Rail Gun Cybersecurity: Safeguarding Against Control Breaches
AUG 6, 20259 MIN READ
Generate Your Research Report Instantly with AI Agent
Patsnap Eureka helps you evaluate technical feasibility & market potential.
Rail Gun Security Background and Objectives
Rail guns, electromagnetic projectile launchers that use powerful electromagnetic forces to accelerate conductive projectiles to extremely high velocities, have emerged as a cutting-edge technology with significant military and potential civilian applications. The development of rail gun technology can be traced back to the early 20th century, but it has gained renewed interest and rapid advancement in recent decades due to advancements in power systems, materials science, and control technologies.
As rail guns become increasingly sophisticated and integrated into various systems, the need for robust cybersecurity measures has become paramount. The primary objective of rail gun cybersecurity is to safeguard these advanced weapon systems against unauthorized access, control breaches, and potential cyber attacks that could compromise their functionality, accuracy, or strategic value.
The evolution of rail gun technology has been marked by significant milestones in power generation, projectile design, and control systems. However, this progress has also introduced new vulnerabilities in the digital realm. As rail guns rely heavily on complex electronic systems for targeting, firing control, and performance optimization, they have become potential targets for cyber threats.
The cybersecurity landscape for rail guns encompasses a wide range of potential risks, including data interception, system manipulation, and denial-of-service attacks. These threats could potentially lead to catastrophic consequences, such as misfiring, inaccurate targeting, or complete system failure. Therefore, the development of comprehensive cybersecurity strategies for rail gun systems has become a critical focus area for military and defense organizations worldwide.
Current technological trends in rail gun cybersecurity include the implementation of advanced encryption protocols, secure communication channels, and robust authentication mechanisms. Additionally, there is a growing emphasis on developing resilient control systems that can detect and mitigate cyber attacks in real-time, ensuring the continued operation of rail gun systems even under adverse conditions.
The objectives of rail gun cybersecurity research and development are multifaceted. They include enhancing the overall security posture of rail gun systems, developing proactive threat detection and response capabilities, and creating standardized security protocols that can be applied across different rail gun platforms. Furthermore, there is a strong focus on integrating cybersecurity considerations into the early stages of rail gun design and development, ensuring that security measures are built-in rather than added as an afterthought.
As rail gun technology continues to advance, the field of cybersecurity must evolve in tandem to address emerging threats and vulnerabilities. This ongoing technological arms race underscores the critical importance of continued investment in rail gun cybersecurity research and development to maintain the strategic advantage and operational integrity of these advanced weapon systems.
As rail guns become increasingly sophisticated and integrated into various systems, the need for robust cybersecurity measures has become paramount. The primary objective of rail gun cybersecurity is to safeguard these advanced weapon systems against unauthorized access, control breaches, and potential cyber attacks that could compromise their functionality, accuracy, or strategic value.
The evolution of rail gun technology has been marked by significant milestones in power generation, projectile design, and control systems. However, this progress has also introduced new vulnerabilities in the digital realm. As rail guns rely heavily on complex electronic systems for targeting, firing control, and performance optimization, they have become potential targets for cyber threats.
The cybersecurity landscape for rail guns encompasses a wide range of potential risks, including data interception, system manipulation, and denial-of-service attacks. These threats could potentially lead to catastrophic consequences, such as misfiring, inaccurate targeting, or complete system failure. Therefore, the development of comprehensive cybersecurity strategies for rail gun systems has become a critical focus area for military and defense organizations worldwide.
Current technological trends in rail gun cybersecurity include the implementation of advanced encryption protocols, secure communication channels, and robust authentication mechanisms. Additionally, there is a growing emphasis on developing resilient control systems that can detect and mitigate cyber attacks in real-time, ensuring the continued operation of rail gun systems even under adverse conditions.
