SST Cybersecurity & Comms: IEC 61850, Time Sync and Logs
AUG 28, 20259 MIN READ
Generate Your Research Report Instantly with AI Agent
Patsnap Eureka helps you evaluate technical feasibility & market potential.
IEC 61850 Evolution and Objectives
The IEC 61850 standard emerged in the late 1990s as a transformative communication protocol specifically designed for electrical substation automation systems. Its development represented a significant shift from proprietary protocols to an open, standardized approach for power system communication. Initially focused on intra-substation communications, IEC 61850 has evolved substantially over the past two decades to address broader power system integration challenges.
The evolution of IEC 61850 can be traced through several key editions. The first edition, published in 2003-2004, established the foundational architecture and communication services. The second edition (2010-2012) expanded functionality with enhanced security features and engineering processes. The most recent third edition has further refined the standard to accommodate emerging technologies and use cases in modern power systems.
A primary objective of IEC 61850 is to achieve vendor-independent interoperability among intelligent electronic devices (IEDs) in substations. This interoperability extends beyond basic data exchange to include configuration, engineering, and maintenance processes. By standardizing these aspects, IEC 61850 significantly reduces integration complexity and lifecycle costs of substation automation systems.
Another critical objective is the future-proofing of communication infrastructures. The standard's abstract data model and service definitions are deliberately separated from specific communication technologies, allowing implementations to evolve with advancing communication technologies without requiring fundamental redesign of the automation system.
In the context of Solid-State Transformers (SSTs), IEC 61850 aims to provide a standardized framework for integrating these advanced power electronic devices into the broader grid infrastructure. SSTs represent a paradigm shift in power transformation technology, replacing conventional electromagnetic transformers with semiconductor-based solutions that offer enhanced control capabilities and efficiency.
The standard's evolution now specifically addresses time synchronization requirements, which are crucial for precise coordination of SST operations and for maintaining accurate cybersecurity logs. As power systems become increasingly distributed and digitalized, maintaining temporal coherence across the network becomes essential for both operational reliability and security monitoring.
Looking forward, IEC 61850 continues to evolve toward supporting more distributed energy resources, enhanced cybersecurity measures, and integration with broader IT/OT systems. The standard's technical committees are actively working on extensions to address emerging requirements in grid-edge technologies, including the specific communication and control needs of advanced power electronic devices like SSTs.
The evolution of IEC 61850 can be traced through several key editions. The first edition, published in 2003-2004, established the foundational architecture and communication services. The second edition (2010-2012) expanded functionality with enhanced security features and engineering processes. The most recent third edition has further refined the standard to accommodate emerging technologies and use cases in modern power systems.
A primary objective of IEC 61850 is to achieve vendor-independent interoperability among intelligent electronic devices (IEDs) in substations. This interoperability extends beyond basic data exchange to include configuration, engineering, and maintenance processes. By standardizing these aspects, IEC 61850 significantly reduces integration complexity and lifecycle costs of substation automation systems.
Another critical objective is the future-proofing of communication infrastructures. The standard's abstract data model and service definitions are deliberately separated from specific communication technologies, allowing implementations to evolve with advancing communication technologies without requiring fundamental redesign of the automation system.
In the context of Solid-State Transformers (SSTs), IEC 61850 aims to provide a standardized framework for integrating these advanced power electronic devices into the broader grid infrastructure. SSTs represent a paradigm shift in power transformation technology, replacing conventional electromagnetic transformers with semiconductor-based solutions that offer enhanced control capabilities and efficiency.
The standard's evolution now specifically addresses time synchronization requirements, which are crucial for precise coordination of SST operations and for maintaining accurate cybersecurity logs. As power systems become increasingly distributed and digitalized, maintaining temporal coherence across the network becomes essential for both operational reliability and security monitoring.
Looking forward, IEC 61850 continues to evolve toward supporting more distributed energy resources, enhanced cybersecurity measures, and integration with broader IT/OT systems. The standard's technical committees are actively working on extensions to address emerging requirements in grid-edge technologies, including the specific communication and control needs of advanced power electronic devices like SSTs.
Market Demand for Secure Substation Communication
The global market for secure substation communication systems is experiencing robust growth, driven by the increasing digitalization of power grids and the rising concerns about cybersecurity threats to critical infrastructure. The Smart Solid-State Transformer (SST) technology represents a significant advancement in grid modernization, requiring sophisticated communication protocols and security measures.
Industry analysts project that the global market for substation automation, which includes secure communication systems, will reach approximately $50 billion by 2027, with a compound annual growth rate exceeding 6%. This growth is particularly pronounced in regions investing heavily in smart grid infrastructure, such as North America, Europe, and parts of Asia-Pacific.
The demand for IEC 61850-compliant communication systems has seen a marked increase as utilities worldwide recognize the benefits of standardized protocols for interoperability and enhanced grid management. Market research indicates that over 70% of new substation installations now specify IEC 61850 compatibility as a requirement, reflecting its growing industry acceptance.
