Quantum Computing and Cryptographic Hashing: Bridging Gaps
JUL 17, 20259 MIN READ
Generate Your Research Report Instantly with AI Agent
Patsnap Eureka helps you evaluate technical feasibility & market potential.
Quantum Computing and Cryptographic Hashing Overview
Quantum computing and cryptographic hashing represent two pivotal areas in modern computer science and information security. Quantum computing harnesses the principles of quantum mechanics to perform complex calculations at unprecedented speeds, potentially revolutionizing fields such as cryptography, drug discovery, and financial modeling. On the other hand, cryptographic hashing is a cornerstone of digital security, providing data integrity and authentication in various applications.
The intersection of these two domains presents both challenges and opportunities. As quantum computers advance, they pose a significant threat to many current cryptographic systems, including those based on hashing algorithms. This potential vulnerability has spurred research into quantum-resistant cryptography and post-quantum hashing methods.
Quantum computing operates on qubits, which can exist in multiple states simultaneously due to superposition. This property, along with entanglement, allows quantum computers to perform certain calculations exponentially faster than classical computers. However, building and maintaining stable quantum systems remains a significant challenge, requiring extreme environmental conditions and sophisticated error correction techniques.
Cryptographic hashing, in contrast, relies on mathematical algorithms to transform input data into fixed-size output strings, called hashes. These functions are designed to be one-way and collision-resistant, making them crucial for digital signatures, password storage, and blockchain technology. The security of many hashing algorithms depends on the computational difficulty of reversing the hash or finding collisions.
The advent of quantum computing threatens to undermine the security assumptions of many classical cryptographic systems. Shor's algorithm, for instance, could potentially break widely-used public-key cryptosystems, while Grover's algorithm could significantly weaken the security of symmetric-key algorithms and hash functions.
This looming threat has catalyzed research into quantum-resistant cryptography and hashing methods. Post-quantum cryptography aims to develop algorithms that remain secure even in the face of quantum attacks. Lattice-based cryptography, hash-based signatures, and multivariate polynomial cryptosystems are among the promising approaches being explored.
Bridging the gap between quantum computing and cryptographic hashing involves not only developing new algorithms but also understanding the fundamental limits of quantum systems and their impact on cryptographic security. This research area is crucial for ensuring the long-term security of digital communications and data storage in a world where quantum computers become increasingly powerful and accessible.
The intersection of these two domains presents both challenges and opportunities. As quantum computers advance, they pose a significant threat to many current cryptographic systems, including those based on hashing algorithms. This potential vulnerability has spurred research into quantum-resistant cryptography and post-quantum hashing methods.
Quantum computing operates on qubits, which can exist in multiple states simultaneously due to superposition. This property, along with entanglement, allows quantum computers to perform certain calculations exponentially faster than classical computers. However, building and maintaining stable quantum systems remains a significant challenge, requiring extreme environmental conditions and sophisticated error correction techniques.
Cryptographic hashing, in contrast, relies on mathematical algorithms to transform input data into fixed-size output strings, called hashes. These functions are designed to be one-way and collision-resistant, making them crucial for digital signatures, password storage, and blockchain technology. The security of many hashing algorithms depends on the computational difficulty of reversing the hash or finding collisions.
The advent of quantum computing threatens to undermine the security assumptions of many classical cryptographic systems. Shor's algorithm, for instance, could potentially break widely-used public-key cryptosystems, while Grover's algorithm could significantly weaken the security of symmetric-key algorithms and hash functions.
This looming threat has catalyzed research into quantum-resistant cryptography and hashing methods. Post-quantum cryptography aims to develop algorithms that remain secure even in the face of quantum attacks. Lattice-based cryptography, hash-based signatures, and multivariate polynomial cryptosystems are among the promising approaches being explored.
Bridging the gap between quantum computing and cryptographic hashing involves not only developing new algorithms but also understanding the fundamental limits of quantum systems and their impact on cryptographic security. This research area is crucial for ensuring the long-term security of digital communications and data storage in a world where quantum computers become increasingly powerful and accessible.
