Longitudinal wave implications in cybersecurity frameworks
AUG 13, 20259 MIN READ
Generate Your Research Report Instantly with AI Agent
Patsnap Eureka helps you evaluate technical feasibility & market potential.
Cybersecurity Wave Evolution
The evolution of cybersecurity frameworks has been closely intertwined with the concept of longitudinal waves, reflecting the dynamic and cyclical nature of cyber threats and defensive strategies. This evolution can be traced through several distinct phases, each characterized by specific technological advancements and security paradigms.
In the early stages of cybersecurity, the focus was primarily on perimeter defense, akin to the initial crest of a longitudinal wave. This phase saw the widespread adoption of firewalls and antivirus software as the primary means of protection. As cyber threats became more sophisticated, the industry witnessed the trough of this wave, realizing the inadequacy of perimeter-based security alone.
The next wave brought about the concept of defense-in-depth, introducing multiple layers of security controls. This phase coincided with the rise of intrusion detection and prevention systems, as well as the implementation of more robust access control mechanisms. The crest of this wave was marked by a more holistic approach to cybersecurity, encompassing both technological and human factors.
As the digital landscape expanded with the proliferation of mobile devices and cloud computing, a new trough emerged. Traditional security models struggled to cope with the increased attack surface and the dissolution of clear network boundaries. This challenge gave rise to the next wave: the zero trust security model.
The zero trust paradigm represents a significant shift in cybersecurity frameworks, aligning with the principles of longitudinal waves by emphasizing continuous verification and adaptive security measures. This approach assumes no implicit trust, regardless of whether the network connection is internal or external, thus creating a more resilient security posture.
Most recently, the cybersecurity landscape has been riding the wave of artificial intelligence and machine learning integration. These technologies have enabled more proactive and predictive security measures, capable of detecting and responding to threats in real-time. This wave is characterized by the use of behavioral analytics, automated threat intelligence, and self-healing networks.
Looking ahead, the next crest in the cybersecurity wave evolution is likely to be shaped by quantum computing and post-quantum cryptography. As quantum computers threaten to break current encryption standards, the cybersecurity community is already preparing for this paradigm shift, developing new cryptographic algorithms resistant to quantum attacks.
Throughout this evolution, each wave has built upon the lessons learned from previous cycles, demonstrating the longitudinal nature of cybersecurity advancements. The continuous oscillation between new threats and defensive innovations underscores the importance of adaptable and forward-thinking cybersecurity frameworks.
In the early stages of cybersecurity, the focus was primarily on perimeter defense, akin to the initial crest of a longitudinal wave. This phase saw the widespread adoption of firewalls and antivirus software as the primary means of protection. As cyber threats became more sophisticated, the industry witnessed the trough of this wave, realizing the inadequacy of perimeter-based security alone.
The next wave brought about the concept of defense-in-depth, introducing multiple layers of security controls. This phase coincided with the rise of intrusion detection and prevention systems, as well as the implementation of more robust access control mechanisms. The crest of this wave was marked by a more holistic approach to cybersecurity, encompassing both technological and human factors.
As the digital landscape expanded with the proliferation of mobile devices and cloud computing, a new trough emerged. Traditional security models struggled to cope with the increased attack surface and the dissolution of clear network boundaries. This challenge gave rise to the next wave: the zero trust security model.
The zero trust paradigm represents a significant shift in cybersecurity frameworks, aligning with the principles of longitudinal waves by emphasizing continuous verification and adaptive security measures. This approach assumes no implicit trust, regardless of whether the network connection is internal or external, thus creating a more resilient security posture.
Most recently, the cybersecurity landscape has been riding the wave of artificial intelligence and machine learning integration. These technologies have enabled more proactive and predictive security measures, capable of detecting and responding to threats in real-time. This wave is characterized by the use of behavioral analytics, automated threat intelligence, and self-healing networks.
Looking ahead, the next crest in the cybersecurity wave evolution is likely to be shaped by quantum computing and post-quantum cryptography. As quantum computers threaten to break current encryption standards, the cybersecurity community is already preparing for this paradigm shift, developing new cryptographic algorithms resistant to quantum attacks.
Throughout this evolution, each wave has built upon the lessons learned from previous cycles, demonstrating the longitudinal nature of cybersecurity advancements. The continuous oscillation between new threats and defensive innovations underscores the importance of adaptable and forward-thinking cybersecurity frameworks.
