PoE++ Vs VPN: Data Protection in Cloud-Based Systems
SEP 24, 20259 MIN READ
Generate Your Research Report Instantly with AI Agent
Patsnap Eureka helps you evaluate technical feasibility & market potential.
PoE++ and VPN Technology Evolution
The evolution of data protection technologies in cloud-based systems has witnessed significant transformations over the past two decades. Point of Encryption (PoE++) and Virtual Private Networks (VPNs) represent two distinct approaches that have evolved along parallel yet interconnected paths to address growing security concerns in distributed computing environments.
VPN technology emerged in the late 1990s primarily as a means to create secure communication channels over public networks. The initial implementations focused on creating encrypted tunnels between fixed endpoints, with protocols like PPTP (Point-to-Point Tunneling Protocol) and L2TP (Layer 2 Tunneling Protocol) dominating the landscape. These early solutions offered basic encryption but suffered from performance limitations and security vulnerabilities.
By the mid-2000s, VPN technology experienced a significant evolution with the widespread adoption of IPsec (Internet Protocol Security) and SSL/TLS (Secure Sockets Layer/Transport Layer Security) based solutions. This marked a shift toward more flexible deployment models and stronger encryption standards, coinciding with the early growth of cloud computing platforms.
The emergence of cloud-native architectures around 2010 prompted another evolutionary leap in VPN technology. Software-defined perimeter (SDP) approaches began replacing traditional perimeter-based security models, introducing concepts like zero-trust networking that fundamentally changed how VPNs operated in cloud environments.
Concurrently, PoE technology followed its own evolutionary trajectory. Early encryption at rest solutions focused primarily on disk-level encryption, with limited integration into application workflows. The introduction of PoE concepts around 2008-2010 represented a paradigm shift toward encrypting data at its origin before transmission or storage.
PoE++ emerged around 2015 as an enhanced framework that extended encryption capabilities throughout the entire data lifecycle. This evolution was characterized by the integration of advanced cryptographic techniques, including homomorphic encryption and secure multi-party computation, enabling data to remain encrypted even during processing.
A critical inflection point occurred around 2018 when regulatory frameworks like GDPR and CCPA elevated data protection requirements, accelerating the adoption and development of both technologies. VPN solutions increasingly incorporated features like split tunneling and multi-factor authentication, while PoE++ implementations expanded to include sophisticated key management systems and hardware-based security modules.
Most recently (2020-2023), both technologies have begun converging in certain applications, with hybrid security models that leverage the strengths of each approach. Modern cloud security architectures frequently implement VPN technologies for secure network access alongside PoE++ principles for data-centric protection, creating defense-in-depth strategies that address the complex threat landscape of contemporary cloud environments.
VPN technology emerged in the late 1990s primarily as a means to create secure communication channels over public networks. The initial implementations focused on creating encrypted tunnels between fixed endpoints, with protocols like PPTP (Point-to-Point Tunneling Protocol) and L2TP (Layer 2 Tunneling Protocol) dominating the landscape. These early solutions offered basic encryption but suffered from performance limitations and security vulnerabilities.
By the mid-2000s, VPN technology experienced a significant evolution with the widespread adoption of IPsec (Internet Protocol Security) and SSL/TLS (Secure Sockets Layer/Transport Layer Security) based solutions. This marked a shift toward more flexible deployment models and stronger encryption standards, coinciding with the early growth of cloud computing platforms.
The emergence of cloud-native architectures around 2010 prompted another evolutionary leap in VPN technology. Software-defined perimeter (SDP) approaches began replacing traditional perimeter-based security models, introducing concepts like zero-trust networking that fundamentally changed how VPNs operated in cloud environments.
Concurrently, PoE technology followed its own evolutionary trajectory. Early encryption at rest solutions focused primarily on disk-level encryption, with limited integration into application workflows. The introduction of PoE concepts around 2008-2010 represented a paradigm shift toward encrypting data at its origin before transmission or storage.
PoE++ emerged around 2015 as an enhanced framework that extended encryption capabilities throughout the entire data lifecycle. This evolution was characterized by the integration of advanced cryptographic techniques, including homomorphic encryption and secure multi-party computation, enabling data to remain encrypted even during processing.
A critical inflection point occurred around 2018 when regulatory frameworks like GDPR and CCPA elevated data protection requirements, accelerating the adoption and development of both technologies. VPN solutions increasingly incorporated features like split tunneling and multi-factor authentication, while PoE++ implementations expanded to include sophisticated key management systems and hardware-based security modules.
