Building a secure boot chain on RISC-V: practical steps
AUG 25, 20259 MIN READ
Generate Your Research Report Instantly with AI Agent
Patsnap Eureka helps you evaluate technical feasibility & market potential.
RISC-V Secure Boot Background and Objectives
Secure boot technology has evolved significantly over the past decade as a critical component of hardware security architecture. RISC-V, as an open instruction set architecture (ISA), presents both unique opportunities and challenges in implementing robust secure boot mechanisms. The evolution of secure boot began with simple ROM-based solutions and has progressed to complex chains of trust involving multiple stages of verification and authentication.
The RISC-V ecosystem has experienced remarkable growth since its inception at UC Berkeley in 2010, transitioning from an academic project to a globally recognized standard for processor design. This open architecture allows unprecedented flexibility in implementing security features, but also requires careful consideration of security implications across the entire boot process.
The primary objective of secure boot in RISC-V systems is to establish and maintain a chain of trust from power-on through the entire boot sequence, ensuring that only authenticated and unmodified code executes on the system. This involves cryptographic verification of each software component before execution, creating an unbroken chain of validated software from the initial boot ROM to the operating system.
Current industry trends indicate growing adoption of RISC-V in security-sensitive applications, including IoT devices, automotive systems, and enterprise infrastructure. This expansion necessitates standardized approaches to secure boot implementation that can be adapted across diverse hardware configurations while maintaining strong security guarantees.
The technical landscape for RISC-V secure boot encompasses several key elements: hardware root of trust, immutable boot ROM, secure key storage, cryptographic acceleration, and tamper resistance mechanisms. These components must work in concert to prevent various attack vectors, including physical tampering, fault injection, and software exploitation attempts.
Recent developments in the RISC-V security extensions, particularly the Physical Memory Protection (PMP) and Trusted Execution Environment (TEE) specifications, provide foundational building blocks for implementing secure boot. However, practical implementation guidelines that bridge theoretical security models with real-world deployment scenarios remain underdeveloped.
The goal of this technical research is to establish a comprehensive framework for implementing secure boot chains in RISC-V systems, addressing both theoretical security requirements and practical implementation challenges. This includes identifying optimal cryptographic algorithms, key management strategies, and verification mechanisms suitable for various resource constraints and threat models.
By examining the evolution of secure boot technologies and their application to RISC-V architecture, this research aims to provide actionable insights for hardware designers, firmware developers, and system architects seeking to implement robust security measures in next-generation RISC-V systems.
The RISC-V ecosystem has experienced remarkable growth since its inception at UC Berkeley in 2010, transitioning from an academic project to a globally recognized standard for processor design. This open architecture allows unprecedented flexibility in implementing security features, but also requires careful consideration of security implications across the entire boot process.
The primary objective of secure boot in RISC-V systems is to establish and maintain a chain of trust from power-on through the entire boot sequence, ensuring that only authenticated and unmodified code executes on the system. This involves cryptographic verification of each software component before execution, creating an unbroken chain of validated software from the initial boot ROM to the operating system.
Current industry trends indicate growing adoption of RISC-V in security-sensitive applications, including IoT devices, automotive systems, and enterprise infrastructure. This expansion necessitates standardized approaches to secure boot implementation that can be adapted across diverse hardware configurations while maintaining strong security guarantees.
The technical landscape for RISC-V secure boot encompasses several key elements: hardware root of trust, immutable boot ROM, secure key storage, cryptographic acceleration, and tamper resistance mechanisms. These components must work in concert to prevent various attack vectors, including physical tampering, fault injection, and software exploitation attempts.
Recent developments in the RISC-V security extensions, particularly the Physical Memory Protection (PMP) and Trusted Execution Environment (TEE) specifications, provide foundational building blocks for implementing secure boot. However, practical implementation guidelines that bridge theoretical security models with real-world deployment scenarios remain underdeveloped.
The goal of this technical research is to establish a comprehensive framework for implementing secure boot chains in RISC-V systems, addressing both theoretical security requirements and practical implementation challenges. This includes identifying optimal cryptographic algorithms, key management strategies, and verification mechanisms suitable for various resource constraints and threat models.
By examining the evolution of secure boot technologies and their application to RISC-V architecture, this research aims to provide actionable insights for hardware designers, firmware developers, and system architects seeking to implement robust security measures in next-generation RISC-V systems.
