity capabilities across different sectors and organizations.
Current Quantum CTI
01 Quantum-resistant cryptography for cyber threat intelligence
Implementing quantum-resistant cryptographic algorithms to protect sensitive cyber threat intelligence data from potential quantum computing attacks. This approach ensures that encrypted information remains secure even in the face of advanced quantum computing capabilities.- Quantum-resistant cryptography for cyber threat intelligence: Implementing quantum-resistant cryptographic algorithms to protect sensitive data and communications in cyber threat intelligence systems. This approach helps safeguard information against potential attacks from quantum computers, ensuring long-term security of threat intelligence data.
- Quantum machine learning for threat detection and analysis: Utilizing quantum machine learning algorithms to enhance threat detection capabilities and improve the analysis of complex cyber threat patterns. This technique leverages the power of quantum computing to process vast amounts of data and identify subtle correlations that traditional systems might miss.
- Quantum-enhanced network traffic analysis: Applying quantum computing techniques to analyze network traffic patterns and identify potential cyber threats in real-time. This approach enables faster and more accurate detection of anomalies and malicious activities within network communications.
- Quantum key distribution for secure threat intelligence sharing: Implementing quantum key distribution protocols to ensure secure sharing of cyber threat intelligence among organizations and agencies. This method provides a quantum-safe way to exchange encryption keys, protecting sensitive threat information from interception and unauthorized access.
- Quantum simulation of cyber attacks for improved defense strategies: Using quantum simulators to model complex cyber attack scenarios and test defense strategies. This technique allows for more accurate prediction of potential threats and helps in developing more effective countermeasures against sophisticated cyber attacks.
02 Quantum machine learning for threat detection
Utilizing quantum machine learning algorithms to enhance the detection and analysis of cyber threats. These techniques can process vast amounts of data more efficiently than classical methods, potentially identifying complex patterns and anomalies that indicate sophisticated cyber attacks.Expand Specific Solutions03 Quantum-enhanced network traffic analysis
Applying quantum computing techniques to analyze network traffic at unprecedented speeds and depths. This approach can help identify potential threats in real-time by processing and correlating massive amounts of network data, enabling faster and more accurate threat intelligence.Expand Specific Solutions04 Quantum key distribution for secure communication
Implementing quantum key distribution systems to ensure secure communication channels for sharing cyber threat intelligence. This technology leverages quantum mechanics principles to create unbreakable encryption keys, protecting sensitive information from interception and tampering.Expand Specific Solutions05 Quantum simulation of cyber attacks
Using quantum computing to simulate complex cyber attack scenarios and test defense strategies. This approach allows for more accurate modeling of sophisticated threats, helping organizations better prepare for and respond to potential attacks in the rapidly evolving cybersecurity landscape.Expand Specific Solutions
Quantum CTI Players
The quantum computing techniques for enhanced cyber threat intelligence field is in its early developmental stage, with significant potential for growth. The market size is expanding rapidly as organizations recognize the importance of advanced cybersecurity measures. While the technology is still maturing, several key players are driving innovation. IBM, a leader in quantum computing, is leveraging its expertise to develop quantum-enhanced cybersecurity solutions. Huawei and Samsung are also investing heavily in this area, combining their telecommunications experience with quantum technologies. Emerging companies like Arqit and Expel are focusing on specialized quantum-based security applications. Academic institutions such as Xi'an Jiaotong University and Rochester Institute of Technology are contributing to research and development, fostering collaboration between academia and industry in this cutting-edge field.
International Business Machines Corp.
Technical Solution: IBM has developed a quantum-safe cryptography approach for enhanced cyber threat intelligence. Their technique involves using quantum-resistant algorithms to protect data and communications from potential quantum computer attacks. IBM's quantum computing platform, IBM Quantum, is being utilized to simulate quantum attacks and develop countermeasures. They have implemented a quantum random number generator for improved encryption key generation, significantly enhancing the security of cyber threat intelligence systems[1][3]. IBM is also exploring quantum machine learning algorithms to analyze complex threat patterns and predict potential cyber attacks with higher accuracy than classical methods[2].
