Open-source RISC-V SOCs: risks, licenses, and support models
AUG 25, 20259 MIN READ
Generate Your Research Report Instantly with AI Agent
Patsnap Eureka helps you evaluate technical feasibility & market potential.
RISC-V Evolution and Objectives
RISC-V has evolved from an academic project at the University of California, Berkeley in 2010 to a global open standard instruction set architecture (ISA) that is revolutionizing the semiconductor industry. Initially designed to support computer architecture research and education, RISC-V has rapidly gained traction as a viable alternative to proprietary architectures like ARM and x86. The evolution of RISC-V has been characterized by its modular design philosophy, which allows for customization while maintaining compatibility across implementations.
The RISC-V Foundation, established in 2015 and later reorganized as RISC-V International in 2020, has played a pivotal role in standardizing the architecture and fostering its adoption. This transition to a Switzerland-based organization was strategically important to ensure RISC-V's global accessibility, particularly amid geopolitical tensions affecting technology transfer. The standardization process has been remarkably inclusive, involving contributions from academia, industry, and government entities worldwide.
From a technical perspective, RISC-V has evolved through several specification versions, each expanding the architecture's capabilities. The base integer instruction sets (RV32I, RV64I) provide the foundation, while standard extensions for multiplication/division (M), atomic operations (A), floating-point (F/D), and compressed instructions (C) have been progressively standardized. More recently, vector extensions (V) and bit manipulation extensions (B) have been developed to address high-performance computing and embedded applications respectively.
The objectives of RISC-V extend beyond merely providing an open ISA. A primary goal is to establish a truly open ecosystem for system-on-chip (SoC) development, enabling innovation without licensing constraints. This includes not only the core architecture but also peripheral interfaces, debug specifications, and software toolchains. The RISC-V community aims to create a comprehensive platform that supports everything from tiny microcontrollers to high-performance server processors.
Another key objective is to address the fragmentation risks inherent in open-source hardware. While customization is a strength of RISC-V, excessive divergence could undermine compatibility. The RISC-V Foundation has implemented compliance testing frameworks and certification processes to ensure implementations remain compatible with the standard, balancing innovation with interoperability.
Looking forward, RISC-V aims to achieve performance parity with established architectures while maintaining its power efficiency advantages. The community is actively developing advanced features like trusted execution environments, virtualization support, and specialized accelerators to address emerging application domains such as AI/ML, edge computing, and secure IoT deployments.
The RISC-V Foundation, established in 2015 and later reorganized as RISC-V International in 2020, has played a pivotal role in standardizing the architecture and fostering its adoption. This transition to a Switzerland-based organization was strategically important to ensure RISC-V's global accessibility, particularly amid geopolitical tensions affecting technology transfer. The standardization process has been remarkably inclusive, involving contributions from academia, industry, and government entities worldwide.
From a technical perspective, RISC-V has evolved through several specification versions, each expanding the architecture's capabilities. The base integer instruction sets (RV32I, RV64I) provide the foundation, while standard extensions for multiplication/division (M), atomic operations (A), floating-point (F/D), and compressed instructions (C) have been progressively standardized. More recently, vector extensions (V) and bit manipulation extensions (B) have been developed to address high-performance computing and embedded applications respectively.
The objectives of RISC-V extend beyond merely providing an open ISA. A primary goal is to establish a truly open ecosystem for system-on-chip (SoC) development, enabling innovation without licensing constraints. This includes not only the core architecture but also peripheral interfaces, debug specifications, and software toolchains. The RISC-V community aims to create a comprehensive platform that supports everything from tiny microcontrollers to high-performance server processors.
Another key objective is to address the fragmentation risks inherent in open-source hardware. While customization is a strength of RISC-V, excessive divergence could undermine compatibility. The RISC-V Foundation has implemented compliance testing frameworks and certification processes to ensure implementations remain compatible with the standard, balancing innovation with interoperability.
Looking forward, RISC-V aims to achieve performance parity with established architectures while maintaining its power efficiency advantages. The community is actively developing advanced features like trusted execution environments, virtualization support, and specialized accelerators to address emerging application domains such as AI/ML, edge computing, and secure IoT deployments.
