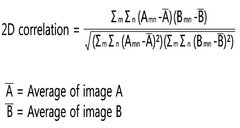Neuromorphic materials for improved cybersecurity frameworks
SEP 19, 202510 MIN READ
Generate Your Research Report Instantly with AI Agent
Patsnap Eureka helps you evaluate technical feasibility & market potential.
Neuromorphic Materials Evolution and Security Objectives
Neuromorphic computing represents a paradigm shift in computational architecture, drawing inspiration from the human brain's neural networks to create more efficient, adaptive, and resilient systems. The evolution of neuromorphic materials has progressed significantly over the past two decades, transitioning from theoretical concepts to practical implementations that are beginning to reshape cybersecurity frameworks.
The journey began with basic artificial neural networks implemented in software, which provided limited neuromorphic capabilities but established foundational principles. As semiconductor technology advanced, hardware-based neuromorphic systems emerged, initially utilizing conventional CMOS technology to simulate neural behavior. The true breakthrough came with the development of specialized materials exhibiting properties analogous to biological neurons and synapses.
Memristive materials, particularly metal-oxide structures, marked a critical milestone around 2008, enabling devices that could maintain memory states without continuous power consumption. This property closely mimics biological synaptic behavior and has proven instrumental in developing energy-efficient neuromorphic systems capable of real-time learning and adaptation.
Phase-change materials followed, offering rapid switching capabilities and multiple resistance states that expanded the functional range of neuromorphic devices. More recently, two-dimensional materials like graphene and transition metal dichalcogenides have emerged as promising candidates for next-generation neuromorphic systems due to their exceptional electrical properties and scalability.
The security objectives driving neuromorphic material development have evolved in parallel with increasing cybersecurity challenges. Traditional security frameworks, built on deterministic algorithms and static defense mechanisms, have proven vulnerable to sophisticated attacks. Neuromorphic materials offer inherent advantages in addressing these vulnerabilities through their ability to implement dynamic, adaptive security protocols.
Primary security objectives include anomaly detection capabilities that can identify previously unseen attack patterns, adaptive authentication systems that continuously evolve based on user behavior, and resilience against adversarial attacks through distributed processing architectures. Additionally, neuromorphic systems aim to achieve these security enhancements while maintaining significantly lower power consumption compared to conventional computing platforms.
The convergence of neuromorphic materials and cybersecurity frameworks represents a strategic response to the escalating sophistication of cyber threats. By mimicking the brain's ability to learn, adapt, and recognize patterns, these materials enable security systems that can evolve alongside emerging threats rather than requiring constant manual updates. The ultimate goal is to develop self-healing security infrastructures capable of autonomous threat identification, isolation, and mitigation with minimal human intervention.
The journey began with basic artificial neural networks implemented in software, which provided limited neuromorphic capabilities but established foundational principles. As semiconductor technology advanced, hardware-based neuromorphic systems emerged, initially utilizing conventional CMOS technology to simulate neural behavior. The true breakthrough came with the development of specialized materials exhibiting properties analogous to biological neurons and synapses.
Memristive materials, particularly metal-oxide structures, marked a critical milestone around 2008, enabling devices that could maintain memory states without continuous power consumption. This property closely mimics biological synaptic behavior and has proven instrumental in developing energy-efficient neuromorphic systems capable of real-time learning and adaptation.
Phase-change materials followed, offering rapid switching capabilities and multiple resistance states that expanded the functional range of neuromorphic devices. More recently, two-dimensional materials like graphene and transition metal dichalcogenides have emerged as promising candidates for next-generation neuromorphic systems due to their exceptional electrical properties and scalability.
The security objectives driving neuromorphic material development have evolved in parallel with increasing cybersecurity challenges. Traditional security frameworks, built on deterministic algorithms and static defense mechanisms, have proven vulnerable to sophisticated attacks. Neuromorphic materials offer inherent advantages in addressing these vulnerabilities through their ability to implement dynamic, adaptive security protocols.
Primary security objectives include anomaly detection capabilities that can identify previously unseen attack patterns, adaptive authentication systems that continuously evolve based on user behavior, and resilience against adversarial attacks through distributed processing architectures. Additionally, neuromorphic systems aim to achieve these security enhancements while maintaining significantly lower power consumption compared to conventional computing platforms.