Market Demand Analysis for RISC-V Security Solutions
The RISC-V architecture has experienced significant market growth in recent years, with increasing adoption across various sectors including IoT, embedded systems, data centers, and automotive applications. This expansion has created a substantial demand for robust security solutions, particularly secure boot implementations. Market research indicates that the global RISC-V market is projected to grow at a compound annual growth rate exceeding 35% through 2027, with security features being a critical driver of this adoption.
Security concerns have become paramount as RISC-V deployments expand into sensitive applications. A recent industry survey revealed that over 70% of organizations considering RISC-V implementation cite security as a primary concern, with secure boot capabilities specifically mentioned by 65% of respondents. This heightened focus on security stems from the increasing frequency and sophistication of firmware-level attacks across all computing platforms.
The market for RISC-V security solutions is being driven by several key factors. First, the open-source nature of RISC-V creates both opportunities and challenges for security implementation, necessitating standardized approaches to secure boot chains. Second, regulatory requirements in sectors such as automotive (ISO 26262), industrial IoT (IEC 62443), and healthcare are mandating verifiable security measures at the hardware level, including secure boot processes.
Enterprise customers represent a significant segment of demand, particularly in edge computing and data center applications where RISC-V is gaining traction. These customers require comprehensive security solutions that integrate seamlessly with existing infrastructure while providing protection against increasingly sophisticated attack vectors.
The financial services sector has emerged as another key market for secure RISC-V implementations, with requirements for tamper-resistant hardware and secure execution environments. Government and defense sectors also represent substantial market opportunities, driven by requirements for supply chain security and protection against nation-state threats.
Geographically, North America currently leads in demand for secure RISC-V solutions, followed by Europe and Asia-Pacific. However, the fastest growth is anticipated in the Asia-Pacific region, particularly in China, where significant investments in domestic RISC-V development are occurring partly due to technology sovereignty concerns.
Market analysis indicates that customers are willing to pay premium prices for RISC-V implementations with comprehensive security features, including robust secure boot chains. This price premium ranges from 15-30% depending on the application domain and security requirements, representing a significant revenue opportunity for solution providers who can deliver effective, standards-compliant secure boot implementations.
Security concerns have become paramount as RISC-V deployments expand into sensitive applications. A recent industry survey revealed that over 70% of organizations considering RISC-V implementation cite security as a primary concern, with secure boot capabilities specifically mentioned by 65% of respondents. This heightened focus on security stems from the increasing frequency and sophistication of firmware-level attacks across all computing platforms.
The market for RISC-V security solutions is being driven by several key factors. First, the open-source nature of RISC-V creates both opportunities and challenges for security implementation, necessitating standardized approaches to secure boot chains. Second, regulatory requirements in sectors such as automotive (ISO 26262), industrial IoT (IEC 62443), and healthcare are mandating verifiable security measures at the hardware level, including secure boot processes.
Enterprise customers represent a significant segment of demand, particularly in edge computing and data center applications where RISC-V is gaining traction. These customers require comprehensive security solutions that integrate seamlessly with existing infrastructure while providing protection against increasingly sophisticated attack vectors.
The financial services sector has emerged as another key market for secure RISC-V implementations, with requirements for tamper-resistant hardware and secure execution environments. Government and defense sectors also represent substantial market opportunities, driven by requirements for supply chain security and protection against nation-state threats.
Geographically, North America currently leads in demand for secure RISC-V solutions, followed by Europe and Asia-Pacific. However, the fastest growth is anticipated in the Asia-Pacific region, particularly in China, where significant investments in domestic RISC-V development are occurring partly due to technology sovereignty concerns.
Market analysis indicates that customers are willing to pay premium prices for RISC-V implementations with comprehensive security features, including robust secure boot chains. This price premium ranges from 15-30% depending on the application domain and security requirements, representing a significant revenue opportunity for solution providers who can deliver effective, standards-compliant secure boot implementations.
Current State and Challenges in RISC-V Secure Boot
The RISC-V architecture has gained significant momentum in recent years, yet its secure boot implementation remains in a developing state compared to more established architectures like ARM and x86. Currently, the RISC-V ecosystem faces several challenges in implementing robust secure boot chains, primarily due to its open and customizable nature which, while advantageous for innovation, creates complexity for standardized security implementations.
