Battery Management System Security: Protecting Data Integrity and Privacy
AUG 8, 20259 MIN READ
Generate Your Research Report Instantly with AI Agent
Patsnap Eureka helps you evaluate technical feasibility & market potential.
BMS Security Background and Objectives
Battery Management System (BMS) security has become a critical concern in the rapidly evolving landscape of electric vehicles and energy storage systems. The increasing reliance on lithium-ion batteries in various applications has highlighted the need for robust protection mechanisms to safeguard data integrity and privacy within BMS. This technology domain has witnessed significant advancements over the past decade, driven by the growing demand for efficient and secure energy management solutions.
The primary objective of BMS security is to ensure the confidentiality, integrity, and availability of critical battery data and control systems. As BMS plays a crucial role in monitoring and managing battery performance, temperature, and state of charge, any compromise in its security could lead to severe consequences, including safety hazards, performance degradation, and unauthorized access to sensitive information.
The evolution of BMS security has been closely tied to the overall development of cybersecurity practices in the automotive and energy sectors. Initially, security measures were primarily focused on physical access control and basic encryption techniques. However, as the complexity of BMS increased and the potential attack vectors expanded, more sophisticated security approaches have been developed and implemented.
One of the key trends in BMS security is the integration of advanced cryptographic protocols to protect data transmission between various components of the system. This includes secure communication channels between battery cells, control units, and external interfaces. Additionally, there has been a growing emphasis on implementing robust authentication mechanisms to prevent unauthorized access and tampering attempts.
The technological goals in this field are multifaceted, encompassing both immediate security enhancements and long-term resilience against emerging threats. Key objectives include developing adaptive security algorithms that can detect and respond to potential attacks in real-time, implementing secure over-the-air update mechanisms for BMS firmware, and creating standardized security protocols specifically tailored for battery management systems.
Furthermore, there is a strong focus on addressing the unique challenges posed by the distributed nature of modern BMS architectures. This includes developing secure methods for data aggregation and analysis across multiple battery modules, as well as implementing privacy-preserving techniques to protect sensitive user information while still allowing for necessary data collection and analysis for system optimization.
As the industry moves towards more interconnected and intelligent energy systems, the importance of BMS security continues to grow. The ongoing research and development efforts aim to create a robust security framework that can adapt to the evolving threat landscape while supporting the increasing functionality and performance requirements of modern battery systems.
The primary objective of BMS security is to ensure the confidentiality, integrity, and availability of critical battery data and control systems. As BMS plays a crucial role in monitoring and managing battery performance, temperature, and state of charge, any compromise in its security could lead to severe consequences, including safety hazards, performance degradation, and unauthorized access to sensitive information.
The evolution of BMS security has been closely tied to the overall development of cybersecurity practices in the automotive and energy sectors. Initially, security measures were primarily focused on physical access control and basic encryption techniques. However, as the complexity of BMS increased and the potential attack vectors expanded, more sophisticated security approaches have been developed and implemented.
One of the key trends in BMS security is the integration of advanced cryptographic protocols to protect data transmission between various components of the system. This includes secure communication channels between battery cells, control units, and external interfaces. Additionally, there has been a growing emphasis on implementing robust authentication mechanisms to prevent unauthorized access and tampering attempts.
The technological goals in this field are multifaceted, encompassing both immediate security enhancements and long-term resilience against emerging threats. Key objectives include developing adaptive security algorithms that can detect and respond to potential attacks in real-time, implementing secure over-the-air update mechanisms for BMS firmware, and creating standardized security protocols specifically tailored for battery management systems.
Furthermore, there is a strong focus on addressing the unique challenges posed by the distributed nature of modern BMS architectures. This includes developing secure methods for data aggregation and analysis across multiple battery modules, as well as implementing privacy-preserving techniques to protect sensitive user information while still allowing for necessary data collection and analysis for system optimization.
As the industry moves towards more interconnected and intelligent energy systems, the importance of BMS security continues to grow. The ongoing research and development efforts aim to create a robust security framework that can adapt to the evolving threat landscape while supporting the increasing functionality and performance requirements of modern battery systems.
Market Demand for Secure BMS
The market demand for secure Battery Management Systems (BMS) has been steadily increasing in recent years, driven by the rapid growth of electric vehicles (EVs) and renewable energy storage systems. As these technologies become more prevalent, the need for robust security measures to protect the integrity and privacy of BMS data has become paramount.
