How to Ensure Solar Inverter Cybersecurity?
JUL 17, 20259 MIN READ
Generate Your Research Report Instantly with AI Agent
Patsnap Eureka helps you evaluate technical feasibility & market potential.
Solar Inverter Security Background and Objectives
Solar inverter cybersecurity has become a critical concern in the rapidly evolving landscape of renewable energy. As solar power generation continues to grow globally, the integration of smart grid technologies and the increasing connectivity of solar inverters have introduced new vulnerabilities to cyber threats. The evolution of solar inverter technology has progressed from simple power conversion devices to sophisticated, network-connected systems capable of two-way communication and advanced grid support functions.
The primary objective in addressing solar inverter cybersecurity is to safeguard the integrity, availability, and confidentiality of these critical components within the power infrastructure. This involves protecting against unauthorized access, data manipulation, and potential disruptions to power generation and distribution. The goal is to develop robust security measures that can withstand evolving cyber threats while maintaining the efficiency and reliability of solar energy systems.
Recent years have witnessed a surge in cyber attacks targeting critical infrastructure, including power grids. Solar inverters, as key components in distributed energy resources, have become attractive targets for malicious actors seeking to exploit vulnerabilities in the energy sector. These attacks could potentially lead to grid instability, power outages, or unauthorized control of energy resources, underscoring the urgency of enhancing cybersecurity measures.
The technical evolution of solar inverters has been marked by increased computational capabilities, advanced communication protocols, and integration with cloud-based monitoring and control systems. While these advancements have improved efficiency and grid integration, they have also expanded the attack surface for potential cyber threats. The challenge lies in balancing the benefits of connectivity and smart functionalities with robust security measures.
Industry standards and regulatory frameworks have begun to address the cybersecurity aspects of solar inverters. Organizations such as the IEC, IEEE, and NIST have developed guidelines and standards specific to the security of power systems and distributed energy resources. These efforts aim to establish a common framework for manufacturers, installers, and operators to implement comprehensive security measures throughout the lifecycle of solar inverter systems.
Looking ahead, the trajectory of solar inverter technology is expected to continue towards greater integration with energy management systems, advanced grid support capabilities, and enhanced data analytics. This evolution necessitates a proactive approach to cybersecurity, incorporating security-by-design principles, continuous monitoring, and adaptive defense mechanisms to stay ahead of emerging threats and ensure the resilience of solar energy infrastructure.
The primary objective in addressing solar inverter cybersecurity is to safeguard the integrity, availability, and confidentiality of these critical components within the power infrastructure. This involves protecting against unauthorized access, data manipulation, and potential disruptions to power generation and distribution. The goal is to develop robust security measures that can withstand evolving cyber threats while maintaining the efficiency and reliability of solar energy systems.
Recent years have witnessed a surge in cyber attacks targeting critical infrastructure, including power grids. Solar inverters, as key components in distributed energy resources, have become attractive targets for malicious actors seeking to exploit vulnerabilities in the energy sector. These attacks could potentially lead to grid instability, power outages, or unauthorized control of energy resources, underscoring the urgency of enhancing cybersecurity measures.
The technical evolution of solar inverters has been marked by increased computational capabilities, advanced communication protocols, and integration with cloud-based monitoring and control systems. While these advancements have improved efficiency and grid integration, they have also expanded the attack surface for potential cyber threats. The challenge lies in balancing the benefits of connectivity and smart functionalities with robust security measures.
Industry standards and regulatory frameworks have begun to address the cybersecurity aspects of solar inverters. Organizations such as the IEC, IEEE, and NIST have developed guidelines and standards specific to the security of power systems and distributed energy resources. These efforts aim to establish a common framework for manufacturers, installers, and operators to implement comprehensive security measures throughout the lifecycle of solar inverter systems.
Looking ahead, the trajectory of solar inverter technology is expected to continue towards greater integration with energy management systems, advanced grid support capabilities, and enhanced data analytics. This evolution necessitates a proactive approach to cybersecurity, incorporating security-by-design principles, continuous monitoring, and adaptive defense mechanisms to stay ahead of emerging threats and ensure the resilience of solar energy infrastructure.
Market Demand for Secure Solar Inverters
The market demand for secure solar inverters has been steadily increasing in recent years, driven by the growing adoption of solar energy systems and the rising awareness of cybersecurity threats in the renewable energy sector. As solar power becomes an increasingly significant component of the global energy mix, the need for robust cybersecurity measures in solar inverters has become paramount.
