ROS 2 Security: SROS2 Policies, Key Handling And Isolation Domains
SEP 19, 20259 MIN READ
Generate Your Research Report Instantly with AI Agent
Patsnap Eureka helps you evaluate technical feasibility & market potential.
ROS 2 Security Evolution and Objectives
The evolution of ROS 2 security represents a significant paradigm shift from its predecessor, ROS 1, which was designed primarily for research environments with minimal security considerations. As robotics systems increasingly deploy in critical infrastructure, healthcare, and industrial settings, security has become paramount. The development of SROS2 (Secure ROS 2) marks a deliberate response to these emerging requirements, integrating security principles from the ground up rather than as an afterthought.
The security architecture of ROS 2 builds upon the DDS (Data Distribution Service) middleware, leveraging its built-in security features while extending them to address robotics-specific concerns. This evolution began with the initial ROS 2 release in 2017 and has progressively matured through subsequent distributions, with significant enhancements in Foxy Fitzroy and Galactic Geochelone releases.
A key objective of ROS 2 security is to provide confidentiality, integrity, and availability guarantees for robot communications without compromising the flexibility and modularity that made ROS popular. SROS2 implements these guarantees through a comprehensive security model that includes authentication, encryption, and access control mechanisms tailored to distributed robotic systems.
The policy framework within SROS2 aims to enable fine-grained access control over ROS resources, allowing system architects to define precisely which nodes can publish or subscribe to specific topics, call services, or access parameters. This granularity supports the principle of least privilege, ensuring components only access resources necessary for their function.
Key handling mechanisms represent another critical objective, addressing the challenges of secure key distribution and management in dynamic robotic environments. The evolution from manual key generation to more automated and scalable approaches reflects the growing complexity of robotic deployments and the need for manageable security solutions.
Isolation domains, a more recent development in the ROS 2 security roadmap, aim to create logical security boundaries within a robotic system. This concept enables different parts of a system to operate with varying security levels, accommodating components with different trust levels or security requirements within the same architecture.
The technical trajectory of ROS 2 security is moving toward greater integration with industry-standard security practices, including hardware security modules, certificate authorities, and compliance with security frameworks like IEC 62443 for industrial automation. This alignment with established security standards represents a strategic objective to facilitate adoption in regulated industries.
Looking forward, the ROS 2 security roadmap includes objectives for improved usability of security features, performance optimization of secure communications, and enhanced tools for security verification and compliance testing. These developments aim to address the current adoption barriers while maintaining robust security guarantees.
The security architecture of ROS 2 builds upon the DDS (Data Distribution Service) middleware, leveraging its built-in security features while extending them to address robotics-specific concerns. This evolution began with the initial ROS 2 release in 2017 and has progressively matured through subsequent distributions, with significant enhancements in Foxy Fitzroy and Galactic Geochelone releases.
A key objective of ROS 2 security is to provide confidentiality, integrity, and availability guarantees for robot communications without compromising the flexibility and modularity that made ROS popular. SROS2 implements these guarantees through a comprehensive security model that includes authentication, encryption, and access control mechanisms tailored to distributed robotic systems.
The policy framework within SROS2 aims to enable fine-grained access control over ROS resources, allowing system architects to define precisely which nodes can publish or subscribe to specific topics, call services, or access parameters. This granularity supports the principle of least privilege, ensuring components only access resources necessary for their function.
Key handling mechanisms represent another critical objective, addressing the challenges of secure key distribution and management in dynamic robotic environments. The evolution from manual key generation to more automated and scalable approaches reflects the growing complexity of robotic deployments and the need for manageable security solutions.
Isolation domains, a more recent development in the ROS 2 security roadmap, aim to create logical security boundaries within a robotic system. This concept enables different parts of a system to operate with varying security levels, accommodating components with different trust levels or security requirements within the same architecture.
The technical trajectory of ROS 2 security is moving toward greater integration with industry-standard security practices, including hardware security modules, certificate authorities, and compliance with security frameworks like IEC 62443 for industrial automation. This alignment with established security standards represents a strategic objective to facilitate adoption in regulated industries.