The automotive industry, in particular, has been a significant driver of demand for secure BMS solutions. With the global EV market expanding at an unprecedented rate, manufacturers are increasingly focused on ensuring the safety and reliability of their vehicles' battery systems. This includes protecting against potential cyber attacks that could compromise vehicle performance, safety, or user privacy.
In the renewable energy sector, large-scale battery storage systems are becoming crucial components of grid infrastructure. These systems require sophisticated BMS to optimize performance and longevity. As these installations grow in size and importance, the need for secure BMS to protect against data breaches and malicious interference has become a top priority for utility companies and energy providers.
The industrial sector has also contributed to the growing demand for secure BMS. As factories and manufacturing facilities increasingly adopt automation and smart technologies, the security of their energy storage systems becomes critical to maintaining operational continuity and protecting proprietary information.
Consumer electronics represent another significant market segment driving demand for secure BMS. With the proliferation of smart devices and wearable technologies, consumers are becoming more aware of the importance of data privacy and security. This awareness has led to increased demand for devices with secure BMS that can protect personal information and ensure device reliability.
The healthcare industry has emerged as a new frontier for BMS applications, particularly in medical devices and portable healthcare equipment. The sensitive nature of patient data and the critical importance of device reliability in medical settings have created a strong demand for highly secure BMS solutions.
As cyber threats continue to evolve and become more sophisticated, the market for secure BMS is expected to grow further. Organizations across various sectors are recognizing the potential risks associated with unsecured battery systems and are actively seeking solutions that can provide comprehensive protection against data breaches, unauthorized access, and tampering.
This growing demand has spurred innovation in the BMS security space, with companies developing advanced encryption techniques, secure communication protocols, and tamper-resistant hardware designs. The market is also seeing increased interest in blockchain technology and artificial intelligence as potential tools for enhancing BMS security and data integrity.
The automotive industry, in particular, has been a significant driver of demand for secure BMS solutions. With the global EV market expanding at an unprecedented rate, manufacturers are increasingly focused on ensuring the safety and reliability of their vehicles' battery systems. This includes protecting against potential cyber attacks that could compromise vehicle performance, safety, or user privacy.
In the renewable energy sector, large-scale battery storage systems are becoming crucial components of grid infrastructure. These systems require sophisticated BMS to optimize performance and longevity. As these installations grow in size and importance, the need for secure BMS to protect against data breaches and malicious interference has become a top priority for utility companies and energy providers.
The industrial sector has also contributed to the growing demand for secure BMS. As factories and manufacturing facilities increasingly adopt automation and smart technologies, the security of their energy storage systems becomes critical to maintaining operational continuity and protecting proprietary information.
Consumer electronics represent another significant market segment driving demand for secure BMS. With the proliferation of smart devices and wearable technologies, consumers are becoming more aware of the importance of data privacy and security. This awareness has led to increased demand for devices with secure BMS that can protect personal information and ensure device reliability.
The healthcare industry has emerged as a new frontier for BMS applications, particularly in medical devices and portable healthcare equipment. The sensitive nature of patient data and the critical importance of device reliability in medical settings have created a strong demand for highly secure BMS solutions.
As cyber threats continue to evolve and become more sophisticated, the market for secure BMS is expected to grow further. Organizations across various sectors are recognizing the potential risks associated with unsecured battery systems and are actively seeking solutions that can provide comprehensive protection against data breaches, unauthorized access, and tampering.
This growing demand has spurred innovation in the BMS security space, with companies developing advanced encryption techniques, secure communication protocols, and tamper-resistant hardware designs. The market is also seeing increased interest in blockchain technology and artificial intelligence as potential tools for enhancing BMS security and data integrity.
Current BMS Security Challenges
Battery Management Systems (BMS) are critical components in modern energy storage solutions, particularly in electric vehicles and renewable energy systems. However, as these systems become more sophisticated and interconnected, they face increasing security challenges that threaten data integrity and privacy.
One of the primary security challenges for BMS is the vulnerability to cyber attacks. As BMS increasingly rely on wireless communication and cloud-based data management, they become potential targets for malicious actors. These attacks can range from data theft to more severe scenarios where attackers gain control over the battery system, potentially leading to safety hazards or system failures.
Data integrity is another significant concern. BMS continuously collect and process vast amounts of data related to battery performance, charging cycles, and overall health. Ensuring the accuracy and reliability of this data is crucial for optimal battery management and longevity. However, data can be compromised through various means, including sensor malfunctions, communication errors, or deliberate tampering. Inaccurate or manipulated data can lead to incorrect decisions in battery management, potentially reducing efficiency or even causing damage to the battery system.