Market Demand Analysis for Open-Source SOCs
The open-source RISC-V SoC market is experiencing unprecedented growth, driven by increasing demand for customizable, vendor-neutral computing solutions. Recent market analyses indicate that the global RISC-V semiconductor market is projected to grow at a CAGR of over 40% through 2027, reflecting the strong industry interest in this architecture.
The primary market demand stems from organizations seeking greater design freedom and reduced dependency on proprietary architectures like ARM and x86. This shift is particularly evident in regions pursuing technological sovereignty, with China, Europe, and India making significant investments in RISC-V development to reduce reliance on US-controlled technologies.
Industry sectors showing the strongest demand include IoT devices, edge computing, and embedded systems, where RISC-V's scalability and power efficiency provide compelling advantages. The automotive sector has also emerged as a significant growth area, with manufacturers exploring RISC-V for next-generation vehicle control systems and autonomous driving platforms.
Enterprise customers are increasingly attracted to open-source SoCs due to long-term cost benefits, despite higher initial engineering investments. The elimination of recurring licensing fees represents substantial savings for high-volume deployments, while the transparency of open-source hardware addresses growing security concerns in critical infrastructure.
Market research indicates that 68% of semiconductor companies are now investing in RISC-V projects, up from just 28% in 2019. This surge reflects both defensive positioning and recognition of genuine market opportunities in the open hardware ecosystem.
The academic and research sectors represent another significant market segment, with universities and research institutions adopting RISC-V as a teaching and research platform. This educational foundation is creating a pipeline of engineers familiar with the architecture, further accelerating industry adoption.
Supply chain resilience has emerged as a critical market driver following recent global disruptions. Organizations are increasingly viewing open-source hardware as a strategic hedge against geopolitical risks affecting proprietary technology access.
However, market analysis reveals persistent challenges in the ecosystem. The fragmentation of RISC-V implementations and support models creates uncertainty for potential adopters. Organizations report concerns about the maturity of development tools, verification methodologies, and production-ready IP blocks compared to established architectures.
Despite these challenges, market forecasts remain highly positive. The combination of technological advantages, economic benefits, and strategic considerations is creating sustained demand growth across multiple sectors, positioning open-source RISC-V SoCs as a transformative force in the semiconductor industry.
The primary market demand stems from organizations seeking greater design freedom and reduced dependency on proprietary architectures like ARM and x86. This shift is particularly evident in regions pursuing technological sovereignty, with China, Europe, and India making significant investments in RISC-V development to reduce reliance on US-controlled technologies.
Industry sectors showing the strongest demand include IoT devices, edge computing, and embedded systems, where RISC-V's scalability and power efficiency provide compelling advantages. The automotive sector has also emerged as a significant growth area, with manufacturers exploring RISC-V for next-generation vehicle control systems and autonomous driving platforms.
Enterprise customers are increasingly attracted to open-source SoCs due to long-term cost benefits, despite higher initial engineering investments. The elimination of recurring licensing fees represents substantial savings for high-volume deployments, while the transparency of open-source hardware addresses growing security concerns in critical infrastructure.
Market research indicates that 68% of semiconductor companies are now investing in RISC-V projects, up from just 28% in 2019. This surge reflects both defensive positioning and recognition of genuine market opportunities in the open hardware ecosystem.
The academic and research sectors represent another significant market segment, with universities and research institutions adopting RISC-V as a teaching and research platform. This educational foundation is creating a pipeline of engineers familiar with the architecture, further accelerating industry adoption.
Supply chain resilience has emerged as a critical market driver following recent global disruptions. Organizations are increasingly viewing open-source hardware as a strategic hedge against geopolitical risks affecting proprietary technology access.
However, market analysis reveals persistent challenges in the ecosystem. The fragmentation of RISC-V implementations and support models creates uncertainty for potential adopters. Organizations report concerns about the maturity of development tools, verification methodologies, and production-ready IP blocks compared to established architectures.