Looking forward, the ROS 2 security roadmap includes objectives for improved usability of security features, performance optimization of secure communications, and enhanced tools for security verification and compliance testing. These developments aim to address the current adoption barriers while maintaining robust security guarantees.
Market Demand for Secure Robotics Systems
The global market for secure robotics systems has experienced significant growth in recent years, driven by the increasing deployment of robots across various industries and the growing concern over cybersecurity threats. As robotic systems become more interconnected and integrated into critical infrastructure, the demand for robust security frameworks like SROS2 (Secure Robot Operating System 2) has intensified.
Manufacturing and industrial automation sectors represent the largest market segment for secure robotics systems, accounting for a substantial portion of the overall demand. These industries deploy robots for precision tasks, assembly lines, and quality control, where security breaches could lead to production disruptions, intellectual property theft, or even physical damage.
Healthcare robotics has emerged as another rapidly growing sector requiring enhanced security measures. Surgical robots, medication dispensing systems, and patient care robots handle sensitive patient data and perform critical procedures, making them attractive targets for cyberattacks. The regulatory requirements in healthcare further drive the adoption of secure robotics frameworks like SROS2.
Defense and security applications constitute a premium segment of the secure robotics market. Military and law enforcement agencies increasingly deploy autonomous or semi-autonomous systems for surveillance, reconnaissance, and threat neutralization. These applications demand the highest levels of security to prevent unauthorized access or control.
The logistics and transportation sector has also witnessed substantial growth in robotics adoption, particularly with the rise of autonomous delivery vehicles and warehouse automation. Companies in this space require robust security frameworks to protect their operations from potential disruptions and to safeguard customer data.
Market research indicates that organizations are increasingly prioritizing security features when selecting robotics platforms. A recent survey of robotics system integrators revealed that over 80% consider security capabilities as "very important" or "critical" in their procurement decisions, compared to just 45% five years ago.
The financial impact of security breaches in robotics systems has further accelerated market demand. The average cost of a security incident involving industrial robots is estimated to be significantly higher than traditional IT security breaches due to potential physical damage, production downtime, and safety implications.
Regional analysis shows North America and Europe leading in the adoption of secure robotics frameworks, with Asia-Pacific representing the fastest-growing market. This growth is particularly driven by China, Japan, and South Korea's aggressive investments in advanced manufacturing and smart city initiatives that incorporate robotics technologies.
Manufacturing and industrial automation sectors represent the largest market segment for secure robotics systems, accounting for a substantial portion of the overall demand. These industries deploy robots for precision tasks, assembly lines, and quality control, where security breaches could lead to production disruptions, intellectual property theft, or even physical damage.
Healthcare robotics has emerged as another rapidly growing sector requiring enhanced security measures. Surgical robots, medication dispensing systems, and patient care robots handle sensitive patient data and perform critical procedures, making them attractive targets for cyberattacks. The regulatory requirements in healthcare further drive the adoption of secure robotics frameworks like SROS2.
Defense and security applications constitute a premium segment of the secure robotics market. Military and law enforcement agencies increasingly deploy autonomous or semi-autonomous systems for surveillance, reconnaissance, and threat neutralization. These applications demand the highest levels of security to prevent unauthorized access or control.
The logistics and transportation sector has also witnessed substantial growth in robotics adoption, particularly with the rise of autonomous delivery vehicles and warehouse automation. Companies in this space require robust security frameworks to protect their operations from potential disruptions and to safeguard customer data.
Market research indicates that organizations are increasingly prioritizing security features when selecting robotics platforms. A recent survey of robotics system integrators revealed that over 80% consider security capabilities as "very important" or "critical" in their procurement decisions, compared to just 45% five years ago.
The financial impact of security breaches in robotics systems has further accelerated market demand. The average cost of a security incident involving industrial robots is estimated to be significantly higher than traditional IT security breaches due to potential physical damage, production downtime, and safety implications.
