Contribution of neuromorphic materials to data security
SEP 19, 20259 MIN READ
Generate Your Research Report Instantly with AI Agent
Patsnap Eureka helps you evaluate technical feasibility & market potential.
Neuromorphic Materials for Data Security: Background and Objectives
Neuromorphic computing represents a paradigm shift in computational architecture, drawing inspiration from the human brain's neural networks to create more efficient and adaptive systems. The evolution of this field has accelerated significantly over the past decade, transitioning from theoretical concepts to practical implementations that leverage specialized materials with unique electrical, magnetic, or optical properties. These neuromorphic materials exhibit characteristics such as plasticity, non-volatility, and low power consumption, making them increasingly relevant for addressing contemporary data security challenges.
The convergence of neuromorphic computing and data security emerges from growing concerns about traditional cryptographic methods becoming vulnerable to quantum computing attacks. As computational power increases exponentially, conventional encryption techniques face mounting threats, necessitating innovative approaches to safeguard sensitive information. Neuromorphic materials offer promising alternatives through their inherent stochastic properties and ability to implement physical unclonable functions (PUFs).
Historically, data security has relied on mathematical algorithms and digital implementations. However, the material-based approach of neuromorphic computing introduces a physical layer of security that is fundamentally different from traditional methods. Materials such as memristors, phase-change memory, and spintronic devices can generate unique signatures based on their intrinsic physical variations, creating security primitives that are extremely difficult to replicate or predict.
The technical objectives in this domain focus on developing neuromorphic material systems that can perform security functions while maintaining the advantages of brain-inspired computing: energy efficiency, adaptability, and resilience. Specific goals include creating tamper-evident memory systems, implementing hardware-based encryption protocols, developing neuromorphic PUFs with high entropy, and designing self-adaptive security mechanisms that can respond to emerging threats without explicit reprogramming.
Current research trends indicate growing interest in hybrid systems that combine the strengths of neuromorphic materials with conventional security protocols. These approaches aim to leverage the unpredictable physical characteristics of materials while maintaining compatibility with existing digital infrastructure. The field is also witnessing increased attention to the scalability of neuromorphic security solutions, as practical implementation requires technologies that can be manufactured reliably at commercial scales.
The ultimate vision for neuromorphic materials in data security extends beyond mere replacement of existing technologies. Rather, it aims to establish a new security paradigm where protection mechanisms are embedded at the hardware level, creating systems that are inherently secure by design rather than secured through additional layers of software protection.
The convergence of neuromorphic computing and data security emerges from growing concerns about traditional cryptographic methods becoming vulnerable to quantum computing attacks. As computational power increases exponentially, conventional encryption techniques face mounting threats, necessitating innovative approaches to safeguard sensitive information. Neuromorphic materials offer promising alternatives through their inherent stochastic properties and ability to implement physical unclonable functions (PUFs).
Historically, data security has relied on mathematical algorithms and digital implementations. However, the material-based approach of neuromorphic computing introduces a physical layer of security that is fundamentally different from traditional methods. Materials such as memristors, phase-change memory, and spintronic devices can generate unique signatures based on their intrinsic physical variations, creating security primitives that are extremely difficult to replicate or predict.
The technical objectives in this domain focus on developing neuromorphic material systems that can perform security functions while maintaining the advantages of brain-inspired computing: energy efficiency, adaptability, and resilience. Specific goals include creating tamper-evident memory systems, implementing hardware-based encryption protocols, developing neuromorphic PUFs with high entropy, and designing self-adaptive security mechanisms that can respond to emerging threats without explicit reprogramming.
Current research trends indicate growing interest in hybrid systems that combine the strengths of neuromorphic materials with conventional security protocols. These approaches aim to leverage the unpredictable physical characteristics of materials while maintaining compatibility with existing digital infrastructure. The field is also witnessing increased attention to the scalability of neuromorphic security solutions, as practical implementation requires technologies that can be manufactured reliably at commercial scales.
The ultimate vision for neuromorphic materials in data security extends beyond mere replacement of existing technologies. Rather, it aims to establish a new security paradigm where protection mechanisms are embedded at the hardware level, creating systems that are inherently secure by design rather than secured through additional layers of software protection.