The RISC-V Foundation has made progress through the development of specifications like the RISC-V Physical Memory Protection (PMP) and the RISC-V Privileged Architecture, which provide foundational elements for secure boot implementations. However, these specifications are still evolving, and industry-wide adoption remains inconsistent across different implementations.
A significant challenge lies in the fragmentation of the RISC-V ecosystem. Unlike ARM or x86 architectures with centralized control over security features, RISC-V implementations vary widely across vendors, leading to inconsistent security capabilities. This fragmentation complicates the establishment of a standardized secure boot methodology that can be universally applied.
Hardware root of trust implementation represents another critical challenge. While RISC-V supports the concept of machine mode (M-mode) as the highest privilege level, many current implementations lack dedicated secure elements or hardware security modules that can serve as immutable anchors for the boot chain. This deficiency increases vulnerability to boot-time attacks and makes it difficult to establish an unbroken chain of trust.
Key management infrastructure for RISC-V secure boot remains underdeveloped. The ecosystem lacks standardized approaches for secure key storage, certificate management, and cryptographic operations essential for signature verification during the boot process. This gap forces implementers to develop custom solutions, increasing complexity and potential security vulnerabilities.
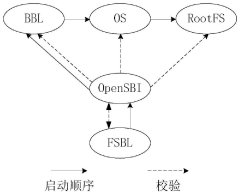
The absence of mature tooling and reference implementations further complicates secure boot development. While projects like OpenSBI (Supervisor Binary Interface) provide some building blocks, comprehensive frameworks and tools specifically designed for RISC-V secure boot remain limited, requiring significant expertise and resources to implement properly.
Attestation mechanisms, crucial for verifying the integrity of the boot process to external entities, are still in nascent stages for RISC-V. This limitation affects the architecture's suitability for applications requiring strong security guarantees, such as financial services or critical infrastructure.
Despite these challenges, the RISC-V community is actively working to address these gaps through initiatives like the RISC-V Security Standing Committee and collaborations with industry partners. The open nature of RISC-V also presents an opportunity to develop innovative security approaches that could potentially surpass traditional architectures in flexibility and robustness.
The RISC-V Foundation has made progress through the development of specifications like the RISC-V Physical Memory Protection (PMP) and the RISC-V Privileged Architecture, which provide foundational elements for secure boot implementations. However, these specifications are still evolving, and industry-wide adoption remains inconsistent across different implementations.
A significant challenge lies in the fragmentation of the RISC-V ecosystem. Unlike ARM or x86 architectures with centralized control over security features, RISC-V implementations vary widely across vendors, leading to inconsistent security capabilities. This fragmentation complicates the establishment of a standardized secure boot methodology that can be universally applied.
Hardware root of trust implementation represents another critical challenge. While RISC-V supports the concept of machine mode (M-mode) as the highest privilege level, many current implementations lack dedicated secure elements or hardware security modules that can serve as immutable anchors for the boot chain. This deficiency increases vulnerability to boot-time attacks and makes it difficult to establish an unbroken chain of trust.
Key management infrastructure for RISC-V secure boot remains underdeveloped. The ecosystem lacks standardized approaches for secure key storage, certificate management, and cryptographic operations essential for signature verification during the boot process. This gap forces implementers to develop custom solutions, increasing complexity and potential security vulnerabilities.
The absence of mature tooling and reference implementations further complicates secure boot development. While projects like OpenSBI (Supervisor Binary Interface) provide some building blocks, comprehensive frameworks and tools specifically designed for RISC-V secure boot remain limited, requiring significant expertise and resources to implement properly.
Attestation mechanisms, crucial for verifying the integrity of the boot process to external entities, are still in nascent stages for RISC-V. This limitation affects the architecture's suitability for applications requiring strong security guarantees, such as financial services or critical infrastructure.
Despite these challenges, the RISC-V community is actively working to address these gaps through initiatives like the RISC-V Security Standing Committee and collaborations with industry partners. The open nature of RISC-V also presents an opportunity to develop innovative security approaches that could potentially surpass traditional architectures in flexibility and robustness.
