Trusted execution on RISC-V: SBI, SMM, and enclaves
AUG 25, 20259 MIN READ
Generate Your Research Report Instantly with AI Agent
Patsnap Eureka helps you evaluate technical feasibility & market potential.
RISC-V TEE Background and Objectives
Trusted Execution Environments (TEEs) have emerged as a critical security technology in modern computing systems, providing isolated execution spaces where sensitive code and data can be processed securely. RISC-V, as an open instruction set architecture (ISA), has gained significant momentum in recent years due to its modularity, extensibility, and open-source nature. The convergence of TEE capabilities with RISC-V presents a compelling opportunity to address security challenges in an open ecosystem.
The evolution of TEE technology began with solutions like ARM TrustZone and Intel SGX, which provided hardware-based isolation for secure processing. However, these proprietary implementations often limited flexibility and transparency. RISC-V's open approach enables a more collaborative and customizable security framework, allowing for diverse implementations tailored to specific use cases while maintaining architectural consistency.
The development of trusted execution capabilities on RISC-V encompasses several key components: Supervisor Binary Interface (SBI), Secure Virtual Machine (SVM), and enclaves. SBI provides a standardized interface between the platform firmware and the operating system, enabling secure system management. SVM extends virtualization capabilities with security guarantees, while enclaves offer isolated execution environments for sensitive applications.
Current market trends indicate growing demand for secure computing solutions across various sectors, including IoT, edge computing, cloud infrastructure, and mobile devices. The open nature of RISC-V positions it uniquely to address security concerns in these domains by enabling transparent security implementations that can be thoroughly vetted by the community, reducing the risk of hidden vulnerabilities.
The primary technical objectives for RISC-V TEE development include establishing standardized interfaces for secure operations, ensuring hardware-software co-design for optimal security-performance balance, and maintaining compatibility with existing software ecosystems. Additionally, there is a focus on scalability across different device classes, from resource-constrained IoT devices to high-performance servers.
Looking forward, the RISC-V TEE ecosystem aims to achieve formal verification of security properties, enhance resistance against side-channel attacks, and develop comprehensive security certification methodologies. These efforts are guided by principles of openness, modularity, and extensibility that characterize the broader RISC-V philosophy.
The convergence of trusted execution capabilities with RISC-V represents a significant shift in the security landscape, potentially democratizing access to robust security features while fostering innovation through open collaboration. This technical exploration seeks to understand the current state, challenges, and future directions of this important technological development.
The evolution of TEE technology began with solutions like ARM TrustZone and Intel SGX, which provided hardware-based isolation for secure processing. However, these proprietary implementations often limited flexibility and transparency. RISC-V's open approach enables a more collaborative and customizable security framework, allowing for diverse implementations tailored to specific use cases while maintaining architectural consistency.
The development of trusted execution capabilities on RISC-V encompasses several key components: Supervisor Binary Interface (SBI), Secure Virtual Machine (SVM), and enclaves. SBI provides a standardized interface between the platform firmware and the operating system, enabling secure system management. SVM extends virtualization capabilities with security guarantees, while enclaves offer isolated execution environments for sensitive applications.
Current market trends indicate growing demand for secure computing solutions across various sectors, including IoT, edge computing, cloud infrastructure, and mobile devices. The open nature of RISC-V positions it uniquely to address security concerns in these domains by enabling transparent security implementations that can be thoroughly vetted by the community, reducing the risk of hidden vulnerabilities.
The primary technical objectives for RISC-V TEE development include establishing standardized interfaces for secure operations, ensuring hardware-software co-design for optimal security-performance balance, and maintaining compatibility with existing software ecosystems. Additionally, there is a focus on scalability across different device classes, from resource-constrained IoT devices to high-performance servers.
Looking forward, the RISC-V TEE ecosystem aims to achieve formal verification of security properties, enhance resistance against side-channel attacks, and develop comprehensive security certification methodologies. These efforts are guided by principles of openness, modularity, and extensibility that characterize the broader RISC-V philosophy.