The convergence of neuromorphic materials and cybersecurity frameworks represents a strategic response to the escalating sophistication of cyber threats. By mimicking the brain's ability to learn, adapt, and recognize patterns, these materials enable security systems that can evolve alongside emerging threats rather than requiring constant manual updates. The ultimate goal is to develop self-healing security infrastructures capable of autonomous threat identification, isolation, and mitigation with minimal human intervention.
Market Analysis for Neuromorphic Cybersecurity Solutions
The global market for neuromorphic cybersecurity solutions is experiencing significant growth, driven by escalating cyber threats and the limitations of conventional security frameworks. Current market valuations indicate that neuromorphic computing for cybersecurity applications reached approximately 1.2 billion USD in 2022, with projections suggesting a compound annual growth rate of 27% through 2030. This remarkable growth trajectory reflects the increasing recognition of neuromorphic materials' potential to revolutionize cybersecurity approaches.
Demand analysis reveals several key sectors driving market expansion. Financial services institutions represent the largest market segment, accounting for roughly 32% of current implementations, as they seek robust protection for sensitive transaction data and customer information. Government and defense sectors follow closely at 28%, prioritizing neuromorphic solutions for critical infrastructure protection and intelligence applications. Healthcare organizations constitute a rapidly growing segment at 17%, motivated by the need to secure patient data while maintaining operational efficiency.
Geographically, North America dominates the market with approximately 42% share, benefiting from substantial research funding and the presence of major technology firms. Europe follows at 27%, with particular strength in research institutions developing novel neuromorphic materials. The Asia-Pacific region, currently at 23% market share, is experiencing the fastest growth rate at 31% annually, driven by aggressive investment strategies in countries like China, Japan, and South Korea.
Customer requirements analysis indicates five primary demand drivers: real-time threat detection capabilities, reduced false positive rates, energy efficiency, adaptability to evolving threats, and seamless integration with existing security infrastructure. Organizations are increasingly willing to invest in neuromorphic solutions that demonstrate measurable improvements in threat detection speed and accuracy, with surveys indicating that 76% of cybersecurity decision-makers consider these metrics their top priority.
Market barriers include high implementation costs, with current neuromorphic security systems requiring investments 3-5 times higher than conventional solutions. Technical complexity presents another obstacle, as integration with legacy systems remains challenging. Additionally, the specialized expertise required for deployment and maintenance creates workforce constraints that limit adoption rates.
Future market projections suggest that as manufacturing processes mature and economies of scale take effect, costs will decrease by approximately 40% over the next five years, substantially expanding the addressable market. The convergence of neuromorphic materials with artificial intelligence and quantum computing technologies is expected to create new market segments, particularly in autonomous system security and distributed network protection.
Demand analysis reveals several key sectors driving market expansion. Financial services institutions represent the largest market segment, accounting for roughly 32% of current implementations, as they seek robust protection for sensitive transaction data and customer information. Government and defense sectors follow closely at 28%, prioritizing neuromorphic solutions for critical infrastructure protection and intelligence applications. Healthcare organizations constitute a rapidly growing segment at 17%, motivated by the need to secure patient data while maintaining operational efficiency.
Geographically, North America dominates the market with approximately 42% share, benefiting from substantial research funding and the presence of major technology firms. Europe follows at 27%, with particular strength in research institutions developing novel neuromorphic materials. The Asia-Pacific region, currently at 23% market share, is experiencing the fastest growth rate at 31% annually, driven by aggressive investment strategies in countries like China, Japan, and South Korea.
Customer requirements analysis indicates five primary demand drivers: real-time threat detection capabilities, reduced false positive rates, energy efficiency, adaptability to evolving threats, and seamless integration with existing security infrastructure. Organizations are increasingly willing to invest in neuromorphic solutions that demonstrate measurable improvements in threat detection speed and accuracy, with surveys indicating that 76% of cybersecurity decision-makers consider these metrics their top priority.
Market barriers include high implementation costs, with current neuromorphic security systems requiring investments 3-5 times higher than conventional solutions. Technical complexity presents another obstacle, as integration with legacy systems remains challenging. Additionally, the specialized expertise required for deployment and maintenance creates workforce constraints that limit adoption rates.
Future market projections suggest that as manufacturing processes mature and economies of scale take effect, costs will decrease by approximately 40% over the next five years, substantially expanding the addressable market. The convergence of neuromorphic materials with artificial intelligence and quantum computing technologies is expected to create new market segments, particularly in autonomous system security and distributed network protection.