Current Secure Boot Implementation Approaches
01 Secure Boot Implementation for RISC-V Architecture
Secure boot mechanisms specifically designed for RISC-V architecture ensure that only authenticated code executes during the boot process. These implementations leverage RISC-V's open instruction set architecture to establish a chain of trust from boot ROM through various boot stages. The security features include verification of digital signatures, integrity checking of firmware components, and protection against unauthorized modifications to the boot sequence.- Secure Boot Implementation for RISC-V Architecture: Secure boot mechanisms specifically designed for RISC-V architecture provide a foundation for establishing a trusted execution environment. These implementations leverage the unique features of RISC-V processors to verify the integrity of boot code before execution. The process typically involves cryptographic verification of firmware components in a sequential chain, ensuring that only authenticated code is executed during the system startup process.
- Root of Trust and Key Management in RISC-V Systems: Establishing a hardware-based root of trust is essential for secure boot chains in RISC-V systems. This involves implementing secure key storage mechanisms and cryptographic modules that protect private keys used for signature verification. The root of trust serves as the foundation for the entire security architecture, enabling the verification of subsequent boot stages through a chain of trust that extends from hardware to the operating system.
- Secure Boot Verification Techniques: Various verification techniques are employed in RISC-V secure boot chains to ensure code integrity and authenticity. These include digital signature verification, hash-based authentication, and certificate validation. The verification process typically occurs at multiple stages of the boot sequence, with each stage verifying the next before transferring control, creating a chain of trust from the initial boot loader to the operating system.
- Secure Boot Protection Against Physical and Side-Channel Attacks: RISC-V secure boot implementations incorporate countermeasures against physical tampering and side-channel attacks. These protections include secure storage for cryptographic keys, memory encryption, and hardware-based isolation mechanisms. Additional security features may include anti-rollback protection to prevent downgrade attacks and runtime integrity verification to detect modifications to critical system components.
- Integration with Trusted Execution Environments: Secure boot chains for RISC-V architectures can be integrated with trusted execution environments to provide comprehensive security. This integration enables secure application execution, protected memory regions, and isolated processing environments. The combination of secure boot and trusted execution creates a foundation for building secure systems that maintain security properties throughout the device lifecycle, from boot to runtime operations.
02 Root of Trust and Key Management in RISC-V Systems
Root of Trust (RoT) implementations for RISC-V processors provide the foundation for secure boot chains. These systems manage cryptographic keys used for verification of boot components and establish hardware-based trust anchors. The key management solutions include secure key storage, key rotation mechanisms, and protection against key extraction attacks, ensuring that the boot process begins with a trusted component that verifies subsequent stages.Expand Specific Solutions03 Attestation and Verification Mechanisms
Attestation and verification mechanisms in RISC-V secure boot chains provide cryptographic proof of system integrity. These mechanisms include measurement of boot components, remote attestation protocols, and verification of firmware signatures. By implementing robust verification at each stage of the boot process, the system can detect unauthorized modifications and prevent execution of compromised code, enhancing the overall security posture.Expand Specific Solutions04 Secure Boot Extensions and Customizations for RISC-V
Extensions and customizations to the RISC-V architecture enable enhanced secure boot capabilities. These include custom security extensions, specialized instructions for cryptographic operations, and hardware security modules integrated with the processor. Such extensions allow for flexible implementation of security policies while maintaining compatibility with the RISC-V instruction set, providing system designers with options to balance security requirements with performance considerations.Expand Specific Solutions05 Protection Against Boot-Time Attacks
Protection mechanisms against various boot-time attacks ensure the integrity of the RISC-V secure boot process. These include defenses against replay attacks, side-channel attacks, physical tampering, and fault injection. Implementation of secure boot monitors, integrity measurement architecture, and runtime verification helps maintain a secure state throughout the boot sequence and detect potential security breaches before they can compromise the system.Expand Specific Solutions
Key Players in RISC-V Security Ecosystem
The secure boot chain on RISC-V is currently in an early growth phase, with market adoption accelerating as RISC-V architecture gains traction in embedded systems and IoT devices. The market size is expanding rapidly, projected to reach significant scale as security becomes paramount in edge computing. Technologically, the field is maturing with key players driving innovation: Huawei and ZTE are developing commercial implementations, while academic institutions like Institute of Software Chinese Academy of Sciences and Zhejiang University contribute foundational research. NVIDIA and Qualcomm are integrating RISC-V secure boot into their ecosystem strategies, while specialized firms like Cysec SA offer dedicated security solutions. Chinese companies including Nanjing Qinheng Microelectronics are developing RISC-V-specific security hardware, indicating a competitive landscape balancing between established tech giants and emerging specialized providers.
