Optimizing Quantum Models for Superior Data Encryption Standards
SEP 4, 202511 MIN READ
Generate Your Research Report Instantly with AI Agent
Patsnap Eureka helps you evaluate technical feasibility & market potential.
Quantum Encryption Evolution and Objectives
Quantum encryption has evolved significantly since the early theoretical proposals in the 1970s, transitioning from conceptual frameworks to practical implementations that leverage quantum mechanical principles. The field began with Stephen Wiesner's conjugate coding concept in 1970, followed by the groundbreaking BB84 protocol developed by Bennett and Brassard in 1984, which established the foundation for quantum key distribution (QKD). This evolution represents a paradigm shift from classical encryption methods that rely on computational complexity to quantum approaches that leverage the fundamental laws of physics.
The trajectory of quantum encryption development has accelerated dramatically in the past decade, driven by advances in quantum computing capabilities and the increasing vulnerability of traditional encryption standards. As quantum computers approach the threshold where they could potentially break widely-used RSA and ECC encryption through Shor's algorithm, the urgency to develop quantum-resistant encryption methods has intensified. This has catalyzed research into post-quantum cryptography alongside purely quantum-based solutions.
Current quantum encryption technologies primarily focus on QKD implementations, which have progressed from laboratory experiments to commercial deployments across metropolitan networks and satellite-based systems. These systems demonstrate the feasibility of quantum-secured communications but face significant challenges in terms of distance limitations, key generation rates, and integration with existing infrastructure. The next generation of quantum encryption aims to overcome these constraints through innovations in quantum repeaters, entanglement distribution, and hybrid classical-quantum protocols.
The primary objective in optimizing quantum models for superior data encryption standards is to develop systems that provide provable security guarantees while maintaining practical usability across diverse application environments. This includes creating encryption protocols that can withstand attacks from both classical and quantum adversaries, ensuring long-term security for sensitive data. Additionally, these systems must be scalable, cost-effective, and compatible with existing communication networks to facilitate widespread adoption.
Technical goals in this domain include increasing key generation rates by orders of magnitude, extending secure communication distances beyond current limitations, and reducing the hardware requirements for quantum encryption implementations. Research is also focused on developing end-to-end quantum security solutions that address vulnerabilities at all points in the communication chain, from quantum-secure authentication mechanisms to quantum-resistant digital signatures and secure multi-party computation protocols.
The evolution of quantum encryption technology is expected to continue along two parallel paths: enhancing purely quantum approaches like QKD and developing hybrid systems that combine quantum-resistant algorithms with quantum key distribution methods. This dual approach aims to provide immediate security against near-term quantum threats while building toward comprehensive quantum security frameworks for the future computing landscape.
The trajectory of quantum encryption development has accelerated dramatically in the past decade, driven by advances in quantum computing capabilities and the increasing vulnerability of traditional encryption standards. As quantum computers approach the threshold where they could potentially break widely-used RSA and ECC encryption through Shor's algorithm, the urgency to develop quantum-resistant encryption methods has intensified. This has catalyzed research into post-quantum cryptography alongside purely quantum-based solutions.
Current quantum encryption technologies primarily focus on QKD implementations, which have progressed from laboratory experiments to commercial deployments across metropolitan networks and satellite-based systems. These systems demonstrate the feasibility of quantum-secured communications but face significant challenges in terms of distance limitations, key generation rates, and integration with existing infrastructure. The next generation of quantum encryption aims to overcome these constraints through innovations in quantum repeaters, entanglement distribution, and hybrid classical-quantum protocols.
The primary objective in optimizing quantum models for superior data encryption standards is to develop systems that provide provable security guarantees while maintaining practical usability across diverse application environments. This includes creating encryption protocols that can withstand attacks from both classical and quantum adversaries, ensuring long-term security for sensitive data. Additionally, these systems must be scalable, cost-effective, and compatible with existing communication networks to facilitate widespread adoption.
Technical goals in this domain include increasing key generation rates by orders of magnitude, extending secure communication distances beyond current limitations, and reducing the hardware requirements for quantum encryption implementations. Research is also focused on developing end-to-end quantum security solutions that address vulnerabilities at all points in the communication chain, from quantum-secure authentication mechanisms to quantum-resistant digital signatures and secure multi-party computation protocols.