Market Demand Analysis
The market demand for cybersecurity solutions incorporating longitudinal wave implications has been steadily increasing in recent years. This growth is primarily driven by the escalating sophistication of cyber threats and the need for more robust, dynamic security frameworks. Organizations across various sectors are recognizing the potential of longitudinal wave analysis to enhance their cybersecurity posture, leading to a surge in demand for related products and services.
The financial sector, in particular, has shown significant interest in longitudinal wave-based cybersecurity frameworks. Banks, insurance companies, and fintech firms are seeking advanced solutions to protect their sensitive data and financial transactions from evolving cyber threats. The healthcare industry is another key market, with hospitals and medical research institutions looking to safeguard patient information and critical research data against increasingly complex cyberattacks.
Government agencies and defense organizations are also major contributors to the market demand. These entities require cutting-edge cybersecurity solutions to protect national security interests and classified information. The adoption of longitudinal wave implications in their security frameworks is seen as a strategic move to stay ahead of state-sponsored cyber threats and sophisticated hacking groups.
The telecommunications industry is emerging as a rapidly growing market for longitudinal wave-based cybersecurity solutions. As 5G networks continue to expand, telecom companies are investing heavily in advanced security measures to protect their infrastructure and customer data. The integration of longitudinal wave analysis into their existing security frameworks is viewed as a crucial step in fortifying their defenses against potential vulnerabilities in next-generation networks.
Small and medium-sized enterprises (SMEs) are increasingly recognizing the importance of robust cybersecurity measures, contributing to the overall market growth. As cyber threats become more democratized, affecting businesses of all sizes, SMEs are seeking cost-effective solutions that incorporate longitudinal wave analysis to enhance their security posture.
The market for cybersecurity solutions with longitudinal wave implications is expected to experience substantial growth in the coming years. This growth is fueled by the increasing frequency and complexity of cyberattacks, stricter data protection regulations, and the growing awareness of cybersecurity risks among organizations. As more businesses undergo digital transformation and adopt cloud-based services, the demand for advanced security frameworks is likely to intensify further.
The financial sector, in particular, has shown significant interest in longitudinal wave-based cybersecurity frameworks. Banks, insurance companies, and fintech firms are seeking advanced solutions to protect their sensitive data and financial transactions from evolving cyber threats. The healthcare industry is another key market, with hospitals and medical research institutions looking to safeguard patient information and critical research data against increasingly complex cyberattacks.
Government agencies and defense organizations are also major contributors to the market demand. These entities require cutting-edge cybersecurity solutions to protect national security interests and classified information. The adoption of longitudinal wave implications in their security frameworks is seen as a strategic move to stay ahead of state-sponsored cyber threats and sophisticated hacking groups.
The telecommunications industry is emerging as a rapidly growing market for longitudinal wave-based cybersecurity solutions. As 5G networks continue to expand, telecom companies are investing heavily in advanced security measures to protect their infrastructure and customer data. The integration of longitudinal wave analysis into their existing security frameworks is viewed as a crucial step in fortifying their defenses against potential vulnerabilities in next-generation networks.
Small and medium-sized enterprises (SMEs) are increasingly recognizing the importance of robust cybersecurity measures, contributing to the overall market growth. As cyber threats become more democratized, affecting businesses of all sizes, SMEs are seeking cost-effective solutions that incorporate longitudinal wave analysis to enhance their security posture.
The market for cybersecurity solutions with longitudinal wave implications is expected to experience substantial growth in the coming years. This growth is fueled by the increasing frequency and complexity of cyberattacks, stricter data protection regulations, and the growing awareness of cybersecurity risks among organizations. As more businesses undergo digital transformation and adopt cloud-based services, the demand for advanced security frameworks is likely to intensify further.
Current Challenges
The cybersecurity landscape is constantly evolving, and the integration of longitudinal wave implications into cybersecurity frameworks presents several significant challenges. One of the primary obstacles is the complexity of implementing longitudinal wave analysis in real-time security systems. Traditional security measures often rely on static or point-in-time assessments, whereas longitudinal waves require continuous monitoring and analysis over extended periods.
Another challenge lies in the vast amount of data that needs to be processed and interpreted when considering longitudinal wave patterns. Cybersecurity teams must develop sophisticated algorithms and machine learning models capable of identifying subtle trends and anomalies over time, which demands substantial computational resources and expertise.
The dynamic nature of cyber threats poses a significant hurdle in effectively leveraging longitudinal wave implications. Attackers continuously adapt their techniques, making it difficult to establish stable baselines for longitudinal analysis. This necessitates frequent updates to the underlying models and frameworks, creating a constant race between defenders and malicious actors.