Huawei Technologies Co., Ltd.
Technical Solution: Huawei has developed a comprehensive secure boot architecture for RISC-V platforms that implements a multi-stage verification process. Their solution begins with an immutable Root of Trust (RoT) embedded in silicon, followed by a series of cryptographically verified boot stages. Huawei's implementation uses hardware-based security mechanisms including Physical Unclonable Functions (PUFs) for device-unique key generation and a dedicated security processor that operates independently from the main RISC-V cores. Their secure boot chain verifies each component before execution using RSA-4096 signatures and SHA-384 hashing algorithms. Huawei has also implemented anti-rollback protection through a secure monotonic counter stored in tamper-resistant memory, preventing downgrade attacks. Their solution includes runtime integrity verification that continuously monitors critical system components for unauthorized modifications, providing protection beyond the boot process.
Strengths: Comprehensive end-to-end security with hardware-based RoT and advanced cryptographic implementations. Their solution scales well across different RISC-V implementations from IoT to server platforms. Weaknesses: Proprietary elements may limit interoperability with third-party components, and the implementation requires significant hardware resources that may be excessive for constrained devices.
NVIDIA Corp.
Technical Solution: NVIDIA has developed a secure boot implementation for RISC-V that leverages their expertise in GPU security. Their approach centers on a hardware security module (HSM) that serves as the Root of Trust, with immutable boot code stored in one-time programmable (OTP) memory. NVIDIA's implementation uses elliptic curve cryptography (ECC) for signature verification, specifically the P-384 curve, which offers strong security with lower computational overhead compared to equivalent-strength RSA. Their secure boot chain includes measured boot capabilities that create cryptographic measurements of each boot component, stored in a Trusted Platform Module (TPM)-like secure element. NVIDIA has integrated their secure boot solution with TensorRT, their deep learning inference optimizer, allowing for secure AI workloads on RISC-V platforms. The implementation includes a secure debug mechanism that requires authentication before enabling debug interfaces, preventing unauthorized access while maintaining serviceability.
Strengths: Strong integration with AI/ML acceleration features and optimized cryptographic operations that minimize boot time impact. Their solution includes robust debug protection mechanisms. Weaknesses: Heavy reliance on NVIDIA's proprietary security architecture may create vendor lock-in, and the implementation may be optimized primarily for systems paired with NVIDIA GPUs rather than standalone RISC-V deployments.
Core Technical Analysis of RISC-V Secure Boot Mechanisms
Boot verification scheme employing RISC-v-oriented architecture
PatentWO2023102757A1
Innovation
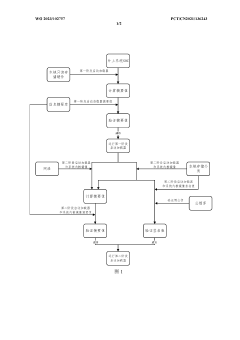
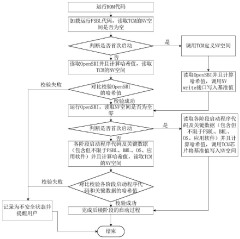
- A boot verification solution based on RISC-V architecture is designed. By constructing a system-on-chip SOC, the information digest algorithm is used to verify the integrity of the one-stage and two-stage boot loaders, and local information digest verification and remote transmission are used according to the loading source. Information digest verification or local digital signature verification methods establish a step-by-step protection mechanism for the multi-level startup process.
Code verification method and device based on RISC-V architecture
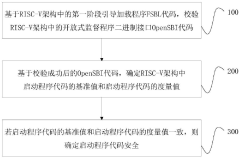
PatentPendingCN117609984A
Innovation
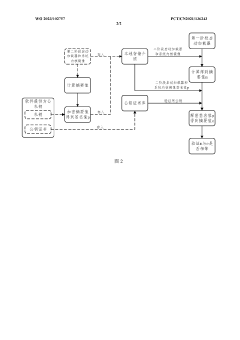
- Through the code verification method based on the RISC-V architecture, the first stage boot loader FSBL code is used to verify the OpenSBI code of the binary interface of the open supervision program to determine the benchmark value and measurement value of the startup program code. If it is consistent, it will confirm its security , use sm3 hashing operation to process undefined reference values and store them in nonvolatile memory of embedded memory to ensure the security and efficiency of the startup process.