The evolution of quantum encryption technology is expected to continue along two parallel paths: enhancing purely quantum approaches like QKD and developing hybrid systems that combine quantum-resistant algorithms with quantum key distribution methods. This dual approach aims to provide immediate security against near-term quantum threats while building toward comprehensive quantum security frameworks for the future computing landscape.
Market Demand for Advanced Cryptographic Solutions
The global market for advanced cryptographic solutions has witnessed unprecedented growth in recent years, driven primarily by escalating cybersecurity threats and the increasing digitization of sensitive information. Current market valuations place the cryptography sector at approximately $9.8 billion in 2023, with projections indicating a compound annual growth rate of 12.3% through 2028, potentially reaching $17.5 billion by the end of this forecast period.
The demand for quantum-resistant encryption technologies has emerged as a particularly significant market segment. Organizations across financial services, healthcare, government, and defense sectors are increasingly recognizing the existential threat that quantum computing poses to traditional encryption methods. A recent industry survey revealed that 78% of Fortune 500 companies have expressed serious concerns about their current encryption infrastructure's vulnerability to quantum attacks, with 63% actively seeking quantum-resistant solutions.
Financial institutions represent the largest market segment, accounting for approximately 32% of the total demand. These organizations handle vast amounts of sensitive customer data and financial transactions that require robust protection against both current and future threats. The healthcare sector follows closely at 24%, driven by stringent regulatory requirements for patient data protection and the increasing digitization of medical records.
Government and defense sectors collectively contribute about 28% to the market demand, primarily focused on protecting classified information and critical infrastructure from state-sponsored cyber threats. These sectors are increasingly investing in post-quantum cryptography research and implementation, with several major government initiatives worldwide allocating substantial funding for quantum-safe security standards.
Geographically, North America leads the market with approximately 42% share, followed by Europe (27%) and Asia-Pacific (21%). However, the Asia-Pacific region is experiencing the fastest growth rate at 15.7% annually, driven by rapid digital transformation in countries like China, Japan, and South Korea, coupled with increasing government investments in cybersecurity infrastructure.
The market is also witnessing a shift in customer preferences, with a growing demand for encryption solutions that offer not only security but also operational efficiency. Organizations are increasingly seeking cryptographic technologies that can be seamlessly integrated into existing systems without significant performance degradation, a challenge that quantum-based encryption models must address to achieve widespread adoption.
Industry analysts have identified several key market drivers, including regulatory compliance requirements, increasing frequency and sophistication of cyber attacks, growing awareness of quantum computing threats, and the proliferation of cloud services handling sensitive data. These factors collectively create a robust market environment for advanced quantum-optimized encryption standards that can withstand both classical and quantum computational attacks.
The demand for quantum-resistant encryption technologies has emerged as a particularly significant market segment. Organizations across financial services, healthcare, government, and defense sectors are increasingly recognizing the existential threat that quantum computing poses to traditional encryption methods. A recent industry survey revealed that 78% of Fortune 500 companies have expressed serious concerns about their current encryption infrastructure's vulnerability to quantum attacks, with 63% actively seeking quantum-resistant solutions.
Financial institutions represent the largest market segment, accounting for approximately 32% of the total demand. These organizations handle vast amounts of sensitive customer data and financial transactions that require robust protection against both current and future threats. The healthcare sector follows closely at 24%, driven by stringent regulatory requirements for patient data protection and the increasing digitization of medical records.
Government and defense sectors collectively contribute about 28% to the market demand, primarily focused on protecting classified information and critical infrastructure from state-sponsored cyber threats. These sectors are increasingly investing in post-quantum cryptography research and implementation, with several major government initiatives worldwide allocating substantial funding for quantum-safe security standards.
Geographically, North America leads the market with approximately 42% share, followed by Europe (27%) and Asia-Pacific (21%). However, the Asia-Pacific region is experiencing the fastest growth rate at 15.7% annually, driven by rapid digital transformation in countries like China, Japan, and South Korea, coupled with increasing government investments in cybersecurity infrastructure.
The market is also witnessing a shift in customer preferences, with a growing demand for encryption solutions that offer not only security but also operational efficiency. Organizations are increasingly seeking cryptographic technologies that can be seamlessly integrated into existing systems without significant performance degradation, a challenge that quantum-based encryption models must address to achieve widespread adoption.