Regional analysis shows North America and Europe leading in the adoption of secure robotics frameworks, with Asia-Pacific representing the fastest-growing market. This growth is particularly driven by China, Japan, and South Korea's aggressive investments in advanced manufacturing and smart city initiatives that incorporate robotics technologies.
SROS2 Current Implementation and Challenges
SROS2 (Secure ROS 2) represents the security extension for the Robot Operating System 2 framework, designed to address the critical security requirements in robotic systems. The current implementation of SROS2 is built upon the DDS Security specification, leveraging its authentication, encryption, and access control mechanisms. This integration provides a foundation for secure communication between ROS 2 nodes, but several implementation challenges persist.
The core security features in SROS2 include node authentication through X.509 certificates, encrypted communications using TLS/DTLS protocols, and permission-based access control. The security model employs a Public Key Infrastructure (PKI) for managing certificates and keys, with tools for certificate generation, distribution, and revocation. However, the current key management system lacks robust mechanisms for secure storage and rotation, creating potential vulnerabilities in long-running robotic systems.
Policy management in SROS2 utilizes XML-based permission files that define which nodes can publish or subscribe to specific topics. While functional, this approach presents significant usability challenges. The complexity of manually creating and maintaining these permission files increases with system scale, often resulting in overly permissive configurations that undermine security objectives. Additionally, the static nature of these policies limits their adaptability to dynamic robotic environments.
Isolation domains, a concept intended to segregate different security contexts within a ROS 2 system, remain underdeveloped in the current implementation. The lack of well-defined boundaries between security domains complicates deployment in multi-tenant or multi-application robotic systems, where different components may require varying levels of security.
Performance overhead represents another significant challenge. The encryption and authentication processes introduce latency that can impact real-time operations critical for robotic systems. This overhead varies depending on message size and frequency, potentially creating bottlenecks in high-throughput scenarios.
Integration with existing ROS 2 tools and workflows remains problematic. Many development and debugging tools lack native support for secured communications, forcing developers to disable security during development and testing phases. This disconnect between development and production environments increases the risk of security vulnerabilities being introduced during deployment.
The adoption of SROS2 is further hindered by limited documentation and educational resources. The steep learning curve associated with security concepts and implementation details discourages many robotics developers from fully embracing these security features, leading to inconsistent security practices across the ROS 2 ecosystem.
The core security features in SROS2 include node authentication through X.509 certificates, encrypted communications using TLS/DTLS protocols, and permission-based access control. The security model employs a Public Key Infrastructure (PKI) for managing certificates and keys, with tools for certificate generation, distribution, and revocation. However, the current key management system lacks robust mechanisms for secure storage and rotation, creating potential vulnerabilities in long-running robotic systems.
Policy management in SROS2 utilizes XML-based permission files that define which nodes can publish or subscribe to specific topics. While functional, this approach presents significant usability challenges. The complexity of manually creating and maintaining these permission files increases with system scale, often resulting in overly permissive configurations that undermine security objectives. Additionally, the static nature of these policies limits their adaptability to dynamic robotic environments.
Isolation domains, a concept intended to segregate different security contexts within a ROS 2 system, remain underdeveloped in the current implementation. The lack of well-defined boundaries between security domains complicates deployment in multi-tenant or multi-application robotic systems, where different components may require varying levels of security.
Performance overhead represents another significant challenge. The encryption and authentication processes introduce latency that can impact real-time operations critical for robotic systems. This overhead varies depending on message size and frequency, potentially creating bottlenecks in high-throughput scenarios.
Integration with existing ROS 2 tools and workflows remains problematic. Many development and debugging tools lack native support for secured communications, forcing developers to disable security during development and testing phases. This disconnect between development and production environments increases the risk of security vulnerabilities being introduced during deployment.
The adoption of SROS2 is further hindered by limited documentation and educational resources. The steep learning curve associated with security concepts and implementation details discourages many robotics developers from fully embracing these security features, leading to inconsistent security practices across the ROS 2 ecosystem.