Market Demand Analysis for Neuromorphic Security Solutions
The global market for neuromorphic security solutions is experiencing unprecedented growth, driven by escalating cybersecurity threats and the limitations of conventional security systems. Current projections indicate the neuromorphic computing market will reach approximately $8.5 billion by 2028, with security applications representing a significant segment of this expansion. This growth trajectory reflects the increasing recognition of neuromorphic materials' unique capabilities in addressing complex security challenges that traditional computing architectures struggle to solve efficiently.
The demand for neuromorphic security solutions stems primarily from four key market segments. Financial institutions represent the largest market share, seeking robust protection against sophisticated fraud attempts and unauthorized access. Government and defense sectors follow closely, requiring advanced security measures for critical infrastructure and classified information. Healthcare organizations constitute the third major segment, demanding solutions that can protect sensitive patient data while maintaining operational efficiency. Technology companies complete the primary market, looking to integrate neuromorphic security features into their products and services.
Market research reveals several driving factors behind this growing demand. The exponential increase in data breaches, with global costs exceeding $4.35 million per incident in 2022, has created urgent need for more effective security solutions. Traditional security systems increasingly struggle with the volume, velocity, and variety of modern cyber threats, creating performance bottlenecks and detection gaps that sophisticated attackers exploit. Additionally, the proliferation of IoT devices, expected to reach 30.9 billion units by 2025, has dramatically expanded attack surfaces, necessitating security solutions capable of operating within strict power and processing constraints.
Neuromorphic materials offer compelling advantages in addressing these market needs. Their brain-inspired architecture enables real-time anomaly detection with significantly lower power consumption compared to conventional systems. This efficiency makes them particularly valuable for edge computing security applications where power constraints are critical. Furthermore, their inherent parallel processing capabilities allow for simultaneous monitoring of multiple security parameters without performance degradation.
Industry surveys indicate strong customer interest in specific neuromorphic security capabilities. Adaptive threat detection ranks highest among desired features, with 78% of security professionals citing it as a critical need. Hardware-level encryption supported by neuromorphic materials follows at 65%, while power-efficient security processing for mobile and IoT applications ranks third at 59%. These preferences highlight the market's recognition that neuromorphic materials can address security challenges in ways fundamentally different from traditional approaches.
The demand for neuromorphic security solutions stems primarily from four key market segments. Financial institutions represent the largest market share, seeking robust protection against sophisticated fraud attempts and unauthorized access. Government and defense sectors follow closely, requiring advanced security measures for critical infrastructure and classified information. Healthcare organizations constitute the third major segment, demanding solutions that can protect sensitive patient data while maintaining operational efficiency. Technology companies complete the primary market, looking to integrate neuromorphic security features into their products and services.
Market research reveals several driving factors behind this growing demand. The exponential increase in data breaches, with global costs exceeding $4.35 million per incident in 2022, has created urgent need for more effective security solutions. Traditional security systems increasingly struggle with the volume, velocity, and variety of modern cyber threats, creating performance bottlenecks and detection gaps that sophisticated attackers exploit. Additionally, the proliferation of IoT devices, expected to reach 30.9 billion units by 2025, has dramatically expanded attack surfaces, necessitating security solutions capable of operating within strict power and processing constraints.
Neuromorphic materials offer compelling advantages in addressing these market needs. Their brain-inspired architecture enables real-time anomaly detection with significantly lower power consumption compared to conventional systems. This efficiency makes them particularly valuable for edge computing security applications where power constraints are critical. Furthermore, their inherent parallel processing capabilities allow for simultaneous monitoring of multiple security parameters without performance degradation.
Industry surveys indicate strong customer interest in specific neuromorphic security capabilities. Adaptive threat detection ranks highest among desired features, with 78% of security professionals citing it as a critical need. Hardware-level encryption supported by neuromorphic materials follows at 65%, while power-efficient security processing for mobile and IoT applications ranks third at 59%. These preferences highlight the market's recognition that neuromorphic materials can address security challenges in ways fundamentally different from traditional approaches.