Time synchronization technologies, essential for precise event correlation and protection functions in substations, are witnessing increased adoption. The market for precision timing solutions in power systems is expanding at nearly 8% annually, with particular emphasis on solutions that can maintain synchronization accuracy under adverse network conditions or cyber attacks.
Cybersecurity concerns have become a primary market driver following several high-profile attacks on power infrastructure. Utility companies are allocating larger portions of their technology budgets to security measures, with spending on substation cybersecurity solutions growing at double-digit rates in many markets. This trend is reinforced by regulatory pressures, as governments worldwide implement stricter compliance requirements for critical infrastructure protection.
The logging and monitoring segment shows significant growth potential, with utilities seeking comprehensive solutions that can provide forensic capabilities for security incidents while supporting operational diagnostics. The market for advanced logging systems with secure storage and tamper-evident features is expected to double within the next five years.
Regional market analysis reveals varying adoption rates, with developed economies leading in implementation but emerging markets showing faster growth rates as they leapfrog older technologies in new infrastructure deployments. North America currently represents the largest market share due to its aggressive grid modernization initiatives and stringent regulatory framework.
Customer requirements are evolving toward integrated solutions that address both operational efficiency and security concerns, creating opportunities for vendors who can deliver comprehensive platforms that incorporate IEC 61850 compliance, robust time synchronization, and advanced security logging capabilities within SST implementations.
Industry analysts project that the global market for substation automation, which includes secure communication systems, will reach approximately $50 billion by 2027, with a compound annual growth rate exceeding 6%. This growth is particularly pronounced in regions investing heavily in smart grid infrastructure, such as North America, Europe, and parts of Asia-Pacific.
The demand for IEC 61850-compliant communication systems has seen a marked increase as utilities worldwide recognize the benefits of standardized protocols for interoperability and enhanced grid management. Market research indicates that over 70% of new substation installations now specify IEC 61850 compatibility as a requirement, reflecting its growing industry acceptance.
Time synchronization technologies, essential for precise event correlation and protection functions in substations, are witnessing increased adoption. The market for precision timing solutions in power systems is expanding at nearly 8% annually, with particular emphasis on solutions that can maintain synchronization accuracy under adverse network conditions or cyber attacks.
Cybersecurity concerns have become a primary market driver following several high-profile attacks on power infrastructure. Utility companies are allocating larger portions of their technology budgets to security measures, with spending on substation cybersecurity solutions growing at double-digit rates in many markets. This trend is reinforced by regulatory pressures, as governments worldwide implement stricter compliance requirements for critical infrastructure protection.
The logging and monitoring segment shows significant growth potential, with utilities seeking comprehensive solutions that can provide forensic capabilities for security incidents while supporting operational diagnostics. The market for advanced logging systems with secure storage and tamper-evident features is expected to double within the next five years.
Regional market analysis reveals varying adoption rates, with developed economies leading in implementation but emerging markets showing faster growth rates as they leapfrog older technologies in new infrastructure deployments. North America currently represents the largest market share due to its aggressive grid modernization initiatives and stringent regulatory framework.
Customer requirements are evolving toward integrated solutions that address both operational efficiency and security concerns, creating opportunities for vendors who can deliver comprehensive platforms that incorporate IEC 61850 compliance, robust time synchronization, and advanced security logging capabilities within SST implementations.
Time Synchronization Challenges in SST
Time synchronization in Solid-State Transformers (SSTs) presents significant technical challenges due to the complex integration of power electronics, digital control systems, and communication networks. The primary challenge stems from the need for precise time alignment across multiple SST modules operating at different voltage levels and potentially distributed across wide geographical areas.
The IEC 61850 standard, which governs communication networks and systems for power utility automation, requires time synchronization accuracy in the microsecond range for critical operations. However, achieving this level of precision in SST environments is complicated by electromagnetic interference generated by high-frequency switching operations, which can disrupt timing signals and introduce jitter in synchronization protocols.
Traditional time synchronization methods such as Network Time Protocol (NTP) typically provide millisecond-level accuracy, which proves insufficient for the real-time control requirements of SSTs. More advanced protocols like Precision Time Protocol (PTP/IEEE 1588) can theoretically achieve sub-microsecond accuracy but face implementation challenges in power electronic environments due to asymmetric network delays and hardware timestamp limitations.
The distributed nature of SST deployments introduces additional synchronization complexities. When multiple SST modules are cascaded or networked across substations, maintaining consistent time references becomes increasingly difficult due to propagation delays and network congestion. This challenge is particularly acute in microgrid applications where SSTs must coordinate with various distributed energy resources.
Cybersecurity requirements further complicate time synchronization efforts. Secure time synchronization protocols must be resistant to spoofing and manipulation attacks, as compromised timing could lead to destabilization of the power system. However, adding security layers often introduces additional latency and processing overhead, creating a technical trade-off between security and synchronization precision.
Hardware limitations present another significant challenge. The computing platforms used in SST controllers may have limited resources for implementing sophisticated time synchronization algorithms. Additionally, the clock drift characteristics of oscillators used in these systems can vary with temperature and aging, requiring continuous calibration and compensation mechanisms.