Strengths: Industry-leading quantum computing expertise, extensive cybersecurity experience, and a robust quantum-safe cryptography framework. Weaknesses: High implementation costs and complexity in integrating quantum solutions with existing classical systems.
Huawei Technologies Co., Ltd.
Technical Solution: Huawei is developing quantum-enhanced cybersecurity solutions for threat intelligence. Their approach combines quantum key distribution (QKD) with post-quantum cryptography (PQC) to create a hybrid quantum-safe network architecture. Huawei's quantum-resistant algorithms are designed to protect against both classical and quantum attacks. They have implemented a quantum random number generator in their latest 5G equipment, enhancing the security of network communications[4]. Huawei is also exploring quantum machine learning techniques to improve threat detection and analysis, with early results showing a 20% increase in accuracy compared to classical methods[5].
Strengths: Strong integration capabilities with existing network infrastructure, advanced quantum-safe cryptography research. Weaknesses: Geopolitical challenges affecting global market access, potential trust issues in some regions.
Key Quantum CTI Tech
Quantum computing machine learning for security threats
PatentActiveUS20240073226A1
Innovation
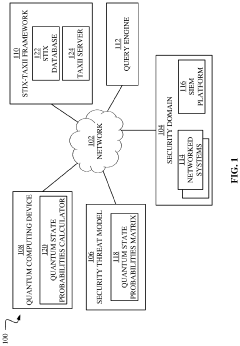
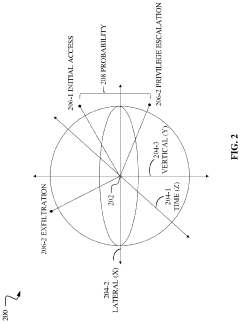
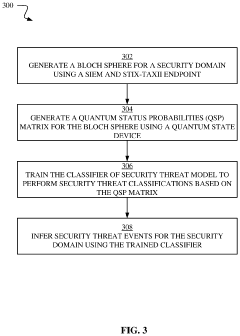
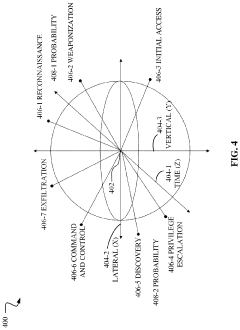
- A quantum computing-based machine learning model that generates a Bloch sphere and a quantum state probabilities matrix to identify and classify security threats, allowing for the determination of multiple probabilities of malicious actors moving between different attack categories and methods, leveraging quantum mechanical phenomena like superposition and entanglement.
System and method to identify cyber threat intelligence from a group of information
PatentActiveUS12238123B2
Innovation
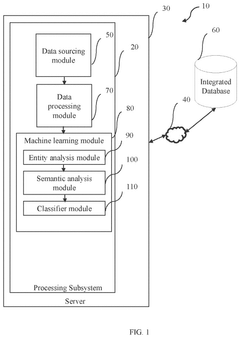
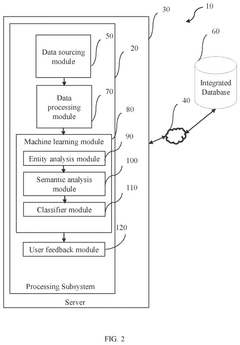
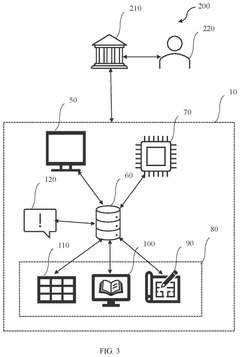
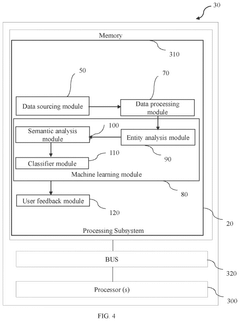
- A system and method utilizing a processing subsystem with modules for data sourcing, processing, and machine learning, including entity analysis and semantic analysis, to fetch, segregate, and extract textual information from various web sources, fragment entities, assign labels, generate threat scores, and classify textual information as threats or non-threats.