SROS2 Policy Implementation Approaches
01 Security policy management in ROS2 environments
Security policies in SROS2 define access control mechanisms that regulate communication between ROS2 nodes. These policies specify which nodes can publish, subscribe, or access services within the ROS2 ecosystem. The implementation includes policy enforcement points that validate requests against defined security rules, ensuring that only authorized components can interact with protected resources. Policy management frameworks allow for dynamic updates and centralized administration of security configurations across distributed robotic systems.- Security policy management in ROS2 environments: Security policies in SROS2 define access control mechanisms that regulate which nodes can communicate with each other and what operations they can perform. These policies can be configured to restrict communication between nodes based on their roles and responsibilities, enhancing the overall security of the ROS2 system. Policy management includes creation, distribution, and enforcement of security rules across distributed robotic systems.
- Key management and cryptographic infrastructure: SROS2 implements robust key handling mechanisms for secure communication between nodes. This includes generation, distribution, storage, and rotation of cryptographic keys used for authentication and encryption. The system utilizes public key infrastructure (PKI) to establish trust relationships between components, enabling secure message passing while maintaining system integrity and confidentiality.
- Isolation domains and containerization: Isolation domains in SROS2 provide logical separation between different components of a robotic system, limiting the potential impact of security breaches. This approach implements containerization and virtualization techniques to create secure boundaries between processes, preventing unauthorized access across domain boundaries. The isolation mechanism ensures that compromised nodes cannot affect the operation of other system components.
- Authentication and access control mechanisms: SROS2 implements comprehensive authentication and access control mechanisms to verify the identity of nodes and users before granting access to system resources. These mechanisms include certificate-based authentication, role-based access control, and fine-grained permission systems that regulate which operations can be performed by specific nodes or users, enhancing the security posture of robotic systems.
- Secure communication protocols and message encryption: SROS2 utilizes secure communication protocols to protect data exchanged between nodes in a robotic system. This includes end-to-end encryption of messages, secure channel establishment, and integrity verification mechanisms to prevent eavesdropping, tampering, and replay attacks. The implementation ensures that sensitive information remains confidential during transmission across potentially untrusted networks.
02 Cryptographic key management for secure communications
Key management in SROS2 involves the generation, distribution, storage, and rotation of cryptographic keys used to secure communications between ROS2 nodes. This includes certificate-based authentication mechanisms where public key infrastructure (PKI) is employed to establish trust relationships. The system supports secure key exchange protocols to establish encrypted channels between nodes, preventing eavesdropping and tampering. Implementations often include key lifecycle management features such as expiration, revocation, and renewal to maintain security over time.Expand Specific Solutions03 Isolation domains and containerization for ROS2
Isolation domains in SROS2 provide logical separation between different components or subsystems within a robotic platform. This approach uses containerization technologies to create boundaries that prevent unauthorized access between domains. Each isolation domain can have its own security context, policies, and access controls, limiting the potential impact of security breaches. The implementation supports multi-tenant architectures where different applications or services can operate securely on the same physical infrastructure without interfering with each other.Expand Specific Solutions04 Authentication and authorization frameworks
Authentication and authorization mechanisms in SROS2 verify the identity of nodes and determine their access rights within the system. These frameworks implement role-based access control (RBAC) where permissions are assigned based on the function or role of each component. The system supports fine-grained permission models that can restrict operations at the topic, service, or parameter level. Authentication protocols may include challenge-response mechanisms, token-based authentication, and integration with external identity providers to leverage existing security infrastructure.Expand Specific Solutions05 Secure middleware for robotic operating systems
Secure middleware implementations for ROS2 provide the foundation for all security features in SROS2. These middleware solutions incorporate encryption for data in transit, ensuring confidentiality and integrity of communications between nodes. They implement secure discovery protocols that prevent unauthorized nodes from joining the network and support message authentication codes (MACs) to verify message integrity. The middleware architecture includes security plugins that can be configured to meet specific security requirements while maintaining compatibility with the ROS2 communication patterns.Expand Specific Solutions
Key Organizations in ROS 2 Security Ecosystem
The ROS 2 security landscape is evolving rapidly, with the market currently in its growth phase as organizations increasingly prioritize secure robotic systems. The global ROS security market is expanding alongside the broader robotics industry, though still relatively niche compared to general cybersecurity. Technologically, SROS2 security implementations show varying maturity levels across companies. Industry leaders like Huawei, NVIDIA, and Google demonstrate advanced capabilities in implementing robust security policies and isolation domains, while companies like Intertrust Technologies and ZTE are developing specialized security frameworks. Academic institutions including Beihang University and Xidian University contribute significant research to advance SROS2 policy frameworks and key management protocols.