Despite these challenges, market forecasts remain highly positive. The combination of technological advantages, economic benefits, and strategic considerations is creating sustained demand growth across multiple sectors, positioning open-source RISC-V SoCs as a transformative force in the semiconductor industry.
RISC-V Technical Landscape and Challenges
The RISC-V architecture has emerged as a significant disruptor in the semiconductor industry, offering an open-source alternative to proprietary instruction set architectures (ISAs). The technical landscape of RISC-V has evolved rapidly since its inception at UC Berkeley in 2010, transforming from an academic project to a global industry standard supported by the RISC-V International Foundation, which now includes over 2,000 members across 70 countries.
The core strength of RISC-V lies in its modular and extensible design philosophy. The base integer instruction set (RV32I/RV64I) provides fundamental operations, while standard extensions such as M (multiplication/division), A (atomic operations), F/D (single/double-precision floating-point), and C (compressed instructions) can be selectively implemented based on application requirements. This modularity enables unprecedented customization for specific use cases, from tiny microcontrollers to high-performance computing systems.
Despite its promising trajectory, RISC-V faces several significant technical challenges. First, the fragmentation risk inherent in its extensible nature could lead to compatibility issues across implementations. While the base ISA ensures a level of standardization, custom extensions might create ecosystem silos that undermine the architecture's portability benefits.
Hardware maturity represents another challenge, particularly for high-performance applications. While RISC-V excels in embedded and IoT contexts, it still lags behind established architectures like Arm and x86 in areas requiring advanced features such as out-of-order execution, sophisticated branch prediction, and high-performance memory subsystems. The performance gap is gradually narrowing but remains significant for compute-intensive workloads.
The software ecosystem, though rapidly developing, presents additional challenges. Compiler optimization for RISC-V, especially for custom extensions, requires substantial engineering effort. Operating system support has improved dramatically with Linux kernel mainline inclusion, but driver availability and optimization remain works in progress. Development tools, debugging capabilities, and middleware solutions are still maturing compared to established architectures.
Verification and security present further technical hurdles. The open nature of RISC-V means implementations must be rigorously verified to ensure compliance with the specification. Security features like trusted execution environments and memory protection are being developed but are not yet as comprehensive as those in proprietary architectures with decades of security hardening.
Geographically, RISC-V development shows interesting patterns, with significant activity clusters in North America (particularly Silicon Valley), Europe (especially in research institutions), and increasingly in Asia, where China has made RISC-V a strategic priority for technological self-sufficiency amid trade restrictions.
The core strength of RISC-V lies in its modular and extensible design philosophy. The base integer instruction set (RV32I/RV64I) provides fundamental operations, while standard extensions such as M (multiplication/division), A (atomic operations), F/D (single/double-precision floating-point), and C (compressed instructions) can be selectively implemented based on application requirements. This modularity enables unprecedented customization for specific use cases, from tiny microcontrollers to high-performance computing systems.
Despite its promising trajectory, RISC-V faces several significant technical challenges. First, the fragmentation risk inherent in its extensible nature could lead to compatibility issues across implementations. While the base ISA ensures a level of standardization, custom extensions might create ecosystem silos that undermine the architecture's portability benefits.
Hardware maturity represents another challenge, particularly for high-performance applications. While RISC-V excels in embedded and IoT contexts, it still lags behind established architectures like Arm and x86 in areas requiring advanced features such as out-of-order execution, sophisticated branch prediction, and high-performance memory subsystems. The performance gap is gradually narrowing but remains significant for compute-intensive workloads.
The software ecosystem, though rapidly developing, presents additional challenges. Compiler optimization for RISC-V, especially for custom extensions, requires substantial engineering effort. Operating system support has improved dramatically with Linux kernel mainline inclusion, but driver availability and optimization remain works in progress. Development tools, debugging capabilities, and middleware solutions are still maturing compared to established architectures.
Verification and security present further technical hurdles. The open nature of RISC-V means implementations must be rigorously verified to ensure compliance with the specification. Security features like trusted execution environments and memory protection are being developed but are not yet as comprehensive as those in proprietary architectures with decades of security hardening.