Most recently (2020-2023), both technologies have begun converging in certain applications, with hybrid security models that leverage the strengths of each approach. Modern cloud security architectures frequently implement VPN technologies for secure network access alongside PoE++ principles for data-centric protection, creating defense-in-depth strategies that address the complex threat landscape of contemporary cloud environments.
Market Demand for Secure Cloud Data Transmission
The demand for secure cloud data transmission solutions has witnessed exponential growth in recent years, driven primarily by the increasing adoption of cloud services across industries. According to market research, the global cloud security market is projected to reach $68.5 billion by 2025, growing at a CAGR of 14.7% from 2020. This substantial growth reflects the critical importance organizations place on protecting sensitive data as it traverses between on-premises infrastructure and cloud environments.
Enterprise customers represent the largest segment demanding secure cloud data transmission technologies, with financial services, healthcare, and government sectors leading adoption. These industries handle particularly sensitive data subject to strict regulatory requirements such as GDPR, HIPAA, and PCI DSS, which mandate robust data protection measures during transmission and storage.
The COVID-19 pandemic has accelerated this market trend significantly. Remote work adoption surged from 30% pre-pandemic to over 70% during peak lockdown periods, creating unprecedented demand for secure remote access solutions. Organizations rapidly deployed cloud services to maintain business continuity, often prioritizing speed over security, which subsequently created substantial demand for retrofitting security solutions.
A key market driver is the evolving threat landscape. Data breaches have increased by 68% since 2020, with attacks specifically targeting data in transit growing even faster. The average cost of a data breach reached $4.24 million in 2021, providing strong financial incentive for organizations to invest in secure transmission technologies.
Customer requirements have evolved beyond basic encryption to demand comprehensive solutions that address multiple aspects of data protection. Modern buyers seek technologies offering end-to-end encryption, zero-trust architecture compatibility, minimal performance impact, and seamless integration with existing infrastructure. The ability to maintain security while supporting high-bandwidth applications like video conferencing and large file transfers has become particularly important.
Regional variations in demand are notable, with North America representing the largest market share at 42%, followed by Europe at 28% and Asia-Pacific showing the fastest growth rate at 16.8% annually. Regulatory environments significantly influence regional adoption patterns, with stricter data sovereignty laws in Europe driving demand for solutions that can maintain compliance across jurisdictional boundaries.
Industry analysts predict continued strong growth in this market segment, with particular emphasis on solutions that can address the security challenges of multi-cloud and hybrid cloud environments. As organizations increasingly distribute workloads across multiple providers, the complexity of securing data transmission grows exponentially, creating demand for more sophisticated protection mechanisms.
Enterprise customers represent the largest segment demanding secure cloud data transmission technologies, with financial services, healthcare, and government sectors leading adoption. These industries handle particularly sensitive data subject to strict regulatory requirements such as GDPR, HIPAA, and PCI DSS, which mandate robust data protection measures during transmission and storage.
The COVID-19 pandemic has accelerated this market trend significantly. Remote work adoption surged from 30% pre-pandemic to over 70% during peak lockdown periods, creating unprecedented demand for secure remote access solutions. Organizations rapidly deployed cloud services to maintain business continuity, often prioritizing speed over security, which subsequently created substantial demand for retrofitting security solutions.
A key market driver is the evolving threat landscape. Data breaches have increased by 68% since 2020, with attacks specifically targeting data in transit growing even faster. The average cost of a data breach reached $4.24 million in 2021, providing strong financial incentive for organizations to invest in secure transmission technologies.
Customer requirements have evolved beyond basic encryption to demand comprehensive solutions that address multiple aspects of data protection. Modern buyers seek technologies offering end-to-end encryption, zero-trust architecture compatibility, minimal performance impact, and seamless integration with existing infrastructure. The ability to maintain security while supporting high-bandwidth applications like video conferencing and large file transfers has become particularly important.
Regional variations in demand are notable, with North America representing the largest market share at 42%, followed by Europe at 28% and Asia-Pacific showing the fastest growth rate at 16.8% annually. Regulatory environments significantly influence regional adoption patterns, with stricter data sovereignty laws in Europe driving demand for solutions that can maintain compliance across jurisdictional boundaries.