Market Demand for Post-Quantum Cryptography
The market demand for post-quantum cryptography has been steadily growing in recent years, driven by the looming threat of quantum computers potentially breaking current cryptographic systems. As quantum computing technology advances, organizations across various sectors are recognizing the need to prepare for a post-quantum era in cybersecurity.
Government agencies and defense departments worldwide are among the primary drivers of this demand. These entities handle highly sensitive information that must remain secure for decades, making them particularly vulnerable to the future threat of quantum attacks. As a result, they are investing heavily in research and development of quantum-resistant cryptographic solutions.
Financial institutions, including banks, insurance companies, and investment firms, are also significant contributors to the market demand. The long-term nature of financial transactions and the critical importance of data confidentiality in this sector necessitate early adoption of post-quantum cryptography to protect against future threats.
The healthcare industry, with its emphasis on patient data privacy and long-term record keeping, is another key market for post-quantum cryptography. As healthcare systems become increasingly digitized and interconnected, the need for robust, future-proof encryption methods becomes more pressing.
In the technology sector, major cloud service providers and software companies are actively exploring post-quantum cryptography solutions. These companies are not only potential customers but also developers of post-quantum cryptographic products, further driving market growth.
The automotive industry, particularly with the rise of connected and autonomous vehicles, is emerging as a new frontier for post-quantum cryptography. The long lifespan of vehicles and the critical nature of their security systems make quantum-resistant encryption essential for future-proofing these technologies.
Telecommunications companies and internet service providers are also showing increased interest in post-quantum cryptography. As the backbone of global communications, these entities are responsible for securing vast amounts of data transmission, making them prime candidates for early adoption of quantum-resistant protocols.
The market demand is further bolstered by regulatory pressures and industry standards. Government bodies and international organizations are beginning to mandate the transition to quantum-resistant cryptography, creating a compliance-driven demand across multiple sectors.
As awareness of the quantum threat grows, small and medium-sized enterprises are also starting to consider post-quantum cryptography solutions, expanding the market beyond large corporations and government entities. This broadening of the customer base is expected to significantly contribute to market growth in the coming years.
Government agencies and defense departments worldwide are among the primary drivers of this demand. These entities handle highly sensitive information that must remain secure for decades, making them particularly vulnerable to the future threat of quantum attacks. As a result, they are investing heavily in research and development of quantum-resistant cryptographic solutions.
Financial institutions, including banks, insurance companies, and investment firms, are also significant contributors to the market demand. The long-term nature of financial transactions and the critical importance of data confidentiality in this sector necessitate early adoption of post-quantum cryptography to protect against future threats.
The healthcare industry, with its emphasis on patient data privacy and long-term record keeping, is another key market for post-quantum cryptography. As healthcare systems become increasingly digitized and interconnected, the need for robust, future-proof encryption methods becomes more pressing.
In the technology sector, major cloud service providers and software companies are actively exploring post-quantum cryptography solutions. These companies are not only potential customers but also developers of post-quantum cryptographic products, further driving market growth.
The automotive industry, particularly with the rise of connected and autonomous vehicles, is emerging as a new frontier for post-quantum cryptography. The long lifespan of vehicles and the critical nature of their security systems make quantum-resistant encryption essential for future-proofing these technologies.
Telecommunications companies and internet service providers are also showing increased interest in post-quantum cryptography. As the backbone of global communications, these entities are responsible for securing vast amounts of data transmission, making them prime candidates for early adoption of quantum-resistant protocols.
The market demand is further bolstered by regulatory pressures and industry standards. Government bodies and international organizations are beginning to mandate the transition to quantum-resistant cryptography, creating a compliance-driven demand across multiple sectors.
As awareness of the quantum threat grows, small and medium-sized enterprises are also starting to consider post-quantum cryptography solutions, expanding the market beyond large corporations and government entities. This broadening of the customer base is expected to significantly contribute to market growth in the coming years.