Geographically, RISC-V development shows interesting patterns, with significant activity clusters in North America (particularly Silicon Valley), Europe (especially in research institutions), and increasingly in Asia, where China has made RISC-V a strategic priority for technological self-sufficiency amid trade restrictions.
Current Open-Source SOC Implementation Models
01 License compliance and intellectual property risks
Open-source RISC-V SOCs involve various licensing models that present intellectual property challenges. Organizations must navigate complex license compliance requirements when integrating RISC-V cores into their designs. The open-source nature creates potential risks related to IP infringement, patent claims, and license compatibility issues. Companies need to implement proper license management strategies and conduct thorough IP audits to mitigate these risks.- License compliance and intellectual property risks: Open-source RISC-V SOCs present unique intellectual property challenges due to their open nature. Organizations must carefully navigate license compliance issues when integrating RISC-V cores with proprietary components. The varying open-source licenses (GPL, MIT, Apache, etc.) require different compliance approaches. Companies must conduct thorough IP audits to ensure they understand the licensing obligations and avoid potential infringement claims or forced code disclosure.
- Security vulnerabilities and hardware trust: Open-source hardware designs like RISC-V SOCs face security challenges including potential backdoors, side-channel attacks, and hardware vulnerabilities. The transparency of open-source designs allows for community scrutiny but also exposes potential attack vectors. Organizations must implement robust security validation processes, hardware root-of-trust mechanisms, and secure boot implementations to mitigate these risks in RISC-V deployments.
- Commercial support models and ecosystem maturity: The RISC-V ecosystem offers various support models ranging from community-based to commercial vendor support. Organizations adopting RISC-V must evaluate the maturity of these support channels, considering factors like documentation quality, tool availability, and long-term maintenance commitments. Commercial support options include subscription services, consulting, and custom implementation assistance, while community support relies on forums, open documentation, and collaborative development.
- Design verification and compatibility challenges: RISC-V implementations face verification challenges due to the flexibility of the instruction set architecture. Ensuring compatibility across different RISC-V implementations requires comprehensive testing and validation. Organizations must address issues related to extensions compatibility, toolchain integration, and performance optimization. The open nature of RISC-V allows for customization but increases the complexity of verification and interoperability testing.
- Supply chain and long-term viability considerations: Organizations adopting open-source RISC-V SOCs must evaluate supply chain resilience and long-term viability. Considerations include the stability of core maintainers, foundry support, manufacturing partnerships, and component availability. Unlike proprietary architectures with established supply chains, RISC-V implementations may have less predictable long-term support. Strategic risk assessment should include contingency planning for design modifications, alternative suppliers, and potential technology migration paths.
02 Security vulnerabilities and hardware trust
Open-source RISC-V implementations may contain security vulnerabilities that pose risks to system integrity. The transparent nature of open-source hardware creates both advantages and challenges for security assessment. Organizations must implement robust security validation processes, hardware root-of-trust mechanisms, and secure boot implementations. Addressing hardware-level security concerns requires specialized expertise and comprehensive testing methodologies to ensure protection against various attack vectors.Expand Specific Solutions03 Support models and ecosystem maturity
The support ecosystem for open-source RISC-V SOCs varies widely in maturity and reliability. Organizations adopting RISC-V technology must evaluate support options including community forums, commercial support contracts, and internal expertise development. The fragmentation of support resources can lead to challenges in troubleshooting, maintenance, and long-term sustainability. Companies need to develop strategies for accessing technical support, documentation, and design resources across the RISC-V ecosystem.Expand Specific Solutions04 Verification and compliance challenges
Ensuring that open-source RISC-V implementations comply with the ISA specification requires comprehensive verification processes. Organizations face challenges in validating hardware designs, ensuring compatibility with software tools, and meeting industry standards. The verification process for RISC-V cores demands specialized expertise and robust testing methodologies. Companies must establish verification frameworks that address both functional correctness and performance requirements.Expand Specific Solutions05 Commercial viability and business model considerations
Adopting open-source RISC-V SOCs presents unique business challenges related to commercialization, market acceptance, and long-term viability. Organizations must develop appropriate business models that balance open-source principles with commercial objectives. Considerations include monetization strategies, competitive differentiation, and market positioning. Companies need to assess the total cost of ownership, including development resources, support requirements, and potential licensing costs when implementing RISC-V solutions.Expand Specific Solutions
Key RISC-V Ecosystem Players
The open-source RISC-V SOC market is currently in an early growth phase, characterized by rapid technological advancement but still evolving maturity. The ecosystem is expanding with estimated market size reaching $1-2 billion, projected to grow significantly as adoption increases across IoT, embedded systems, and data centers. Technical maturity varies considerably among key players, with academic institutions (National University of Defense Technology, Zhejiang University, Southeast University) focusing on research innovation, while commercial entities like Alibaba, Tencent, and China Mobile develop practical implementations. Western companies such as SAP and Capital One are exploring RISC-V for specific applications, while Chinese companies including Nanjing Qinheng Microelectronics and Super Core Technology are advancing commercial-grade SOCs, though standardization of support models and licensing frameworks remains a challenge.