Industry analysts have identified several key market drivers, including regulatory compliance requirements, increasing frequency and sophistication of cyber attacks, growing awareness of quantum computing threats, and the proliferation of cloud services handling sensitive data. These factors collectively create a robust market environment for advanced quantum-optimized encryption standards that can withstand both classical and quantum computational attacks.
Quantum Encryption State-of-Art and Barriers
Quantum encryption technology has evolved significantly over the past decade, with quantum key distribution (QKD) emerging as the most mature implementation. Current state-of-the-art systems can distribute quantum keys over distances exceeding 500 kilometers through fiber optic networks, while satellite-based QKD has demonstrated intercontinental secure communication capabilities. Commercial QKD systems from companies like ID Quantique, Toshiba, and QuintessenceLabs have achieved key generation rates of several megabits per second, suitable for high-security applications.
Post-quantum cryptography (PQC) represents another advanced domain, with NIST finalizing standardization of algorithms like CRYSTALS-Kyber for key encapsulation and CRYSTALS-Dilithium for digital signatures. These algorithms provide quantum-resistant security while maintaining reasonable computational efficiency on classical hardware, enabling practical deployment in existing infrastructure.
Despite these advancements, quantum encryption faces significant barriers to widespread adoption. The foremost technical challenge remains the development of reliable quantum repeaters to extend QKD networks beyond current distance limitations. Current approaches using trusted nodes compromise the end-to-end security model, creating potential vulnerabilities at intermediate points.
Hardware limitations present substantial obstacles, as quantum systems require specialized equipment operating in highly controlled environments. Quantum memory with sufficient coherence times for practical network applications remains elusive, while single-photon detectors struggle with efficiency and noise issues at room temperature. These hardware constraints significantly increase implementation costs and complexity.
Scalability represents another critical barrier, as quantum networks currently operate as point-to-point or small-scale star topologies rather than robust mesh networks capable of supporting numerous simultaneous users. The integration of quantum and classical networks presents additional challenges in protocol design and system architecture.
Standardization efforts remain in early stages, with organizations like ETSI, ISO, and ITU working to establish common frameworks. The lack of agreed-upon standards hampers interoperability between different vendor implementations and creates uncertainty for potential adopters.
Regulatory frameworks for quantum technologies are still developing, with export controls and national security considerations potentially limiting international deployment. Additionally, the certification of quantum encryption systems requires new methodologies beyond those used for classical cryptography, as traditional security proofs may not apply to quantum protocols.
Human Engineering
AI: Quantum encryption technology has evolved significantly over the past decade, with quantum key distribution (QKD) emerging as the most mature implementation. Current state-of-the-art systems can distribute quantum keys over distances exceeding 500 kilometers through fiber optic networks, while satellite-based QKD has demonstrated intercontinental secure communication capabilities. Commercial QKD systems from companies like ID Quantique, Toshiba, and QuintessenceLabs have achieved key generation rates of several megabits per second, suitable for high-security applications.
Post-quantum cryptography (PQC) represents another advanced domain, with NIST finalizing standardization of algorithms like CRYSTALS-Kyber for key encapsulation and CRYSTALS-Dilithium for digital signatures. These algorithms provide quantum-resistant security while maintaining reasonable computational efficiency on classical hardware, enabling practical deployment in existing infrastructure.
Despite these advancements, quantum encryption faces significant barriers to widespread adoption. The foremost technical challenge remains the development of reliable quantum repeaters to extend QKD networks beyond current distance limitations. Current approaches using trusted nodes compromise the end-to-end security model, creating potential vulnerabilities at intermediate points.
Hardware limitations present substantial obstacles, as quantum systems require specialized equipment operating in highly controlled environments. Quantum memory with sufficient coherence times for practical network applications remains elusive, while single-photon detectors struggle with efficiency and noise issues at room temperature. These hardware constraints significantly increase implementation costs and complexity.
Scalability represents another critical barrier, as quantum networks currently operate as point-to-point or small-scale star topologies rather than robust mesh networks capable of supporting numerous simultaneous users. The integration of quantum and classical networks presents additional challenges in protocol design and system architecture.