The objectives of rail gun cybersecurity research and development are multifaceted. They include enhancing the overall security posture of rail gun systems, developing proactive threat detection and response capabilities, and creating standardized security protocols that can be applied across different rail gun platforms. Furthermore, there is a strong focus on integrating cybersecurity considerations into the early stages of rail gun design and development, ensuring that security measures are built-in rather than added as an afterthought.
As rail gun technology continues to advance, the field of cybersecurity must evolve in tandem to address emerging threats and vulnerabilities. This ongoing technological arms race underscores the critical importance of continued investment in rail gun cybersecurity research and development to maintain the strategic advantage and operational integrity of these advanced weapon systems.
Market Analysis for Rail Gun Cybersecurity Solutions
The market for rail gun cybersecurity solutions is experiencing rapid growth, driven by the increasing adoption of advanced electromagnetic propulsion systems in military and research applications. As rail gun technology becomes more sophisticated, the need for robust cybersecurity measures to protect these systems from potential control breaches has become paramount.
The global rail gun market is projected to expand significantly over the next decade, with a corresponding increase in demand for specialized cybersecurity solutions. This growth is primarily fueled by investments from major defense contractors and government agencies in countries such as the United States, China, and Russia. These entities are actively developing rail gun systems for naval and land-based applications, creating a substantial market for cybersecurity products tailored to this emerging technology.
Key market segments for rail gun cybersecurity solutions include military and defense, research institutions, and aerospace industries. The defense sector represents the largest market share, as militaries worldwide seek to secure their advanced weapons systems against potential cyber threats. Research institutions and aerospace companies also contribute to market demand, particularly in the development and testing phases of rail gun technology.
The market landscape is characterized by a mix of established cybersecurity firms adapting their existing solutions for rail gun applications and specialized startups focusing exclusively on this niche. Major players in the defense industry are also developing in-house cybersecurity capabilities to protect their rail gun systems, further driving market growth and innovation.
Geographically, North America currently dominates the market for rail gun cybersecurity solutions, followed by Asia-Pacific and Europe. This distribution aligns with the regions where rail gun development is most active. However, as the technology matures and potentially spreads to other countries, the market for cybersecurity solutions is expected to expand globally.
Key drivers of market growth include the increasing complexity of rail gun control systems, the rising frequency and sophistication of cyber attacks targeting military infrastructure, and stringent government regulations mandating robust cybersecurity measures for advanced weapons systems. Additionally, the potential dual-use nature of rail gun technology in both military and civilian applications is expected to create new market opportunities for cybersecurity providers.
Challenges facing the market include the highly specialized nature of rail gun technology, which requires tailored cybersecurity solutions, and the limited pool of experts with both rail gun and cybersecurity expertise. These factors may initially constrain market growth but also present opportunities for firms that can successfully bridge this knowledge gap.
The global rail gun market is projected to expand significantly over the next decade, with a corresponding increase in demand for specialized cybersecurity solutions. This growth is primarily fueled by investments from major defense contractors and government agencies in countries such as the United States, China, and Russia. These entities are actively developing rail gun systems for naval and land-based applications, creating a substantial market for cybersecurity products tailored to this emerging technology.
Key market segments for rail gun cybersecurity solutions include military and defense, research institutions, and aerospace industries. The defense sector represents the largest market share, as militaries worldwide seek to secure their advanced weapons systems against potential cyber threats. Research institutions and aerospace companies also contribute to market demand, particularly in the development and testing phases of rail gun technology.
The market landscape is characterized by a mix of established cybersecurity firms adapting their existing solutions for rail gun applications and specialized startups focusing exclusively on this niche. Major players in the defense industry are also developing in-house cybersecurity capabilities to protect their rail gun systems, further driving market growth and innovation.
Geographically, North America currently dominates the market for rail gun cybersecurity solutions, followed by Asia-Pacific and Europe. This distribution aligns with the regions where rail gun development is most active. However, as the technology matures and potentially spreads to other countries, the market for cybersecurity solutions is expected to expand globally.