Zhejiang University
Technical Solution: Zhejiang University has developed the "ZJV" RISC-V processor series as part of their academic research initiatives. Their implementation focuses on educational and research applications with a modular architecture that allows for easy customization and extension. The ZJV platform includes configurable cache hierarchies, optional floating-point units, and parameterizable pipeline depths to support different performance targets. Their licensing approach is fully academic, with all designs released under permissive open-source licenses (primarily MIT license) that encourage both academic and commercial adoption. The support model is centered around academic collaboration, with detailed documentation, teaching materials, and laboratory exercises available publicly. Zhejiang University regularly hosts workshops and training sessions on RISC-V architecture and provides a simulation environment for testing and verification without hardware.
Strengths: Excellent educational resources and documentation; highly modular design facilitates customization for specific research needs; permissive licensing reduces legal barriers to adoption. Weaknesses: Limited commercial support infrastructure; performance optimizations may lag behind industry implementations; development pace depends on academic funding cycles and research priorities.
Institute of Software Chinese Academy of Sciences
Technical Solution: The Institute of Software at the Chinese Academy of Sciences has developed "ISCAS-RISC-V," an open-source SoC platform focused on security, reliability, and formal verification. Their implementation includes hardware-based security features such as memory protection units, secure boot mechanisms, and physical unclonable functions (PUFs) for device authentication. The licensing model follows a tiered approach with core components released under the Apache 2.0 license, while advanced security modules are available under a research license that requires attribution and collaboration. Their support model emphasizes rigorous verification and certification, with comprehensive test suites, formal verification tools, and security analysis frameworks. The Institute maintains a dedicated research team for vulnerability assessment and provides regular security bulletins and patches for known issues. They collaborate with industry partners to ensure practical applicability while maintaining academic rigor in their implementations.
Strengths: Strong focus on formal verification reduces reliability risks; comprehensive security features suitable for critical applications; academic backing ensures theoretical soundness of implementations. Weaknesses: Research-oriented approach may limit commercial readiness; complex licensing structure for advanced features; support resources primarily oriented toward technical researchers rather than commercial developers.
Critical IP and Licensing Frameworks
Chip starting method and device, electronic equipment and storage medium
PatentPendingCN117827313A
Innovation
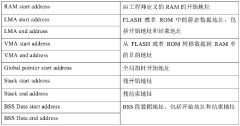
- Provide a universal RISC-V chip startup method, including loading predefined startup code, initializing variables, vector tables, global pointers and stack pointers, performing peripheral or system function initialization, and copying data from FLASH to RAM to achieve BSS segment initialization, written in C language to simplify the programming process.