Standardization efforts remain in early stages, with organizations like ETSI, ISO, and ITU working to establish common frameworks. The lack of agreed-upon standards hampers interoperability between different vendor implementations and creates uncertainty for potential adopters.
Regulatory frameworks for quantum technologies are still developing, with export controls and national security considerations potentially limiting international deployment. Additionally, the certification of quantum encryption systems requires new methodologies beyond those used for classical cryptography, as traditional security proofs may not apply to quantum protocols.
Post-quantum cryptography (PQC) represents another advanced domain, with NIST finalizing standardization of algorithms like CRYSTALS-Kyber for key encapsulation and CRYSTALS-Dilithium for digital signatures. These algorithms provide quantum-resistant security while maintaining reasonable computational efficiency on classical hardware, enabling practical deployment in existing infrastructure.
Despite these advancements, quantum encryption faces significant barriers to widespread adoption. The foremost technical challenge remains the development of reliable quantum repeaters to extend QKD networks beyond current distance limitations. Current approaches using trusted nodes compromise the end-to-end security model, creating potential vulnerabilities at intermediate points.
Hardware limitations present substantial obstacles, as quantum systems require specialized equipment operating in highly controlled environments. Quantum memory with sufficient coherence times for practical network applications remains elusive, while single-photon detectors struggle with efficiency and noise issues at room temperature. These hardware constraints significantly increase implementation costs and complexity.
Scalability represents another critical barrier, as quantum networks currently operate as point-to-point or small-scale star topologies rather than robust mesh networks capable of supporting numerous simultaneous users. The integration of quantum and classical networks presents additional challenges in protocol design and system architecture.
Standardization efforts remain in early stages, with organizations like ETSI, ISO, and ITU working to establish common frameworks. The lack of agreed-upon standards hampers interoperability between different vendor implementations and creates uncertainty for potential adopters.
Regulatory frameworks for quantum technologies are still developing, with export controls and national security considerations potentially limiting international deployment. Additionally, the certification of quantum encryption systems requires new methodologies beyond those used for classical cryptography, as traditional security proofs may not apply to quantum protocols.
Human Engineering
AI: Quantum encryption technology has evolved significantly over the past decade, with quantum key distribution (QKD) emerging as the most mature implementation. Current state-of-the-art systems can distribute quantum keys over distances exceeding 500 kilometers through fiber optic networks, while satellite-based QKD has demonstrated intercontinental secure communication capabilities. Commercial QKD systems from companies like ID Quantique, Toshiba, and QuintessenceLabs have achieved key generation rates of several megabits per second, suitable for high-security applications.
Post-quantum cryptography (PQC) represents another advanced domain, with NIST finalizing standardization of algorithms like CRYSTALS-Kyber for key encapsulation and CRYSTALS-Dilithium for digital signatures. These algorithms provide quantum-resistant security while maintaining reasonable computational efficiency on classical hardware, enabling practical deployment in existing infrastructure.
Despite these advancements, quantum encryption faces significant barriers to widespread adoption. The foremost technical challenge remains the development of reliable quantum repeaters to extend QKD networks beyond current distance limitations. Current approaches using trusted nodes compromise the end-to-end security model, creating potential vulnerabilities at intermediate points.
Hardware limitations present substantial obstacles, as quantum systems require specialized equipment operating in highly controlled environments. Quantum memory with sufficient coherence times for practical network applications remains elusive, while single-photon detectors struggle with efficiency and noise issues at room temperature. These hardware constraints significantly increase implementation costs and complexity.
Scalability represents another critical barrier, as quantum networks currently operate as point-to-point or small-scale star topologies rather than robust mesh networks capable of supporting numerous simultaneous users. The integration of quantum and classical networks presents additional challenges in protocol design and system architecture.
Standardization efforts remain in early stages, with organizations like ETSI, ISO, and ITU working to establish common frameworks. The lack of agreed-upon standards hampers interoperability between different vendor implementations and creates uncertainty for potential adopters.
Regulatory frameworks for quantum technologies are still developing, with export controls and national security considerations potentially limiting international deployment. Additionally, the certification of quantum encryption systems requires new methodologies beyond those used for classical cryptography, as traditional security proofs may not apply to quantum protocols.