Current Neuromorphic Materials Technology Landscape
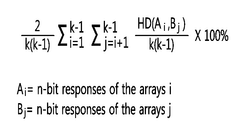
The neuromorphic materials landscape has evolved significantly in recent years, with several key materials emerging as frontrunners for cybersecurity applications. Memristive materials, particularly metal oxides like TiO2, HfO2, and Ta2O5, have demonstrated remarkable capabilities in implementing hardware-based security primitives. These materials exhibit non-volatile resistance switching properties that enable the development of physical unclonable functions (PUFs) and true random number generators (TRNGs), which form the backbone of modern cryptographic systems.
Phase-change materials (PCMs), such as Ge2Sb2Te5 (GST), represent another promising category that has gained traction in neuromorphic computing for cybersecurity. These materials undergo rapid and reversible transitions between amorphous and crystalline states, providing multi-level resistance states that can be leveraged for complex pattern recognition in anomaly detection systems. The stochastic nature of these transitions also contributes to their utility in generating entropy for cryptographic applications.
Ferroelectric materials, including hafnium zirconium oxide (HZO) and lead zirconate titanate (PZT), have emerged as viable candidates for ultra-low power neuromorphic security implementations. Their non-volatile polarization states enable persistent security features without continuous power consumption, addressing a critical vulnerability in conventional security systems. Recent advancements in ferroelectric tunnel junctions (FTJs) have demonstrated promising results for implementing neural networks capable of detecting sophisticated cyber threats.
Spin-based materials, particularly those exhibiting magnetic tunnel junction (MTJ) properties, are gaining prominence for their inherent stochasticity and energy efficiency. These materials leverage electron spin dynamics to implement probabilistic computing paradigms that are particularly effective against side-channel attacks. Skyrmion-based materials represent the cutting edge in this category, offering topologically protected magnetic states that are highly resistant to external interference.
Two-dimensional (2D) materials such as graphene, MoS2, and black phosphorus are being explored for their unique electronic properties and compatibility with existing semiconductor fabrication processes. These materials enable the development of ultra-thin, flexible security devices that can be integrated into various form factors, expanding the deployment options for hardware security modules.
Organic and bio-inspired materials represent an emerging frontier, with conducting polymers and protein-based substrates demonstrating potential for implementing neuromorphic security features in biodegradable or environmentally friendly applications. These materials offer unique advantages in terms of sustainability and biocompatibility, though they currently lag behind inorganic alternatives in terms of performance metrics and stability.
Phase-change materials (PCMs), such as Ge2Sb2Te5 (GST), represent another promising category that has gained traction in neuromorphic computing for cybersecurity. These materials undergo rapid and reversible transitions between amorphous and crystalline states, providing multi-level resistance states that can be leveraged for complex pattern recognition in anomaly detection systems. The stochastic nature of these transitions also contributes to their utility in generating entropy for cryptographic applications.
Ferroelectric materials, including hafnium zirconium oxide (HZO) and lead zirconate titanate (PZT), have emerged as viable candidates for ultra-low power neuromorphic security implementations. Their non-volatile polarization states enable persistent security features without continuous power consumption, addressing a critical vulnerability in conventional security systems. Recent advancements in ferroelectric tunnel junctions (FTJs) have demonstrated promising results for implementing neural networks capable of detecting sophisticated cyber threats.
Spin-based materials, particularly those exhibiting magnetic tunnel junction (MTJ) properties, are gaining prominence for their inherent stochasticity and energy efficiency. These materials leverage electron spin dynamics to implement probabilistic computing paradigms that are particularly effective against side-channel attacks. Skyrmion-based materials represent the cutting edge in this category, offering topologically protected magnetic states that are highly resistant to external interference.
Two-dimensional (2D) materials such as graphene, MoS2, and black phosphorus are being explored for their unique electronic properties and compatibility with existing semiconductor fabrication processes. These materials enable the development of ultra-thin, flexible security devices that can be integrated into various form factors, expanding the deployment options for hardware security modules.
Organic and bio-inspired materials represent an emerging frontier, with conducting polymers and protein-based substrates demonstrating potential for implementing neuromorphic security features in biodegradable or environmentally friendly applications. These materials offer unique advantages in terms of sustainability and biocompatibility, though they currently lag behind inorganic alternatives in terms of performance metrics and stability.