Privacy issues also pose a substantial challenge. The data collected by BMS can reveal sensitive information about user behavior, location, and energy consumption patterns. In the case of electric vehicles, this data could potentially be used to track an individual's movements or habits. Protecting this personal information from unauthorized access or misuse is a critical concern, especially in light of increasingly stringent data protection regulations worldwide.
Interoperability and standardization present additional challenges. As the BMS market grows, a multitude of proprietary systems and protocols have emerged. This lack of standardization can create security vulnerabilities, as different systems may have varying levels of security implementation. It also complicates the process of integrating security measures across different platforms and manufacturers.
The rapid pace of technological advancement in battery technology and energy management systems further compounds these security challenges. As new features and capabilities are introduced, they often outpace the development of corresponding security measures. This creates a constant need for updating and improving security protocols to address emerging threats and vulnerabilities.
Resource constraints in BMS hardware also pose significant challenges. Many BMS, especially in smaller or lower-cost applications, have limited computational power and memory. This can restrict the implementation of robust security measures, such as advanced encryption or real-time threat detection, which often require substantial processing capabilities.
Lastly, the physical security of BMS components is an often overlooked challenge. While much focus is placed on cybersecurity, physical tampering or unauthorized access to BMS hardware can also compromise system integrity and data security. Developing tamper-resistant hardware and secure physical interfaces is crucial in creating a comprehensive security solution for BMS.
One of the primary security challenges for BMS is the vulnerability to cyber attacks. As BMS increasingly rely on wireless communication and cloud-based data management, they become potential targets for malicious actors. These attacks can range from data theft to more severe scenarios where attackers gain control over the battery system, potentially leading to safety hazards or system failures.
Data integrity is another significant concern. BMS continuously collect and process vast amounts of data related to battery performance, charging cycles, and overall health. Ensuring the accuracy and reliability of this data is crucial for optimal battery management and longevity. However, data can be compromised through various means, including sensor malfunctions, communication errors, or deliberate tampering. Inaccurate or manipulated data can lead to incorrect decisions in battery management, potentially reducing efficiency or even causing damage to the battery system.
Privacy issues also pose a substantial challenge. The data collected by BMS can reveal sensitive information about user behavior, location, and energy consumption patterns. In the case of electric vehicles, this data could potentially be used to track an individual's movements or habits. Protecting this personal information from unauthorized access or misuse is a critical concern, especially in light of increasingly stringent data protection regulations worldwide.
Interoperability and standardization present additional challenges. As the BMS market grows, a multitude of proprietary systems and protocols have emerged. This lack of standardization can create security vulnerabilities, as different systems may have varying levels of security implementation. It also complicates the process of integrating security measures across different platforms and manufacturers.
The rapid pace of technological advancement in battery technology and energy management systems further compounds these security challenges. As new features and capabilities are introduced, they often outpace the development of corresponding security measures. This creates a constant need for updating and improving security protocols to address emerging threats and vulnerabilities.
Resource constraints in BMS hardware also pose significant challenges. Many BMS, especially in smaller or lower-cost applications, have limited computational power and memory. This can restrict the implementation of robust security measures, such as advanced encryption or real-time threat detection, which often require substantial processing capabilities.
Lastly, the physical security of BMS components is an often overlooked challenge. While much focus is placed on cybersecurity, physical tampering or unauthorized access to BMS hardware can also compromise system integrity and data security. Developing tamper-resistant hardware and secure physical interfaces is crucial in creating a comprehensive security solution for BMS.
Existing BMS Security Solutions
01 Secure data transmission and storage in Battery Management Systems
Battery Management Systems (BMS) require secure methods for transmitting and storing sensitive data. This includes encryption techniques, secure communication protocols, and tamper-resistant storage solutions to protect battery-related information from unauthorized access or manipulation.- Secure data transmission and storage in Battery Management Systems: Battery Management Systems (BMS) require secure methods for transmitting and storing sensitive data. This includes encryption techniques, secure communication protocols, and tamper-resistant storage solutions to protect battery-related information from unauthorized access or manipulation.
- Privacy-preserving data collection and analysis: Implementing privacy-preserving techniques in BMS data collection and analysis ensures that user information remains confidential while still allowing for meaningful insights. This may involve data anonymization, differential privacy, or federated learning approaches to protect individual privacy while enabling system-wide optimization.