Industry analysts predict continued strong growth in this market segment, with particular emphasis on solutions that can address the security challenges of multi-cloud and hybrid cloud environments. As organizations increasingly distribute workloads across multiple providers, the complexity of securing data transmission grows exponentially, creating demand for more sophisticated protection mechanisms.
Technical Challenges in Cloud Data Protection
Cloud-based systems face significant technical challenges in data protection, particularly when comparing PoE++ (Power over Ethernet Plus Plus) and VPN (Virtual Private Network) technologies. These challenges stem from the inherent complexity of cloud architectures and the evolving nature of cyber threats targeting cloud environments.
Data encryption represents a primary challenge, as cloud systems must secure data both at rest and in transit. While VPNs excel at creating encrypted tunnels for data transmission, they introduce latency issues that can impact real-time applications. PoE++ systems, primarily designed for power delivery, lack native encryption capabilities, requiring additional security layers that may increase system complexity.
Authentication mechanisms present another critical challenge. Cloud environments require robust identity verification to prevent unauthorized access. VPN solutions typically offer multi-factor authentication options but may struggle with seamless integration across diverse cloud platforms. PoE++ systems, being primarily hardware-focused, often have limited authentication capabilities, necessitating supplementary security measures.
Network segmentation and access control pose significant technical hurdles. VPNs can create secure network segments but may introduce configuration complexities when implemented across hybrid cloud environments. PoE++ networks, while efficient for powering devices, lack inherent segmentation capabilities, potentially exposing connected devices to broader network vulnerabilities.
Scalability challenges emerge as cloud deployments grow. VPN solutions often face performance degradation with increased user loads, requiring complex load-balancing configurations. PoE++ systems encounter power delivery limitations when scaling, potentially restricting the deployment of security monitoring devices in larger networks.
Compliance and regulatory requirements add another layer of technical complexity. Different jurisdictions impose varying data protection standards, requiring cloud systems to implement adaptable security measures. VPNs must support diverse encryption standards to meet global compliance requirements, while PoE++ implementations must ensure power delivery doesn't compromise security monitoring capabilities.
Incident response capabilities present ongoing challenges. Cloud-based systems require real-time threat detection and mitigation. VPN solutions may introduce visibility gaps that complicate security monitoring, while PoE++ systems must ensure continuous power to security infrastructure during incidents, often requiring redundant power paths.
Legacy system integration remains problematic for both technologies. Many organizations maintain hybrid environments with legacy components that may not support modern VPN protocols or PoE++ power requirements, necessitating complex adaptation layers that can introduce security vulnerabilities.
Data encryption represents a primary challenge, as cloud systems must secure data both at rest and in transit. While VPNs excel at creating encrypted tunnels for data transmission, they introduce latency issues that can impact real-time applications. PoE++ systems, primarily designed for power delivery, lack native encryption capabilities, requiring additional security layers that may increase system complexity.
Authentication mechanisms present another critical challenge. Cloud environments require robust identity verification to prevent unauthorized access. VPN solutions typically offer multi-factor authentication options but may struggle with seamless integration across diverse cloud platforms. PoE++ systems, being primarily hardware-focused, often have limited authentication capabilities, necessitating supplementary security measures.
Network segmentation and access control pose significant technical hurdles. VPNs can create secure network segments but may introduce configuration complexities when implemented across hybrid cloud environments. PoE++ networks, while efficient for powering devices, lack inherent segmentation capabilities, potentially exposing connected devices to broader network vulnerabilities.
Scalability challenges emerge as cloud deployments grow. VPN solutions often face performance degradation with increased user loads, requiring complex load-balancing configurations. PoE++ systems encounter power delivery limitations when scaling, potentially restricting the deployment of security monitoring devices in larger networks.
Compliance and regulatory requirements add another layer of technical complexity. Different jurisdictions impose varying data protection standards, requiring cloud systems to implement adaptable security measures. VPNs must support diverse encryption standards to meet global compliance requirements, while PoE++ implementations must ensure power delivery doesn't compromise security monitoring capabilities.
Incident response capabilities present ongoing challenges. Cloud-based systems require real-time threat detection and mitigation. VPN solutions may introduce visibility gaps that complicate security monitoring, while PoE++ systems must ensure continuous power to security infrastructure during incidents, often requiring redundant power paths.
Legacy system integration remains problematic for both technologies. Many organizations maintain hybrid environments with legacy components that may not support modern VPN protocols or PoE++ power requirements, necessitating complex adaptation layers that can introduce security vulnerabilities.