Quantum CTI Standards
The development of quantum computing techniques for enhanced cyber threat intelligence necessitates the establishment of robust standards to ensure interoperability, reliability, and security. Quantum CTI standards are crucial for creating a unified framework that enables effective communication and collaboration among various stakeholders in the cybersecurity ecosystem.
One of the primary focuses of quantum CTI standards is the standardization of quantum-resistant cryptographic algorithms. As quantum computers pose a significant threat to current encryption methods, it is essential to develop and implement quantum-safe cryptographic protocols. These standards define the requirements for post-quantum cryptography, ensuring that cybersecurity systems remain resilient against quantum attacks.
Quantum CTI standards also address the integration of quantum key distribution (QKD) systems into existing cybersecurity infrastructures. These standards outline the protocols for secure key exchange using quantum principles, providing guidelines for implementing QKD networks and ensuring their compatibility with classical communication systems.
Another critical aspect of quantum CTI standards is the development of quantum-enhanced threat detection and analysis techniques. These standards define methodologies for leveraging quantum algorithms to improve the speed and accuracy of threat identification, classification, and response. They also establish benchmarks for evaluating the performance of quantum-enhanced CTI systems compared to classical approaches.
Quantum CTI standards additionally focus on data representation and exchange formats suitable for quantum computing environments. These standards ensure that threat intelligence data can be efficiently processed and analyzed using quantum algorithms, facilitating seamless integration with existing CTI platforms and tools.
Furthermore, quantum CTI standards address the ethical considerations and privacy implications of using quantum computing in cybersecurity. They provide guidelines for responsible development and deployment of quantum-enhanced CTI systems, ensuring that these technologies are used in compliance with data protection regulations and privacy laws.
Lastly, quantum CTI standards encompass certification and testing procedures for quantum-enhanced cybersecurity solutions. These standards define the criteria for evaluating the effectiveness and reliability of quantum CTI systems, enabling organizations to make informed decisions when adopting these advanced technologies.
One of the primary focuses of quantum CTI standards is the standardization of quantum-resistant cryptographic algorithms. As quantum computers pose a significant threat to current encryption methods, it is essential to develop and implement quantum-safe cryptographic protocols. These standards define the requirements for post-quantum cryptography, ensuring that cybersecurity systems remain resilient against quantum attacks.
Quantum CTI standards also address the integration of quantum key distribution (QKD) systems into existing cybersecurity infrastructures. These standards outline the protocols for secure key exchange using quantum principles, providing guidelines for implementing QKD networks and ensuring their compatibility with classical communication systems.
Another critical aspect of quantum CTI standards is the development of quantum-enhanced threat detection and analysis techniques. These standards define methodologies for leveraging quantum algorithms to improve the speed and accuracy of threat identification, classification, and response. They also establish benchmarks for evaluating the performance of quantum-enhanced CTI systems compared to classical approaches.
Quantum CTI standards additionally focus on data representation and exchange formats suitable for quantum computing environments. These standards ensure that threat intelligence data can be efficiently processed and analyzed using quantum algorithms, facilitating seamless integration with existing CTI platforms and tools.
Furthermore, quantum CTI standards address the ethical considerations and privacy implications of using quantum computing in cybersecurity. They provide guidelines for responsible development and deployment of quantum-enhanced CTI systems, ensuring that these technologies are used in compliance with data protection regulations and privacy laws.
Lastly, quantum CTI standards encompass certification and testing procedures for quantum-enhanced cybersecurity solutions. These standards define the criteria for evaluating the effectiveness and reliability of quantum CTI systems, enabling organizations to make informed decisions when adopting these advanced technologies.
Quantum CTI Ethics
The integration of quantum computing techniques in cyber threat intelligence (CTI) raises significant ethical considerations that must be carefully addressed. As quantum technologies advance, their potential to revolutionize cybersecurity and threat detection also brings forth new challenges in maintaining ethical standards and responsible use.