The solar inverter market is experiencing rapid growth, with projections indicating a compound annual growth rate (CAGR) of over 15% from 2021 to 2026. This growth is primarily fueled by the increasing installation of solar photovoltaic (PV) systems in both residential and commercial sectors. As these systems become more interconnected and integrated into smart grids, the potential vulnerabilities to cyber attacks have also increased, creating a strong demand for secure inverter solutions.
Utility companies and large-scale solar farm operators are particularly concerned about the cybersecurity of their solar inverters. These entities require inverters that can withstand sophisticated cyber attacks and protect critical infrastructure from potential disruptions. The financial implications of a successful cyber attack on solar inverters could be substantial, including power outages, equipment damage, and loss of revenue, further driving the demand for secure solutions.
Residential and commercial solar system owners are also becoming more aware of the importance of cybersecurity in their inverters. As smart home and building management systems become more prevalent, the integration of solar inverters into these networks has created new entry points for potential cyber threats. Consumers are increasingly seeking inverters with built-in security features to protect their personal data and ensure the reliability of their energy systems.
Government regulations and industry standards are playing a crucial role in shaping the market demand for secure solar inverters. Many countries have implemented or are in the process of implementing cybersecurity requirements for grid-connected devices, including solar inverters. These regulations are compelling manufacturers to prioritize security features in their product development and creating a market preference for compliant inverters.
The insurance industry is also influencing the demand for secure solar inverters. As cyber risks associated with renewable energy systems become more apparent, insurance providers are adjusting their policies and premiums based on the cybersecurity measures in place. This trend is encouraging solar system owners and operators to invest in more secure inverter technologies to mitigate potential financial risks and obtain more favorable insurance terms.
In response to these market demands, solar inverter manufacturers are increasingly focusing on developing advanced cybersecurity features. These include secure communication protocols, encryption technologies, regular firmware updates, and remote monitoring capabilities. The ability to demonstrate robust cybersecurity measures has become a key differentiator in the competitive solar inverter market, with manufacturers leveraging their security credentials to gain market share and customer trust.
The solar inverter market is experiencing rapid growth, with projections indicating a compound annual growth rate (CAGR) of over 15% from 2021 to 2026. This growth is primarily fueled by the increasing installation of solar photovoltaic (PV) systems in both residential and commercial sectors. As these systems become more interconnected and integrated into smart grids, the potential vulnerabilities to cyber attacks have also increased, creating a strong demand for secure inverter solutions.
Utility companies and large-scale solar farm operators are particularly concerned about the cybersecurity of their solar inverters. These entities require inverters that can withstand sophisticated cyber attacks and protect critical infrastructure from potential disruptions. The financial implications of a successful cyber attack on solar inverters could be substantial, including power outages, equipment damage, and loss of revenue, further driving the demand for secure solutions.
Residential and commercial solar system owners are also becoming more aware of the importance of cybersecurity in their inverters. As smart home and building management systems become more prevalent, the integration of solar inverters into these networks has created new entry points for potential cyber threats. Consumers are increasingly seeking inverters with built-in security features to protect their personal data and ensure the reliability of their energy systems.
Government regulations and industry standards are playing a crucial role in shaping the market demand for secure solar inverters. Many countries have implemented or are in the process of implementing cybersecurity requirements for grid-connected devices, including solar inverters. These regulations are compelling manufacturers to prioritize security features in their product development and creating a market preference for compliant inverters.
The insurance industry is also influencing the demand for secure solar inverters. As cyber risks associated with renewable energy systems become more apparent, insurance providers are adjusting their policies and premiums based on the cybersecurity measures in place. This trend is encouraging solar system owners and operators to invest in more secure inverter technologies to mitigate potential financial risks and obtain more favorable insurance terms.
In response to these market demands, solar inverter manufacturers are increasingly focusing on developing advanced cybersecurity features. These include secure communication protocols, encryption technologies, regular firmware updates, and remote monitoring capabilities. The ability to demonstrate robust cybersecurity measures has become a key differentiator in the competitive solar inverter market, with manufacturers leveraging their security credentials to gain market share and customer trust.
Current Cybersecurity Challenges in Solar Inverters
Solar inverter cybersecurity faces numerous challenges in today's interconnected energy landscape. As these devices play a crucial role in converting DC power from solar panels to AC power for the grid, their vulnerability to cyber threats poses significant risks to the stability and reliability of power systems.