- Blockchain-based data integrity for Battery Management Systems: Utilizing blockchain technology to ensure data integrity in BMS. This approach creates an immutable and transparent record of battery-related data, making it resistant to tampering and providing a reliable audit trail for various stakeholders in the battery ecosystem.
- Access control and authentication mechanisms: Implementing robust access control and authentication mechanisms in BMS to ensure that only authorized personnel can access sensitive battery data and control functions. This may include multi-factor authentication, role-based access control, and secure key management systems.
- Real-time monitoring and anomaly detection: Incorporating real-time monitoring and anomaly detection capabilities in BMS to identify potential security breaches or data integrity issues. This involves using machine learning algorithms and statistical analysis to detect unusual patterns or behaviors that may indicate unauthorized access or data manipulation attempts.
02 Privacy-preserving data analytics for BMS
Implementing privacy-preserving techniques in data analytics for Battery Management Systems allows for the extraction of valuable insights while protecting individual user data. This may involve anonymization, differential privacy, or federated learning approaches to maintain user privacy while optimizing battery performance and longevity.Expand Specific Solutions03 Blockchain-based data integrity for BMS
Utilizing blockchain technology to ensure data integrity in Battery Management Systems provides a tamper-proof and transparent record of battery-related data. This approach can enhance trust in the data collected from electric vehicles and energy storage systems, enabling more reliable analysis and decision-making.Expand Specific Solutions04 Access control and authentication mechanisms for BMS
Implementing robust access control and authentication mechanisms in Battery Management Systems helps prevent unauthorized access to sensitive battery data and control functions. This includes multi-factor authentication, role-based access control, and secure key management to ensure that only authorized personnel can interact with the BMS.Expand Specific Solutions05 Real-time data validation and error detection in BMS
Incorporating real-time data validation and error detection techniques in Battery Management Systems helps maintain data integrity and identify potential security breaches or system malfunctions. This may involve machine learning algorithms, statistical analysis, and anomaly detection to ensure the accuracy and reliability of battery-related data.Expand Specific Solutions
Key Players in BMS Security
The Battery Management System (BMS) security market is in a growth phase, driven by increasing adoption of electric vehicles and energy storage systems. The market size is expanding rapidly, with projections indicating significant growth in the coming years. Technologically, BMS security is evolving, with companies like LG Energy Solution, Contemporary Amperex Technology, and Samsung SDI leading innovations. These firms are developing advanced encryption, authentication, and intrusion detection features to protect data integrity and privacy. Other players like Honda, Toyota, and Sony are also contributing to BMS security advancements, particularly in automotive applications. The competitive landscape is dynamic, with both established electronics giants and specialized battery technology firms vying for market share.
Samsung SDI Co., Ltd.
Technical Solution: Samsung SDI's BMS security solution leverages their expertise in both battery technology and consumer electronics security. Their system employs a dedicated security chip with a physical unclonable function (PUF) for unique device identification and secure key generation[9]. Samsung's BMS uses end-to-end encryption for all data communications, with a focus on lightweight cryptographic algorithms suitable for resource-constrained environments. They have implemented a secure element for storing sensitive data and performing cryptographic operations, isolated from the main BMS processor. Samsung's solution also includes a secure firmware update mechanism with rollback protection and a hardware-backed secure boot process. Additionally, they have developed a cloud-based monitoring system with multi-factor authentication and encrypted data storage for remote battery management and diagnostics[10].
Strengths: Integration of advanced security features from consumer electronics, lightweight cryptography for efficiency, and secure cloud-based monitoring. Weaknesses: Potential dependency on Samsung's ecosystem for full functionality, may require adaptation for use with non-Samsung battery systems.
Sensata Technologies, Inc.
Technical Solution: Sensata Technologies has developed a BMS security solution that focuses on protecting the integrity of sensor data and the privacy of battery usage information. Their approach utilizes secure microcontrollers with built-in cryptographic accelerators to ensure efficient encryption and authentication of sensor data[7]. Sensata's BMS implements a secure communication protocol that includes message authentication codes (MACs) to prevent data tampering and replay attacks. They have also developed a novel technique for privacy-preserving battery state estimation, which allows for accurate monitoring of battery health without compromising user privacy[8]. Additionally, Sensata's solution includes secure boot and firmware validation mechanisms to protect against malware and unauthorized modifications to the BMS software.