The convergence of trusted execution capabilities with RISC-V represents a significant shift in the security landscape, potentially democratizing access to robust security features while fostering innovation through open collaboration. This technical exploration seeks to understand the current state, challenges, and future directions of this important technological development.
Market Demand for RISC-V Security Solutions
The global market for RISC-V security solutions is experiencing significant growth, driven by increasing concerns about hardware security vulnerabilities and the need for trusted execution environments across various computing platforms. Current market analysis indicates that the security segment represents one of the fastest-growing areas within the broader RISC-V ecosystem, with particular demand coming from IoT, edge computing, and critical infrastructure sectors.
Enterprise customers are increasingly seeking open-source hardware security solutions that provide transparency while maintaining robust protection mechanisms. This demand stems from growing distrust of proprietary security implementations following numerous high-profile hardware vulnerabilities discovered in recent years. The market for trusted execution environments specifically has seen compound annual growth rates exceeding industry averages as organizations prioritize data protection and secure computing environments.
Financial services, healthcare, and government sectors demonstrate the strongest demand for RISC-V security solutions, particularly those implementing trusted execution capabilities like enclaves. These industries handle highly sensitive data and face strict regulatory requirements regarding data protection and system integrity. The ability to verify security implementations through open-source hardware designs represents a significant market differentiator for RISC-V-based solutions.
Geographically, North America and Europe currently lead in adoption of advanced RISC-V security features, though Asia-Pacific markets are showing the fastest growth rates as regional semiconductor manufacturers increasingly incorporate RISC-V cores into their security-focused product lines. China's push for technological self-sufficiency has particularly accelerated demand for domestically-produced secure computing solutions based on RISC-V architecture.
Market research indicates that customers are willing to pay premium prices for RISC-V implementations that include comprehensive security features like trusted execution environments, secure boot capabilities, and hardware-based key management. This price premium ranges widely based on application requirements but demonstrates the strong value proposition of security features in the RISC-V ecosystem.
Industry analysts project that the market for RISC-V security solutions will continue expanding as the architecture gains broader adoption in enterprise and critical infrastructure applications. The development of standardized security extensions and trusted execution environments represents a crucial factor in this growth trajectory, with SBI, SVM, and enclave technologies positioned as key enablers for market expansion into security-sensitive domains previously dominated by proprietary architectures.
Enterprise customers are increasingly seeking open-source hardware security solutions that provide transparency while maintaining robust protection mechanisms. This demand stems from growing distrust of proprietary security implementations following numerous high-profile hardware vulnerabilities discovered in recent years. The market for trusted execution environments specifically has seen compound annual growth rates exceeding industry averages as organizations prioritize data protection and secure computing environments.
Financial services, healthcare, and government sectors demonstrate the strongest demand for RISC-V security solutions, particularly those implementing trusted execution capabilities like enclaves. These industries handle highly sensitive data and face strict regulatory requirements regarding data protection and system integrity. The ability to verify security implementations through open-source hardware designs represents a significant market differentiator for RISC-V-based solutions.
Geographically, North America and Europe currently lead in adoption of advanced RISC-V security features, though Asia-Pacific markets are showing the fastest growth rates as regional semiconductor manufacturers increasingly incorporate RISC-V cores into their security-focused product lines. China's push for technological self-sufficiency has particularly accelerated demand for domestically-produced secure computing solutions based on RISC-V architecture.
Market research indicates that customers are willing to pay premium prices for RISC-V implementations that include comprehensive security features like trusted execution environments, secure boot capabilities, and hardware-based key management. This price premium ranges widely based on application requirements but demonstrates the strong value proposition of security features in the RISC-V ecosystem.
Industry analysts project that the market for RISC-V security solutions will continue expanding as the architecture gains broader adoption in enterprise and critical infrastructure applications. The development of standardized security extensions and trusted execution environments represents a crucial factor in this growth trajectory, with SBI, SVM, and enclave technologies positioned as key enablers for market expansion into security-sensitive domains previously dominated by proprietary architectures.