Current Challenges in Quantum-Resistant Hashing
The field of quantum-resistant hashing faces several significant challenges as the development of quantum computing continues to advance. One of the primary concerns is the potential vulnerability of current cryptographic hash functions to quantum attacks, particularly those based on the Shor's and Grover's algorithms. These quantum algorithms could potentially break many of the widely used hash functions, compromising the security of digital signatures, message authentication codes, and other cryptographic protocols.
A major challenge lies in developing new hash functions that can withstand attacks from both classical and quantum computers. This requires a deep understanding of quantum computing principles and their potential impact on cryptographic systems. Researchers are exploring various approaches, including lattice-based, multivariate, and hash-based cryptography, to create quantum-resistant alternatives. However, each of these approaches comes with its own set of challenges in terms of efficiency, key size, and implementation complexity.
Another significant hurdle is the need for standardization and widespread adoption of quantum-resistant hash functions. The cryptographic community must reach a consensus on which algorithms are truly secure against quantum attacks and can be practically implemented across various systems and platforms. This process involves extensive testing, peer review, and validation, which can take years to complete.
Performance is another critical challenge in quantum-resistant hashing. Many post-quantum cryptographic algorithms require significantly more computational resources than their classical counterparts. This can lead to increased processing times and energy consumption, potentially limiting their applicability in resource-constrained environments such as IoT devices or mobile platforms.
The transition from current cryptographic systems to quantum-resistant ones presents a substantial challenge. Organizations and governments need to develop migration strategies that allow for the coexistence of classical and quantum-resistant algorithms during the transition period. This includes updating existing infrastructure, software, and protocols to support new hash functions without disrupting current operations.
Lastly, there is the challenge of future-proofing quantum-resistant hash functions. As quantum computing technology evolves, new attack vectors may emerge, requiring continuous research and development to stay ahead of potential threats. This necessitates a flexible approach to cryptographic design that can adapt to future advancements in both quantum and classical computing.
A major challenge lies in developing new hash functions that can withstand attacks from both classical and quantum computers. This requires a deep understanding of quantum computing principles and their potential impact on cryptographic systems. Researchers are exploring various approaches, including lattice-based, multivariate, and hash-based cryptography, to create quantum-resistant alternatives. However, each of these approaches comes with its own set of challenges in terms of efficiency, key size, and implementation complexity.
Another significant hurdle is the need for standardization and widespread adoption of quantum-resistant hash functions. The cryptographic community must reach a consensus on which algorithms are truly secure against quantum attacks and can be practically implemented across various systems and platforms. This process involves extensive testing, peer review, and validation, which can take years to complete.
Performance is another critical challenge in quantum-resistant hashing. Many post-quantum cryptographic algorithms require significantly more computational resources than their classical counterparts. This can lead to increased processing times and energy consumption, potentially limiting their applicability in resource-constrained environments such as IoT devices or mobile platforms.
The transition from current cryptographic systems to quantum-resistant ones presents a substantial challenge. Organizations and governments need to develop migration strategies that allow for the coexistence of classical and quantum-resistant algorithms during the transition period. This includes updating existing infrastructure, software, and protocols to support new hash functions without disrupting current operations.
Lastly, there is the challenge of future-proofing quantum-resistant hash functions. As quantum computing technology evolves, new attack vectors may emerge, requiring continuous research and development to stay ahead of potential threats. This necessitates a flexible approach to cryptographic design that can adapt to future advancements in both quantum and classical computing.
Existing Quantum-Resistant Hash Functions
01 Quantum-resistant cryptographic hashing algorithms
Development of cryptographic hashing algorithms that are resistant to attacks from quantum computers. These algorithms are designed to maintain security even in the presence of powerful quantum computing capabilities, ensuring long-term data protection and integrity in the post-quantum era.- Quantum-resistant cryptographic hashing algorithms: Development of cryptographic hashing algorithms that are resistant to attacks from quantum computers. These algorithms are designed to maintain security even in the presence of powerful quantum computing capabilities, ensuring long-term data protection and integrity in the post-quantum era.