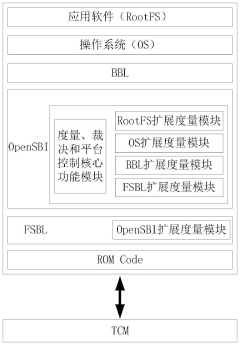
Hardware-Software Co-design Considerations
Implementing a secure boot chain on RISC-V platforms requires careful consideration of hardware-software integration points to ensure security guarantees are maintained across the entire system. The hardware architecture must provide fundamental security primitives that software components can leverage to establish a chain of trust. RISC-V's open ISA presents unique opportunities and challenges in this domain.
The hardware foundation must include secure storage elements for root keys and measurements, such as one-time programmable (OTP) memory or secure non-volatile storage that resists physical attacks. These elements should be accessible only through well-defined hardware interfaces with appropriate access controls. Additionally, the implementation of hardware-based cryptographic accelerators optimized for signature verification operations can significantly improve boot time while reducing power consumption during the verification process.
Trusted execution environments (TEEs) play a crucial role in the hardware-software boundary. RISC-V implementations should consider incorporating physical memory protection (PMP) mechanisms to isolate secure boot components from potential software-based attacks. The hardware should provide mechanisms for measuring and attesting to the state of software components, enabling verification at each stage of the boot process.
From the software perspective, developers must design boot stages with clear separation of privileges and responsibilities. Each stage should be minimal in size and complexity, focusing solely on verifying the next stage before transferring control. The software architecture should implement defense-in-depth strategies, ensuring that compromise of one component doesn't lead to system-wide security failures.
Communication interfaces between hardware and software components require careful design. Clear API definitions for accessing security features like key storage, cryptographic operations, and secure boot policy enforcement are essential. These interfaces should be thoroughly documented and undergo rigorous security review to prevent exploitation through API misuse.
Performance considerations must be balanced with security requirements. Hardware acceleration for cryptographic operations should be leveraged where available, but software implementations must be optimized for platforms lacking such features. Boot time is often critical in embedded systems, necessitating efficient verification algorithms and potential implementation of parallel verification processes where the hardware supports it.
Testing methodologies should span the hardware-software boundary, including fault injection testing to verify that hardware security features respond appropriately to attempted exploits. Simulation environments that can model both hardware and software components provide valuable platforms for security validation before physical implementation.
The hardware foundation must include secure storage elements for root keys and measurements, such as one-time programmable (OTP) memory or secure non-volatile storage that resists physical attacks. These elements should be accessible only through well-defined hardware interfaces with appropriate access controls. Additionally, the implementation of hardware-based cryptographic accelerators optimized for signature verification operations can significantly improve boot time while reducing power consumption during the verification process.
Trusted execution environments (TEEs) play a crucial role in the hardware-software boundary. RISC-V implementations should consider incorporating physical memory protection (PMP) mechanisms to isolate secure boot components from potential software-based attacks. The hardware should provide mechanisms for measuring and attesting to the state of software components, enabling verification at each stage of the boot process.
From the software perspective, developers must design boot stages with clear separation of privileges and responsibilities. Each stage should be minimal in size and complexity, focusing solely on verifying the next stage before transferring control. The software architecture should implement defense-in-depth strategies, ensuring that compromise of one component doesn't lead to system-wide security failures.
Communication interfaces between hardware and software components require careful design. Clear API definitions for accessing security features like key storage, cryptographic operations, and secure boot policy enforcement are essential. These interfaces should be thoroughly documented and undergo rigorous security review to prevent exploitation through API misuse.
Performance considerations must be balanced with security requirements. Hardware acceleration for cryptographic operations should be leveraged where available, but software implementations must be optimized for platforms lacking such features. Boot time is often critical in embedded systems, necessitating efficient verification algorithms and potential implementation of parallel verification processes where the hardware supports it.