Environmental factors also impact synchronization performance. Temperature variations, vibration, and electromagnetic fields present in power system environments can affect the stability of local oscillators, leading to increased drift rates and synchronization errors over time. These effects are particularly pronounced in outdoor installations where environmental conditions fluctuate significantly.
The IEC 61850 standard, which governs communication networks and systems for power utility automation, requires time synchronization accuracy in the microsecond range for critical operations. However, achieving this level of precision in SST environments is complicated by electromagnetic interference generated by high-frequency switching operations, which can disrupt timing signals and introduce jitter in synchronization protocols.
Traditional time synchronization methods such as Network Time Protocol (NTP) typically provide millisecond-level accuracy, which proves insufficient for the real-time control requirements of SSTs. More advanced protocols like Precision Time Protocol (PTP/IEEE 1588) can theoretically achieve sub-microsecond accuracy but face implementation challenges in power electronic environments due to asymmetric network delays and hardware timestamp limitations.
The distributed nature of SST deployments introduces additional synchronization complexities. When multiple SST modules are cascaded or networked across substations, maintaining consistent time references becomes increasingly difficult due to propagation delays and network congestion. This challenge is particularly acute in microgrid applications where SSTs must coordinate with various distributed energy resources.
Cybersecurity requirements further complicate time synchronization efforts. Secure time synchronization protocols must be resistant to spoofing and manipulation attacks, as compromised timing could lead to destabilization of the power system. However, adding security layers often introduces additional latency and processing overhead, creating a technical trade-off between security and synchronization precision.
Hardware limitations present another significant challenge. The computing platforms used in SST controllers may have limited resources for implementing sophisticated time synchronization algorithms. Additionally, the clock drift characteristics of oscillators used in these systems can vary with temperature and aging, requiring continuous calibration and compensation mechanisms.
Environmental factors also impact synchronization performance. Temperature variations, vibration, and electromagnetic fields present in power system environments can affect the stability of local oscillators, leading to increased drift rates and synchronization errors over time. These effects are particularly pronounced in outdoor installations where environmental conditions fluctuate significantly.
Current Time Synchronization Solutions for SST
01 IEC 61850 Time Synchronization Protocols
Time synchronization protocols are essential for maintaining accurate timing in IEC 61850-based power systems. These protocols ensure that all devices in the network operate with a unified time reference, which is critical for event sequencing, data logging, and coordinated operations. Various synchronization methods including PTP (Precision Time Protocol), NTP (Network Time Protocol), and SNTP are implemented to achieve precise time alignment across distributed energy systems, enhancing the reliability of protection and control functions.- IEC 61850 Time Synchronization Protocols: Time synchronization is critical in IEC 61850-based power systems to ensure accurate event sequencing and data correlation. Various protocols like PTP (Precision Time Protocol) and NTP (Network Time Protocol) are implemented to maintain precise timing across distributed substations and control systems. These protocols help maintain millisecond or microsecond-level accuracy required for proper operation of protection and control functions in smart grid environments.
- Cybersecurity for IEC 61850 Communication Networks: Securing IEC 61850 communication networks involves implementing multiple layers of protection against cyber threats. This includes encryption of data transmissions, authentication mechanisms for devices and users, network segmentation, and intrusion detection systems. These security measures help protect critical infrastructure from unauthorized access while maintaining the performance requirements of power system automation applications.
- Secure Logging and Audit Trails in IEC 61850 Systems: Secure logging mechanisms in IEC 61850 systems provide tamper-evident records of system events, user actions, and security incidents. These logs capture time-synchronized data about access attempts, configuration changes, and communication anomalies. Implementing cryptographically secured audit trails ensures the integrity of log data for forensic analysis and compliance with regulatory requirements in critical infrastructure protection.
- Time-Synchronized Event Analysis for Power Systems: Time-synchronized event analysis enables accurate correlation of events across distributed power system components. By maintaining precise timing information in logs and event records, operators can reconstruct the sequence of events during disturbances or cyber incidents. This capability is essential for root cause analysis, system protection coordination, and identifying potential security breaches in IEC 61850 environments.
- Integration of Time Synchronization with Security Monitoring: Integrating precise time synchronization with security monitoring systems enhances threat detection capabilities in IEC 61850 networks. This integration allows security systems to correlate events across multiple devices and identify timing-based attacks such as replay attacks or time manipulation attempts. Advanced monitoring solutions use synchronized timestamps to detect anomalies in communication patterns and system behavior that may indicate cybersecurity threats.