Strengths: Strong focus on sensor data integrity and privacy-preserving techniques. Weaknesses: May have limited features compared to more comprehensive security solutions offered by larger competitors.
Core BMS Security Innovations
Protected system for controlling power transactions for an electric vehicle
PatentActiveIN6388CHENP2014A
Innovation
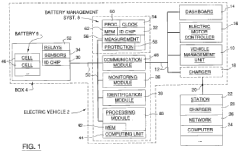
- A protected system for controlling power transactions in electric vehicles, incorporating identification modules, integrity sensors, a monitoring module, device identification, processing, and communication modules to track and verify the integrity of the battery, its box, and management system, and alert in case of energy imbalances or breaches.
Battery security systems and methods
PatentPendingUS20250094551A1
Innovation
- A battery security system that employs a battery management system (BMS) to manage a security key or token, verifying ownership and preventing operation if stolen, using a control system to communicate with the BMS and remotely deactivate batteries if necessary.
Regulatory Framework for BMS
The regulatory framework for Battery Management System (BMS) security is a critical aspect of ensuring data integrity and privacy in the rapidly evolving electric vehicle (EV) and energy storage industries. As the adoption of EVs and large-scale energy storage systems continues to grow, governments and regulatory bodies worldwide are recognizing the need for comprehensive guidelines to protect sensitive information and maintain the integrity of BMS data.
In the United States, the National Highway Traffic Safety Administration (NHTSA) has been at the forefront of developing regulations for vehicle cybersecurity, including BMS security. The agency has issued guidelines that emphasize the importance of implementing robust security measures throughout the vehicle's lifecycle, from design to decommissioning. These guidelines specifically address the need for secure communication protocols, encryption of sensitive data, and regular security audits for BMS components.
The European Union has taken a proactive approach with the implementation of the General Data Protection Regulation (GDPR), which has significant implications for BMS security. While not specifically targeting BMS, the GDPR's stringent requirements for data protection and privacy apply to the personal data collected and processed by these systems. This has led to increased focus on data minimization, user consent, and the right to be forgotten in BMS design and operation.
In China, the Cybersecurity Law and the more recent Data Security Law have set the foundation for BMS security regulations. These laws mandate strict data localization requirements and emphasize the protection of critical infrastructure, which includes electric vehicle charging networks and their associated BMS. Chinese authorities have also issued specific guidelines for the automotive industry, addressing the security of connected vehicles and their components.
International standards organizations play a crucial role in shaping the regulatory landscape for BMS security. The ISO/SAE 21434 standard, developed jointly by the International Organization for Standardization (ISO) and the Society of Automotive Engineers (SAE), provides a comprehensive framework for cybersecurity in road vehicles. This standard includes specific provisions for securing battery management systems and is being widely adopted by automotive manufacturers and suppliers globally.
The regulatory framework for BMS security is still evolving, with many countries in the process of developing or refining their approaches. There is a growing trend towards harmonization of standards across different regions to facilitate global trade and ensure consistent security practices. However, challenges remain in balancing the need for stringent security measures with the practicalities of implementation and the rapid pace of technological advancement in the BMS field.
In the United States, the National Highway Traffic Safety Administration (NHTSA) has been at the forefront of developing regulations for vehicle cybersecurity, including BMS security. The agency has issued guidelines that emphasize the importance of implementing robust security measures throughout the vehicle's lifecycle, from design to decommissioning. These guidelines specifically address the need for secure communication protocols, encryption of sensitive data, and regular security audits for BMS components.
The European Union has taken a proactive approach with the implementation of the General Data Protection Regulation (GDPR), which has significant implications for BMS security. While not specifically targeting BMS, the GDPR's stringent requirements for data protection and privacy apply to the personal data collected and processed by these systems. This has led to increased focus on data minimization, user consent, and the right to be forgotten in BMS design and operation.
In China, the Cybersecurity Law and the more recent Data Security Law have set the foundation for BMS security regulations. These laws mandate strict data localization requirements and emphasize the protection of critical infrastructure, which includes electric vehicle charging networks and their associated BMS. Chinese authorities have also issued specific guidelines for the automotive industry, addressing the security of connected vehicles and their components.
International standards organizations play a crucial role in shaping the regulatory landscape for BMS security. The ISO/SAE 21434 standard, developed jointly by the International Organization for Standardization (ISO) and the Society of Automotive Engineers (SAE), provides a comprehensive framework for cybersecurity in road vehicles. This standard includes specific provisions for securing battery management systems and is being widely adopted by automotive manufacturers and suppliers globally.