Intertrust Technologies Corp.
Technical Solution: Intertrust has developed a specialized security solution for ROS 2 that focuses on digital rights management and trusted computing principles. Their approach extends SROS2 with advanced key protection mechanisms that leverage Intertrust's expertise in whitebox cryptography and tamper-resistant software. The solution includes a secure key vault that protects cryptographic keys even when the operating system is compromised, ensuring that node authentication and communication encryption remain secure under advanced attack scenarios. Intertrust's framework enhances the SROS2 policy model with dynamic permission management that can adapt access rights based on contextual factors such as location, time, and system state. Their implementation also features sophisticated isolation domains that combine software-based compartmentalization with hardware security features to create trusted execution environments for critical ROS 2 components, effectively preventing unauthorized access to sensitive algorithms and data.
Strengths: Industry-leading expertise in digital rights management applied to robotics; excellent protection against reverse engineering and tampering; sophisticated key protection even on compromised systems. Weaknesses: Potential licensing complexity; may introduce additional computational overhead; specialized focus may not address all aspects of robotics security equally.
Google LLC
Technical Solution: Google has developed comprehensive security enhancements for ROS 2 through their contributions to SROS2 (Secure Robot Operating System 2). Their approach focuses on implementing DDS Security specifications with X.509 certificate-based authentication and authorization. Google's implementation leverages Transport Layer Security (TLS) for encrypted communications between ROS 2 nodes and provides tools for automated certificate management and distribution. Their security framework includes a policy-driven approach where administrators can define fine-grained access control policies that specify which nodes can publish or subscribe to specific topics, ensuring that only authorized components can exchange sensitive data. Google has also contributed to the development of isolation domains in ROS 2, allowing segregation of different subsystems to contain potential security breaches.
Strengths: Strong integration with cloud infrastructure and enterprise security systems; robust certificate management tools; extensive documentation and community support. Weaknesses: Implementation complexity may be challenging for smaller teams; potential performance overhead in resource-constrained environments; requires significant security expertise to properly configure.
Critical Security Technologies in SROS2
ROS system safety performance improvement method and system and storage medium
PatentPendingCN117354008A
Innovation
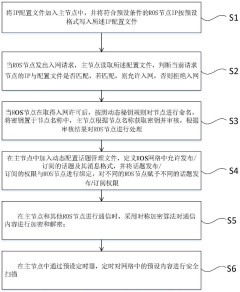
- Restrict the IPs connected to the ROS network by setting the IP configuration file in the master node, use dynamic key rules to name the nodes and perform identity authentication, dynamically configure the topic management file to bind publish/subscribe permissions, and use it during communication The symmetric encryption algorithm encrypts communication content, performs security scans on the network regularly, and eliminates illegal nodes and topics.
Attack method for robot operating system ROS message
PatentActiveCN112738022A
Innovation
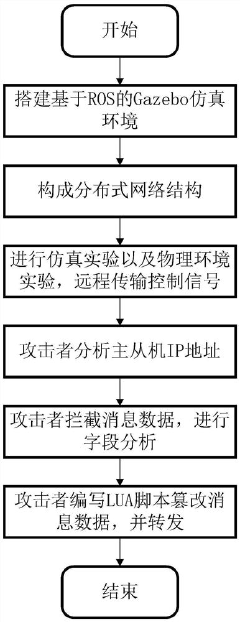
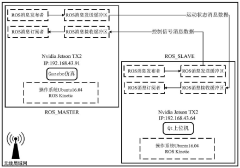
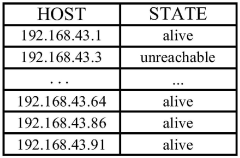
- By combining the Ettercap network sniffing tool and the NMAP port scanning tool, the control signal is intercepted and tampered, and the LUA language is used to write a filter to perform field analysis and tampering in the TCPROS transmission packet between the ROS MASTER and the slave machine, and implement a data tampering attack.