02 Cybersecurity for IEC 61850 Communication Networks
Securing IEC 61850 communication networks involves implementing multiple layers of protection against cyber threats. This includes authentication mechanisms, encryption of data transmissions, access control systems, and intrusion detection capabilities. Security measures are designed to protect against unauthorized access, data manipulation, and denial-of-service attacks while maintaining the performance requirements of power system operations. Advanced security frameworks incorporate threat intelligence and adaptive defense mechanisms to address evolving cybersecurity challenges in smart grid environments.Expand Specific Solutions03 Secure Event Logging and Audit Trails
Secure event logging systems capture and store critical operational data and security events in IEC 61850 environments. These systems implement tamper-resistant logging mechanisms that ensure the integrity and confidentiality of recorded information. Comprehensive audit trails track user activities, system changes, and security incidents, providing forensic evidence for incident investigation and compliance verification. Advanced logging architectures incorporate distributed storage, cryptographic validation, and automated analysis to detect anomalous patterns that might indicate security breaches.Expand Specific Solutions04 Time-Based Security Mechanisms
Time-based security mechanisms leverage precise synchronization to enhance protection of IEC 61850 systems. These include time-stamped authentication tokens, time-limited access credentials, and temporal correlation of security events across distributed networks. By incorporating accurate timing information into security protocols, systems can detect replay attacks, timing anomalies, and synchronization manipulations that might indicate malicious activity. Time-based security approaches also enable more effective coordination of security responses and more accurate forensic analysis following security incidents.Expand Specific Solutions05 Integrated Security Monitoring and Management
Integrated security monitoring systems provide comprehensive oversight of IEC 61850 networks by correlating time synchronization data with security logs and operational parameters. These systems implement continuous monitoring of network traffic, device status, and timing accuracy to detect potential security breaches or operational anomalies. Security management frameworks incorporate automated response capabilities, centralized policy enforcement, and adaptive security measures that adjust protection levels based on threat intelligence and system status. Advanced implementations leverage machine learning algorithms to identify subtle patterns indicating potential security threats.Expand Specific Solutions
Key Industry Players in Substation Automation
The IEC 61850 time synchronization and cybersecurity communications landscape for Solid-State Transformers (SST) is currently in a growth phase, with an estimated market value exceeding $500 million and expanding at 15% annually. The technology is approaching maturity, with key players demonstrating varying levels of implementation sophistication. State Grid Corp. of China and its research institutes lead in large-scale deployment, while NARI Technology and NR Electric have developed comprehensive solutions integrating time synchronization with cybersecurity logging. Western companies like Hitachi Energy and ABB Group offer complementary technologies with strong security features. Academic institutions including North China Electric Power University and Peking University contribute significant research advancements, creating a competitive ecosystem balancing established utility requirements with emerging security standards.
Hitachi Energy Ltd.
Technical Solution: Hitachi Energy has developed an advanced IEC 61850-compliant solution specifically designed for Solid State Transformer (SST) applications. Their system features a distributed time synchronization architecture that combines IEEE 1588v2 PTP with GNSS-based timing to achieve sub-microsecond accuracy across SST networks. This precision is critical for the high-frequency switching operations in SSTs. Their cybersecurity framework implements a defense-in-depth approach with comprehensive logging capabilities that capture both operational and security events. The logging system employs cryptographic signing and tamper-evident storage to ensure log integrity, with timestamps synchronized to the global time reference. Hitachi Energy's communication solution for SSTs leverages IEC 61850 GOOSE messaging for critical control functions and MMS for configuration and monitoring, with extensions to support the unique requirements of power electronic interfaces in SSTs. Their implementation includes specialized data models for representing SST-specific functions within the IEC 61850 object model[2][4].
Strengths: Extensive experience with global utility deployments; strong integration with existing substation automation systems; advanced cybersecurity features with international compliance. Weaknesses: Solutions may require significant customization for different regional grid requirements; potentially higher implementation costs compared to local vendors.
China Electric Power Research Institute Ltd.
Technical Solution: China Electric Power Research Institute has developed comprehensive IEC 61850-based solutions for smart substations with advanced time synchronization mechanisms. Their approach integrates IEEE 1588v2 Precision Time Protocol (PTP) with IEC 61850 communication frameworks to achieve microsecond-level synchronization accuracy across substation automation systems. The institute has created a multi-layered cybersecurity architecture specifically for Solid State Transformers (SSTs) that includes real-time security event logging and correlation analysis. Their system implements secure logging mechanisms that capture and store critical events with precise timestamps, enabling forensic analysis during security incidents. The institute has also developed specialized communication protocols that optimize the unique characteristics of SSTs while maintaining compliance with IEC 61850 standards, allowing for seamless integration with existing power grid infrastructure while supporting the advanced control requirements of SSTs[1][3].
Strengths: Strong integration of IEC 61850 with existing Chinese grid infrastructure; extensive field testing and deployment experience; deep understanding of national cybersecurity requirements. Weaknesses: Solutions may be optimized primarily for Chinese market specifications; potential interoperability challenges with international vendors' implementations.
Critical Security Logging Technologies
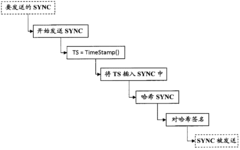
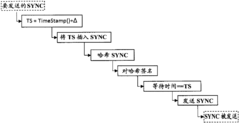
Secure clock synchronization
PatentActiveCN102472998A
Innovation
- By pre-preparing and signing the timestamps of synchronization messages in the master clock device and transmitting them before the scheduled transmission time, low-priority queues and blocking intervals are used to ensure that synchronization messages are not interfered with by low-priority messages during transmission. Ensure timestamp security.