- Quantum hashing for secure communication: Utilization of quantum properties to create secure hashing mechanisms for communication protocols. This approach leverages quantum phenomena such as superposition and entanglement to generate highly secure hash values that are theoretically impossible to reverse-engineer using classical computing methods.
- Hybrid classical-quantum hashing schemes: Development of hybrid hashing schemes that combine classical cryptographic techniques with quantum-inspired algorithms. These hybrid approaches aim to provide enhanced security by leveraging the strengths of both classical and quantum computing paradigms, offering a transitional solution as quantum technologies evolve.
- Quantum-safe blockchain and distributed ledger technologies: Integration of quantum-resistant hashing algorithms into blockchain and distributed ledger technologies. This ensures the long-term security and integrity of decentralized systems, protecting them against potential attacks from future quantum computers while maintaining the benefits of distributed consensus mechanisms.
- Post-quantum cryptographic standards and protocols: Development and standardization of post-quantum cryptographic protocols that incorporate quantum-resistant hashing algorithms. These efforts aim to establish new industry standards and best practices for implementing quantum-safe cryptographic systems across various applications and industries.
02 Quantum hashing for secure communication
Utilization of quantum properties to create secure hashing mechanisms for communication protocols. This approach leverages quantum phenomena such as superposition and entanglement to generate highly secure hash values that are theoretically impossible to reverse-engineer using classical computing methods.Expand Specific Solutions03 Hybrid classical-quantum hashing schemes
Development of hybrid hashing schemes that combine classical cryptographic techniques with quantum-inspired algorithms. These hybrid approaches aim to provide enhanced security by leveraging the strengths of both classical and quantum computing paradigms, offering a transitional solution as quantum technologies continue to evolve.Expand Specific Solutions04 Quantum-based random number generation for hashing
Integration of quantum random number generators (QRNG) into cryptographic hashing processes. QRNGs exploit quantum mechanical properties to produce truly random numbers, which can significantly enhance the unpredictability and security of hash functions used in various cryptographic applications.Expand Specific Solutions05 Post-quantum cryptographic protocols using advanced hashing
Design and implementation of post-quantum cryptographic protocols that incorporate advanced hashing techniques. These protocols aim to secure data and communications against potential threats from both classical and quantum adversaries, ensuring long-term security in various applications such as blockchain, digital signatures, and secure key exchange.Expand Specific Solutions
Key Players in Quantum Computing Research
The quantum computing and cryptographic hashing landscape is in a transitional phase, with significant market growth potential but varying levels of technological maturity. The market is characterized by a mix of established tech giants, specialized quantum computing firms, and academic institutions. Companies like IBM, Google, and D-Wave Systems are leading in quantum hardware development, while others like Terra Quantum AG and Zapata Computing focus on quantum software solutions. The field is seeing increased interest from financial institutions such as Wells Fargo and Capital One, indicating potential applications in secure financial transactions. Chinese companies like QuantumCTek and Shenzhou Quantum are making strides in quantum communication networks, reflecting the global nature of this technological race. The involvement of diverse players suggests a competitive and rapidly evolving ecosystem, with both hardware and software innovations driving progress in bridging quantum computing and cryptographic hashing.
Google LLC
Technical Solution: Google's approach to quantum computing and cryptographic hashing focuses on developing quantum-resistant cryptography and exploring quantum algorithms for cryptanalysis. They have introduced the OpenSSQ (Open-Source Secure Quantum) framework, which aims to create quantum-resistant cryptographic primitives[1]. Google's quantum computer, Sycamore, has demonstrated quantum supremacy by performing a specific computation in 200 seconds that would take a classical supercomputer 10,000 years[2]. In the realm of cryptographic hashing, Google is researching post-quantum cryptography to ensure data security in the face of quantum threats. They are actively participating in the NIST Post-Quantum Cryptography standardization process, contributing to the development of quantum-resistant algorithms[3].