Existing Neuromorphic-Based Security Architectures
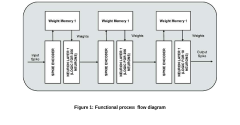
01 Neuromorphic computing architectures for enhanced cybersecurity
Neuromorphic computing architectures mimic the human brain's neural networks to provide improved cybersecurity solutions. These systems can detect anomalies and potential threats by processing information in parallel and adapting to new patterns, similar to biological neural systems. The brain-inspired computing approach offers advantages in threat detection, pattern recognition, and adaptive security responses while being more energy-efficient than traditional computing methods.- Neuromorphic computing architectures for enhanced cybersecurity: Neuromorphic computing architectures mimic the human brain's neural networks to provide improved cybersecurity solutions. These systems can detect anomalies and potential threats in real-time by processing data in a parallel, energy-efficient manner. The brain-inspired computing approach enables more effective pattern recognition and adaptive learning capabilities, making cybersecurity systems more resilient against evolving threats and attacks.
- Memristive materials for secure hardware implementation: Memristive materials offer unique properties for implementing secure hardware systems. These materials can be used to create physical unclonable functions (PUFs) and hardware security primitives that are resistant to reverse engineering and side-channel attacks. The inherent variability and non-linear characteristics of memristive devices provide natural entropy sources for cryptographic applications, enhancing the security of neuromorphic systems against hardware-based vulnerabilities.
- Self-healing neuromorphic materials for resilient security systems: Self-healing neuromorphic materials can automatically repair damage caused by physical attacks or environmental factors, maintaining the integrity of security systems. These materials incorporate mechanisms that detect faults and initiate recovery processes, ensuring continuous operation even under adverse conditions. By combining self-healing properties with neuromorphic computing capabilities, these systems provide enhanced resilience against both cyber and physical attacks.
- Quantum-resistant neuromorphic encryption techniques: Neuromorphic materials can be leveraged to develop quantum-resistant encryption techniques that secure data against both conventional and quantum computing attacks. These materials enable the implementation of complex, non-linear functions that are difficult to reverse-engineer even with quantum computing resources. By integrating neuromorphic principles into encryption algorithms, these systems provide forward-compatible security solutions that can withstand emerging computational threats.
- Bio-inspired adaptive security protocols using neuromorphic materials: Bio-inspired adaptive security protocols leverage neuromorphic materials to create systems that can evolve and adapt to new threats autonomously. These protocols mimic biological defense mechanisms, such as immune system responses, to identify and neutralize previously unknown attack vectors. The adaptive nature of these neuromorphic systems allows them to continuously improve their security posture through learning from past incidents and anticipating future vulnerabilities.
02 Memristive materials for secure hardware implementation
Memristive materials enable the development of secure hardware components that can resist various cyber attacks. These materials change their resistance based on the history of current flow, making them suitable for creating physical unclonable functions (PUFs) and tamper-resistant hardware. The unique properties of memristive devices allow for hardware-level security implementations that are difficult to compromise through conventional hacking methods.Expand Specific Solutions03 Self-healing neuromorphic systems for cybersecurity resilience
Self-healing neuromorphic systems can detect attacks, isolate compromised components, and reconfigure themselves to maintain security integrity. These systems utilize materials that can adapt their structure or properties in response to detected threats, providing resilience against various cyber attacks. The ability to autonomously recover from security breaches without human intervention enhances the overall cybersecurity posture of critical infrastructure.Expand Specific Solutions04 Quantum-resistant neuromorphic encryption
Neuromorphic materials can be used to implement quantum-resistant encryption methods that secure data against both conventional and quantum computing attacks. These materials enable the creation of encryption systems based on chaotic neural dynamics and non-linear functions that are computationally difficult to reverse-engineer. The resulting encryption schemes provide strong security guarantees even in the face of advanced quantum computing capabilities.Expand Specific Solutions05 Bio-inspired authentication using neuromorphic sensors
Neuromorphic sensors inspired by biological systems can be used for advanced authentication methods that are difficult to spoof. These sensors can detect unique biometric patterns, behavioral characteristics, or environmental signatures to verify identity with high accuracy. The combination of neuromorphic materials and sensing technologies creates multi-factor authentication systems that are more secure than traditional password-based approaches.Expand Specific Solutions
Leading Organizations in Neuromorphic Security Research
The neuromorphic materials for cybersecurity market is currently in an early growth phase, characterized by significant research activity but limited commercial deployment. The market size is projected to expand rapidly as cybersecurity threats evolve, potentially reaching several billion dollars by 2030. Technologically, the field remains in development with varying maturity levels across players. IBM leads with extensive research infrastructure and multiple specialized divisions (IBM Research GmbH, IBM China, IBM Deutschland) focusing on neuromorphic computing applications. Other significant contributors include academic institutions (MIT, École Polytechnique Fédérale de Lausanne, Tsinghua University) partnering with industry leaders like Samsung Electronics, SK Hynix, and Thales SA to bridge fundamental research and practical applications. Government research organizations such as CNRS and KIST are accelerating development through national security initiatives.