Key drivers of market growth include the increasing complexity of rail gun control systems, the rising frequency and sophistication of cyber attacks targeting military infrastructure, and stringent government regulations mandating robust cybersecurity measures for advanced weapons systems. Additionally, the potential dual-use nature of rail gun technology in both military and civilian applications is expected to create new market opportunities for cybersecurity providers.
Challenges facing the market include the highly specialized nature of rail gun technology, which requires tailored cybersecurity solutions, and the limited pool of experts with both rail gun and cybersecurity expertise. These factors may initially constrain market growth but also present opportunities for firms that can successfully bridge this knowledge gap.
Current Cybersecurity Challenges in Rail Gun Systems
Rail gun systems, while representing a significant advancement in military technology, face a myriad of cybersecurity challenges in the modern digital landscape. These challenges stem from the increasing complexity of rail gun control systems and their integration with networked infrastructure, making them potential targets for cyber attacks.
One of the primary cybersecurity challenges in rail gun systems is the vulnerability of their control networks. These networks, responsible for precise timing and power management, are often interconnected with other military systems, creating potential entry points for malicious actors. The high-speed nature of rail gun operations demands real-time data processing and control, which can be compromised if the network is breached, leading to catastrophic failures or misfires.
Another significant challenge is the protection of sensitive operational data. Rail gun systems generate and process vast amounts of data related to targeting, projectile characteristics, and power management. Ensuring the confidentiality and integrity of this data is crucial, as any compromise could reveal critical military capabilities or strategies to adversaries.
The increasing reliance on software-defined controls in rail gun systems introduces additional vulnerabilities. As these systems become more software-dependent, the risk of code exploitation and malware injection rises. Attackers could potentially manipulate the rail gun's firing parameters, alter targeting data, or even disable the system entirely through sophisticated cyber attacks.
Supply chain security presents another formidable challenge. The components and software used in rail gun systems often come from various suppliers, each representing a potential weak link in the security chain. Ensuring the integrity and security of these components throughout their lifecycle, from manufacturing to deployment, is a complex task that requires rigorous vetting and continuous monitoring.
Furthermore, the rapid evolution of cyber threats poses a constant challenge to rail gun cybersecurity. As new attack vectors and techniques emerge, defense mechanisms must be continuously updated and improved. This necessitates a proactive approach to cybersecurity, including regular vulnerability assessments, penetration testing, and the implementation of adaptive security measures.
The human factor in cybersecurity cannot be overlooked. Personnel operating rail gun systems must be trained to recognize and respond to cyber threats. Social engineering attacks, insider threats, and human error remain significant vulnerabilities that can compromise even the most sophisticated technical defenses.
Lastly, the integration of rail gun systems with broader military networks and command structures introduces complexities in maintaining a robust security posture. Balancing the need for interoperability with the imperative of security requires careful consideration and innovative solutions to prevent cascading vulnerabilities across interconnected systems.
One of the primary cybersecurity challenges in rail gun systems is the vulnerability of their control networks. These networks, responsible for precise timing and power management, are often interconnected with other military systems, creating potential entry points for malicious actors. The high-speed nature of rail gun operations demands real-time data processing and control, which can be compromised if the network is breached, leading to catastrophic failures or misfires.
Another significant challenge is the protection of sensitive operational data. Rail gun systems generate and process vast amounts of data related to targeting, projectile characteristics, and power management. Ensuring the confidentiality and integrity of this data is crucial, as any compromise could reveal critical military capabilities or strategies to adversaries.
The increasing reliance on software-defined controls in rail gun systems introduces additional vulnerabilities. As these systems become more software-dependent, the risk of code exploitation and malware injection rises. Attackers could potentially manipulate the rail gun's firing parameters, alter targeting data, or even disable the system entirely through sophisticated cyber attacks.