Compliance and Certification Standards
The adoption of SROS2 in critical systems necessitates adherence to various compliance and certification standards across different industries. In the automotive sector, ISO 26262 (Road Vehicles - Functional Safety) establishes requirements for electronic and electrical systems in vehicles, requiring SROS2 implementations to demonstrate robust security mechanisms that prevent unauthorized access and ensure system integrity. Similarly, the Automotive SPICE (Software Process Improvement and Capability Determination) framework evaluates software development processes, with SROS2 needing to meet its security-related process areas.
For industrial robotics and automation, IEC 62443 (Industrial Automation and Control Systems Security) provides a comprehensive framework for securing industrial control systems. SROS2's security features, particularly its policy enforcement and isolation domains, must align with the standard's requirements for zone segmentation and secure communication. The standard's defense-in-depth approach complements SROS2's layered security model, making compliance achievable but requiring thorough documentation and testing.
In healthcare robotics, FDA regulations for medical devices (including 21 CFR Part 820) and IEC 62304 (Medical Device Software Life Cycle Processes) impose stringent requirements on software security. SROS2 implementations must demonstrate that key handling procedures meet the confidentiality and integrity requirements specified in these standards, with particular attention to audit trails and access controls.
For general cybersecurity certification, Common Criteria (ISO/IEC 15408) provides a framework for evaluating security properties of IT products. SROS2 can be evaluated against specific Protection Profiles, with its security policies and isolation domains mapped to security functional requirements. Additionally, FIPS 140-2/3 certification may be required for cryptographic modules used in SROS2, particularly for government applications.
The Robot Operating System 2 (ROS 2) community has begun developing specific compliance guidelines for SROS2 implementations, though these are still evolving. These guidelines aim to provide a standardized approach to documenting security features and demonstrating compliance with relevant standards. Organizations implementing SROS2 should maintain comprehensive documentation of security policies, key management procedures, and isolation domain configurations to facilitate certification processes.
Achieving compliance often requires third-party assessment and certification, with costs and timeframes varying significantly based on the standard and certification level sought. Organizations should factor these considerations into project planning when implementing SROS2 in regulated environments.
For industrial robotics and automation, IEC 62443 (Industrial Automation and Control Systems Security) provides a comprehensive framework for securing industrial control systems. SROS2's security features, particularly its policy enforcement and isolation domains, must align with the standard's requirements for zone segmentation and secure communication. The standard's defense-in-depth approach complements SROS2's layered security model, making compliance achievable but requiring thorough documentation and testing.
In healthcare robotics, FDA regulations for medical devices (including 21 CFR Part 820) and IEC 62304 (Medical Device Software Life Cycle Processes) impose stringent requirements on software security. SROS2 implementations must demonstrate that key handling procedures meet the confidentiality and integrity requirements specified in these standards, with particular attention to audit trails and access controls.
For general cybersecurity certification, Common Criteria (ISO/IEC 15408) provides a framework for evaluating security properties of IT products. SROS2 can be evaluated against specific Protection Profiles, with its security policies and isolation domains mapped to security functional requirements. Additionally, FIPS 140-2/3 certification may be required for cryptographic modules used in SROS2, particularly for government applications.
The Robot Operating System 2 (ROS 2) community has begun developing specific compliance guidelines for SROS2 implementations, though these are still evolving. These guidelines aim to provide a standardized approach to documenting security features and demonstrating compliance with relevant standards. Organizations implementing SROS2 should maintain comprehensive documentation of security policies, key management procedures, and isolation domain configurations to facilitate certification processes.