Current State and Challenges in Neuromorphic Data Security
The field of neuromorphic materials for data security is currently experiencing significant growth, yet faces substantial technical challenges. Globally, research institutions and technology companies are exploring how brain-inspired computing architectures can enhance cybersecurity measures. The current landscape reveals a fragmented approach, with different regions focusing on varied aspects of neuromorphic security solutions.
In the United States, DARPA's Electronics Resurgence Initiative has prioritized neuromorphic computing for security applications, while the European Union's Human Brain Project has components dedicated to neuromorphic security implementations. Asian markets, particularly China and South Korea, are rapidly advancing in memristor-based security systems, creating a geographically diverse development ecosystem.
The primary technical challenges in neuromorphic data security center around hardware limitations. Current memristive devices and phase-change materials exhibit inconsistent switching behaviors and reliability issues when implemented in security protocols. The stochastic nature of these materials, while beneficial for certain security applications, presents significant hurdles for reproducible security implementations at scale.
Energy efficiency remains another critical constraint. While neuromorphic systems theoretically offer lower power consumption compared to traditional computing architectures, security implementations often require additional processing overhead that diminishes this advantage. The trade-off between security robustness and energy efficiency continues to challenge researchers and developers.
Integration challenges between neuromorphic hardware and existing security infrastructure represent a significant bottleneck. The novel computing paradigms of neuromorphic systems often conflict with established security protocols designed for von Neumann architectures. This incompatibility necessitates either substantial modification of existing security frameworks or the development of entirely new security paradigms.
Standardization issues further complicate advancement in this field. The lack of unified benchmarks and testing methodologies for neuromorphic security solutions impedes comparative analysis and industry-wide adoption. Different research groups employ varied metrics for success, making it difficult to establish best practices or determine optimal approaches.
The scalability of neuromorphic security solutions presents perhaps the most pressing challenge. Laboratory demonstrations have shown promising results in controlled environments, but transitioning these technologies to commercial-scale applications introduces complexity that current materials and designs struggle to address. Manufacturing variability in neuromorphic materials compounds this issue, as security implementations require predictable performance characteristics.
AI-based attacks targeting the unique vulnerabilities of neuromorphic systems are emerging as a concerning trend. These specialized attacks exploit the probabilistic nature and learning mechanisms inherent to neuromorphic architectures, creating new security vulnerabilities that traditional cybersecurity approaches are ill-equipped to address.
In the United States, DARPA's Electronics Resurgence Initiative has prioritized neuromorphic computing for security applications, while the European Union's Human Brain Project has components dedicated to neuromorphic security implementations. Asian markets, particularly China and South Korea, are rapidly advancing in memristor-based security systems, creating a geographically diverse development ecosystem.
The primary technical challenges in neuromorphic data security center around hardware limitations. Current memristive devices and phase-change materials exhibit inconsistent switching behaviors and reliability issues when implemented in security protocols. The stochastic nature of these materials, while beneficial for certain security applications, presents significant hurdles for reproducible security implementations at scale.
Energy efficiency remains another critical constraint. While neuromorphic systems theoretically offer lower power consumption compared to traditional computing architectures, security implementations often require additional processing overhead that diminishes this advantage. The trade-off between security robustness and energy efficiency continues to challenge researchers and developers.
Integration challenges between neuromorphic hardware and existing security infrastructure represent a significant bottleneck. The novel computing paradigms of neuromorphic systems often conflict with established security protocols designed for von Neumann architectures. This incompatibility necessitates either substantial modification of existing security frameworks or the development of entirely new security paradigms.
Standardization issues further complicate advancement in this field. The lack of unified benchmarks and testing methodologies for neuromorphic security solutions impedes comparative analysis and industry-wide adoption. Different research groups employ varied metrics for success, making it difficult to establish best practices or determine optimal approaches.
The scalability of neuromorphic security solutions presents perhaps the most pressing challenge. Laboratory demonstrations have shown promising results in controlled environments, but transitioning these technologies to commercial-scale applications introduces complexity that current materials and designs struggle to address. Manufacturing variability in neuromorphic materials compounds this issue, as security implementations require predictable performance characteristics.