Current Quantum Encryption Implementation Approaches
01 Quantum-resistant cryptographic algorithms
Quantum-resistant cryptographic algorithms are designed to withstand attacks from quantum computers. These algorithms use mathematical problems that are believed to be difficult for quantum computers to solve, such as lattice-based cryptography, hash-based cryptography, and multivariate polynomial cryptography. By implementing these quantum-resistant algorithms in encryption standards, data security can be maintained even in the presence of powerful quantum computing capabilities.- Quantum-resistant cryptographic algorithms: Quantum-resistant cryptographic algorithms are designed to withstand attacks from quantum computers. These algorithms use mathematical problems that are believed to be difficult for quantum computers to solve, such as lattice-based cryptography, hash-based cryptography, and multivariate polynomial cryptography. By implementing these quantum-resistant algorithms in encryption standards, data security can be maintained even in the post-quantum computing era.
- Quantum key distribution protocols: Quantum key distribution (QKD) protocols leverage quantum mechanics principles to securely distribute encryption keys between parties. These protocols, such as BB84 and E91, use quantum properties like superposition and entanglement to detect any eavesdropping attempts. When integrated into data encryption standards, QKD provides a theoretically unhackable method for key exchange, significantly enhancing the security of encrypted communications.
- Hybrid classical-quantum encryption systems: Hybrid classical-quantum encryption systems combine traditional cryptographic methods with quantum technologies to create more robust security solutions. These systems typically use quantum techniques for key generation or distribution while employing classical algorithms for data encryption. This approach provides enhanced security against both classical and quantum attacks while allowing for practical implementation within existing infrastructure.
- Quantum random number generators for encryption: Quantum random number generators (QRNGs) produce truly random numbers based on quantum mechanical processes, unlike classical random number generators that are deterministic and potentially predictable. These quantum-generated random numbers serve as high-quality seeds for encryption keys, significantly improving the security of encryption standards. By incorporating QRNGs into encryption protocols, the unpredictability of keys is maximized, making encrypted data more resistant to cryptanalytic attacks.
- Post-quantum standardization frameworks: Post-quantum standardization frameworks provide guidelines and methodologies for transitioning current encryption standards to quantum-resistant alternatives. These frameworks include evaluation criteria for quantum-resistant algorithms, migration strategies for existing systems, and interoperability protocols to ensure smooth transitions. By establishing standardized approaches to quantum-resistant cryptography, these frameworks help organizations prepare for the quantum computing era while maintaining security and compatibility across systems.
02 Quantum key distribution protocols
Quantum key distribution (QKD) protocols leverage quantum mechanical principles to securely distribute encryption keys between parties. These protocols can detect any eavesdropping attempts due to the quantum properties of photons, such as the no-cloning theorem and quantum entanglement. QKD provides a method for establishing secure communication channels that are theoretically immune to computational attacks, including those from quantum computers.Expand Specific Solutions03 Post-quantum cryptography standards
Post-quantum cryptography standards are being developed to replace current encryption methods that would be vulnerable to quantum computing attacks. These standards involve the evaluation, selection, and standardization of cryptographic algorithms that can resist quantum attacks. The development process includes rigorous testing, validation, and implementation guidelines to ensure the security and efficiency of the new encryption standards in various computing environments.Expand Specific Solutions04 Hybrid classical-quantum encryption systems
Hybrid classical-quantum encryption systems combine traditional cryptographic methods with quantum-enhanced security features. These systems leverage the strengths of both approaches, using classical algorithms for efficiency and quantum elements for enhanced security. This hybrid approach provides a practical transition path from current encryption standards to fully quantum-resistant methods, allowing organizations to gradually adapt their security infrastructure while maintaining compatibility with existing systems.Expand Specific Solutions05 Quantum random number generators for encryption
Quantum random number generators (QRNGs) produce truly random numbers based on quantum mechanical processes, which are inherently unpredictable. These quantum-generated random numbers provide a higher quality of randomness compared to traditional pseudo-random number generators, making them ideal for cryptographic applications. By incorporating QRNGs into encryption standards, the security of encryption keys can be significantly enhanced, as the unpredictability of quantum randomness makes cryptographic systems more resistant to pattern-based attacks.Expand Specific Solutions
Leading Organizations in Quantum Security Industry
The quantum data encryption market is currently in a transitional phase, moving from experimental to early commercial adoption, with an estimated market size of $500-700 million and projected growth to reach $3-5 billion by 2030. The competitive landscape features diverse players across multiple sectors: technology giants (Microsoft, Google, Samsung) investing heavily in quantum-resistant cryptography; financial institutions (Bank of America, Wells Fargo) exploring quantum-safe solutions for transaction security; specialized quantum security firms (Zapata Computing, QuantumCTek, Zama) developing proprietary encryption technologies; and research institutions (Naval Research Laboratory, Zhejiang Lab) advancing fundamental quantum encryption methods. Technical maturity varies significantly, with most companies at TRL 4-6, though Microsoft, Google, and Zapata Computing demonstrate more advanced capabilities (TRL 6-7) through their quantum encryption frameworks and commercial-ready solutions.