RISC-V TEE Technical Challenges
The implementation of Trusted Execution Environments (TEEs) on RISC-V architecture faces several significant technical challenges that must be addressed to ensure robust security guarantees. These challenges span hardware design, software implementation, and ecosystem development aspects.
One primary challenge is the standardization of security extensions within the RISC-V ecosystem. Unlike established architectures like ARM TrustZone or Intel SGX, RISC-V's open nature means that security extensions are still evolving, creating fragmentation in implementation approaches. This lack of unified standards complicates the development of consistent security solutions across different RISC-V implementations.
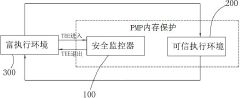
Hardware-level challenges include the implementation of secure memory isolation mechanisms. While RISC-V's Physical Memory Protection (PMP) provides basic memory isolation capabilities, developing sophisticated memory protection schemes that can efficiently support enclave-based trusted execution remains complex. The balance between security guarantees and performance overhead presents significant design challenges.
The Supervisor Binary Interface (SBI) implementation for security functions introduces another layer of complexity. Creating a standardized interface that allows secure communication between different privilege levels while maintaining strong isolation properties requires careful design considerations. Current SBI specifications need enhancement to fully support TEE requirements.
Secure Virtual Machine (SVM) implementations face challenges related to hypervisor security. Ensuring that the virtualization layer cannot compromise the security guarantees of enclaves running in virtual machines requires sophisticated hardware support and software design patterns that are still evolving in the RISC-V ecosystem.
Key management and secure boot processes present additional hurdles. Establishing a chain of trust from boot to runtime execution requires hardware root-of-trust mechanisms that are not yet standardized across RISC-V implementations. The diversity of RISC-V hardware platforms complicates the development of universal secure boot solutions.
Performance considerations also pose significant challenges. Security mechanisms inevitably introduce overhead, and optimizing TEE implementations to minimize this overhead while maintaining strong security guarantees requires sophisticated engineering approaches. The resource constraints of many RISC-V deployments, particularly in embedded systems, exacerbate this challenge.
Finally, verification and certification of RISC-V TEE implementations present methodological challenges. Formal verification techniques for complex security properties are still evolving, and established certification frameworks like Common Criteria need adaptation to address the unique characteristics of RISC-V-based security solutions.
One primary challenge is the standardization of security extensions within the RISC-V ecosystem. Unlike established architectures like ARM TrustZone or Intel SGX, RISC-V's open nature means that security extensions are still evolving, creating fragmentation in implementation approaches. This lack of unified standards complicates the development of consistent security solutions across different RISC-V implementations.
Hardware-level challenges include the implementation of secure memory isolation mechanisms. While RISC-V's Physical Memory Protection (PMP) provides basic memory isolation capabilities, developing sophisticated memory protection schemes that can efficiently support enclave-based trusted execution remains complex. The balance between security guarantees and performance overhead presents significant design challenges.
The Supervisor Binary Interface (SBI) implementation for security functions introduces another layer of complexity. Creating a standardized interface that allows secure communication between different privilege levels while maintaining strong isolation properties requires careful design considerations. Current SBI specifications need enhancement to fully support TEE requirements.
Secure Virtual Machine (SVM) implementations face challenges related to hypervisor security. Ensuring that the virtualization layer cannot compromise the security guarantees of enclaves running in virtual machines requires sophisticated hardware support and software design patterns that are still evolving in the RISC-V ecosystem.
Key management and secure boot processes present additional hurdles. Establishing a chain of trust from boot to runtime execution requires hardware root-of-trust mechanisms that are not yet standardized across RISC-V implementations. The diversity of RISC-V hardware platforms complicates the development of universal secure boot solutions.
Performance considerations also pose significant challenges. Security mechanisms inevitably introduce overhead, and optimizing TEE implementations to minimize this overhead while maintaining strong security guarantees requires sophisticated engineering approaches. The resource constraints of many RISC-V deployments, particularly in embedded systems, exacerbate this challenge.
Finally, verification and certification of RISC-V TEE implementations present methodological challenges. Formal verification techniques for complex security properties are still evolving, and established certification frameworks like Common Criteria need adaptation to address the unique characteristics of RISC-V-based security solutions.