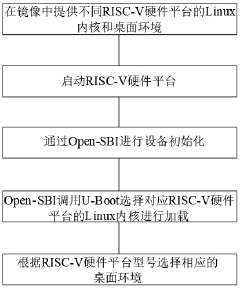
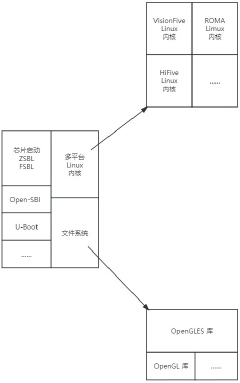
Multi-RISC-V platform-oriented general Linux operating system mirror image design method
PatentInactiveCN117075957A
Innovation
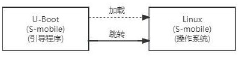
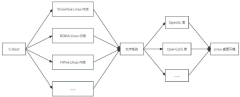
- Design a universal Linux operating system image method for multiple RISC-V platforms. By providing Linux kernel and desktop environment components for different RISC-V hardware platforms, Open-SBI and U-Boot are used for device initialization and kernel loading. According to the hardware The platform model loads the desktop environment, realizes adaptive kernel and file system selection, and builds a unified system image.
Risk Mitigation Strategies
To effectively mitigate risks associated with open-source RISC-V SoCs, organizations must implement comprehensive strategies that address technical, legal, and operational challenges. A multi-layered approach begins with thorough due diligence on all open-source components, including verification of license compliance and compatibility across the entire SoC stack. This process should involve legal experts specializing in open-source licensing to prevent potential intellectual property conflicts.
Establishing redundant supply chains represents another critical mitigation strategy. Organizations should avoid single-source dependencies by identifying multiple vendors or community solutions for essential components. This approach provides alternatives should support for a particular component become unavailable or if licensing terms change unexpectedly.
Active community participation serves as both a risk mitigation strategy and a competitive advantage. By contributing resources to relevant open-source projects, organizations can influence development directions, gain early insight into potential issues, and build relationships with key community members. This involvement helps ensure that critical components remain well-maintained and aligned with organizational needs.
Internal capability development forms the foundation of long-term risk management. Organizations should invest in building in-house expertise for core RISC-V technologies, enabling them to maintain, modify, or replace components when necessary. This capability reduces dependency on external support and provides greater control over the technology stack.
Formal support agreements with commercial entities offering RISC-V solutions provide an additional safety net. These agreements should clearly define service levels, response times, and long-term support commitments. For mission-critical applications, organizations might consider dual-sourcing strategies that combine open-source implementations with commercial alternatives.
Continuous monitoring of the RISC-V ecosystem is essential for early risk identification. This includes tracking changes in licensing terms, community health metrics, and technical roadmaps of key components. Establishing a dedicated open-source program office can centralize these monitoring efforts and coordinate appropriate responses to emerging risks.
Finally, organizations should develop contingency plans for various risk scenarios, including license changes, project abandonment, or security vulnerabilities. These plans should outline specific actions, responsible parties, and recovery timelines to minimize potential disruption to development or production environments.
Establishing redundant supply chains represents another critical mitigation strategy. Organizations should avoid single-source dependencies by identifying multiple vendors or community solutions for essential components. This approach provides alternatives should support for a particular component become unavailable or if licensing terms change unexpectedly.
Active community participation serves as both a risk mitigation strategy and a competitive advantage. By contributing resources to relevant open-source projects, organizations can influence development directions, gain early insight into potential issues, and build relationships with key community members. This involvement helps ensure that critical components remain well-maintained and aligned with organizational needs.
Internal capability development forms the foundation of long-term risk management. Organizations should invest in building in-house expertise for core RISC-V technologies, enabling them to maintain, modify, or replace components when necessary. This capability reduces dependency on external support and provides greater control over the technology stack.
Formal support agreements with commercial entities offering RISC-V solutions provide an additional safety net. These agreements should clearly define service levels, response times, and long-term support commitments. For mission-critical applications, organizations might consider dual-sourcing strategies that combine open-source implementations with commercial alternatives.
Continuous monitoring of the RISC-V ecosystem is essential for early risk identification. This includes tracking changes in licensing terms, community health metrics, and technical roadmaps of key components. Establishing a dedicated open-source program office can centralize these monitoring efforts and coordinate appropriate responses to emerging risks.