Interoperability between different security systems and data sources is another critical challenge. To fully harness the power of longitudinal wave analysis, organizations need to integrate data from various security tools, network devices, and external threat intelligence feeds. However, the lack of standardized data formats and APIs can hinder seamless integration and data sharing.
Privacy and compliance concerns also present obstacles in implementing longitudinal wave analysis in cybersecurity frameworks. The need for long-term data retention and analysis may conflict with data protection regulations, requiring organizations to strike a delicate balance between security effectiveness and regulatory compliance.
The shortage of skilled professionals who understand both cybersecurity principles and longitudinal wave analysis techniques is a significant bottleneck. This skills gap makes it challenging for organizations to develop, implement, and maintain advanced security frameworks that incorporate longitudinal wave implications.
Lastly, the cost and resource requirements associated with implementing and maintaining such sophisticated security frameworks can be prohibitive for many organizations, especially small and medium-sized enterprises. The need for advanced hardware, software, and ongoing expertise can strain budgets and limit widespread adoption of these cutting-edge approaches to cybersecurity.
Another challenge lies in the vast amount of data that needs to be processed and interpreted when considering longitudinal wave patterns. Cybersecurity teams must develop sophisticated algorithms and machine learning models capable of identifying subtle trends and anomalies over time, which demands substantial computational resources and expertise.
The dynamic nature of cyber threats poses a significant hurdle in effectively leveraging longitudinal wave implications. Attackers continuously adapt their techniques, making it difficult to establish stable baselines for longitudinal analysis. This necessitates frequent updates to the underlying models and frameworks, creating a constant race between defenders and malicious actors.
Interoperability between different security systems and data sources is another critical challenge. To fully harness the power of longitudinal wave analysis, organizations need to integrate data from various security tools, network devices, and external threat intelligence feeds. However, the lack of standardized data formats and APIs can hinder seamless integration and data sharing.
Privacy and compliance concerns also present obstacles in implementing longitudinal wave analysis in cybersecurity frameworks. The need for long-term data retention and analysis may conflict with data protection regulations, requiring organizations to strike a delicate balance between security effectiveness and regulatory compliance.
The shortage of skilled professionals who understand both cybersecurity principles and longitudinal wave analysis techniques is a significant bottleneck. This skills gap makes it challenging for organizations to develop, implement, and maintain advanced security frameworks that incorporate longitudinal wave implications.
Lastly, the cost and resource requirements associated with implementing and maintaining such sophisticated security frameworks can be prohibitive for many organizations, especially small and medium-sized enterprises. The need for advanced hardware, software, and ongoing expertise can strain budgets and limit widespread adoption of these cutting-edge approaches to cybersecurity.
Existing Security Solutions
01 Generation and propagation of longitudinal waves
Longitudinal waves are characterized by particle motion parallel to the direction of wave propagation. Various devices and methods are used to generate and propagate these waves in different mediums, including solids, liquids, and gases. Applications range from acoustic systems to seismic exploration.- Generation and propagation of longitudinal waves: Longitudinal waves are characterized by oscillations parallel to the direction of wave propagation. Various devices and methods are used to generate and propagate these waves in different mediums, including solids, liquids, and gases. Applications range from acoustic systems to seismic exploration.
- Ultrasonic longitudinal wave applications: Ultrasonic longitudinal waves are utilized in numerous fields, including medical imaging, non-destructive testing, and industrial processes. These high-frequency waves can penetrate materials, allowing for detailed analysis and manipulation of internal structures without causing damage.
- Longitudinal wave sensors and detectors: Sensors and detectors designed specifically for longitudinal waves are crucial in various applications. These devices can measure properties such as wave amplitude, frequency, and propagation speed, enabling accurate data collection for research, quality control, and monitoring purposes.
- Longitudinal wave energy harvesting: Innovative technologies are being developed to harness energy from longitudinal waves, particularly in environments with abundant wave activity. These systems convert wave motion into usable electrical energy, offering potential applications in renewable energy and remote power generation.
- Longitudinal wave manipulation and control: Advanced techniques for manipulating and controlling longitudinal waves are emerging, allowing for precise shaping, focusing, and steering of wave fronts. These methods enhance the effectiveness of wave-based technologies in fields such as communications, material processing, and medical treatments.