Supply chain security presents another formidable challenge. The components and software used in rail gun systems often come from various suppliers, each representing a potential weak link in the security chain. Ensuring the integrity and security of these components throughout their lifecycle, from manufacturing to deployment, is a complex task that requires rigorous vetting and continuous monitoring.
Furthermore, the rapid evolution of cyber threats poses a constant challenge to rail gun cybersecurity. As new attack vectors and techniques emerge, defense mechanisms must be continuously updated and improved. This necessitates a proactive approach to cybersecurity, including regular vulnerability assessments, penetration testing, and the implementation of adaptive security measures.
The human factor in cybersecurity cannot be overlooked. Personnel operating rail gun systems must be trained to recognize and respond to cyber threats. Social engineering attacks, insider threats, and human error remain significant vulnerabilities that can compromise even the most sophisticated technical defenses.
Lastly, the integration of rail gun systems with broader military networks and command structures introduces complexities in maintaining a robust security posture. Balancing the need for interoperability with the imperative of security requires careful consideration and innovative solutions to prevent cascading vulnerabilities across interconnected systems.
Existing Rail Gun Control Protection Strategies
01 Electronic control systems for rail guns
Advanced electronic control systems are utilized in rail guns to manage power distribution, firing sequences, and projectile acceleration. These systems often incorporate sensors, microprocessors, and sophisticated algorithms to optimize performance and ensure precise timing of electromagnetic pulses.- Electronic control systems for rail guns: Advanced electronic control systems are implemented to manage and optimize rail gun operations. These systems regulate power supply, projectile loading, firing sequences, and overall performance monitoring. They often incorporate sensors, microprocessors, and sophisticated algorithms to enhance accuracy, efficiency, and safety of rail gun systems.
- Projectile loading and firing mechanisms: Innovative mechanisms are developed for efficient loading and firing of projectiles in rail guns. These designs focus on improving the speed and reliability of the loading process, as well as ensuring precise alignment and timing during firing. Some systems incorporate automated loading systems, while others use advanced mechanical designs to enhance performance.
- Power supply and energy management: Specialized power supply systems and energy management techniques are crucial for rail gun operation. These systems often involve high-capacity capacitors, pulse-forming networks, and advanced switching mechanisms to deliver the intense bursts of electrical energy required for rail gun firing. Energy recovery and efficiency optimization are key considerations in these designs.
- Rail and armature design improvements: Advancements in rail and armature designs aim to enhance the performance and durability of rail gun systems. These improvements focus on reducing wear, managing heat generation, and optimizing electromagnetic interactions. Novel materials, surface treatments, and geometric configurations are explored to address challenges such as rail erosion and armature integrity.
- Safety and monitoring systems: Comprehensive safety and monitoring systems are integrated into rail gun designs to prevent accidents and ensure reliable operation. These systems may include temperature sensors, pressure monitors, misfire detection mechanisms, and fail-safe shutdown procedures. Advanced diagnostics and real-time monitoring capabilities are implemented to enhance overall system safety and performance.
02 Projectile guidance and stabilization mechanisms
Rail guns employ various mechanisms to guide and stabilize projectiles during launch and flight. These may include specialized rail designs, electromagnetic field shaping, and aerodynamic features integrated into the projectile itself to enhance accuracy and range.Expand Specific Solutions03 Power supply and capacitor bank systems
High-capacity power supply and capacitor bank systems are crucial components in rail gun technology. These systems store and rapidly discharge enormous amounts of electrical energy to generate the electromagnetic fields necessary for projectile acceleration.Expand Specific Solutions04 Rail and conductor design innovations
Advancements in rail and conductor designs focus on improving durability, conductivity, and heat dissipation. Novel materials and configurations are explored to withstand the extreme conditions generated during rail gun operation and enhance overall system efficiency.Expand Specific Solutions05 Safety and breach prevention mechanisms
Rail gun systems incorporate various safety features and breach prevention mechanisms to ensure secure operation and protect against unauthorized access or use. These may include advanced locking systems, fail-safe protocols, and monitoring devices to detect and respond to potential security threats.Expand Specific Solutions
Key Players in Rail Gun Cybersecurity Industry
The rail gun cybersecurity market is in its early growth stage, driven by increasing threats to critical infrastructure. Market size is expanding as rail operators prioritize digital security, though exact figures are limited. Technological maturity varies among key players. Established companies like Siemens AG, Huawei Technologies, and Lockheed Martin bring advanced capabilities, while specialized firms like Cylus Cyber Security offer tailored rail security solutions. Research institutions such as Korea Railroad Research Institute and Railway Technical Research Institute contribute to innovation. The competitive landscape is diverse, with traditional rail technology providers, cybersecurity specialists, and major tech corporations vying for market share in this emerging field.