Finally, organizations should develop contingency plans for various risk scenarios, including license changes, project abandonment, or security vulnerabilities. These plans should outline specific actions, responsible parties, and recovery timelines to minimize potential disruption to development or production environments.
Commercial Support Ecosystem
The RISC-V commercial support ecosystem has evolved significantly in recent years, transforming from a primarily academic initiative to a robust commercial environment. Companies like SiFive, Andes Technology, and Microchip have established comprehensive support models for their RISC-V implementations, offering various tiers of technical assistance, documentation, and development tools.
These commercial entities typically provide multi-layered support structures, ranging from basic community forums to premium enterprise-level support with guaranteed response times and dedicated technical account managers. SiFive, for instance, offers professional services that include architectural consulting, custom core design, and optimization services tailored to specific application requirements.
The ecosystem also features specialized third-party support providers who bridge the gap between open-source foundations and commercial implementation. These companies offer integration services, verification support, and production-ready toolchains that complement the core RISC-V technology. Notably, companies like Imperas and Lauterbach have developed sophisticated debugging and simulation tools specifically optimized for RISC-V architectures.
Training and certification programs have emerged as another critical component of the commercial support ecosystem. Organizations like the RISC-V International Association collaborate with industry partners to develop standardized certification programs, ensuring consistent knowledge and implementation quality across the ecosystem. These programs help address the skills gap that often accompanies emerging technologies.
Cloud service providers have also entered the RISC-V support landscape, with companies like AWS and Google Cloud offering development environments and simulation platforms that enable teams to prototype and test RISC-V designs without significant hardware investments. These services typically include pre-configured development environments with optimized toolchains and debugging capabilities.
The commercial support ecosystem extends to silicon manufacturing partners who provide fabrication services optimized for RISC-V designs. TSMC, GlobalFoundries, and other foundries have developed process design kits specifically tailored for RISC-V implementations, streamlining the path from design to production.
As the ecosystem matures, subscription-based support models are becoming increasingly common, allowing organizations to budget predictably for ongoing technical assistance while receiving regular updates, security patches, and access to evolving design resources. These models often include different tiers catering to various organizational needs, from individual developers to large enterprises deploying RISC-V at scale.
These commercial entities typically provide multi-layered support structures, ranging from basic community forums to premium enterprise-level support with guaranteed response times and dedicated technical account managers. SiFive, for instance, offers professional services that include architectural consulting, custom core design, and optimization services tailored to specific application requirements.
The ecosystem also features specialized third-party support providers who bridge the gap between open-source foundations and commercial implementation. These companies offer integration services, verification support, and production-ready toolchains that complement the core RISC-V technology. Notably, companies like Imperas and Lauterbach have developed sophisticated debugging and simulation tools specifically optimized for RISC-V architectures.
Training and certification programs have emerged as another critical component of the commercial support ecosystem. Organizations like the RISC-V International Association collaborate with industry partners to develop standardized certification programs, ensuring consistent knowledge and implementation quality across the ecosystem. These programs help address the skills gap that often accompanies emerging technologies.
Cloud service providers have also entered the RISC-V support landscape, with companies like AWS and Google Cloud offering development environments and simulation platforms that enable teams to prototype and test RISC-V designs without significant hardware investments. These services typically include pre-configured development environments with optimized toolchains and debugging capabilities.
The commercial support ecosystem extends to silicon manufacturing partners who provide fabrication services optimized for RISC-V designs. TSMC, GlobalFoundries, and other foundries have developed process design kits specifically tailored for RISC-V implementations, streamlining the path from design to production.
As the ecosystem matures, subscription-based support models are becoming increasingly common, allowing organizations to budget predictably for ongoing technical assistance while receiving regular updates, security patches, and access to evolving design resources. These models often include different tiers catering to various organizational needs, from individual developers to large enterprises deploying RISC-V at scale.
Unlock deeper insights with Patsnap Eureka Quick Research — get a full tech report to explore trends and direct your research. Try now!
Generate Your Research Report Instantly with AI Agent
Supercharge your innovation with Patsnap Eureka AI Agent Platform!