Achieving compliance often requires third-party assessment and certification, with costs and timeframes varying significantly based on the standard and certification level sought. Organizations should factor these considerations into project planning when implementing SROS2 in regulated environments.
Cross-Platform Security Integration
The integration of SROS2 security mechanisms across diverse computing platforms presents significant challenges and opportunities for the ROS 2 ecosystem. Current robotic systems frequently operate in heterogeneous environments, utilizing various operating systems including Linux, Windows, macOS, and real-time operating systems (RTOS) such as QNX and VxWorks. Each platform implements security primitives differently, creating inconsistencies in how SROS2 policies and key management are handled across environments.
Security integration efforts must address the fundamental differences in cryptographic libraries and secure storage mechanisms across platforms. While Linux-based systems typically leverage OpenSSL and kernel keyring features, Windows environments may rely on CNG (Cryptography API: Next Generation) and the Windows Certificate Store. These differences necessitate platform-specific adaptations of SROS2's security infrastructure while maintaining consistent security guarantees.
The challenge extends to embedded systems commonly used in robotics, where computational and memory constraints limit the implementation of full security features. Lightweight cryptographic alternatives and optimized security protocols are being developed to accommodate these resource-constrained environments without compromising the core security model of SROS2.
Container technologies and virtualization present another dimension to cross-platform security integration. Docker, Kubernetes, and other containerization solutions are increasingly adopted in ROS 2 deployments, requiring special consideration for key distribution and policy enforcement across container boundaries. The isolation domains concept in SROS2 must be extended to recognize and respect container boundaries while enabling secure cross-container communication.
Cloud-robotics integration further complicates the security landscape, as ROS 2 systems increasingly connect to cloud services across different platforms. Secure authentication and communication between on-premise robots and cloud infrastructure demands consistent implementation of TLS/SSL protocols and certificate validation across all platforms involved in the communication chain.
Recent developments in the ROS 2 community have focused on creating platform-agnostic security interfaces that abstract away underlying platform differences. These efforts include standardized API layers for cryptographic operations and secure storage, allowing SROS2 to maintain consistent behavior regardless of the underlying operating system. The Security Working Group has prioritized this work to ensure that security policies can be defined once and deployed consistently across heterogeneous robot fleets.
Security integration efforts must address the fundamental differences in cryptographic libraries and secure storage mechanisms across platforms. While Linux-based systems typically leverage OpenSSL and kernel keyring features, Windows environments may rely on CNG (Cryptography API: Next Generation) and the Windows Certificate Store. These differences necessitate platform-specific adaptations of SROS2's security infrastructure while maintaining consistent security guarantees.
The challenge extends to embedded systems commonly used in robotics, where computational and memory constraints limit the implementation of full security features. Lightweight cryptographic alternatives and optimized security protocols are being developed to accommodate these resource-constrained environments without compromising the core security model of SROS2.
Container technologies and virtualization present another dimension to cross-platform security integration. Docker, Kubernetes, and other containerization solutions are increasingly adopted in ROS 2 deployments, requiring special consideration for key distribution and policy enforcement across container boundaries. The isolation domains concept in SROS2 must be extended to recognize and respect container boundaries while enabling secure cross-container communication.
Cloud-robotics integration further complicates the security landscape, as ROS 2 systems increasingly connect to cloud services across different platforms. Secure authentication and communication between on-premise robots and cloud infrastructure demands consistent implementation of TLS/SSL protocols and certificate validation across all platforms involved in the communication chain.
Recent developments in the ROS 2 community have focused on creating platform-agnostic security interfaces that abstract away underlying platform differences. These efforts include standardized API layers for cryptographic operations and secure storage, allowing SROS2 to maintain consistent behavior regardless of the underlying operating system. The Security Working Group has prioritized this work to ensure that security policies can be defined once and deployed consistently across heterogeneous robot fleets.
Unlock deeper insights with Patsnap Eureka Quick Research — get a full tech report to explore trends and direct your research. Try now!
Generate Your Research Report Instantly with AI Agent
Supercharge your innovation with Patsnap Eureka AI Agent Platform!