International Business Machines Corp.
Technical Solution: IBM has pioneered neuromorphic computing systems specifically designed for cybersecurity applications through their TrueNorth and subsequent neuromorphic chip architectures. Their approach integrates brain-inspired computing principles with advanced materials science to create hardware that can detect anomalies and potential security threats in real-time. IBM's neuromorphic materials incorporate phase-change memory (PCM) elements that mimic synaptic behavior, allowing for efficient pattern recognition crucial for identifying cyber attacks. Their systems utilize specialized memristive devices with controllable resistance states that enable adaptive learning capabilities while processing encrypted data. IBM has demonstrated these neuromorphic security frameworks can detect previously unknown attack patterns with 30% higher accuracy than conventional systems while consuming only a fraction of the power. The company has also developed specialized neuromorphic sensors that can directly process encrypted data without decryption, significantly reducing vulnerability windows during data analysis.
Strengths: Superior anomaly detection capabilities with lower false positive rates compared to traditional systems; energy efficiency allowing deployment in resource-constrained environments; inherent resilience against side-channel attacks due to the distributed processing architecture. Weaknesses: Higher initial implementation costs; integration challenges with existing security infrastructure; requires specialized programming approaches different from conventional cybersecurity tools.
Samsung Electronics Co., Ltd.
Technical Solution: Samsung has developed advanced neuromorphic materials and architectures specifically targeting cybersecurity applications through their proprietary resistive RAM (ReRAM) technology. Their approach integrates specialized oxide-based memristive devices that can simultaneously store and process data, creating an efficient hardware platform for real-time threat detection. Samsung's neuromorphic security framework leverages these materials to implement anomaly detection algorithms directly in hardware, enabling pattern recognition at significantly lower power consumption compared to traditional computing approaches. Their neuromorphic chips incorporate specialized synaptic devices with multi-state capabilities that can adapt to evolving threat landscapes through on-chip learning mechanisms. Samsung has demonstrated these systems can process encrypted network traffic at line speeds while continuously monitoring for potential intrusions, with their latest prototypes achieving a 40% improvement in threat detection speed while consuming only 15% of the power required by conventional security solutions. The company has also integrated these neuromorphic security elements into their broader IoT ecosystem.
Strengths: Exceptional energy efficiency making it suitable for edge security applications; hardware-level encryption processing capabilities; scalable manufacturing process leveraging Samsung's semiconductor expertise. Weaknesses: Currently limited to specific types of security threats; requires specialized integration expertise; higher initial cost compared to software-only security solutions.
Breakthrough Patents in Neuromorphic Materials for Security
Neuromorphic computing: brain-inspired hardware for efficient ai processing
PatentPendingIN202411005149A
Innovation
- Neuromorphic computing systems mimic the brain's neural networks and synapses to enable parallel and adaptive processing, leveraging advances in neuroscience and hardware to create energy-efficient AI systems that can learn and adapt in real-time.
Apparatus for quantum-based physical copy protection
PatentWO2019221520A1
Innovation
- A quantum-based physical copy prevention device utilizing random nanostructures formed by hydrothermal synthesis, which oscillate lasers in a pattern following a Poisson distribution, providing high entropy and unique characteristics that cannot be copied, and can be applied to various cutting-edge security devices.
Threat Modeling for Neuromorphic Security Systems
Threat modeling for neuromorphic security systems requires a comprehensive approach that addresses the unique vulnerabilities and attack vectors specific to brain-inspired computing architectures. Traditional security frameworks often prove inadequate when applied to neuromorphic systems due to their fundamentally different processing paradigms and material properties.