Current SBI, SVM and Enclave Implementations
01 RISC-V Trusted Execution Environment (TEE) Architecture
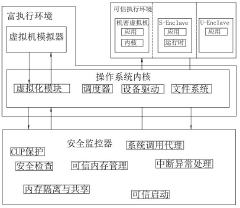
RISC-V processors can implement trusted execution environments that provide secure isolation between normal and secure worlds. These architectures typically include hardware-based security features specific to the RISC-V instruction set architecture, enabling secure boot, runtime integrity verification, and protected execution of sensitive code. The implementation often leverages RISC-V's extensibility to add security-specific instructions and privilege modes that support the creation of secure enclaves where code can execute in isolation from the rest of the system.- RISC-V Trusted Execution Environment (TEE) Implementation: Implementation of Trusted Execution Environments specifically designed for RISC-V architecture. These implementations provide secure enclaves where sensitive code and data can be processed in isolation from the rest of the system. The TEE ensures that even if the main operating system is compromised, the protected execution environment remains secure. These solutions typically include hardware-based isolation mechanisms, secure boot processes, and cryptographic operations to maintain the integrity and confidentiality of sensitive operations.
- Supervisor Binary Interface (SBI) Security Extensions: Security extensions to the RISC-V Supervisor Binary Interface that provide a standardized way for the supervisor (operating system) to interact with the machine-level functionality. These extensions enable secure communication between privilege levels and support features such as remote attestation, secure key management, and trusted I/O operations. By implementing security features at the SBI level, RISC-V systems can provide consistent security guarantees across different hardware implementations while maintaining the open and extensible nature of the architecture.
- Secure Virtual Machine (SVM) for RISC-V: Implementations of Secure Virtual Machine technology for RISC-V processors that enable isolated execution of virtual machines with hardware-enforced security boundaries. These solutions provide memory isolation, secure I/O, and protected execution contexts for virtual machines running on RISC-V hardware. SVM implementations typically leverage RISC-V's privilege modes and memory protection mechanisms to ensure that virtual machines cannot access each other's memory or resources without proper authorization, even in the presence of a compromised hypervisor.
- Hardware-based Security Mechanisms for RISC-V: Hardware-based security mechanisms specifically designed for RISC-V architecture that provide fundamental building blocks for trusted execution. These include secure boot mechanisms, hardware root of trust, physical memory protection, and cryptographic accelerators. By implementing security features directly in hardware, these solutions provide stronger security guarantees than software-only approaches and form the foundation upon which higher-level security features like enclaves and trusted execution environments can be built.
- Enclave-based Isolation for RISC-V Applications: Implementation of secure enclaves for RISC-V that provide isolated execution environments for sensitive applications. These enclaves protect the confidentiality and integrity of code and data from unauthorized access, even from privileged software like the operating system or hypervisor. Enclave solutions typically include mechanisms for secure enclave creation, attestation to verify the integrity of the enclave, secure memory encryption, and protected I/O channels. These features enable developers to build applications that can handle sensitive data securely even in untrusted environments.