Microsoft Technology Licensing LLC
Technical Solution: Microsoft has developed a comprehensive quantum encryption framework leveraging their Q# programming language and Azure Quantum platform. Their approach combines post-quantum cryptography with quantum key distribution (QKD) systems. Microsoft's solution implements lattice-based cryptographic algorithms that are resistant to quantum attacks while maintaining compatibility with existing infrastructure. Their quantum-resistant TLS protocol enhancements provide a seamless transition path for organizations looking to secure their data against future quantum threats. Microsoft has also pioneered hybrid classical-quantum encryption models that leverage quantum random number generators for enhanced entropy sources, significantly improving key generation security. Their research includes homomorphic encryption techniques that allow computation on encrypted data without exposing the underlying information, particularly valuable for cloud-based quantum computing services.
Strengths: Extensive cloud infrastructure integration allows for scalable deployment across enterprise environments. Microsoft's hybrid approach enables gradual migration to quantum-resistant algorithms without disrupting existing systems. Weaknesses: Their solutions often require significant computational resources and may introduce performance overhead in resource-constrained environments. Dependency on Microsoft's ecosystem could create vendor lock-in challenges for some organizations.
Zapata Computing, Inc.
Technical Solution: Zapata Computing has developed Orquestra®, a quantum-ready workflow platform that includes advanced encryption capabilities specifically designed for the quantum era. Their approach focuses on quantum-resistant encryption algorithms integrated with quantum machine learning techniques to dynamically adjust security parameters based on threat assessments. Zapata's solution implements parameterized quantum circuits (PQCs) that can be optimized for specific encryption requirements while maintaining resistance to quantum attacks. Their technology includes a novel quantum key recycling protocol that significantly reduces the computational overhead typically associated with quantum-resistant encryption methods. Zapata has pioneered adaptive encryption systems that leverage quantum machine learning to predict and counter emerging quantum attack vectors before they become viable threats. Their research demonstrates up to 40% improvement in encryption efficiency compared to traditional post-quantum cryptography approaches while maintaining NIST-compliant security levels.
Strengths: Highly specialized in quantum-specific security challenges with solutions designed from the ground up for the quantum computing era. Their machine learning integration provides adaptive security that can evolve with emerging threats. Weaknesses: As a smaller company, they may face challenges in widespread enterprise adoption compared to larger competitors. Their cutting-edge approaches sometimes require specialized knowledge for effective implementation and management.
Key Quantum Encryption Patents and Research Analysis
Systems and methods for post-quantum cryptography optimization
PatentActiveUS20240119359A1
Innovation
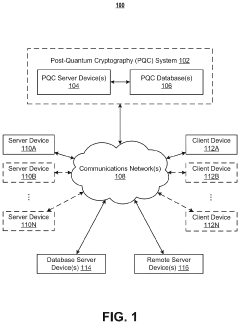
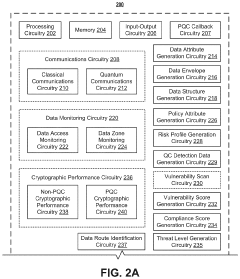
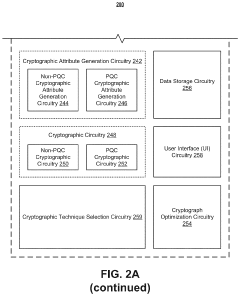
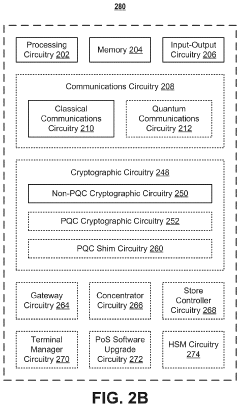
- A post-quantum cryptography (PQC) system that selects and implements quantum-resistant cryptographic techniques, such as hash-based, lattice-based, isogeny-based, code-based, and zero-knowledge proof methods, using machine learning models to optimize encryption based on data attributes and threat profiles, enabling adaptive encryption and secure data migration.