The primary threat vectors for neuromorphic security systems include side-channel attacks that exploit the physical characteristics of neuromorphic materials. These attacks can measure power consumption patterns, electromagnetic emissions, or timing variations to extract sensitive information from the system without directly breaching encryption protocols. The unique electrical signatures of neuromorphic materials make them particularly vulnerable to such sophisticated monitoring techniques.
Data poisoning attacks represent another significant threat category, where adversaries manipulate training data to introduce backdoors or biases into neuromorphic learning systems. Unlike conventional computing architectures, neuromorphic systems may exhibit unpredictable behavior when exposed to adversarial inputs due to their adaptive and plastic nature, potentially leading to catastrophic security failures that are difficult to detect through standard monitoring methods.
Hardware-level threats must also be considered, including physical tampering with neuromorphic materials or circuits. The emerging nature of these materials means that standard anti-tampering measures may not be directly applicable, necessitating novel protective approaches. Additionally, the analog nature of many neuromorphic computing elements introduces unique vulnerabilities related to signal integrity and noise susceptibility.
Architectural threats arise from the distributed processing nature of neuromorphic systems. The spike-based communication protocols commonly used in these systems create potential attack surfaces that have no direct analog in traditional computing environments. Adversaries could potentially manipulate spike timing or routing to compromise system integrity or extract protected information.
Modeling these threats requires specialized frameworks that account for the temporal dynamics and material properties unique to neuromorphic computing. Traditional threat modeling methodologies like STRIDE or PASTA must be extended to incorporate neuromorphic-specific considerations, including spike-timing dependent plasticity vulnerabilities, memristive state manipulation, and analog signal interference vectors.
Effective threat modeling for neuromorphic security systems ultimately demands cross-disciplinary expertise spanning materials science, neuroscience, and cybersecurity. As these systems move from research environments to commercial applications, developing comprehensive threat models will be essential for establishing appropriate security controls and mitigation strategies tailored to the unique characteristics of neuromorphic materials and architectures.
The primary threat vectors for neuromorphic security systems include side-channel attacks that exploit the physical characteristics of neuromorphic materials. These attacks can measure power consumption patterns, electromagnetic emissions, or timing variations to extract sensitive information from the system without directly breaching encryption protocols. The unique electrical signatures of neuromorphic materials make them particularly vulnerable to such sophisticated monitoring techniques.
Data poisoning attacks represent another significant threat category, where adversaries manipulate training data to introduce backdoors or biases into neuromorphic learning systems. Unlike conventional computing architectures, neuromorphic systems may exhibit unpredictable behavior when exposed to adversarial inputs due to their adaptive and plastic nature, potentially leading to catastrophic security failures that are difficult to detect through standard monitoring methods.
Hardware-level threats must also be considered, including physical tampering with neuromorphic materials or circuits. The emerging nature of these materials means that standard anti-tampering measures may not be directly applicable, necessitating novel protective approaches. Additionally, the analog nature of many neuromorphic computing elements introduces unique vulnerabilities related to signal integrity and noise susceptibility.
Architectural threats arise from the distributed processing nature of neuromorphic systems. The spike-based communication protocols commonly used in these systems create potential attack surfaces that have no direct analog in traditional computing environments. Adversaries could potentially manipulate spike timing or routing to compromise system integrity or extract protected information.
Modeling these threats requires specialized frameworks that account for the temporal dynamics and material properties unique to neuromorphic computing. Traditional threat modeling methodologies like STRIDE or PASTA must be extended to incorporate neuromorphic-specific considerations, including spike-timing dependent plasticity vulnerabilities, memristive state manipulation, and analog signal interference vectors.
Effective threat modeling for neuromorphic security systems ultimately demands cross-disciplinary expertise spanning materials science, neuroscience, and cybersecurity. As these systems move from research environments to commercial applications, developing comprehensive threat models will be essential for establishing appropriate security controls and mitigation strategies tailored to the unique characteristics of neuromorphic materials and architectures.
Regulatory Compliance for Neuromorphic Security Implementation
The implementation of neuromorphic materials in cybersecurity frameworks necessitates careful navigation of complex regulatory landscapes across different jurisdictions. Organizations deploying these advanced technologies must comply with established cybersecurity regulations while adapting to emerging standards specific to neuromorphic computing.