Current Data Protection Implementation Methods
01 PoE++ Power Management for VPN Security Devices
Power over Ethernet Plus Plus (PoE++) technology enables the delivery of higher power levels to network devices while supporting VPN security functions. These systems integrate power management capabilities with data protection mechanisms, allowing for secure remote access while efficiently powering network infrastructure. The implementation includes power controllers that can prioritize critical security functions during power constraints, ensuring continuous VPN operation for data protection.- PoE++ Power Management for VPN Security Devices: Power over Ethernet Plus Plus (PoE++) technology enables the delivery of higher power levels to network devices while supporting VPN security functions. These systems integrate power management with data protection mechanisms, allowing secure VPN gateways and encryption devices to operate efficiently with reduced infrastructure requirements. The implementation includes power monitoring circuits and intelligent power allocation to ensure stable operation of security components while maintaining data protection integrity.
- Secure VPN Tunneling with Enhanced Data Protection: Advanced VPN tunneling technologies incorporate multiple encryption layers and authentication mechanisms to protect data transmitted over public networks. These solutions implement secure key exchange protocols, traffic analysis prevention, and packet inspection capabilities to ensure confidentiality and integrity of sensitive information. The technologies include split tunneling configurations, multi-factor authentication integration, and dynamic security policy enforcement to adapt to changing threat landscapes while maintaining optimal performance.
- Network Architecture for PoE++ and VPN Integration: Specialized network architectures combine PoE++ power delivery with VPN security infrastructure to create robust data protection environments. These designs incorporate segmented network zones, dedicated power management controllers, and security policy enforcement points. The integration allows for centralized management of both power resources and security protocols, enabling efficient deployment of secure communication endpoints while ensuring continuous operation during power fluctuations or security events.
- Remote Access Security with PoE++ Powered Devices: Remote access solutions utilizing PoE++ powered security appliances provide enhanced data protection for distributed networks. These systems implement secure authentication protocols, encrypted communication channels, and access control mechanisms specifically designed for power-constrained environments. The technology enables deployment of security gateways in remote locations with limited infrastructure while maintaining enterprise-grade data protection capabilities through optimized power consumption and security processing.
- Monitoring and Management Systems for Secure PoE++ VPN Networks: Comprehensive monitoring and management systems for PoE++ powered VPN networks provide real-time visibility into both power consumption and security status. These solutions incorporate analytics for detecting power anomalies that might indicate security breaches, centralized configuration management for security policies, and automated responses to potential threats. The integration of power and security monitoring enables more effective threat detection while ensuring optimal resource allocation for critical security functions.
02 Secure VPN Gateway Architecture with Enhanced Data Protection
Advanced VPN gateway architectures incorporate multiple security layers to protect data transmission across networks. These systems implement encryption protocols, authentication mechanisms, and traffic monitoring to prevent unauthorized access and data breaches. The architecture includes dedicated hardware components that process encrypted traffic efficiently while maintaining separation between secure and non-secure network zones, enhancing overall data protection capabilities.Expand Specific Solutions03 Network Traffic Management for PoE-Powered VPN Systems
Systems that combine PoE++ power delivery with VPN technologies implement specialized traffic management capabilities to optimize both power and data security. These solutions prioritize critical VPN traffic while managing power allocation to connected devices, ensuring reliable operation during peak demand periods. The traffic management systems include quality of service mechanisms that maintain VPN connection stability and data protection while balancing power requirements across the network infrastructure.Expand Specific Solutions04 Remote Access Control Systems with Integrated Power and Security Management
Integrated solutions that combine remote access control with power management capabilities provide enhanced data protection for distributed networks. These systems implement role-based access controls that work in conjunction with power delivery mechanisms to ensure that only authorized devices receive both network connectivity and power. The solutions include monitoring capabilities that detect anomalous power consumption patterns that might indicate security breaches, adding an additional layer of data protection.Expand Specific Solutions05 Edge Computing Security for PoE-Powered VPN Networks
Edge computing implementations that leverage PoE++ technology for power delivery incorporate specialized security mechanisms for VPN connections at network boundaries. These systems process security functions locally at edge devices, reducing latency while maintaining data protection standards. The architecture includes distributed security processing capabilities that work in conjunction with centralized VPN management, creating multiple layers of protection for sensitive data while efficiently utilizing available power resources.Expand Specific Solutions
Key Industry Players in Network Security
The PoE++ vs VPN data protection landscape is evolving rapidly, currently in a growth phase with increasing market adoption as organizations prioritize cloud security. The market is expanding significantly due to remote work trends and growing cyber threats, with projections indicating substantial growth through 2027. Technologically, solutions are maturing with industry leaders like Cisco, Huawei, and Palo Alto Networks driving innovation in VPN technologies, while Avaya and VMware advance PoE++ implementations. Cisco maintains market leadership in both domains, with Huawei and Juniper Networks gaining market share through enhanced security features. The competitive landscape is characterized by rapid innovation cycles as vendors integrate zero-trust principles and AI-powered threat detection into their offerings.