One of the primary challenges is the increasing connectivity of solar inverters to the internet and smart grid systems. While this connectivity enables remote monitoring and control, it also exposes inverters to potential cyber attacks. Hackers could potentially exploit these connections to manipulate power output, disrupt grid operations, or even cause widespread blackouts.
Legacy systems and outdated firmware present another major challenge. Many older solar inverters lack robust security features and are not regularly updated, leaving them susceptible to known vulnerabilities. The long lifespan of solar installations often means that outdated equipment remains in use for extended periods, creating persistent security gaps.
The complexity of solar inverter systems also contributes to cybersecurity challenges. These devices often incorporate various components and software from different vendors, making it difficult to ensure consistent security measures across the entire system. This complexity can lead to unforeseen vulnerabilities and integration issues that cybercriminals may exploit.
Insufficient authentication and access control mechanisms pose additional risks. Many solar inverters lack strong authentication protocols or rely on default passwords, making unauthorized access relatively easy for attackers. Implementing robust access controls and multi-factor authentication can be challenging, especially for distributed solar installations.
Data privacy and integrity concerns also present significant challenges. Solar inverters collect and transmit sensitive data about energy production and consumption patterns. Ensuring the confidentiality and integrity of this data is crucial to prevent unauthorized access and manipulation, which could lead to financial losses or compromised grid operations.
The rapid pace of technological advancements in solar energy systems outstrips the development of corresponding cybersecurity measures. As new features and capabilities are introduced, security considerations often lag behind, creating potential vulnerabilities that attackers can exploit.
Lastly, the lack of standardized cybersecurity protocols and regulations specific to solar inverters complicates efforts to ensure consistent security across the industry. While general cybersecurity standards exist, their application to solar inverter systems is often unclear or insufficient, leaving manufacturers and operators without clear guidance on best practices and minimum security requirements.
One of the primary challenges is the increasing connectivity of solar inverters to the internet and smart grid systems. While this connectivity enables remote monitoring and control, it also exposes inverters to potential cyber attacks. Hackers could potentially exploit these connections to manipulate power output, disrupt grid operations, or even cause widespread blackouts.
Legacy systems and outdated firmware present another major challenge. Many older solar inverters lack robust security features and are not regularly updated, leaving them susceptible to known vulnerabilities. The long lifespan of solar installations often means that outdated equipment remains in use for extended periods, creating persistent security gaps.
The complexity of solar inverter systems also contributes to cybersecurity challenges. These devices often incorporate various components and software from different vendors, making it difficult to ensure consistent security measures across the entire system. This complexity can lead to unforeseen vulnerabilities and integration issues that cybercriminals may exploit.
Insufficient authentication and access control mechanisms pose additional risks. Many solar inverters lack strong authentication protocols or rely on default passwords, making unauthorized access relatively easy for attackers. Implementing robust access controls and multi-factor authentication can be challenging, especially for distributed solar installations.
Data privacy and integrity concerns also present significant challenges. Solar inverters collect and transmit sensitive data about energy production and consumption patterns. Ensuring the confidentiality and integrity of this data is crucial to prevent unauthorized access and manipulation, which could lead to financial losses or compromised grid operations.
The rapid pace of technological advancements in solar energy systems outstrips the development of corresponding cybersecurity measures. As new features and capabilities are introduced, security considerations often lag behind, creating potential vulnerabilities that attackers can exploit.
Lastly, the lack of standardized cybersecurity protocols and regulations specific to solar inverters complicates efforts to ensure consistent security across the industry. While general cybersecurity standards exist, their application to solar inverter systems is often unclear or insufficient, leaving manufacturers and operators without clear guidance on best practices and minimum security requirements.
Existing Cybersecurity Solutions for Solar Inverters
01 Secure communication protocols for solar inverters
Implementing secure communication protocols is crucial for protecting solar inverters from cyber threats. This includes encryption methods, authentication mechanisms, and secure data transmission techniques to prevent unauthorized access and data interception.- Secure communication protocols for solar inverters: Implementing secure communication protocols in solar inverters to protect against cyber threats. This includes encryption methods, authentication mechanisms, and secure data transmission techniques to ensure the integrity and confidentiality of communications between inverters and other components of the solar power system.
- Intrusion detection and prevention systems: Integrating intrusion detection and prevention systems into solar inverter networks to identify and mitigate potential cyber attacks. These systems monitor network traffic, detect anomalies, and implement defensive measures to protect the inverter and connected devices from unauthorized access or malicious activities.