02 Ultrasonic longitudinal wave applications
Ultrasonic longitudinal waves are utilized in numerous fields, including medical imaging, non-destructive testing, and industrial processes. These high-frequency waves can penetrate materials, allowing for internal inspection and precise measurements without causing damage.Expand Specific Solutions03 Longitudinal wave sensors and detection systems
Sensors and detection systems designed to measure and analyze longitudinal waves are crucial in various applications. These systems can detect vibrations, pressure changes, and material properties, enabling advanced monitoring and control in fields such as structural health monitoring and process control.Expand Specific Solutions04 Longitudinal wave energy harvesting and conversion
Technologies for harvesting and converting energy from longitudinal waves are being developed. These innovations aim to capture and utilize the energy from various sources, such as ocean waves or mechanical vibrations, potentially providing sustainable power generation solutions.Expand Specific Solutions05 Longitudinal wave manipulation and control
Advanced techniques for manipulating and controlling longitudinal waves are emerging. These methods involve shaping wave fronts, focusing energy, and selectively attenuating or amplifying waves. Applications include improved communication systems, enhanced material processing, and novel acoustic devices.Expand Specific Solutions
Key Industry Players
The cybersecurity landscape for longitudinal wave implications in frameworks is evolving rapidly, with the market in its growth phase. As the technology matures, competition is intensifying among key players like AS0001, Inc., Expel, Inc., and CrowdStrike, Inc. These companies are developing innovative solutions to address the complex challenges of integrating longitudinal wave concepts into existing security architectures. The market size is expanding as organizations recognize the potential of this technology to enhance threat detection and response capabilities. However, the technology's full potential is yet to be realized, with ongoing research and development efforts focused on improving its effectiveness and scalability across diverse cybersecurity applications.
CrowdStrike, Inc.
Technical Solution: CrowdStrike has developed a novel approach to cybersecurity that leverages longitudinal wave analysis in their Falcon platform. This technology uses continuous monitoring and real-time threat intelligence to detect and respond to cyber threats. The system analyzes patterns of behavior over time, similar to how longitudinal waves propagate, to identify anomalies and potential security breaches. CrowdStrike's cloud-native architecture allows for rapid deployment and scalability, enabling organizations to protect endpoints, cloud workloads, and identity and data[1][3]. Their AI-powered threat detection engine processes trillions of events per week, providing a comprehensive view of the threat landscape and allowing for proactive threat hunting[2].
Strengths: Cloud-native architecture for scalability, AI-powered threat detection, and real-time response capabilities. Weaknesses: Potential for false positives in complex environments, and reliance on continuous internet connectivity for cloud-based operations.
ServiceNow, Inc.
Technical Solution: ServiceNow has integrated longitudinal wave concepts into its Security Operations and Governance, Risk, and Compliance (GRC) platforms to enhance cybersecurity frameworks. The company's approach involves creating a continuous, wave-like flow of security information across an organization's IT infrastructure. ServiceNow's Security Incident Response solution uses machine learning to analyze patterns of security events over time, similar to longitudinal wave propagation, to identify and prioritize potential threats[10]. The platform's Security Operations Center (SOC) Workspace provides real-time visibility into security incidents, allowing teams to respond quickly and effectively to emerging threats. Additionally, ServiceNow's Continuous Authorization and Assessment solution enables organizations to maintain a constant state of compliance by continuously monitoring and assessing their security posture against regulatory requirements and industry standards[11].
Strengths: Seamless integration with IT service management, automated workflow capabilities, and comprehensive visibility across the enterprise. Weaknesses: Complexity in implementation for organizations with legacy systems, and potential for over-reliance on automation without human oversight.
Core Innovations
Cyber attack information analyzing program, cyber attack information analyzing method, and information processing device
PatentWO2020017000A1
Innovation
- A cyber attack information analysis program and method that collects, analyzes, and outputs information on cyber threat intelligence, specifically identifying and monitoring IP addresses by determining their lifetime and address bands, allowing for the prioritization of long-lived IP addresses that are likely to be associated with persistent attacks.
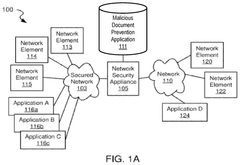
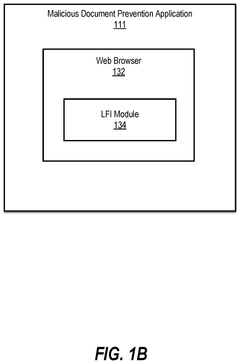
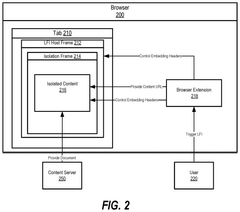
Malicious document prevention mechanism
PatentPendingUS20250240319A1
Innovation
- Implementing a layered frame isolation (LFI) mechanism in web browsers to render potentially malicious web pages in a sandboxed frame structure, controlling resource access through browser extensions without modifying the browser or installing additional systems.