Siemens AG
Technical Solution: Siemens AG has developed a comprehensive Rail Gun Cybersecurity solution that integrates multiple layers of protection. Their approach includes advanced encryption protocols for control systems, real-time threat detection using AI-powered algorithms, and a secure communication framework for rail infrastructure. Siemens' solution implements a zero-trust architecture, ensuring that every access attempt is verified, regardless of its origin[1]. The system also features adaptive security measures that can automatically respond to potential threats, isolating compromised components to prevent system-wide breaches[3]. Additionally, Siemens has incorporated blockchain technology for immutable logging of all system activities, enhancing forensic capabilities in the event of a security incident[5].
Strengths: Comprehensive multi-layered approach, AI-powered threat detection, and blockchain integration for enhanced security logging. Weaknesses: Potential complexity in implementation and high initial costs for infrastructure upgrades.
Huawei Technologies Co., Ltd.
Technical Solution: Huawei has developed a Rail Cybersecurity solution that leverages its expertise in 5G and IoT technologies. Their approach focuses on creating a secure, high-bandwidth communication network for rail systems. Huawei's solution includes end-to-end encryption for all data transmissions, utilizing quantum-resistant algorithms to future-proof against potential quantum computing threats[6]. The system incorporates AI-driven intrusion detection and prevention mechanisms, capable of identifying and mitigating sophisticated cyber attacks in real-time. Huawei has also implemented a secure-by-design approach in their hardware components, including tamper-resistant modules for critical control systems[8]. Their solution offers a centralized security management platform that provides comprehensive visibility and control over the entire rail network's cybersecurity posture.
Strengths: Strong integration with 5G and IoT technologies, quantum-resistant encryption, and secure hardware design. Weaknesses: Potential geopolitical concerns in some markets due to the company's origin.
Core Innovations in Rail Gun Cybersecurity
System and method for transmitting and receiving data for a rail vehicle
PatentWO2019096610A1
Innovation
- A system with a security system that decouples the control level of a rail vehicle from its communication device, using filters and security protocols to check and monitor data, implemented as modular electronic components or software solutions, including virtual machines, to prevent unauthorized access by filtering and encrypting data before it reaches the control level.
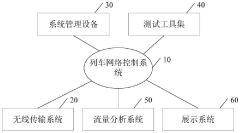
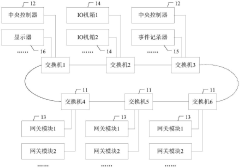
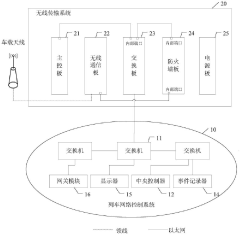
Attack and defense target range system for train network control system and implementation method of attack and defense target range system
PatentPendingCN117134928A
Innovation
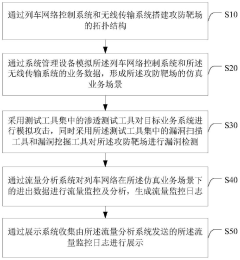
- Designed an attack and defense range system including a train network control system, wireless transmission system, system management equipment, testing tool set, traffic analysis system and display system. By building topology, simulating business data, conducting penetration testing and vulnerability detection, traffic Monitoring and log display enable security assessment of simulated business scenarios and data transmission of the train network.