Testing methodologies should span the hardware-software boundary, including fault injection testing to verify that hardware security features respond appropriately to attempted exploits. Simulation environments that can model both hardware and software components provide valuable platforms for security validation before physical implementation.
Security Certification and Compliance Requirements
Implementing a secure boot chain on RISC-V platforms requires adherence to various security certification standards and compliance requirements. These frameworks ensure that the secure boot implementation meets industry-recognized security levels and can be trusted in critical applications. The Common Criteria (CC) certification represents one of the most widely recognized security evaluation frameworks, with Evaluation Assurance Levels (EAL) ranging from EAL1 to EAL7, where RISC-V secure boot implementations typically target EAL4+ for commercial applications and EAL5+ for high-security government or military applications.
FIPS 140-3, the Federal Information Processing Standard for cryptographic modules, establishes specific requirements for secure boot implementations, particularly regarding cryptographic algorithm selection, key management, and tamper resistance. RISC-V secure boot chains must implement FIPS-approved algorithms for digital signatures and hash functions to achieve compliance, with SHA-256/384/512 and RSA-3072 or ECDSA being common choices.
The Payment Card Industry Data Security Standard (PCI DSS) imposes additional requirements for systems handling payment data, mandating secure boot as part of a defense-in-depth strategy. For IoT applications, the ETSI EN 303 645 standard provides baseline security requirements, including secure boot provisions to prevent unauthorized firmware modifications.
Regional regulations add another layer of compliance considerations. The EU Cyber Resilience Act and the proposed US Cyber Trust Mark program both emphasize secure boot as a fundamental security control for connected devices. In China, the TC260 security standards similarly require secure boot mechanisms for critical infrastructure systems.
Military and aerospace applications follow even stricter guidelines, such as the US Department of Defense's Security Technical Implementation Guides (STIGs) and the DO-326A airworthiness security process, both requiring robust secure boot implementations with hardware root of trust.
Certification processes typically involve extensive documentation, including Security Targets (ST) and Protection Profiles (PP), along with rigorous testing by accredited laboratories. For RISC-V implementations, certification costs can range from $100,000 for basic certifications to over $1 million for high-assurance evaluations, with timelines spanning from 6 to 24 months depending on the certification level sought.
To streamline compliance, RISC-V secure boot implementations should incorporate security requirements early in the design phase, leverage pre-certified components where possible, and maintain comprehensive documentation of security controls and testing procedures throughout the development lifecycle.
FIPS 140-3, the Federal Information Processing Standard for cryptographic modules, establishes specific requirements for secure boot implementations, particularly regarding cryptographic algorithm selection, key management, and tamper resistance. RISC-V secure boot chains must implement FIPS-approved algorithms for digital signatures and hash functions to achieve compliance, with SHA-256/384/512 and RSA-3072 or ECDSA being common choices.
The Payment Card Industry Data Security Standard (PCI DSS) imposes additional requirements for systems handling payment data, mandating secure boot as part of a defense-in-depth strategy. For IoT applications, the ETSI EN 303 645 standard provides baseline security requirements, including secure boot provisions to prevent unauthorized firmware modifications.
Regional regulations add another layer of compliance considerations. The EU Cyber Resilience Act and the proposed US Cyber Trust Mark program both emphasize secure boot as a fundamental security control for connected devices. In China, the TC260 security standards similarly require secure boot mechanisms for critical infrastructure systems.
Military and aerospace applications follow even stricter guidelines, such as the US Department of Defense's Security Technical Implementation Guides (STIGs) and the DO-326A airworthiness security process, both requiring robust secure boot implementations with hardware root of trust.
Certification processes typically involve extensive documentation, including Security Targets (ST) and Protection Profiles (PP), along with rigorous testing by accredited laboratories. For RISC-V implementations, certification costs can range from $100,000 for basic certifications to over $1 million for high-assurance evaluations, with timelines spanning from 6 to 24 months depending on the certification level sought.
To streamline compliance, RISC-V secure boot implementations should incorporate security requirements early in the design phase, leverage pre-certified components where possible, and maintain comprehensive documentation of security controls and testing procedures throughout the development lifecycle.
Unlock deeper insights with Patsnap Eureka Quick Research — get a full tech report to explore trends and direct your research. Try now!
Generate Your Research Report Instantly with AI Agent
Supercharge your innovation with Patsnap Eureka AI Agent Platform!