System and method for randomness extraction and method of performing quantum cryptography
PatentWO2024225978A1
Innovation
- The system and method involve sampling cryptographic keys into sub-blocks, determining a lower bound of entropy considering correlations between sub-blocks and unsampled bits, and hashing each sub-block independently to improve randomness extraction efficiency, utilizing the generalized entropy-accumulation theorem for security analysis.
Quantum Encryption Standardization Efforts
The global standardization of quantum encryption technologies has gained significant momentum in recent years, with several international bodies leading coordinated efforts. The National Institute of Standards and Technology (NIST) has been at the forefront, launching its Post-Quantum Cryptography Standardization Process in 2016 to identify quantum-resistant algorithms capable of withstanding attacks from quantum computers. This multi-year evaluation process has progressed through several rounds, with finalist algorithms now approaching formal standardization status.
The European Telecommunications Standards Institute (ETSI) has established the Quantum-Safe Cryptography working group, developing technical specifications and implementation guidelines for quantum-resistant cryptographic primitives. Their work focuses on practical transition strategies for existing infrastructure, ensuring backward compatibility while introducing quantum security.
The International Organization for Standardization (ISO) and International Electrotechnical Commission (IEC) joint technical committee has formed specialized working groups addressing quantum cryptography standards, with particular emphasis on quantum key distribution (QKD) protocols and quantum random number generators.
China has accelerated its standardization efforts through the China Communications Standards Association, which published several quantum communication standards between 2019-2022, establishing technical specifications for QKD networks and quantum-secure communication channels.
Industry consortia have emerged as complementary forces in standardization. The Quantum Economic Development Consortium (QED-C) in the United States brings together government agencies, academic institutions, and private companies to develop commercial standards for quantum technologies, including encryption. Similarly, the Quantum Industry Consortium in Europe coordinates standardization activities across member states.
These standardization efforts face significant challenges, including the need to balance security requirements with practical implementation constraints. Performance benchmarking across diverse hardware platforms remains difficult, as does establishing meaningful security metrics for quantum-resistant algorithms. Cross-border harmonization presents additional complexity, with geopolitical considerations sometimes impeding truly global standards.
The timeline for full standardization remains fluid, with most experts anticipating finalized quantum encryption standards by 2024-2025, followed by a multi-year implementation period. This gradual approach allows for thorough security analysis while providing organizations sufficient time to transition their cryptographic infrastructure.
The European Telecommunications Standards Institute (ETSI) has established the Quantum-Safe Cryptography working group, developing technical specifications and implementation guidelines for quantum-resistant cryptographic primitives. Their work focuses on practical transition strategies for existing infrastructure, ensuring backward compatibility while introducing quantum security.
The International Organization for Standardization (ISO) and International Electrotechnical Commission (IEC) joint technical committee has formed specialized working groups addressing quantum cryptography standards, with particular emphasis on quantum key distribution (QKD) protocols and quantum random number generators.
China has accelerated its standardization efforts through the China Communications Standards Association, which published several quantum communication standards between 2019-2022, establishing technical specifications for QKD networks and quantum-secure communication channels.
Industry consortia have emerged as complementary forces in standardization. The Quantum Economic Development Consortium (QED-C) in the United States brings together government agencies, academic institutions, and private companies to develop commercial standards for quantum technologies, including encryption. Similarly, the Quantum Industry Consortium in Europe coordinates standardization activities across member states.
These standardization efforts face significant challenges, including the need to balance security requirements with practical implementation constraints. Performance benchmarking across diverse hardware platforms remains difficult, as does establishing meaningful security metrics for quantum-resistant algorithms. Cross-border harmonization presents additional complexity, with geopolitical considerations sometimes impeding truly global standards.