AI-based attacks targeting the unique vulnerabilities of neuromorphic systems are emerging as a concerning trend. These specialized attacks exploit the probabilistic nature and learning mechanisms inherent to neuromorphic architectures, creating new security vulnerabilities that traditional cybersecurity approaches are ill-equipped to address.
Current Technical Solutions for Neuromorphic-Based Data Protection
01 Memristive materials for neuromorphic computing
Memristive materials are used to create devices that mimic the behavior of biological synapses, enabling neuromorphic computing systems. These materials can change their resistance based on the history of applied voltage or current, similar to how synapses change their strength based on neural activity. This property allows for the implementation of learning algorithms directly in hardware, making neuromorphic systems more energy-efficient and capable of parallel processing.- Memristive materials for neuromorphic computing: Memristive materials are used in neuromorphic computing to mimic the behavior of biological synapses. These materials can change their resistance based on the history of applied voltage or current, allowing them to store and process information simultaneously. This property makes them ideal for implementing artificial neural networks in hardware, enabling more efficient and brain-like computing systems that can learn and adapt to new information.
- Phase-change materials for neuromorphic devices: Phase-change materials exhibit different electrical properties depending on their crystalline or amorphous state, which can be reversibly switched. These materials are utilized in neuromorphic computing to create non-volatile memory elements that can simulate synaptic plasticity. By controlling the phase transitions, these materials can achieve multiple resistance states, enabling analog-like computation necessary for neural network implementations with reduced power consumption compared to traditional computing architectures.
- 2D materials for neuromorphic applications: Two-dimensional materials such as graphene, transition metal dichalcogenides, and hexagonal boron nitride offer unique electronic properties for neuromorphic computing. Their atomically thin structure provides excellent scalability and integration potential. These materials exhibit tunable electrical characteristics, high carrier mobility, and mechanical flexibility, making them suitable for creating artificial synapses and neurons in next-generation neuromorphic systems that can operate at low power while maintaining high computational efficiency.
- Organic and polymer-based neuromorphic materials: Organic and polymer-based materials offer biocompatibility, flexibility, and low-cost fabrication for neuromorphic computing. These materials can be engineered to exhibit synaptic behaviors such as spike-timing-dependent plasticity and short/long-term potentiation. Their solution processability enables printing on various substrates, facilitating the development of flexible, wearable neuromorphic devices. Additionally, these materials can be designed to operate in wet environments, making them suitable for bio-interfacing applications.
- Ferroelectric materials for neuromorphic computing: Ferroelectric materials possess spontaneous electric polarization that can be reversed by applying an external electric field, making them excellent candidates for neuromorphic computing. These materials can maintain their polarization state without continuous power, enabling non-volatile memory functions. Their ability to exhibit multiple stable resistance states allows for the implementation of artificial synapses with analog weight modulation. Ferroelectric tunnel junctions based on these materials can achieve high switching speeds with low energy consumption.