Strengths: Advanced quantum hardware, strong research team, and significant resources for R&D. Weaknesses: Quantum computers still face scalability and error correction challenges, limiting practical applications in cryptography.
D-Wave Systems, Inc.
Technical Solution: D-Wave focuses on quantum annealing, a specialized form of quantum computing. While not directly applicable to traditional cryptographic hashing, their approach offers potential in optimization problems related to cryptography. D-Wave's latest quantum annealer, Advantage, features over 5000 qubits and 15-way qubit connectivity[7]. In the context of cryptographic hashing, D-Wave's systems could potentially be used for certain aspects of cryptanalysis, such as finding collisions in hash functions. They are exploring applications in quantum-assisted machine learning, which could have implications for analyzing cryptographic systems[8]. D-Wave has also been investigating hybrid quantum-classical algorithms that could be relevant to post-quantum cryptography.
Strengths: Leader in quantum annealing technology, with the highest number of qubits in a commercial system. Weaknesses: Limited to specific types of optimization problems, not directly applicable to general-purpose quantum computing tasks.
Innovations in Post-Quantum Cryptographic Hashing
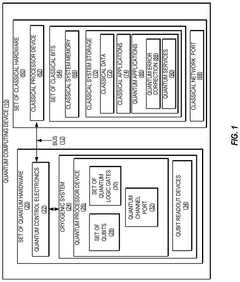
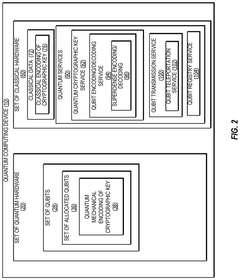
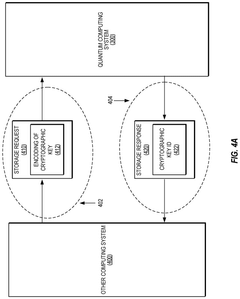
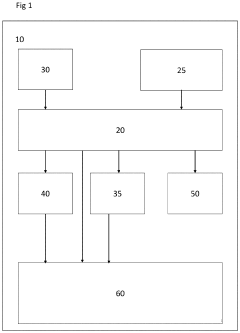
Cryptographic key management for distributed quantum computing systems
PatentActiveUS20240333482A1
Innovation
- The implementation of superdense coding using quantum mechanical encoding protocols that distribute cryptographic keys across multiple qubits, allowing for efficient storage, management, and retrieval of keys by encoding them in fewer qubits than classical bits, ensuring data integrity through spatial distribution and qubit teleportation or swap operations.
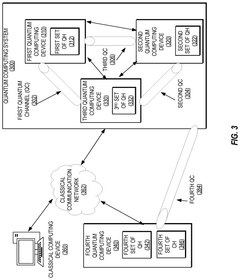
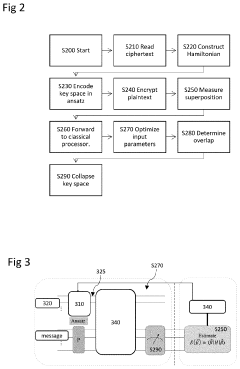
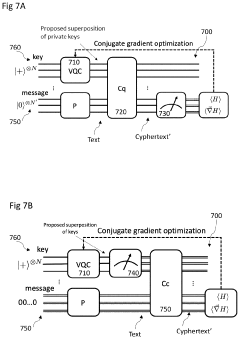
Variational Quantum Attack for Cryptographic Protocols
PatentPendingUS20240163073A1
Innovation
- A method that reduces the number of qubits required for attacking cryptographic protocols by fragmenting Bloch spheres and using quantum annealing or tensor networks, applicable to both symmetric and non-symmetric protocols, to determine encryption keys by constructing a Hamiltonian based on ciphertext and adjusting quantum circuit parameters for optimal overlap.