- Firmware security and update mechanisms: Developing secure firmware update mechanisms and implementing measures to protect the integrity of inverter firmware. This includes cryptographic signing of firmware updates, secure boot processes, and mechanisms to prevent unauthorized modifications to the inverter's operating system and software.
- Access control and authentication systems: Implementing robust access control and authentication systems for solar inverters to prevent unauthorized access and ensure that only authorized personnel can modify settings or perform maintenance. This may include multi-factor authentication, role-based access control, and secure remote access protocols.
- Network segmentation and isolation: Employing network segmentation and isolation techniques to limit the potential impact of cyber attacks on solar inverter systems. This involves separating critical components of the solar power system into distinct network segments, implementing firewalls, and using virtual private networks (VPNs) for secure remote access.
02 Intrusion detection and prevention systems
Integrating intrusion detection and prevention systems into solar inverter networks helps identify and mitigate potential cyber attacks. These systems monitor network traffic, detect anomalies, and implement countermeasures to protect the inverter infrastructure.Expand Specific Solutions03 Firmware security and update mechanisms
Ensuring the security of solar inverter firmware and implementing secure update mechanisms is essential for maintaining cybersecurity. This includes measures to prevent unauthorized firmware modifications, secure boot processes, and authenticated update procedures.Expand Specific Solutions04 Access control and authentication systems
Implementing robust access control and authentication systems for solar inverters helps prevent unauthorized access and ensures that only authorized personnel can interact with the devices. This includes multi-factor authentication, role-based access control, and secure remote access solutions.Expand Specific Solutions05 Network segmentation and isolation
Employing network segmentation and isolation techniques helps contain potential cyber threats and limit their impact on solar inverter systems. This involves separating critical components, implementing firewalls, and creating secure zones within the network architecture.Expand Specific Solutions
Key Players in Solar Inverter Cybersecurity
The solar inverter cybersecurity market is in a growth phase, driven by increasing adoption of solar energy and rising concerns about grid security. The global market size is expanding rapidly, with projections indicating significant growth in the coming years. Technologically, the field is evolving quickly, with major players like SMA Solar Technology, Sungrow Power Supply, and Fronius International leading innovation. These companies are developing advanced security features, including encryption protocols and remote monitoring systems. Emerging players such as Enphase Energy and Huawei Digital Power are also making strides in this space, focusing on integrated security solutions for smart inverters. The competitive landscape is characterized by a mix of established manufacturers and new entrants, all striving to enhance cybersecurity measures in response to evolving threats and regulatory requirements.
SMA Solar Technology AG
Technical Solution: SMA Solar Technology AG has developed a comprehensive cybersecurity approach for solar inverters. Their strategy includes multi-layered protection mechanisms, such as secure boot processes, encrypted firmware updates, and role-based access control[1]. SMA's inverters utilize hardware-based security elements, like Trusted Platform Modules (TPM), to store cryptographic keys and perform secure operations[2]. They have also implemented a robust patch management system, ensuring timely updates to address newly discovered vulnerabilities. SMA's inverters support secure communication protocols like TLS 1.3 for data transmission, and they have integrated intrusion detection systems to monitor and alert on suspicious activities[3]. Additionally, SMA conducts regular security audits and penetration testing to identify and mitigate potential vulnerabilities in their solar inverter systems.
Strengths: Comprehensive multi-layered security approach, hardware-based security elements, and regular security audits. Weaknesses: Potential complexity in managing multiple security features, which may require specialized knowledge for installation and maintenance.
Sungrow Power Supply Co., Ltd.
Technical Solution: Sungrow has implemented a robust cybersecurity framework for their solar inverters, focusing on both hardware and software protection. Their inverters incorporate secure boot mechanisms and cryptographic modules to ensure the integrity of the system[4]. Sungrow has developed a proprietary security chip that provides hardware-level encryption and authentication for critical operations. Their inverters support secure communication protocols and utilize VPN technology for remote access, enhancing data protection during transmission[5]. Sungrow also employs a comprehensive identity and access management system, ensuring that only authorized personnel can access and modify inverter settings. Regular firmware updates are provided through a secure update mechanism, addressing potential vulnerabilities and enhancing system security over time.
Strengths: Proprietary security chip for hardware-level protection, secure remote access capabilities. Weaknesses: Potential dependency on proprietary technology may limit interoperability with third-party security solutions.