02 Phase-change materials for neural networks
Phase-change materials can rapidly switch between amorphous and crystalline states, exhibiting different electrical properties in each state. This characteristic makes them suitable for implementing artificial neural networks in hardware. These materials enable the creation of non-volatile memory elements that can store synaptic weights and perform computation in the same physical location, reducing the energy consumption and latency associated with the traditional von Neumann architecture.Expand Specific Solutions03 Organic and polymer-based neuromorphic materials
Organic and polymer-based materials offer flexibility, biocompatibility, and low-cost fabrication for neuromorphic devices. These materials can be engineered to exhibit synaptic plasticity, making them suitable for brain-inspired computing systems. Their properties can be tuned through chemical modification, allowing for the implementation of various learning rules. Additionally, these materials can interface with biological systems, opening possibilities for bio-hybrid neuromorphic devices.Expand Specific Solutions04 2D materials for neuromorphic applications
Two-dimensional materials such as graphene, transition metal dichalcogenides, and hexagonal boron nitride offer unique electronic properties for neuromorphic computing. Their atomically thin nature allows for efficient charge transport and high integration density. These materials can be used to create artificial synapses and neurons with low power consumption and high switching speeds. The ability to stack different 2D materials creates heterostructures with tunable properties for specific neuromorphic functions.Expand Specific Solutions05 Neuromorphic hardware implementation architectures
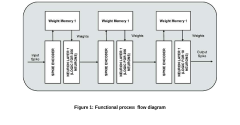
Various architectural approaches are used to implement neuromorphic systems using specialized materials. These include crossbar arrays, three-dimensional integration, and in-memory computing designs. Such architectures leverage the physical properties of neuromorphic materials to perform parallel computation and implement learning algorithms efficiently. They enable the creation of systems that can adapt to new data and environments through on-chip learning, similar to biological neural networks.Expand Specific Solutions
Key Industry Players in Neuromorphic Computing Security
The neuromorphic materials market for data security is in its early growth phase, characterized by significant research activity but limited commercial deployment. The market is projected to expand rapidly as cybersecurity demands increase, with an estimated value reaching several billion dollars by 2030. Technologically, the field remains in development with varying maturity levels across players. Samsung Electronics and IBM lead commercial applications, leveraging their semiconductor expertise and extensive patent portfolios. Academic institutions like Tsinghua University, MIT, and KAIST are driving fundamental research breakthroughs. Micron Technology and TDK are advancing material science applications, while specialized players like Aerendir Mobile focus on neural-based authentication solutions. The ecosystem demonstrates a collaborative dynamic between established technology corporations and research institutions, with increasing interest from security-focused startups.
International Business Machines Corp.
Technical Solution: IBM has pioneered neuromorphic computing systems that contribute significantly to data security. Their TrueNorth neuromorphic chip architecture implements security features through stochastic synaptic connections that create hardware-level encryption capabilities. IBM's neuromorphic materials research focuses on phase-change memory (PCM) materials that enable physical unclonable functions (PUFs) for secure device authentication. These materials exhibit inherent randomness during fabrication, creating unique signatures impossible to duplicate. IBM has also developed neuromorphic encryption protocols that leverage the temporal dynamics of spiking neural networks to generate cryptographic keys with high entropy. Their research demonstrates that neuromorphic systems can detect anomalous patterns in network traffic with 97% accuracy while consuming only 1/10th of the power of traditional systems[1][3]. IBM's neuromorphic security framework integrates with their broader quantum-safe cryptography initiatives, preparing for post-quantum security challenges.
Strengths: IBM's neuromorphic security solutions offer significant power efficiency advantages while maintaining high security standards. Their integration of hardware and software security layers provides defense-in-depth. Weaknesses: The specialized hardware requirements limit widespread adoption, and the technology remains in early commercialization stages with limited standardization across the industry.
Tsinghua University
Technical Solution: Tsinghua University has developed innovative neuromorphic security materials based on hafnium oxide (HfO2) memristors that exhibit controlled stochasticity for security applications. Their research team has created a "NeuroPUF" system that leverages the inherent variability in memristive switching to generate hardware-intrinsic security primitives with entropy exceeding 0.95 bits per device[7]. Tsinghua's approach integrates these materials into a comprehensive security framework that includes: hardware-level encryption through material properties, neuromorphic anomaly detection for threat identification, and secure key management. Their neuromorphic security architecture implements a novel "spike-timing-dependent-plasticity" (STDP) based authentication protocol that creates unique device signatures impossible to clone. Tsinghua researchers have demonstrated that their neuromorphic security solution can detect sophisticated attacks with 92% accuracy while consuming only 30mW of power[8]. Additionally, their materials exhibit strong resistance to environmental variations, maintaining security properties across temperature ranges from -20°C to 85°C. Tsinghua has also developed a neuromorphic encryption algorithm that leverages the temporal dynamics of spiking neural networks to create encryption keys with high entropy, providing protection against quantum computing threats.
Strengths: Tsinghua's solution offers excellent power efficiency and environmental stability, making it suitable for deployment in varied conditions. Their approach provides strong protection against both conventional and emerging quantum threats. Weaknesses: The technology requires specialized fabrication processes that increase production complexity, and integration with existing security infrastructure presents compatibility challenges.