Quantum Computing Impact on Cybersecurity
The advent of quantum computing poses significant challenges to the field of cybersecurity, particularly in the realm of cryptographic systems. As quantum computers become more powerful and sophisticated, they have the potential to break many of the encryption methods currently used to protect sensitive data and communications.
One of the most immediate concerns is the vulnerability of widely-used public-key cryptography algorithms, such as RSA and elliptic curve cryptography, to quantum attacks. These algorithms rely on the difficulty of factoring large numbers or solving discrete logarithm problems, which quantum computers could potentially solve much faster than classical computers using Shor's algorithm.
This threat has led to increased research and development in the field of post-quantum cryptography, which aims to create encryption methods that are resistant to both classical and quantum attacks. Various approaches are being explored, including lattice-based cryptography, hash-based signatures, and code-based cryptography.
However, the impact of quantum computing on cybersecurity extends beyond encryption. Quantum key distribution (QKD) offers the potential for unconditionally secure communication by leveraging the principles of quantum mechanics. While QKD systems are already in use, their widespread adoption faces challenges related to infrastructure requirements and practical implementation.
Quantum computing also presents opportunities for enhancing cybersecurity. Quantum random number generators can produce truly random numbers, which are crucial for creating strong encryption keys. Additionally, quantum sensing technologies may improve the detection of intrusions and unauthorized access attempts in secure systems.
The cybersecurity industry must adapt to these changes by developing quantum-resistant algorithms and protocols. This transition will require significant updates to existing infrastructure and systems, posing logistical and financial challenges for organizations across various sectors.
As quantum computing continues to advance, it is crucial for cybersecurity professionals to stay informed about the latest developments and potential vulnerabilities. Collaboration between quantum physicists, cryptographers, and security experts will be essential in addressing the complex challenges posed by this emerging technology.
One of the most immediate concerns is the vulnerability of widely-used public-key cryptography algorithms, such as RSA and elliptic curve cryptography, to quantum attacks. These algorithms rely on the difficulty of factoring large numbers or solving discrete logarithm problems, which quantum computers could potentially solve much faster than classical computers using Shor's algorithm.
This threat has led to increased research and development in the field of post-quantum cryptography, which aims to create encryption methods that are resistant to both classical and quantum attacks. Various approaches are being explored, including lattice-based cryptography, hash-based signatures, and code-based cryptography.
However, the impact of quantum computing on cybersecurity extends beyond encryption. Quantum key distribution (QKD) offers the potential for unconditionally secure communication by leveraging the principles of quantum mechanics. While QKD systems are already in use, their widespread adoption faces challenges related to infrastructure requirements and practical implementation.
Quantum computing also presents opportunities for enhancing cybersecurity. Quantum random number generators can produce truly random numbers, which are crucial for creating strong encryption keys. Additionally, quantum sensing technologies may improve the detection of intrusions and unauthorized access attempts in secure systems.
The cybersecurity industry must adapt to these changes by developing quantum-resistant algorithms and protocols. This transition will require significant updates to existing infrastructure and systems, posing logistical and financial challenges for organizations across various sectors.
As quantum computing continues to advance, it is crucial for cybersecurity professionals to stay informed about the latest developments and potential vulnerabilities. Collaboration between quantum physicists, cryptographers, and security experts will be essential in addressing the complex challenges posed by this emerging technology.
Standardization Efforts for Post-Quantum Cryptography
The standardization efforts for post-quantum cryptography have gained significant momentum in recent years, driven by the looming threat of quantum computers to current cryptographic systems. The National Institute of Standards and Technology (NIST) has been at the forefront of these efforts, initiating a process to develop, evaluate, and standardize quantum-resistant public-key cryptographic algorithms.
NIST's Post-Quantum Cryptography Standardization Process, launched in 2016, has progressed through multiple rounds of evaluation. The process has focused on selecting algorithms for public-key encryption, key-establishment, and digital signatures that can withstand attacks from both classical and quantum computers. After rigorous analysis and public scrutiny, NIST announced the first group of selected algorithms in July 2022.