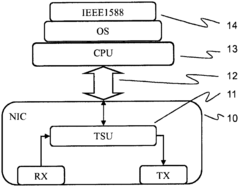
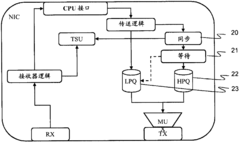
Time setting device for digital substation
PatentInactiveCN101650548A
Innovation
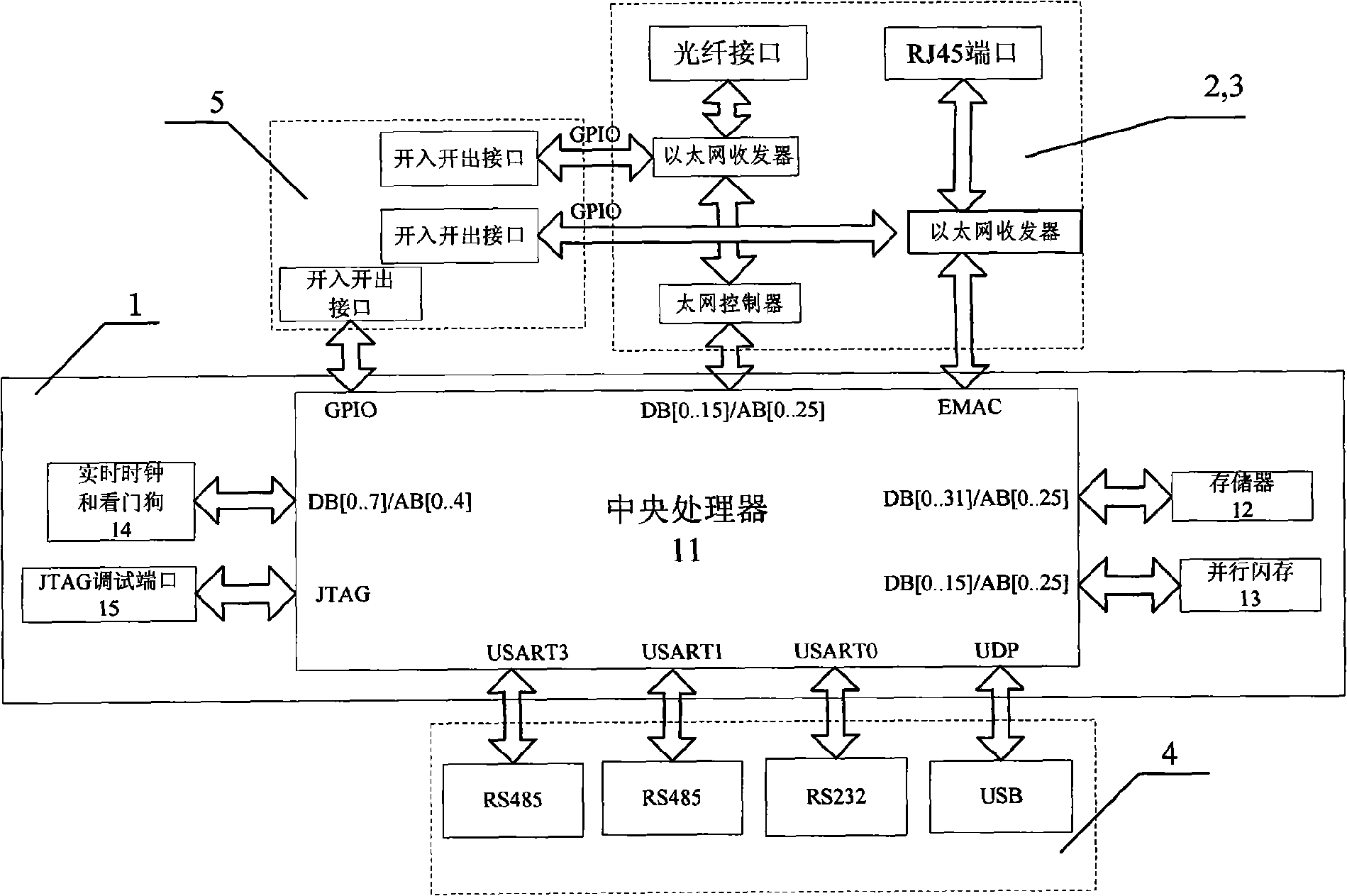
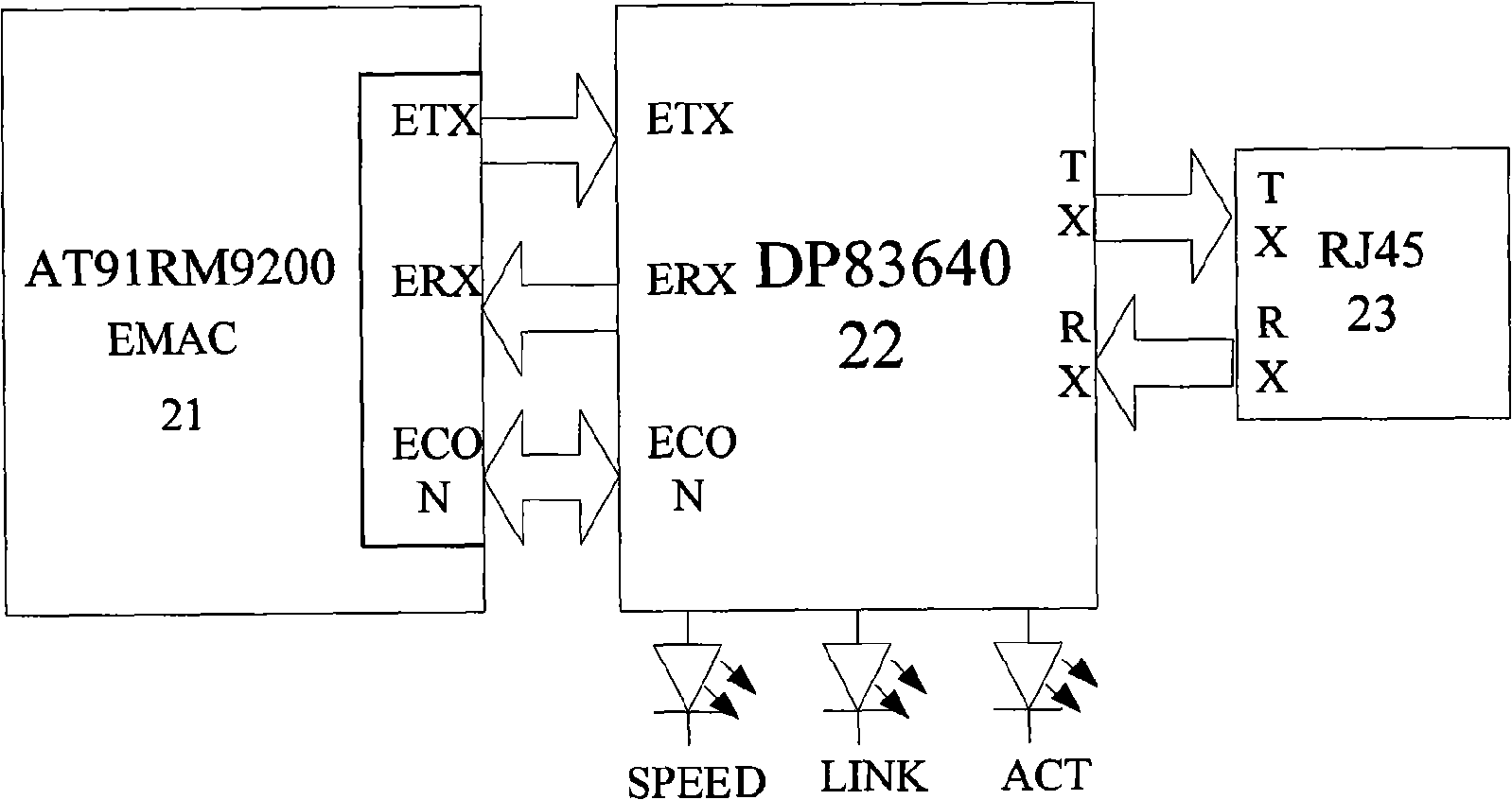
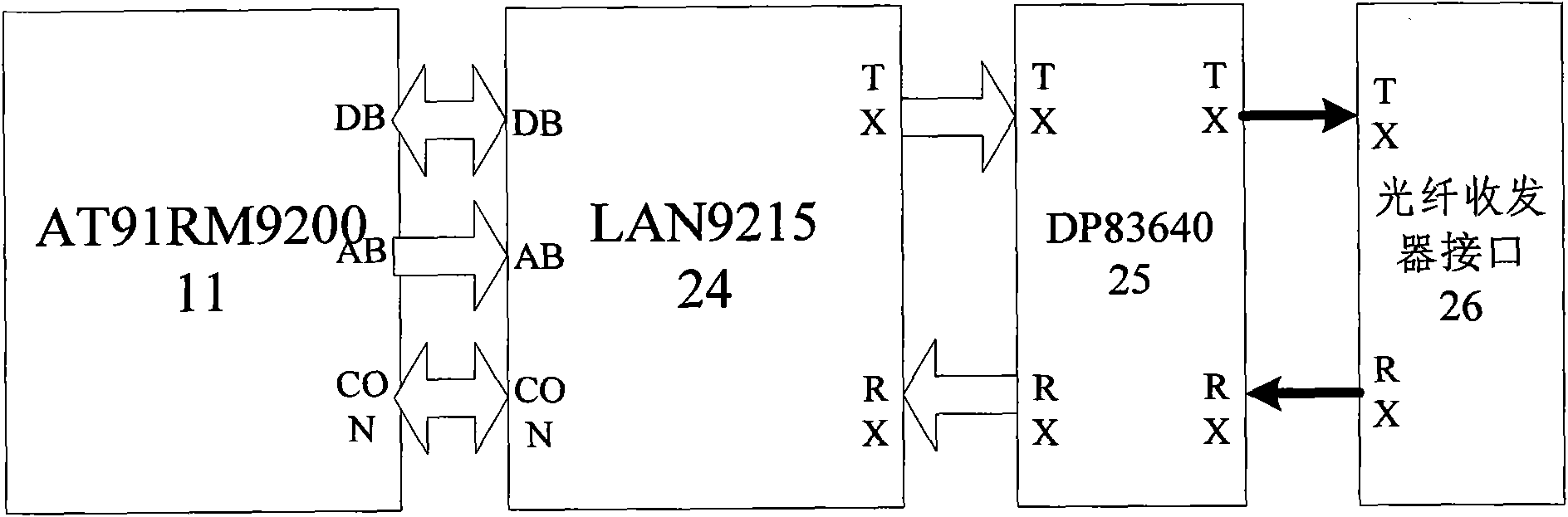
- Design a digital substation time synchronization device including a core processing module, a PTP event processing module, an Ethernet communication interface module, a serial communication interface module and a switching input and output module. It uses the central processor AT91RM9200 and related hardware components to implement the IEEE1588 standard. High-precision clock synchronization, supports Ethernet and serial communications, and provides flexible configuration and scalability.