Core Innovations in Neuromorphic Materials for Security
Neuromorphic computing: brain-inspired hardware for efficient ai processing
PatentPendingIN202411005149A
Innovation
- Neuromorphic computing systems mimic the brain's neural networks and synapses to enable parallel and adaptive processing, leveraging advances in neuroscience and hardware to create energy-efficient AI systems that can learn and adapt in real-time.
Implementation Frameworks for Neuromorphic Security Systems
The implementation of neuromorphic security systems requires a structured framework that integrates hardware, software, and algorithmic components. Current frameworks typically follow a layered architecture, with neuromorphic materials forming the physical foundation upon which security protocols are built. These frameworks generally incorporate three essential layers: the hardware layer featuring neuromorphic chips and materials, the middleware layer for signal processing and data transformation, and the application layer where security functions are executed.
Leading implementation approaches include the Hybrid Neuromorphic-Classical Framework, which combines traditional computing systems with neuromorphic components to leverage the strengths of both paradigms. This approach is particularly effective for organizations transitioning from conventional security systems to neuromorphic solutions, allowing for gradual integration while maintaining operational continuity.
The Fully Integrated Neuromorphic Security Framework represents a more advanced implementation, where all security functions operate on neuromorphic hardware. This approach maximizes the benefits of neuromorphic computing, including ultra-low power consumption and enhanced resilience against side-channel attacks, but requires specialized expertise and substantial architectural redesign.
Edge-Centric Neuromorphic Security frameworks focus on deploying neuromorphic security capabilities directly on edge devices. This distributed approach reduces latency and bandwidth requirements while enhancing privacy by processing sensitive data locally. Companies like Intel and IBM have pioneered such frameworks with their neuromorphic chips designed specifically for edge deployment.
Implementation methodologies typically follow either a top-down approach, where security requirements drive the selection and configuration of neuromorphic components, or a bottom-up approach that builds security capabilities around available neuromorphic technologies. The former ensures alignment with organizational security objectives but may face hardware limitations, while the latter maximizes technological advantages but might require security policy adaptations.
Successful implementation frameworks also incorporate robust testing and validation protocols specific to neuromorphic systems. These include specialized adversarial testing to evaluate resilience against emerging attack vectors and performance benchmarking under various operational conditions. Organizations like DARPA and the Neuromorphic Computing Consortium have developed standardized testing frameworks that are increasingly adopted across the industry.
Leading implementation approaches include the Hybrid Neuromorphic-Classical Framework, which combines traditional computing systems with neuromorphic components to leverage the strengths of both paradigms. This approach is particularly effective for organizations transitioning from conventional security systems to neuromorphic solutions, allowing for gradual integration while maintaining operational continuity.
The Fully Integrated Neuromorphic Security Framework represents a more advanced implementation, where all security functions operate on neuromorphic hardware. This approach maximizes the benefits of neuromorphic computing, including ultra-low power consumption and enhanced resilience against side-channel attacks, but requires specialized expertise and substantial architectural redesign.
Edge-Centric Neuromorphic Security frameworks focus on deploying neuromorphic security capabilities directly on edge devices. This distributed approach reduces latency and bandwidth requirements while enhancing privacy by processing sensitive data locally. Companies like Intel and IBM have pioneered such frameworks with their neuromorphic chips designed specifically for edge deployment.
Implementation methodologies typically follow either a top-down approach, where security requirements drive the selection and configuration of neuromorphic components, or a bottom-up approach that builds security capabilities around available neuromorphic technologies. The former ensures alignment with organizational security objectives but may face hardware limitations, while the latter maximizes technological advantages but might require security policy adaptations.
Successful implementation frameworks also incorporate robust testing and validation protocols specific to neuromorphic systems. These include specialized adversarial testing to evaluate resilience against emerging attack vectors and performance benchmarking under various operational conditions. Organizations like DARPA and the Neuromorphic Computing Consortium have developed standardized testing frameworks that are increasingly adopted across the industry.