The selected algorithms include CRYSTALS-Kyber for general encryption, and CRYSTALS-Dilithium, FALCON, and SPHINCS+ for digital signatures. These algorithms are based on various mathematical problems, such as lattices and hash functions, which are believed to be resistant to quantum attacks. NIST continues to evaluate additional candidates for potential standardization in future rounds.
Parallel to NIST's efforts, other international bodies are also contributing to post-quantum cryptography standardization. The European Telecommunications Standards Institute (ETSI) has established a Quantum-Safe Cryptography working group, which is developing standards and guidelines for the transition to quantum-safe cryptography. Similarly, the Internet Engineering Task Force (IETF) is working on integrating post-quantum algorithms into existing internet protocols.
The standardization process has also spurred collaboration between academia, industry, and government agencies. Many tech giants, including Google, Microsoft, and IBM, are actively participating in the development and testing of post-quantum algorithms. This collaborative approach ensures that the standardized algorithms are not only theoretically secure but also practical for real-world implementation across various platforms and use cases.
As the standardization efforts progress, there is an increasing focus on the challenges of transitioning existing systems to post-quantum cryptography. This includes developing migration strategies, ensuring backward compatibility, and addressing the increased key sizes and computational requirements of many post-quantum algorithms. Standardization bodies are also considering the need for crypto-agility, allowing systems to easily switch between different cryptographic algorithms as the threat landscape evolves.
The ongoing standardization efforts are crucial for ensuring global cybersecurity in the quantum era. They provide a framework for the development of quantum-resistant cryptographic solutions and guide organizations in preparing for the transition. As these standards continue to evolve, they will play a pivotal role in shaping the future of secure communication and data protection in a world where quantum computers are a reality.
NIST's Post-Quantum Cryptography Standardization Process, launched in 2016, has progressed through multiple rounds of evaluation. The process has focused on selecting algorithms for public-key encryption, key-establishment, and digital signatures that can withstand attacks from both classical and quantum computers. After rigorous analysis and public scrutiny, NIST announced the first group of selected algorithms in July 2022.
The selected algorithms include CRYSTALS-Kyber for general encryption, and CRYSTALS-Dilithium, FALCON, and SPHINCS+ for digital signatures. These algorithms are based on various mathematical problems, such as lattices and hash functions, which are believed to be resistant to quantum attacks. NIST continues to evaluate additional candidates for potential standardization in future rounds.
Parallel to NIST's efforts, other international bodies are also contributing to post-quantum cryptography standardization. The European Telecommunications Standards Institute (ETSI) has established a Quantum-Safe Cryptography working group, which is developing standards and guidelines for the transition to quantum-safe cryptography. Similarly, the Internet Engineering Task Force (IETF) is working on integrating post-quantum algorithms into existing internet protocols.
The standardization process has also spurred collaboration between academia, industry, and government agencies. Many tech giants, including Google, Microsoft, and IBM, are actively participating in the development and testing of post-quantum algorithms. This collaborative approach ensures that the standardized algorithms are not only theoretically secure but also practical for real-world implementation across various platforms and use cases.
As the standardization efforts progress, there is an increasing focus on the challenges of transitioning existing systems to post-quantum cryptography. This includes developing migration strategies, ensuring backward compatibility, and addressing the increased key sizes and computational requirements of many post-quantum algorithms. Standardization bodies are also considering the need for crypto-agility, allowing systems to easily switch between different cryptographic algorithms as the threat landscape evolves.
The ongoing standardization efforts are crucial for ensuring global cybersecurity in the quantum era. They provide a framework for the development of quantum-resistant cryptographic solutions and guide organizations in preparing for the transition. As these standards continue to evolve, they will play a pivotal role in shaping the future of secure communication and data protection in a world where quantum computers are a reality.
Unlock deeper insights with Patsnap Eureka Quick Research — get a full tech report to explore trends and direct your research. Try now!
Generate Your Research Report Instantly with AI Agent
Supercharge your innovation with Patsnap Eureka AI Agent Platform!