Regulatory Framework for Rail Gun Cybersecurity
The regulatory framework for rail gun cybersecurity is a critical component in ensuring the safe and secure operation of these advanced weapon systems. As rail guns become increasingly integrated into modern military arsenals, the need for comprehensive cybersecurity regulations has become paramount. These regulations aim to protect rail gun systems from potential control breaches and unauthorized access, which could have severe consequences for national security and military operations.
The framework typically encompasses a multi-layered approach to cybersecurity, addressing various aspects of rail gun technology and its associated control systems. At its core, the regulatory structure mandates the implementation of robust encryption protocols for all communication channels between the rail gun and its control systems. This includes both wired and wireless connections, ensuring that command and control signals remain secure from interception or manipulation.
Additionally, the framework often requires the establishment of strict access control measures. This involves implementing multi-factor authentication for personnel operating the rail gun systems, as well as maintaining detailed logs of all access attempts and system interactions. Such measures help prevent unauthorized individuals from gaining control of the weapon and provide a clear audit trail in the event of a security incident.
Another key aspect of the regulatory framework is the requirement for regular security assessments and penetration testing. These evaluations help identify potential vulnerabilities in the rail gun's cybersecurity defenses and allow for timely remediation. The framework typically specifies the frequency and scope of these assessments, ensuring that they are conducted thoroughly and consistently across all deployed systems.
The regulations also address the supply chain security for rail gun components and software. This includes vetting suppliers, implementing secure development practices, and conducting rigorous testing of all hardware and software before integration into the rail gun system. Such measures help mitigate the risk of compromised components or malicious code being introduced during the manufacturing or maintenance processes.
Furthermore, the regulatory framework often mandates the development and maintenance of comprehensive incident response plans. These plans outline the steps to be taken in the event of a cybersecurity breach, including containment procedures, forensic analysis protocols, and reporting requirements. By establishing clear guidelines for incident handling, the framework ensures a rapid and effective response to potential security threats.
Lastly, the regulations typically include provisions for ongoing training and awareness programs for personnel involved in the operation and maintenance of rail gun systems. These programs aim to educate staff about the latest cybersecurity threats and best practices, fostering a culture of security consciousness throughout the organization.
The framework typically encompasses a multi-layered approach to cybersecurity, addressing various aspects of rail gun technology and its associated control systems. At its core, the regulatory structure mandates the implementation of robust encryption protocols for all communication channels between the rail gun and its control systems. This includes both wired and wireless connections, ensuring that command and control signals remain secure from interception or manipulation.
Additionally, the framework often requires the establishment of strict access control measures. This involves implementing multi-factor authentication for personnel operating the rail gun systems, as well as maintaining detailed logs of all access attempts and system interactions. Such measures help prevent unauthorized individuals from gaining control of the weapon and provide a clear audit trail in the event of a security incident.
Another key aspect of the regulatory framework is the requirement for regular security assessments and penetration testing. These evaluations help identify potential vulnerabilities in the rail gun's cybersecurity defenses and allow for timely remediation. The framework typically specifies the frequency and scope of these assessments, ensuring that they are conducted thoroughly and consistently across all deployed systems.
The regulations also address the supply chain security for rail gun components and software. This includes vetting suppliers, implementing secure development practices, and conducting rigorous testing of all hardware and software before integration into the rail gun system. Such measures help mitigate the risk of compromised components or malicious code being introduced during the manufacturing or maintenance processes.
Furthermore, the regulatory framework often mandates the development and maintenance of comprehensive incident response plans. These plans outline the steps to be taken in the event of a cybersecurity breach, including containment procedures, forensic analysis protocols, and reporting requirements. By establishing clear guidelines for incident handling, the framework ensures a rapid and effective response to potential security threats.