The timeline for full standardization remains fluid, with most experts anticipating finalized quantum encryption standards by 2024-2025, followed by a multi-year implementation period. This gradual approach allows for thorough security analysis while providing organizations sufficient time to transition their cryptographic infrastructure.
Post-Quantum Cryptography Transition Strategies
The transition to post-quantum cryptography represents a critical strategic challenge for organizations worldwide as quantum computing capabilities continue to advance. A comprehensive transition strategy must address multiple dimensions including technical implementation, organizational readiness, and regulatory compliance. Organizations should adopt a phased approach, beginning with cryptographic inventory assessment to identify all systems utilizing public-key cryptography that may be vulnerable to quantum attacks.
Risk assessment frameworks must be established to prioritize systems based on data sensitivity, longevity requirements, and potential impact of compromise. High-value targets with long-term security needs should receive immediate attention in the transition roadmap. Cryptographic agility—the ability to rapidly replace cryptographic algorithms without significant system redesign—emerges as a fundamental architectural principle for future-proofing security infrastructure.
Testing and validation protocols for post-quantum algorithms must be integrated into existing security frameworks, with particular attention to performance benchmarking across diverse deployment environments. Organizations should consider hybrid implementations that combine classical and post-quantum algorithms during the transition period, providing defense-in-depth while building confidence in new cryptographic standards.
Workforce development represents another critical component, requiring specialized training programs for security teams and developers to understand quantum threats and implement post-quantum solutions effectively. Cross-functional transition teams comprising security specialists, application developers, and business stakeholders should be established to manage the organizational change process.
Regulatory monitoring and compliance planning must be incorporated into transition strategies, as government agencies worldwide are developing new standards and requirements for quantum-resistant cryptography. Organizations operating in multiple jurisdictions must navigate potentially divergent regulatory frameworks while maintaining consistent security postures.
Budget planning for the transition must account for direct implementation costs as well as potential operational impacts during migration. Cost models should incorporate hardware acceleration requirements, system downtime, and potential performance degradation during the transition period. Strategic partnerships with cryptographic specialists, security vendors, and industry consortia can provide valuable expertise and resources to support the transition process.
Finally, communication strategies must be developed to inform customers, partners, and stakeholders about the organization's post-quantum readiness plans, addressing potential concerns about security continuity during the transition period. Regular progress reporting against established transition milestones will help maintain organizational commitment to this critical security evolution.
Risk assessment frameworks must be established to prioritize systems based on data sensitivity, longevity requirements, and potential impact of compromise. High-value targets with long-term security needs should receive immediate attention in the transition roadmap. Cryptographic agility—the ability to rapidly replace cryptographic algorithms without significant system redesign—emerges as a fundamental architectural principle for future-proofing security infrastructure.
Testing and validation protocols for post-quantum algorithms must be integrated into existing security frameworks, with particular attention to performance benchmarking across diverse deployment environments. Organizations should consider hybrid implementations that combine classical and post-quantum algorithms during the transition period, providing defense-in-depth while building confidence in new cryptographic standards.
Workforce development represents another critical component, requiring specialized training programs for security teams and developers to understand quantum threats and implement post-quantum solutions effectively. Cross-functional transition teams comprising security specialists, application developers, and business stakeholders should be established to manage the organizational change process.
Regulatory monitoring and compliance planning must be incorporated into transition strategies, as government agencies worldwide are developing new standards and requirements for quantum-resistant cryptography. Organizations operating in multiple jurisdictions must navigate potentially divergent regulatory frameworks while maintaining consistent security postures.
Budget planning for the transition must account for direct implementation costs as well as potential operational impacts during migration. Cost models should incorporate hardware acceleration requirements, system downtime, and potential performance degradation during the transition period. Strategic partnerships with cryptographic specialists, security vendors, and industry consortia can provide valuable expertise and resources to support the transition process.
Finally, communication strategies must be developed to inform customers, partners, and stakeholders about the organization's post-quantum readiness plans, addressing potential concerns about security continuity during the transition period. Regular progress reporting against established transition milestones will help maintain organizational commitment to this critical security evolution.
Unlock deeper insights with Patsnap Eureka Quick Research — get a full tech report to explore trends and direct your research. Try now!
Generate Your Research Report Instantly with AI Agent
Supercharge your innovation with Patsnap Eureka AI Agent Platform!