Regulatory Compliance
Regulatory compliance in the context of longitudinal wave implications for cybersecurity frameworks has become increasingly complex and critical. As cyber threats evolve and become more sophisticated, regulatory bodies worldwide have been compelled to adapt their guidelines and requirements to address these emerging challenges. The integration of longitudinal wave analysis into cybersecurity frameworks has necessitated a reevaluation of existing compliance standards and the development of new regulations.
Many jurisdictions have begun to incorporate specific provisions related to longitudinal wave detection and mitigation into their cybersecurity regulations. For instance, the European Union's General Data Protection Regulation (GDPR) now includes clauses that mandate organizations to implement robust measures against longitudinal wave attacks as part of their data protection strategies. Similarly, the United States' National Institute of Standards and Technology (NIST) has updated its Cybersecurity Framework to include guidelines on longitudinal wave defense mechanisms.
Financial institutions, in particular, face stringent compliance requirements due to the sensitive nature of their data and operations. The Payment Card Industry Data Security Standard (PCI DSS) has been revised to include specific controls for detecting and preventing longitudinal wave intrusions in payment processing systems. These new regulations have significant implications for organizations' cybersecurity strategies and resource allocation.
Compliance with these evolving regulations presents both challenges and opportunities for businesses. On one hand, organizations must invest in new technologies and expertise to meet the regulatory requirements for longitudinal wave protection. This can be costly and time-consuming, particularly for smaller enterprises with limited resources. On the other hand, compliance can serve as a competitive advantage, demonstrating a commitment to robust cybersecurity practices and potentially attracting security-conscious customers and partners.
The regulatory landscape surrounding longitudinal wave implications in cybersecurity frameworks is dynamic and continues to evolve. As new threats emerge and technologies advance, regulatory bodies are likely to further refine their requirements. Organizations must stay vigilant and adaptable, continuously monitoring regulatory changes and updating their compliance strategies accordingly. This may involve regular risk assessments, staff training, and investments in cutting-edge cybersecurity solutions that address longitudinal wave vulnerabilities.
Ultimately, regulatory compliance in this area is not just about meeting legal obligations but also about fostering a culture of cybersecurity resilience. By aligning with these regulations, organizations can enhance their overall security posture, protect sensitive data, and build trust with stakeholders. As the regulatory framework continues to mature, it is expected to play a crucial role in shaping the future of cybersecurity practices and technologies related to longitudinal wave defense.
Many jurisdictions have begun to incorporate specific provisions related to longitudinal wave detection and mitigation into their cybersecurity regulations. For instance, the European Union's General Data Protection Regulation (GDPR) now includes clauses that mandate organizations to implement robust measures against longitudinal wave attacks as part of their data protection strategies. Similarly, the United States' National Institute of Standards and Technology (NIST) has updated its Cybersecurity Framework to include guidelines on longitudinal wave defense mechanisms.
Financial institutions, in particular, face stringent compliance requirements due to the sensitive nature of their data and operations. The Payment Card Industry Data Security Standard (PCI DSS) has been revised to include specific controls for detecting and preventing longitudinal wave intrusions in payment processing systems. These new regulations have significant implications for organizations' cybersecurity strategies and resource allocation.
Compliance with these evolving regulations presents both challenges and opportunities for businesses. On one hand, organizations must invest in new technologies and expertise to meet the regulatory requirements for longitudinal wave protection. This can be costly and time-consuming, particularly for smaller enterprises with limited resources. On the other hand, compliance can serve as a competitive advantage, demonstrating a commitment to robust cybersecurity practices and potentially attracting security-conscious customers and partners.
The regulatory landscape surrounding longitudinal wave implications in cybersecurity frameworks is dynamic and continues to evolve. As new threats emerge and technologies advance, regulatory bodies are likely to further refine their requirements. Organizations must stay vigilant and adaptable, continuously monitoring regulatory changes and updating their compliance strategies accordingly. This may involve regular risk assessments, staff training, and investments in cutting-edge cybersecurity solutions that address longitudinal wave vulnerabilities.
Ultimately, regulatory compliance in this area is not just about meeting legal obligations but also about fostering a culture of cybersecurity resilience. By aligning with these regulations, organizations can enhance their overall security posture, protect sensitive data, and build trust with stakeholders. As the regulatory framework continues to mature, it is expected to play a crucial role in shaping the future of cybersecurity practices and technologies related to longitudinal wave defense.