02 Supervisor Binary Interface (SBI) for Security Services
The RISC-V Supervisor Binary Interface (SBI) provides a standardized way for higher privilege software to request services from lower privilege software. In security contexts, SBI can be extended to provide secure services such as key management, cryptographic operations, and secure storage access. This abstraction layer allows for consistent security implementations across different RISC-V platforms while maintaining isolation between privilege levels, which is essential for building trusted execution environments.Expand Specific Solutions03 Secure Virtual Machine (SVM) Implementation on RISC-V
Secure Virtual Machine implementations on RISC-V provide hardware-enforced isolation between virtual machines, preventing unauthorized access to sensitive data and operations. These implementations typically leverage RISC-V's privilege modes and memory protection mechanisms to create isolated execution environments. SVM technology enables multiple operating systems or applications to run concurrently while maintaining strong security boundaries, which is particularly important for systems processing sensitive information or requiring high levels of isolation between workloads.Expand Specific Solutions04 Enclave-based Security for RISC-V Systems
Enclaves provide isolated execution environments within RISC-V processors where sensitive code and data can be processed securely, even in the presence of a compromised operating system. These secure enclaves typically implement memory encryption, integrity protection, and attestation mechanisms to ensure that the code running inside the enclave has not been tampered with. The enclave architecture allows developers to minimize the trusted computing base by isolating security-critical components from the rest of the system, reducing the attack surface.Expand Specific Solutions05 Hardware-based Trust Anchors and Attestation Mechanisms
RISC-V security implementations often include hardware-based trust anchors that serve as the root of trust for the entire system. These trust anchors, which may include secure boot mechanisms, hardware security modules, or physical unclonable functions, provide a foundation for establishing and maintaining trust throughout the system's operation. Attestation mechanisms allow the system to prove its security state to remote parties, enabling secure communication and verification that the system is running trusted software in a secure configuration.Expand Specific Solutions
Key RISC-V Security Ecosystem Players
The trusted execution on RISC-V landscape is evolving rapidly, currently in an early growth phase with increasing market adoption. The global market for secure computing environments is projected to expand significantly as IoT, cloud computing, and edge devices proliferate. Intel leads with mature TEE solutions like SGX, while VMware and Red Hat contribute significant virtualization expertise. Emerging players include Huawei Cloud and Inspur, developing RISC-V-based security solutions. Google, Microsoft, and Dell are investing in hardware-software co-design approaches. Academic institutions like Fudan University and Indian Institute of Science are advancing theoretical foundations. The technology is approaching commercial viability but requires standardization across SBI, SVM, and enclave implementations to achieve widespread adoption.
Intel Corp.
Technical Solution: Intel has developed Trust Domain Extensions (TDX) technology that can be adapted to RISC-V architecture. Their approach focuses on creating isolated execution environments (enclaves) that protect sensitive code and data from privileged software attacks. For RISC-V, Intel is exploring hardware-based trusted execution environments that leverage the open nature of RISC-V ISA while maintaining compatibility with their existing security frameworks. Intel's solution incorporates memory encryption, integrity protection, and secure boot mechanisms specifically optimized for RISC-V's modular architecture. Their implementation extends the RISC-V Supervisor Binary Interface (SBI) with additional security primitives and integrates with Supervisor-mode Virtual Machine (SVM) specifications to enable secure virtualization.
Strengths: Extensive experience with TEE technologies (SGX, TDX); strong hardware security expertise; established ecosystem. Weaknesses: Primary focus remains on x86 architecture; relatively new to RISC-V implementations; potential conflicts between proprietary security approaches and RISC-V's open philosophy.
Microsoft Technology Licensing LLC
Technical Solution: Microsoft has developed a RISC-V trusted execution environment that extends their Pluton security architecture. Their approach focuses on integrating hardware-based security features with the RISC-V SBI to create a comprehensive security solution. Microsoft's implementation includes secure boot mechanisms, runtime integrity verification, and isolated execution environments. The solution leverages RISC-V's PMP (Physical Memory Protection) features and extends them with additional security primitives. Microsoft has also contributed to the RISC-V SVM specification, focusing on secure virtualization capabilities. Their approach includes a security monitor that manages the lifecycle of secure enclaves and provides attestation services. The implementation is designed to support Microsoft's confidential computing initiatives and extends to edge computing scenarios where RISC-V processors are increasingly deployed.
Strengths: Strong integration with cloud services for remote attestation; comprehensive security ecosystem; experience with TEE across multiple architectures. Weaknesses: Potential vendor lock-in concerns; relatively new to RISC-V ecosystem; implementation complexity may impact performance on resource-constrained devices.
Core RISC-V TEE Technologies Analysis
Trusted execution environment implementation method, computer equipment and storage medium
PatentActiveCN117494108A
Innovation
- By adding enclaves in addition to the virtual machine manager and confidential virtual machines, use the security monitor to create trusted execution environment instances, including confidential virtual machines, management state enclaves and user state enclaves, and configure two-stage page tables to achieve memory isolation and sharing, perform status switching and recovery and security checks.