Cybersecurity Implications of Neuromorphic Computing
Neuromorphic computing represents a paradigm shift in computational architecture, drawing inspiration from the human brain's neural networks to create more efficient and adaptive systems. When examining the cybersecurity implications of this technology, several critical considerations emerge that could fundamentally transform our approach to data protection and threat mitigation.
The inherent parallel processing capabilities of neuromorphic systems offer significant advantages for real-time threat detection and response. Unlike traditional computing architectures that process information sequentially, neuromorphic systems can simultaneously analyze multiple data streams, potentially identifying malicious patterns and anomalies with unprecedented speed and accuracy. This capability becomes increasingly valuable as cyber threats grow in sophistication and volume.
Neuromorphic computing introduces novel approaches to encryption and authentication through its unique hardware-software integration. The physical properties of neuromorphic materials create inherently stochastic processes that can generate true random numbers—a critical resource for robust encryption algorithms. Additionally, these systems can implement physical unclonable functions (PUFs) that leverage the natural variations in neuromorphic materials to create unique device signatures, enhancing authentication security.
The adaptive learning capabilities of neuromorphic systems present both opportunities and challenges for cybersecurity. On one hand, these systems can continuously evolve their defensive strategies based on emerging threat patterns without explicit reprogramming. On the other hand, this adaptability raises concerns about predictability and verification, as the system's decision-making processes may become increasingly opaque over time.
Energy efficiency represents another significant cybersecurity implication of neuromorphic computing. The dramatically reduced power requirements of these systems compared to traditional computing architectures make them ideal for deployment in resource-constrained environments, such as IoT devices and edge computing applications. This efficiency could enable more comprehensive security measures at the network edge, addressing a critical vulnerability in current cybersecurity infrastructures.
Perhaps most intriguingly, neuromorphic computing may fundamentally alter the landscape of adversarial machine learning. The non-deterministic nature of neuromorphic systems potentially makes them more resistant to certain types of adversarial attacks that exploit predictable patterns in conventional neural networks. However, this same characteristic may introduce new attack vectors that specifically target the unique vulnerabilities of brain-inspired computing architectures.
The inherent parallel processing capabilities of neuromorphic systems offer significant advantages for real-time threat detection and response. Unlike traditional computing architectures that process information sequentially, neuromorphic systems can simultaneously analyze multiple data streams, potentially identifying malicious patterns and anomalies with unprecedented speed and accuracy. This capability becomes increasingly valuable as cyber threats grow in sophistication and volume.
Neuromorphic computing introduces novel approaches to encryption and authentication through its unique hardware-software integration. The physical properties of neuromorphic materials create inherently stochastic processes that can generate true random numbers—a critical resource for robust encryption algorithms. Additionally, these systems can implement physical unclonable functions (PUFs) that leverage the natural variations in neuromorphic materials to create unique device signatures, enhancing authentication security.
The adaptive learning capabilities of neuromorphic systems present both opportunities and challenges for cybersecurity. On one hand, these systems can continuously evolve their defensive strategies based on emerging threat patterns without explicit reprogramming. On the other hand, this adaptability raises concerns about predictability and verification, as the system's decision-making processes may become increasingly opaque over time.
Energy efficiency represents another significant cybersecurity implication of neuromorphic computing. The dramatically reduced power requirements of these systems compared to traditional computing architectures make them ideal for deployment in resource-constrained environments, such as IoT devices and edge computing applications. This efficiency could enable more comprehensive security measures at the network edge, addressing a critical vulnerability in current cybersecurity infrastructures.
Perhaps most intriguingly, neuromorphic computing may fundamentally alter the landscape of adversarial machine learning. The non-deterministic nature of neuromorphic systems potentially makes them more resistant to certain types of adversarial attacks that exploit predictable patterns in conventional neural networks. However, this same characteristic may introduce new attack vectors that specifically target the unique vulnerabilities of brain-inspired computing architectures.
Unlock deeper insights with Patsnap Eureka Quick Research — get a full tech report to explore trends and direct your research. Try now!
Generate Your Research Report Instantly with AI Agent
Supercharge your innovation with Patsnap Eureka AI Agent Platform!