Huawei Technologies Co., Ltd.
Technical Solution: Huawei's solution for data protection in cloud-based systems leverages both PoE++ and VPN technologies through their "Intelligent Cloud-Network" architecture. Their PoE++ implementation supports IEEE 802.3bt standard delivering up to 90W of power while incorporating AI-driven power management that dynamically allocates power based on device needs and security priorities. This is integrated with their CloudEngine series switches that feature built-in security mechanisms to prevent unauthorized power access. For VPN protection, Huawei offers their CloudVPN solution that utilizes Software-Defined Perimeter (SDP) principles to create "zero trust" network access. Their VPN technology employs quantum-resistant encryption algorithms and incorporates AI-based threat detection that can identify anomalous traffic patterns in encrypted tunnels without decrypting the content. Huawei's unified management platform, CloudCampus, allows administrators to orchestrate both PoE++ and VPN security policies from a single interface, enabling consistent security enforcement across hybrid cloud environments.
Strengths: Huawei's solution offers superior power efficiency with AI-driven power allocation, reducing energy consumption while maintaining security. Their integrated management platform simplifies administration of complex security policies. Weaknesses: Geopolitical concerns may limit adoption in certain markets. The solution's deep integration with Huawei's ecosystem may create interoperability challenges with third-party security tools.
Cisco Technology, Inc.
Technical Solution: Cisco's approach to data protection in cloud-based systems involves a comprehensive security architecture that integrates both PoE++ and VPN technologies. For PoE++ (Power over Ethernet), Cisco has developed the Universal Power over Ethernet (UPOE+) which delivers up to 90W per port, enabling secure power delivery to network devices while maintaining data integrity. This technology supports their Software-Defined Access (SDA) framework, which creates micro-segmentation within networks to contain potential breaches. On the VPN front, Cisco's AnyConnect Secure Mobility Client provides end-to-end encryption for remote access, while their Next-Generation Encryption (NGE) algorithms ensure data confidentiality with minimal performance impact. Their Secure Access Service Edge (SASE) framework combines cloud-native security functions with WAN capabilities to provide secure access regardless of user location. Cisco's integrated approach allows organizations to implement defense-in-depth strategies where PoE++ secures the physical layer while VPN technologies protect data in transit.
Strengths: Cisco's integrated ecosystem allows seamless implementation of both technologies within existing infrastructure. Their SASE framework provides comprehensive security with centralized policy management. Weaknesses: The solution requires significant investment in Cisco's ecosystem, creating potential vendor lock-in. Implementation complexity may require specialized expertise, increasing operational costs.
Core Security Technologies Analysis
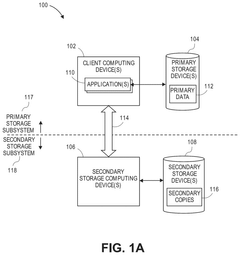
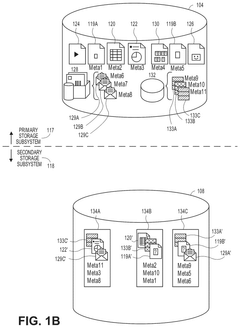
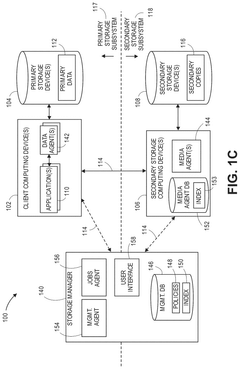
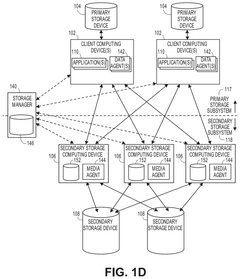
Data protection component scaling in a cloud- based data storage system
PatentActiveUS12199952B2
Innovation
- The system dynamically adds and removes proxy data protection agents in a cloud data storage system to process data protection jobs on an on-demand basis, efficiently scaling virtual machines to minimize costs and resource usage by powering down decommissioned agents and machines.