UEFI firmware starting method based on RISC-V architecture embedded device
PatentPendingCN117785314A
Innovation
- Split SBI from the SEC stage of EDK2 and exist as an independent part before the SEC stage to achieve the flexibility and scalability of the SBI stage and increase the possibility of security verification and mode switching. The EDK2 stage is in S-mode. The SBI stage is in M-mode, which simplifies the debugging and update process.
RISC-V Security Standards and Compliance
The RISC-V architecture has established several security standards and compliance frameworks to ensure consistent implementation of security features across different hardware platforms. These standards are critical for establishing trust in RISC-V-based systems, particularly for applications requiring high security assurance levels.
The RISC-V Foundation's Security Standing Committee has developed comprehensive security specifications that address various aspects of trusted execution environments. These specifications include mandatory security extensions and optional features that implementers can adopt based on their security requirements. The compliance framework ensures that vendors adhere to these specifications, providing a standardized approach to security implementation.
Key security standards for RISC-V include the Physical Memory Protection (PMP) specification, which enables fine-grained memory access control, and the Privileged Architecture specification that defines security domains and privilege levels. These foundational standards form the basis for implementing trusted execution environments on RISC-V platforms.
For trusted execution specifically, the RISC-V Supervisor Binary Interface (SBI) standard defines the interface between the supervisor mode and machine mode, establishing a secure communication channel between these privilege levels. This standardization is crucial for implementing security features like secure boot and runtime attestation.
The Secure Virtual Machine (SVM) specification builds upon these foundations to provide hardware-enforced isolation for virtual machines. It standardizes the interfaces and mechanisms for secure virtualization, enabling confidential computing applications where the hypervisor itself may not be trusted.
Enclave implementations on RISC-V follow the Trusted Execution Environment (TEE) standards, which define how secure enclaves should be isolated, attested, and managed. These standards ensure interoperability between different enclave implementations and provide a common security model for developers.
Compliance testing for RISC-V security features involves rigorous verification against established security criteria. The RISC-V Foundation has developed compliance test suites that validate implementations against the security specifications. These tests verify correct implementation of security features like memory isolation, secure boot, and cryptographic acceleration.
Industry certification programs are emerging to validate RISC-V implementations against recognized security standards such as Common Criteria and FIPS 140-3. These certification processes help establish trust in RISC-V-based security solutions and facilitate their adoption in security-sensitive applications.
The RISC-V Foundation's Security Standing Committee has developed comprehensive security specifications that address various aspects of trusted execution environments. These specifications include mandatory security extensions and optional features that implementers can adopt based on their security requirements. The compliance framework ensures that vendors adhere to these specifications, providing a standardized approach to security implementation.
Key security standards for RISC-V include the Physical Memory Protection (PMP) specification, which enables fine-grained memory access control, and the Privileged Architecture specification that defines security domains and privilege levels. These foundational standards form the basis for implementing trusted execution environments on RISC-V platforms.
For trusted execution specifically, the RISC-V Supervisor Binary Interface (SBI) standard defines the interface between the supervisor mode and machine mode, establishing a secure communication channel between these privilege levels. This standardization is crucial for implementing security features like secure boot and runtime attestation.
The Secure Virtual Machine (SVM) specification builds upon these foundations to provide hardware-enforced isolation for virtual machines. It standardizes the interfaces and mechanisms for secure virtualization, enabling confidential computing applications where the hypervisor itself may not be trusted.
Enclave implementations on RISC-V follow the Trusted Execution Environment (TEE) standards, which define how secure enclaves should be isolated, attested, and managed. These standards ensure interoperability between different enclave implementations and provide a common security model for developers.
Compliance testing for RISC-V security features involves rigorous verification against established security criteria. The RISC-V Foundation has developed compliance test suites that validate implementations against the security specifications. These tests verify correct implementation of security features like memory isolation, secure boot, and cryptographic acceleration.