Lastly, the regulations typically include provisions for ongoing training and awareness programs for personnel involved in the operation and maintenance of rail gun systems. These programs aim to educate staff about the latest cybersecurity threats and best practices, fostering a culture of security consciousness throughout the organization.
Threat Modeling for Rail Gun Control Systems
Threat modeling for rail gun control systems is a critical process in identifying and mitigating potential cybersecurity risks. This approach involves systematically analyzing the system architecture, data flows, and potential attack vectors to develop a comprehensive security strategy. The first step in threat modeling is to define the system boundaries and components, including the control interfaces, power systems, targeting mechanisms, and communication channels.
Once the system components are identified, potential threats are enumerated and categorized. These may include unauthorized access attempts, data interception, malware injection, and denial-of-service attacks. Each threat is then assessed based on its likelihood and potential impact on the rail gun's operation and overall mission objectives. This assessment helps prioritize security measures and allocate resources effectively.
A key aspect of threat modeling for rail gun control systems is the identification of trust boundaries. These boundaries delineate where different levels of trust are established within the system, such as between the control center and the rail gun itself, or between different subsystems within the rail gun. Understanding these trust boundaries is crucial for implementing appropriate authentication and authorization mechanisms.
Data flow analysis is another essential component of the threat modeling process. By mapping out how information moves through the system, from user input to weapon activation, potential points of vulnerability can be identified. This analysis helps in implementing data validation, encryption, and integrity checks at critical junctures within the control system.
The threat model also considers the specific operational environment of rail guns. Factors such as electromagnetic interference, physical security of installations, and potential insider threats are incorporated into the analysis. This holistic approach ensures that both cyber and physical security aspects are addressed in the overall security strategy.
Based on the threat model, security controls and countermeasures are designed and implemented. These may include multi-factor authentication for system access, end-to-end encryption for command transmissions, intrusion detection systems, and regular security audits. The model also informs the development of incident response plans and recovery procedures in case of a successful attack.
Continuous updating of the threat model is essential as new vulnerabilities are discovered and the threat landscape evolves. This iterative process ensures that the rail gun control system's security posture remains robust and adaptive to emerging cybersecurity challenges.
Once the system components are identified, potential threats are enumerated and categorized. These may include unauthorized access attempts, data interception, malware injection, and denial-of-service attacks. Each threat is then assessed based on its likelihood and potential impact on the rail gun's operation and overall mission objectives. This assessment helps prioritize security measures and allocate resources effectively.
A key aspect of threat modeling for rail gun control systems is the identification of trust boundaries. These boundaries delineate where different levels of trust are established within the system, such as between the control center and the rail gun itself, or between different subsystems within the rail gun. Understanding these trust boundaries is crucial for implementing appropriate authentication and authorization mechanisms.
Data flow analysis is another essential component of the threat modeling process. By mapping out how information moves through the system, from user input to weapon activation, potential points of vulnerability can be identified. This analysis helps in implementing data validation, encryption, and integrity checks at critical junctures within the control system.
The threat model also considers the specific operational environment of rail guns. Factors such as electromagnetic interference, physical security of installations, and potential insider threats are incorporated into the analysis. This holistic approach ensures that both cyber and physical security aspects are addressed in the overall security strategy.
Based on the threat model, security controls and countermeasures are designed and implemented. These may include multi-factor authentication for system access, end-to-end encryption for command transmissions, intrusion detection systems, and regular security audits. The model also informs the development of incident response plans and recovery procedures in case of a successful attack.
Continuous updating of the threat model is essential as new vulnerabilities are discovered and the threat landscape evolves. This iterative process ensures that the rail gun control system's security posture remains robust and adaptive to emerging cybersecurity challenges.
Unlock deeper insights with Patsnap Eureka Quick Research — get a full tech report to explore trends and direct your research. Try now!
Generate Your Research Report Instantly with AI Agent
Supercharge your innovation with Patsnap Eureka AI Agent Platform!