In the United States, the National Institute of Standards and Technology (NIST) has developed frameworks that, while not explicitly addressing neuromorphic security, provide foundational compliance requirements. Organizations implementing neuromorphic security solutions must demonstrate alignment with NIST SP 800-53 controls and the Cybersecurity Framework. The Federal Information Security Modernization Act (FISMA) also imposes significant compliance burdens for federal agencies considering neuromorphic security implementations.
European regulations present additional complexity, particularly through the General Data Protection Regulation (GDPR) and the Network and Information Systems (NIS) Directive. Neuromorphic security systems processing personal data must incorporate privacy-by-design principles and demonstrate robust data protection measures. The EU's proposed AI Act may further regulate neuromorphic systems based on their risk classification, potentially requiring conformity assessments before deployment.
Industry-specific regulations add another layer of compliance requirements. Financial institutions implementing neuromorphic security must adhere to standards like PCI DSS for payment card security and financial regulations such as SOX. Healthcare organizations face HIPAA compliance challenges when neuromorphic systems interact with protected health information, requiring careful implementation of technical safeguards.
Certification pathways for neuromorphic security technologies remain underdeveloped. Currently, organizations must adapt existing certification frameworks like Common Criteria (ISO/IEC 15408) or FIPS 140-3 for cryptographic modules. Industry stakeholders are advocating for specialized certification programs that address the unique characteristics of neuromorphic computing in security applications.
Regulatory gaps present significant challenges as current frameworks were not designed with neuromorphic computing in mind. The novel architecture of neuromorphic materials creates ambiguity regarding compliance requirements, particularly concerning explainability and auditability of security decisions. International standardization bodies including ISO, IEEE, and ITU are beginning to develop technical standards specifically addressing neuromorphic computing security.
Organizations implementing neuromorphic security solutions should adopt a proactive compliance strategy, engaging with regulators early in the development process and participating in regulatory sandboxes where available. Maintaining comprehensive documentation of security controls, conducting regular risk assessments, and establishing clear governance structures will be essential for demonstrating regulatory compliance as the regulatory landscape continues to evolve alongside this emerging technology.
In the United States, the National Institute of Standards and Technology (NIST) has developed frameworks that, while not explicitly addressing neuromorphic security, provide foundational compliance requirements. Organizations implementing neuromorphic security solutions must demonstrate alignment with NIST SP 800-53 controls and the Cybersecurity Framework. The Federal Information Security Modernization Act (FISMA) also imposes significant compliance burdens for federal agencies considering neuromorphic security implementations.
European regulations present additional complexity, particularly through the General Data Protection Regulation (GDPR) and the Network and Information Systems (NIS) Directive. Neuromorphic security systems processing personal data must incorporate privacy-by-design principles and demonstrate robust data protection measures. The EU's proposed AI Act may further regulate neuromorphic systems based on their risk classification, potentially requiring conformity assessments before deployment.
Industry-specific regulations add another layer of compliance requirements. Financial institutions implementing neuromorphic security must adhere to standards like PCI DSS for payment card security and financial regulations such as SOX. Healthcare organizations face HIPAA compliance challenges when neuromorphic systems interact with protected health information, requiring careful implementation of technical safeguards.
Certification pathways for neuromorphic security technologies remain underdeveloped. Currently, organizations must adapt existing certification frameworks like Common Criteria (ISO/IEC 15408) or FIPS 140-3 for cryptographic modules. Industry stakeholders are advocating for specialized certification programs that address the unique characteristics of neuromorphic computing in security applications.
Regulatory gaps present significant challenges as current frameworks were not designed with neuromorphic computing in mind. The novel architecture of neuromorphic materials creates ambiguity regarding compliance requirements, particularly concerning explainability and auditability of security decisions. International standardization bodies including ISO, IEEE, and ITU are beginning to develop technical standards specifically addressing neuromorphic computing security.
Organizations implementing neuromorphic security solutions should adopt a proactive compliance strategy, engaging with regulators early in the development process and participating in regulatory sandboxes where available. Maintaining comprehensive documentation of security controls, conducting regular risk assessments, and establishing clear governance structures will be essential for demonstrating regulatory compliance as the regulatory landscape continues to evolve alongside this emerging technology.
Unlock deeper insights with Patsnap Eureka Quick Research — get a full tech report to explore trends and direct your research. Try now!
Generate Your Research Report Instantly with AI Agent
Supercharge your innovation with Patsnap Eureka AI Agent Platform!