Power over ethernet computer system
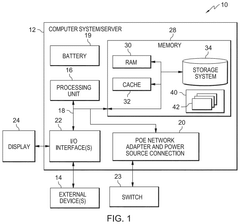
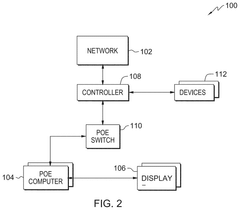
PatentPendingUS20250023748A1
Innovation
- A Power over Ethernet (PoE) computer system that integrates a processing unit, memory, and network adapter, allowing for both data and power to be received through a single Ethernet connection, with optional battery backup and power management to ensure adequate power delivery to components.
Compliance and Regulatory Framework
The regulatory landscape governing data protection in cloud environments has evolved significantly in recent years, creating a complex framework that organizations must navigate when implementing security solutions like PoE++ or VPNs. The General Data Protection Regulation (GDPR) in Europe stands as one of the most comprehensive regulatory frameworks, mandating strict data protection measures including encryption, access controls, and breach notification protocols. Organizations deploying either PoE++ or VPN solutions must ensure these technologies align with GDPR's principles of data minimization and privacy by design.
In the United States, a patchwork of regulations exists, including the California Consumer Privacy Act (CCPA) and sector-specific legislation like HIPAA for healthcare and GLBA for financial services. These regulations impose varying requirements for data encryption, transmission security, and access controls that directly impact the implementation of cloud security technologies. The Health Insurance Portability and Accountability Act (HIPAA) specifically requires robust encryption for protected health information, making the security capabilities of both PoE++ and VPN solutions critical considerations for healthcare organizations.
Industry-specific compliance frameworks further complicate the regulatory landscape. The Payment Card Industry Data Security Standard (PCI DSS) mandates specific security controls for organizations handling payment card data, including requirements for network segmentation and encryption that influence technology selection between PoE++ and VPN approaches. Similarly, ISO 27001 certification demands comprehensive information security management systems that must account for the specific security properties of chosen data protection technologies.
Cross-border data transfer regulations present additional challenges when implementing cloud security solutions. The invalidation of the EU-US Privacy Shield and subsequent development of the Trans-Atlantic Data Privacy Framework have created uncertainty regarding compliant mechanisms for international data flows. Organizations must evaluate how PoE++ and VPN technologies address these requirements, particularly regarding data localization and transfer restrictions.
Regulatory compliance also extends to technical implementation standards. NIST Special Publications provide detailed guidance on encryption standards and key management practices that directly impact the security efficacy of both PoE++ and VPN solutions. Similarly, the Cloud Security Alliance's Cloud Controls Matrix offers a framework for assessing cloud security controls against various regulatory requirements, providing a valuable benchmark for evaluating the compliance capabilities of different data protection approaches.
The evolving nature of these regulations necessitates forward-looking compliance strategies. Emerging regulations like the EU's NIS2 Directive and various proposed federal privacy laws in the United States will likely impose additional requirements on cloud security implementations, potentially influencing the long-term viability of different technical approaches to data protection in cloud environments.
In the United States, a patchwork of regulations exists, including the California Consumer Privacy Act (CCPA) and sector-specific legislation like HIPAA for healthcare and GLBA for financial services. These regulations impose varying requirements for data encryption, transmission security, and access controls that directly impact the implementation of cloud security technologies. The Health Insurance Portability and Accountability Act (HIPAA) specifically requires robust encryption for protected health information, making the security capabilities of both PoE++ and VPN solutions critical considerations for healthcare organizations.
Industry-specific compliance frameworks further complicate the regulatory landscape. The Payment Card Industry Data Security Standard (PCI DSS) mandates specific security controls for organizations handling payment card data, including requirements for network segmentation and encryption that influence technology selection between PoE++ and VPN approaches. Similarly, ISO 27001 certification demands comprehensive information security management systems that must account for the specific security properties of chosen data protection technologies.
Cross-border data transfer regulations present additional challenges when implementing cloud security solutions. The invalidation of the EU-US Privacy Shield and subsequent development of the Trans-Atlantic Data Privacy Framework have created uncertainty regarding compliant mechanisms for international data flows. Organizations must evaluate how PoE++ and VPN technologies address these requirements, particularly regarding data localization and transfer restrictions.