The regulatory framework for BMS security is still evolving, with many countries in the process of developing or refining their approaches. There is a growing trend towards harmonization of standards across different regions to facilitate global trade and ensure consistent security practices. However, challenges remain in balancing the need for stringent security measures with the practicalities of implementation and the rapid pace of technological advancement in the BMS field.
BMS Security Risk Assessment
Battery Management System (BMS) security risk assessment is a critical process in ensuring the integrity and privacy of data within electric vehicle (EV) ecosystems. This assessment involves identifying potential vulnerabilities, evaluating the likelihood and impact of security breaches, and developing mitigation strategies to protect against cyber threats.
One of the primary risks in BMS security is unauthorized access to sensitive data. This includes vehicle performance metrics, battery health information, and user behavior patterns. Malicious actors could exploit these vulnerabilities to compromise user privacy, manipulate battery performance, or even cause safety hazards. The assessment must consider various attack vectors, such as wireless communication interfaces, physical access points, and software vulnerabilities.
Another significant risk is data tampering. Attackers may attempt to alter battery parameters, state of charge calculations, or thermal management settings. Such manipulations could lead to reduced battery life, decreased vehicle performance, or even catastrophic failures. The risk assessment should evaluate the potential impact of data tampering on both individual vehicles and fleet-wide operations.
Denial of service (DoS) attacks pose another threat to BMS security. These attacks could disrupt communication between the BMS and other vehicle systems, potentially rendering the EV inoperable or causing unexpected behavior. The assessment must consider the resilience of the BMS against such attacks and the potential consequences for vehicle safety and reliability.
Supply chain vulnerabilities are also a crucial aspect of BMS security risk assessment. As BMS components often involve multiple suppliers and manufacturers, the potential for compromised hardware or software entering the supply chain must be evaluated. This includes assessing the security practices of suppliers, verifying the authenticity of components, and implementing robust testing procedures.
The risk assessment should also consider the potential for insider threats. Employees or contractors with privileged access to BMS data or systems could intentionally or unintentionally compromise security. Evaluating access controls, monitoring systems, and employee training programs is essential in mitigating these risks.
Furthermore, the assessment must account for the evolving nature of cyber threats. As attack techniques become more sophisticated, the BMS security risk landscape continues to change. Regular reassessment and updating of security measures are necessary to maintain an effective defense against emerging threats.
One of the primary risks in BMS security is unauthorized access to sensitive data. This includes vehicle performance metrics, battery health information, and user behavior patterns. Malicious actors could exploit these vulnerabilities to compromise user privacy, manipulate battery performance, or even cause safety hazards. The assessment must consider various attack vectors, such as wireless communication interfaces, physical access points, and software vulnerabilities.
Another significant risk is data tampering. Attackers may attempt to alter battery parameters, state of charge calculations, or thermal management settings. Such manipulations could lead to reduced battery life, decreased vehicle performance, or even catastrophic failures. The risk assessment should evaluate the potential impact of data tampering on both individual vehicles and fleet-wide operations.
Denial of service (DoS) attacks pose another threat to BMS security. These attacks could disrupt communication between the BMS and other vehicle systems, potentially rendering the EV inoperable or causing unexpected behavior. The assessment must consider the resilience of the BMS against such attacks and the potential consequences for vehicle safety and reliability.
Supply chain vulnerabilities are also a crucial aspect of BMS security risk assessment. As BMS components often involve multiple suppliers and manufacturers, the potential for compromised hardware or software entering the supply chain must be evaluated. This includes assessing the security practices of suppliers, verifying the authenticity of components, and implementing robust testing procedures.
The risk assessment should also consider the potential for insider threats. Employees or contractors with privileged access to BMS data or systems could intentionally or unintentionally compromise security. Evaluating access controls, monitoring systems, and employee training programs is essential in mitigating these risks.
Furthermore, the assessment must account for the evolving nature of cyber threats. As attack techniques become more sophisticated, the BMS security risk landscape continues to change. Regular reassessment and updating of security measures are necessary to maintain an effective defense against emerging threats.
Unlock deeper insights with Patsnap Eureka Quick Research — get a full tech report to explore trends and direct your research. Try now!
Generate Your Research Report Instantly with AI Agent
Supercharge your innovation with Patsnap Eureka AI Agent Platform!