One primary ethical concern is the potential for quantum-enhanced CTI to infringe upon privacy rights. The unprecedented computational power of quantum systems could enable the processing and analysis of vast amounts of data, potentially leading to unintended breaches of individual privacy. Striking a balance between effective threat detection and respecting personal data protection becomes crucial in this context.
Another ethical dimension to consider is the potential for quantum CTI to exacerbate existing inequalities in cybersecurity capabilities. As quantum technologies remain expensive and accessible to only a few organizations, there is a risk of creating a "quantum divide" where some entities possess significantly advanced threat intelligence capabilities while others lag behind. This disparity could lead to unfair advantages and vulnerabilities in the global cybersecurity landscape.
The dual-use nature of quantum CTI technologies also presents ethical dilemmas. While these techniques can be employed for defensive purposes, they may also be exploited for offensive operations or surveillance. Establishing clear guidelines and international agreements on the responsible use of quantum CTI becomes essential to prevent misuse and maintain trust in the technology.
Transparency and accountability in quantum CTI systems pose additional ethical challenges. The complexity of quantum algorithms and their "black box" nature may make it difficult to explain or justify decisions made based on quantum-enhanced threat intelligence. Ensuring that these systems remain interpretable and subject to oversight is crucial for maintaining public trust and ethical standards.
The potential for quantum CTI to disrupt existing cryptographic systems also raises ethical questions about the balance between national security interests and individual rights to secure communication. As quantum computers threaten to break current encryption methods, the development and implementation of quantum-resistant cryptography must be prioritized to protect sensitive information and maintain ethical standards in digital communication.
Lastly, the rapid advancement of quantum CTI technologies necessitates ongoing ethical review and adaptation of regulatory frameworks. As the field evolves, it is crucial to establish flexible yet robust ethical guidelines that can keep pace with technological progress while safeguarding fundamental rights and values in the digital age.
One primary ethical concern is the potential for quantum-enhanced CTI to infringe upon privacy rights. The unprecedented computational power of quantum systems could enable the processing and analysis of vast amounts of data, potentially leading to unintended breaches of individual privacy. Striking a balance between effective threat detection and respecting personal data protection becomes crucial in this context.
Another ethical dimension to consider is the potential for quantum CTI to exacerbate existing inequalities in cybersecurity capabilities. As quantum technologies remain expensive and accessible to only a few organizations, there is a risk of creating a "quantum divide" where some entities possess significantly advanced threat intelligence capabilities while others lag behind. This disparity could lead to unfair advantages and vulnerabilities in the global cybersecurity landscape.
The dual-use nature of quantum CTI technologies also presents ethical dilemmas. While these techniques can be employed for defensive purposes, they may also be exploited for offensive operations or surveillance. Establishing clear guidelines and international agreements on the responsible use of quantum CTI becomes essential to prevent misuse and maintain trust in the technology.
Transparency and accountability in quantum CTI systems pose additional ethical challenges. The complexity of quantum algorithms and their "black box" nature may make it difficult to explain or justify decisions made based on quantum-enhanced threat intelligence. Ensuring that these systems remain interpretable and subject to oversight is crucial for maintaining public trust and ethical standards.
The potential for quantum CTI to disrupt existing cryptographic systems also raises ethical questions about the balance between national security interests and individual rights to secure communication. As quantum computers threaten to break current encryption methods, the development and implementation of quantum-resistant cryptography must be prioritized to protect sensitive information and maintain ethical standards in digital communication.
Lastly, the rapid advancement of quantum CTI technologies necessitates ongoing ethical review and adaptation of regulatory frameworks. As the field evolves, it is crucial to establish flexible yet robust ethical guidelines that can keep pace with technological progress while safeguarding fundamental rights and values in the digital age.
Unlock deeper insights with Patsnap Eureka Quick Research — get a full tech report to explore trends and direct your research. Try now!
Generate Your Research Report Instantly with AI Agent
Supercharge your innovation with Patsnap Eureka AI Agent Platform!