Core Innovations in Solar Inverter Security
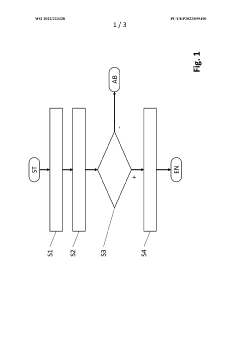
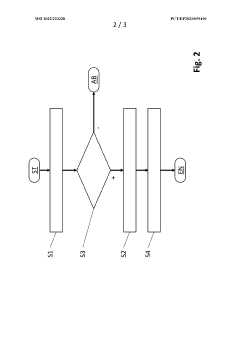
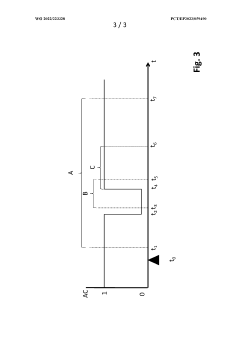
Method for defining authentication data of a user at an energy conversion device, and energy conversion device
PatentWO2022223328A1
Innovation
- A method that allows users to reassess and permanently store new authentication data on the device by disconnecting and reconnecting the energy conversion device within specified time windows, ensuring the user's proximity and preventing unauthorized access, using a communication processor that can be powered independently of the network.
Regulatory Framework for Solar Inverter Security
The regulatory framework for solar inverter security is a critical component in ensuring the cybersecurity of these essential devices in the renewable energy ecosystem. As the integration of solar power into the electrical grid continues to grow, governments and industry bodies have recognized the need for comprehensive guidelines and standards to protect against potential cyber threats.
At the international level, organizations such as the International Electrotechnical Commission (IEC) have developed standards specifically addressing the cybersecurity of power systems components, including solar inverters. The IEC 62351 series of standards provides a foundation for securing communication protocols used in power system operations, which is directly applicable to solar inverter security.
In the United States, the North American Electric Reliability Corporation (NERC) has established Critical Infrastructure Protection (CIP) standards that apply to bulk electric system components, including large-scale solar installations. While these standards may not directly address small-scale residential solar inverters, they set a precedent for cybersecurity practices in the energy sector.
The European Union has implemented the Network and Information Security (NIS) Directive, which requires operators of essential services, including those in the energy sector, to take appropriate security measures and report significant incidents. This directive has implications for solar inverter manufacturers and operators within the EU.
At the national level, countries are developing their own regulatory frameworks. For instance, Australia's Clean Energy Council has published guidelines for grid-connected energy systems via inverters, which include cybersecurity considerations. Similarly, Germany's Federal Office for Information Security (BSI) has issued technical guidelines for the secure implementation of smart meter gateways, which can be extended to solar inverter security.
Regulatory bodies are increasingly focusing on supply chain security as well. The U.S. Department of Energy's Cyber Testing for Resilient Industrial Control Systems (CyTRICS) program aims to identify vulnerabilities in the energy sector supply chain, including solar inverter components.
As the threat landscape evolves, regulatory frameworks are expected to become more stringent and specific to solar inverter cybersecurity. Future regulations may mandate regular security assessments, incident reporting protocols, and minimum security standards for solar inverter firmware and software. Additionally, certification schemes for cybersecure solar inverters are likely to emerge, providing a standardized way to assess and verify the security capabilities of these devices.
At the international level, organizations such as the International Electrotechnical Commission (IEC) have developed standards specifically addressing the cybersecurity of power systems components, including solar inverters. The IEC 62351 series of standards provides a foundation for securing communication protocols used in power system operations, which is directly applicable to solar inverter security.
In the United States, the North American Electric Reliability Corporation (NERC) has established Critical Infrastructure Protection (CIP) standards that apply to bulk electric system components, including large-scale solar installations. While these standards may not directly address small-scale residential solar inverters, they set a precedent for cybersecurity practices in the energy sector.
The European Union has implemented the Network and Information Security (NIS) Directive, which requires operators of essential services, including those in the energy sector, to take appropriate security measures and report significant incidents. This directive has implications for solar inverter manufacturers and operators within the EU.
At the national level, countries are developing their own regulatory frameworks. For instance, Australia's Clean Energy Council has published guidelines for grid-connected energy systems via inverters, which include cybersecurity considerations. Similarly, Germany's Federal Office for Information Security (BSI) has issued technical guidelines for the secure implementation of smart meter gateways, which can be extended to solar inverter security.
Regulatory bodies are increasingly focusing on supply chain security as well. The U.S. Department of Energy's Cyber Testing for Resilient Industrial Control Systems (CyTRICS) program aims to identify vulnerabilities in the energy sector supply chain, including solar inverter components.