Risk Assessment Strategies
Risk assessment strategies in the context of longitudinal wave implications for cybersecurity frameworks require a comprehensive approach that considers both the temporal and spatial aspects of potential threats. These strategies must evolve to address the dynamic nature of cyber threats that propagate and mutate over time, much like longitudinal waves.
A key component of these strategies is the implementation of continuous monitoring systems that can detect and analyze patterns of attack propagation across networks. These systems should be capable of identifying the initial point of compromise and tracking the spread of malicious activities through various network segments. By understanding the wave-like progression of threats, security teams can better predict potential targets and implement preemptive measures.
Another critical aspect is the development of risk scoring models that incorporate time-based factors. Traditional risk assessment methods often provide a static snapshot of vulnerabilities, but longitudinal wave analysis demands a more dynamic approach. These models should consider the velocity of threat propagation, the persistence of attack campaigns, and the potential for threats to resurface after periods of dormancy.
Threat intelligence integration plays a vital role in longitudinal risk assessment. By aggregating and analyzing data from multiple sources over extended periods, organizations can identify emerging trends and anticipate future attack vectors. This approach enables the creation of proactive defense strategies that are aligned with the long-term evolution of cyber threats.
Scenario planning and simulation exercises are essential tools for evaluating the effectiveness of risk assessment strategies against longitudinal wave attacks. These exercises should model various attack progression scenarios, testing the organization's ability to detect, contain, and mitigate threats at different stages of propagation. The insights gained from these simulations can inform the refinement of security controls and incident response procedures.
Furthermore, risk assessment strategies must consider the cascading effects of longitudinal wave attacks across interconnected systems and supply chains. This requires a holistic view of the organization's digital ecosystem, including third-party relationships and data flows. By mapping these connections and assessing the potential for wave-like propagation of threats through these channels, organizations can develop more robust risk mitigation strategies.
Lastly, the implementation of adaptive security architectures is crucial for addressing the challenges posed by longitudinal wave implications. These architectures should be capable of dynamically adjusting security controls based on real-time risk assessments, ensuring that defenses evolve in tandem with the changing threat landscape. This approach enables organizations to maintain a proactive security posture in the face of complex, long-term cyber threats.
A key component of these strategies is the implementation of continuous monitoring systems that can detect and analyze patterns of attack propagation across networks. These systems should be capable of identifying the initial point of compromise and tracking the spread of malicious activities through various network segments. By understanding the wave-like progression of threats, security teams can better predict potential targets and implement preemptive measures.
Another critical aspect is the development of risk scoring models that incorporate time-based factors. Traditional risk assessment methods often provide a static snapshot of vulnerabilities, but longitudinal wave analysis demands a more dynamic approach. These models should consider the velocity of threat propagation, the persistence of attack campaigns, and the potential for threats to resurface after periods of dormancy.
Threat intelligence integration plays a vital role in longitudinal risk assessment. By aggregating and analyzing data from multiple sources over extended periods, organizations can identify emerging trends and anticipate future attack vectors. This approach enables the creation of proactive defense strategies that are aligned with the long-term evolution of cyber threats.
Scenario planning and simulation exercises are essential tools for evaluating the effectiveness of risk assessment strategies against longitudinal wave attacks. These exercises should model various attack progression scenarios, testing the organization's ability to detect, contain, and mitigate threats at different stages of propagation. The insights gained from these simulations can inform the refinement of security controls and incident response procedures.
Furthermore, risk assessment strategies must consider the cascading effects of longitudinal wave attacks across interconnected systems and supply chains. This requires a holistic view of the organization's digital ecosystem, including third-party relationships and data flows. By mapping these connections and assessing the potential for wave-like propagation of threats through these channels, organizations can develop more robust risk mitigation strategies.
Lastly, the implementation of adaptive security architectures is crucial for addressing the challenges posed by longitudinal wave implications. These architectures should be capable of dynamically adjusting security controls based on real-time risk assessments, ensuring that defenses evolve in tandem with the changing threat landscape. This approach enables organizations to maintain a proactive security posture in the face of complex, long-term cyber threats.
Unlock deeper insights with Patsnap Eureka Quick Research — get a full tech report to explore trends and direct your research. Try now!
Generate Your Research Report Instantly with AI Agent
Supercharge your innovation with Patsnap Eureka AI Agent Platform!