Regulatory compliance also extends to technical implementation standards. NIST Special Publications provide detailed guidance on encryption standards and key management practices that directly impact the security efficacy of both PoE++ and VPN solutions. Similarly, the Cloud Security Alliance's Cloud Controls Matrix offers a framework for assessing cloud security controls against various regulatory requirements, providing a valuable benchmark for evaluating the compliance capabilities of different data protection approaches.
The evolving nature of these regulations necessitates forward-looking compliance strategies. Emerging regulations like the EU's NIS2 Directive and various proposed federal privacy laws in the United States will likely impose additional requirements on cloud security implementations, potentially influencing the long-term viability of different technical approaches to data protection in cloud environments.
Energy Efficiency vs Security Trade-offs
The trade-off between energy efficiency and security represents a critical consideration in the PoE++ versus VPN debate for cloud-based data protection systems. Power over Ethernet Plus Plus (PoE++) technology offers significant energy advantages through its consolidated power and data transmission capabilities, reducing the need for separate power infrastructure and potentially lowering overall energy consumption by 15-30% compared to traditional network setups.
However, this energy efficiency comes with security implications. PoE++ systems typically operate on a more simplified network architecture that may offer fewer security layers than dedicated VPN solutions. The consolidated nature of power and data transmission creates potential single points of failure that could be exploited by sophisticated threat actors.
VPN solutions, while providing robust encryption and secure tunneling capabilities, demand considerably higher computational resources. Enterprise-grade VPN implementations can increase system energy consumption by 20-45% due to the intensive cryptographic operations required for maintaining secure connections. This energy overhead becomes particularly significant in large-scale cloud deployments where thousands of simultaneous connections must be maintained.
The security-energy balance varies significantly across different deployment scenarios. Edge computing applications may benefit more from PoE++ solutions where physical security can supplement network security while minimizing energy footprint. Conversely, highly sensitive cloud environments handling regulated data may justify the energy premium of comprehensive VPN implementations despite their higher power demands.
Recent innovations are beginning to address this dichotomy. Adaptive security protocols that dynamically adjust encryption levels based on threat assessment and data sensitivity show promise in optimizing the security-energy balance. Similarly, hardware-accelerated encryption technologies are reducing the energy penalty associated with VPN implementations by 30-40% compared to software-only solutions.
Organizations must consider their specific security requirements, compliance obligations, and sustainability goals when evaluating these technologies. The optimal approach increasingly involves hybrid architectures that leverage PoE++ for appropriate network segments while implementing targeted VPN protection for sensitive data pathways, thereby achieving a balanced compromise between energy efficiency and security requirements.
However, this energy efficiency comes with security implications. PoE++ systems typically operate on a more simplified network architecture that may offer fewer security layers than dedicated VPN solutions. The consolidated nature of power and data transmission creates potential single points of failure that could be exploited by sophisticated threat actors.
VPN solutions, while providing robust encryption and secure tunneling capabilities, demand considerably higher computational resources. Enterprise-grade VPN implementations can increase system energy consumption by 20-45% due to the intensive cryptographic operations required for maintaining secure connections. This energy overhead becomes particularly significant in large-scale cloud deployments where thousands of simultaneous connections must be maintained.
The security-energy balance varies significantly across different deployment scenarios. Edge computing applications may benefit more from PoE++ solutions where physical security can supplement network security while minimizing energy footprint. Conversely, highly sensitive cloud environments handling regulated data may justify the energy premium of comprehensive VPN implementations despite their higher power demands.
Recent innovations are beginning to address this dichotomy. Adaptive security protocols that dynamically adjust encryption levels based on threat assessment and data sensitivity show promise in optimizing the security-energy balance. Similarly, hardware-accelerated encryption technologies are reducing the energy penalty associated with VPN implementations by 30-40% compared to software-only solutions.
Organizations must consider their specific security requirements, compliance obligations, and sustainability goals when evaluating these technologies. The optimal approach increasingly involves hybrid architectures that leverage PoE++ for appropriate network segments while implementing targeted VPN protection for sensitive data pathways, thereby achieving a balanced compromise between energy efficiency and security requirements.
Unlock deeper insights with Patsnap Eureka Quick Research — get a full tech report to explore trends and direct your research. Try now!
Generate Your Research Report Instantly with AI Agent
Supercharge your innovation with Patsnap Eureka AI Agent Platform!