As the threat landscape evolves, regulatory frameworks are expected to become more stringent and specific to solar inverter cybersecurity. Future regulations may mandate regular security assessments, incident reporting protocols, and minimum security standards for solar inverter firmware and software. Additionally, certification schemes for cybersecure solar inverters are likely to emerge, providing a standardized way to assess and verify the security capabilities of these devices.
Economic Impact of Solar Inverter Security Measures
The implementation of cybersecurity measures for solar inverters carries significant economic implications for various stakeholders in the solar energy industry. These security measures, while essential for protecting critical infrastructure, inevitably impact the cost structure of solar inverter manufacturing and deployment.
For manufacturers, the integration of robust cybersecurity features into solar inverters necessitates additional research and development investments. This includes costs associated with designing secure hardware components, developing encrypted communication protocols, and implementing advanced authentication mechanisms. These upfront expenses can lead to higher production costs, potentially affecting the final price of solar inverters in the market.
End-users, including residential and commercial solar system owners, may face increased initial costs when purchasing secure solar inverters. However, this investment can be viewed as a long-term economic benefit, as it mitigates the risk of costly cyberattacks that could result in system downtime, data breaches, or even physical damage to equipment.
For utility companies and grid operators, the economic impact of solar inverter security measures is multifaceted. On one hand, implementing comprehensive security protocols across the grid infrastructure requires substantial financial resources. This includes costs related to upgrading existing systems, training personnel, and maintaining ongoing security operations. On the other hand, these investments can lead to significant cost savings by preventing potential cyber incidents that could disrupt power supply, damage equipment, or compromise sensitive data.
The insurance sector is also affected by the adoption of solar inverter security measures. As the risk profile of solar energy systems improves with enhanced cybersecurity, insurers may adjust their policies and premiums accordingly. This could potentially lead to reduced insurance costs for solar system owners and operators who implement robust security measures.
From a broader economic perspective, the development and implementation of solar inverter security measures can stimulate growth in the cybersecurity industry. This creates new job opportunities, drives innovation, and potentially opens up new export markets for countries at the forefront of solar cybersecurity technology.
However, it is important to note that the economic impact of these security measures may vary across different regions and market segments. Developing countries, for instance, may face challenges in balancing the need for affordable solar energy solutions with the implementation of advanced cybersecurity features. This could potentially slow down the adoption of solar technology in these markets if not addressed through appropriate policy measures or international cooperation.
For manufacturers, the integration of robust cybersecurity features into solar inverters necessitates additional research and development investments. This includes costs associated with designing secure hardware components, developing encrypted communication protocols, and implementing advanced authentication mechanisms. These upfront expenses can lead to higher production costs, potentially affecting the final price of solar inverters in the market.
End-users, including residential and commercial solar system owners, may face increased initial costs when purchasing secure solar inverters. However, this investment can be viewed as a long-term economic benefit, as it mitigates the risk of costly cyberattacks that could result in system downtime, data breaches, or even physical damage to equipment.
For utility companies and grid operators, the economic impact of solar inverter security measures is multifaceted. On one hand, implementing comprehensive security protocols across the grid infrastructure requires substantial financial resources. This includes costs related to upgrading existing systems, training personnel, and maintaining ongoing security operations. On the other hand, these investments can lead to significant cost savings by preventing potential cyber incidents that could disrupt power supply, damage equipment, or compromise sensitive data.
The insurance sector is also affected by the adoption of solar inverter security measures. As the risk profile of solar energy systems improves with enhanced cybersecurity, insurers may adjust their policies and premiums accordingly. This could potentially lead to reduced insurance costs for solar system owners and operators who implement robust security measures.
From a broader economic perspective, the development and implementation of solar inverter security measures can stimulate growth in the cybersecurity industry. This creates new job opportunities, drives innovation, and potentially opens up new export markets for countries at the forefront of solar cybersecurity technology.
However, it is important to note that the economic impact of these security measures may vary across different regions and market segments. Developing countries, for instance, may face challenges in balancing the need for affordable solar energy solutions with the implementation of advanced cybersecurity features. This could potentially slow down the adoption of solar technology in these markets if not addressed through appropriate policy measures or international cooperation.
Unlock deeper insights with Patsnap Eureka Quick Research — get a full tech report to explore trends and direct your research. Try now!
Generate Your Research Report Instantly with AI Agent
Supercharge your innovation with Patsnap Eureka AI Agent Platform!