Industry certification programs are emerging to validate RISC-V implementations against recognized security standards such as Common Criteria and FIPS 140-3. These certification processes help establish trust in RISC-V-based security solutions and facilitate their adoption in security-sensitive applications.
Open Source vs Proprietary TEE Approaches
The landscape of Trusted Execution Environment (TEE) implementations for RISC-V presents a fascinating dichotomy between open source and proprietary approaches. Open source TEE solutions for RISC-V, such as Keystone and MultiZone Security, offer transparency, community-driven development, and flexibility. These implementations allow for peer review of security mechanisms, potentially leading to more robust solutions through the "many eyes" principle. The open nature facilitates customization for specific use cases and encourages broader adoption across the RISC-V ecosystem.
In contrast, proprietary TEE approaches like Hex Five's MultiZone Security (in its commercial version) and Sanctum provide vendor-guaranteed security assurances and often include professional support services. These solutions typically undergo rigorous internal security audits and may offer performance optimizations that aren't publicly disclosed. For enterprises requiring certification or compliance with specific security standards, proprietary solutions often provide more straightforward paths to verification.
The RISC-V community has shown a strong preference for open standards, reflected in initiatives like the RISC-V TEE Task Group working to standardize TEE interfaces. This standardization effort aims to ensure interoperability between different TEE implementations while allowing both open source and proprietary solutions to coexist in the ecosystem.
From a technical perspective, open source TEEs often leverage RISC-V's Physical Memory Protection (PMP) and memory isolation features directly, with transparent implementation details. Proprietary solutions may employ additional proprietary hardware extensions or custom firmware that enhances security but remains closed-source.
Market dynamics reveal interesting patterns: open source TEEs tend to gain traction in academic research, IoT applications, and environments where customization is paramount. Proprietary solutions find stronger adoption in high-security applications like financial services, military systems, and scenarios where formal security guarantees are non-negotiable.
The choice between open source and proprietary approaches ultimately depends on specific requirements including security assurance levels, customization needs, budget constraints, and long-term support considerations. Many organizations adopt hybrid approaches, using open source foundations with proprietary enhancements for critical security components.
As RISC-V continues to mature, we anticipate convergence toward standardized TEE interfaces that allow both open source and proprietary implementations to flourish, giving system designers the freedom to choose solutions that best match their security and business requirements.
In contrast, proprietary TEE approaches like Hex Five's MultiZone Security (in its commercial version) and Sanctum provide vendor-guaranteed security assurances and often include professional support services. These solutions typically undergo rigorous internal security audits and may offer performance optimizations that aren't publicly disclosed. For enterprises requiring certification or compliance with specific security standards, proprietary solutions often provide more straightforward paths to verification.
The RISC-V community has shown a strong preference for open standards, reflected in initiatives like the RISC-V TEE Task Group working to standardize TEE interfaces. This standardization effort aims to ensure interoperability between different TEE implementations while allowing both open source and proprietary solutions to coexist in the ecosystem.
From a technical perspective, open source TEEs often leverage RISC-V's Physical Memory Protection (PMP) and memory isolation features directly, with transparent implementation details. Proprietary solutions may employ additional proprietary hardware extensions or custom firmware that enhances security but remains closed-source.
Market dynamics reveal interesting patterns: open source TEEs tend to gain traction in academic research, IoT applications, and environments where customization is paramount. Proprietary solutions find stronger adoption in high-security applications like financial services, military systems, and scenarios where formal security guarantees are non-negotiable.
The choice between open source and proprietary approaches ultimately depends on specific requirements including security assurance levels, customization needs, budget constraints, and long-term support considerations. Many organizations adopt hybrid approaches, using open source foundations with proprietary enhancements for critical security components.
As RISC-V continues to mature, we anticipate convergence toward standardized TEE interfaces that allow both open source and proprietary implementations to flourish, giving system designers the freedom to choose solutions that best match their security and business requirements.
Unlock deeper insights with Patsnap Eureka Quick Research — get a full tech report to explore trends and direct your research. Try now!
Generate Your Research Report Instantly with AI Agent
Supercharge your innovation with Patsnap Eureka AI Agent Platform!