Regulatory Compliance Requirements
The implementation of IEC 61850, time synchronization, and cybersecurity logging in Solid-State Transformers (SSTs) must adhere to a complex framework of regulatory requirements across multiple jurisdictions. These compliance mandates are essential for ensuring system reliability, security, and interoperability in critical power infrastructure deployments.
NERC CIP (North American Electric Reliability Corporation Critical Infrastructure Protection) standards represent a cornerstone of regulatory compliance for power systems in North America. Specifically, NERC CIP-007-6 mandates comprehensive security event monitoring and logging capabilities, while CIP-005-5 requires robust electronic security perimeters with appropriate access controls. For SST implementations utilizing IEC 61850, these requirements necessitate precise integration of security logging mechanisms with communication protocols.
The European Network and Information Security Directive (NIS Directive) imposes additional compliance requirements for operators of essential services in the energy sector across EU member states. This directive specifically addresses cybersecurity measures, including requirements for incident reporting and security monitoring that directly impact how time synchronization and logging must be implemented in SST systems utilizing IEC 61850 communications.
IEEE 1588 Precision Time Protocol (PTP) compliance is critical for time synchronization aspects of SST implementations. The standard provides specifications for precise time synchronization across networked devices, with power industry applications requiring adherence to the IEEE C37.238 Power Profile, which defines specific parameters for power system applications requiring sub-microsecond accuracy.
IEC 62351 series standards specifically address security aspects of power system communication protocols, including IEC 61850. These standards mandate specific security controls for authentication, encryption, and key management that must be incorporated into any compliant implementation. Particularly, IEC 62351-6 addresses security for IEC 61850 profiles, with explicit requirements for securing GOOSE and SV communications that are essential for SST operations.
The International Organization for Standardization (ISO) and International Electrotechnical Commission (IEC) joint standard ISO/IEC 27001 provides an overarching framework for information security management systems. For SST implementations, compliance with this standard requires comprehensive security controls covering aspects of time synchronization and logging to ensure data integrity and confidentiality.
Regional grid codes and utility-specific requirements introduce additional compliance considerations that vary by deployment location. These often include specific mandates for time synchronization accuracy, event logging retention periods, and cybersecurity incident reporting that must be addressed in SST implementations utilizing IEC 61850 communications.
NERC CIP (North American Electric Reliability Corporation Critical Infrastructure Protection) standards represent a cornerstone of regulatory compliance for power systems in North America. Specifically, NERC CIP-007-6 mandates comprehensive security event monitoring and logging capabilities, while CIP-005-5 requires robust electronic security perimeters with appropriate access controls. For SST implementations utilizing IEC 61850, these requirements necessitate precise integration of security logging mechanisms with communication protocols.
The European Network and Information Security Directive (NIS Directive) imposes additional compliance requirements for operators of essential services in the energy sector across EU member states. This directive specifically addresses cybersecurity measures, including requirements for incident reporting and security monitoring that directly impact how time synchronization and logging must be implemented in SST systems utilizing IEC 61850 communications.
IEEE 1588 Precision Time Protocol (PTP) compliance is critical for time synchronization aspects of SST implementations. The standard provides specifications for precise time synchronization across networked devices, with power industry applications requiring adherence to the IEEE C37.238 Power Profile, which defines specific parameters for power system applications requiring sub-microsecond accuracy.
IEC 62351 series standards specifically address security aspects of power system communication protocols, including IEC 61850. These standards mandate specific security controls for authentication, encryption, and key management that must be incorporated into any compliant implementation. Particularly, IEC 62351-6 addresses security for IEC 61850 profiles, with explicit requirements for securing GOOSE and SV communications that are essential for SST operations.
The International Organization for Standardization (ISO) and International Electrotechnical Commission (IEC) joint standard ISO/IEC 27001 provides an overarching framework for information security management systems. For SST implementations, compliance with this standard requires comprehensive security controls covering aspects of time synchronization and logging to ensure data integrity and confidentiality.
Regional grid codes and utility-specific requirements introduce additional compliance considerations that vary by deployment location. These often include specific mandates for time synchronization accuracy, event logging retention periods, and cybersecurity incident reporting that must be addressed in SST implementations utilizing IEC 61850 communications.
Interoperability Testing Methodologies
Interoperability testing methodologies for IEC 61850, time synchronization, and cybersecurity logs in Solid-State Transformers (SSTs) require systematic approaches to ensure seamless integration across diverse vendor implementations. These methodologies must verify that different components can communicate effectively while maintaining security standards.
The conformance testing approach forms the foundation of interoperability assessment, validating that implementations adhere to the IEC 61850 standard specifications. This includes verification of data models, service interfaces, and communication protocols. For SST applications, special attention must be given to the Manufacturing Message Specification (MMS), Generic Object Oriented Substation Events (GOOSE), and Sampled Values (SV) protocols.
Interoperability test beds represent a critical infrastructure component for comprehensive evaluation. These controlled environments simulate real-world conditions while allowing for detailed monitoring and analysis of interactions between different vendor implementations. Test beds should incorporate hardware-in-the-loop capabilities to evaluate SST control systems under various operational scenarios, including fault conditions and cybersecurity incidents.
Time synchronization testing methodologies focus on evaluating the precision and reliability of synchronization mechanisms. This includes assessment of IEEE 1588 Precision Time Protocol (PTP) implementations, verification of synchronization accuracy under network stress conditions, and evaluation of timing resilience against spoofing attacks. For SSTs, time synchronization is particularly crucial for coordinated control actions and accurate event sequencing in security logs.
Security log interoperability testing examines the consistency and completeness of log formats across different system components. Methodologies should verify that security events are properly captured, timestamped, and formatted according to standards like Syslog or Common Event Format (CEF). This ensures that security information and event management (SIEM) systems can effectively aggregate and analyze logs from diverse SST components.
Cross-vendor testing protocols establish standardized procedures for evaluating interoperability between equipment from different manufacturers. These protocols define test cases, expected outcomes, and evaluation criteria. For SST applications, cross-vendor testing should address both normal operation scenarios and edge cases that might expose interoperability issues, particularly during fault conditions or cyber incidents.
Certification programs provide formal validation of interoperability compliance. These programs typically involve independent testing laboratories that verify implementations against established criteria. For IEC 61850 in SST applications, certification should encompass communication protocols, time synchronization accuracy, and security log formats to ensure comprehensive interoperability across the ecosystem.
The conformance testing approach forms the foundation of interoperability assessment, validating that implementations adhere to the IEC 61850 standard specifications. This includes verification of data models, service interfaces, and communication protocols. For SST applications, special attention must be given to the Manufacturing Message Specification (MMS), Generic Object Oriented Substation Events (GOOSE), and Sampled Values (SV) protocols.
Interoperability test beds represent a critical infrastructure component for comprehensive evaluation. These controlled environments simulate real-world conditions while allowing for detailed monitoring and analysis of interactions between different vendor implementations. Test beds should incorporate hardware-in-the-loop capabilities to evaluate SST control systems under various operational scenarios, including fault conditions and cybersecurity incidents.
Time synchronization testing methodologies focus on evaluating the precision and reliability of synchronization mechanisms. This includes assessment of IEEE 1588 Precision Time Protocol (PTP) implementations, verification of synchronization accuracy under network stress conditions, and evaluation of timing resilience against spoofing attacks. For SSTs, time synchronization is particularly crucial for coordinated control actions and accurate event sequencing in security logs.
Security log interoperability testing examines the consistency and completeness of log formats across different system components. Methodologies should verify that security events are properly captured, timestamped, and formatted according to standards like Syslog or Common Event Format (CEF). This ensures that security information and event management (SIEM) systems can effectively aggregate and analyze logs from diverse SST components.
Cross-vendor testing protocols establish standardized procedures for evaluating interoperability between equipment from different manufacturers. These protocols define test cases, expected outcomes, and evaluation criteria. For SST applications, cross-vendor testing should address both normal operation scenarios and edge cases that might expose interoperability issues, particularly during fault conditions or cyber incidents.
Certification programs provide formal validation of interoperability compliance. These programs typically involve independent testing laboratories that verify implementations against established criteria. For IEC 61850 in SST applications, certification should encompass communication protocols, time synchronization accuracy, and security log formats to ensure comprehensive interoperability across the ecosystem.
Unlock deeper insights with Patsnap Eureka Quick Research — get a full tech report to explore trends and direct your research. Try now!
Generate Your Research Report Instantly with AI Agent
Supercharge your innovation with Patsnap Eureka AI Agent Platform!